Cisco 350-401 Implementing and Operating Cisco Enterprise Network Core Technologies (ENCOR) Online Training
Cisco 350-401 Online Training
The questions for 350-401 were last updated at Jan 27,2026.
- Exam Code: 350-401
- Exam Name: Implementing and Operating Cisco Enterprise Network Core Technologies (ENCOR)
- Certification Provider: Cisco
- Latest update: Jan 27,2026
What is a characteristic of a virtual machine?
- A . It must be aware of other virtual machines, in order to allocate physical resources for them
- B . It is deployable without a hypervisor to host it
- C . It must run the same operating system as its host
- D . It relies on hypervisors to allocate computing resources for it
Refer to the exhibit.
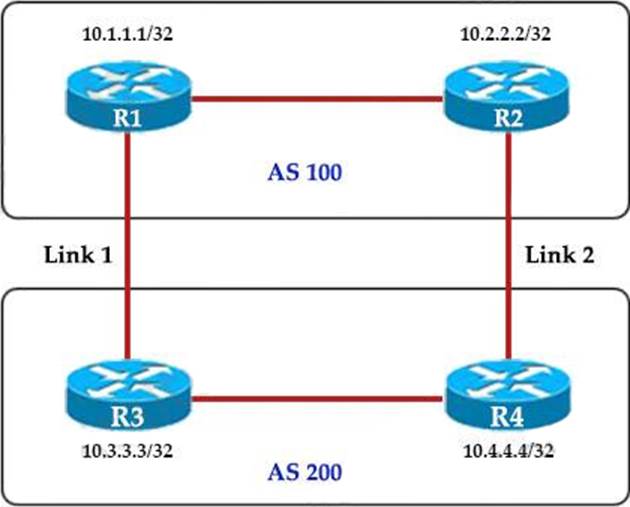
An engineer must ensure that all traffic leaving AS 200 will choose Link 2 as the exit point.
Assuming that all BGP neighbor relationships have been formed and that the attributes have not been changed on any of the routers, which configuration accomplish task?
- A . R4(config-router)bgp default local-preference 200
- B . R3(config-router)neighbor 10.1.1.1 weight 200
- C . R3(config-router)bgp default local-preference 200
- D . R4(config-router)nighbor 10.2.2.2 weight 200
A company has an existing Cisco 5520 HA cluster using SSO. An engineer deploys a new single Cisco Catalyst 9800 WLC to test new features. The engineer successfully configures a mobility tunnel between the 5520 cluster and 9800 WLC. Client connected to the corporate WLAN roam seamlessly between access points on the 5520 and 9800 WLC. After a failure on the primary 5520 WLC, all WLAN services remain functional; however, Client roam between the 5520 and 9800 controllers without dropping their connection.
Which feature must be configured to remedy the issue?
- A . mobility MAC on the 5520 cluster
- B . mobility MAC on the 9800 WLC
- C . new mobility on the 5520 cluster
- D . new mobility on the 9800 WLC
Refer to the exhibit.
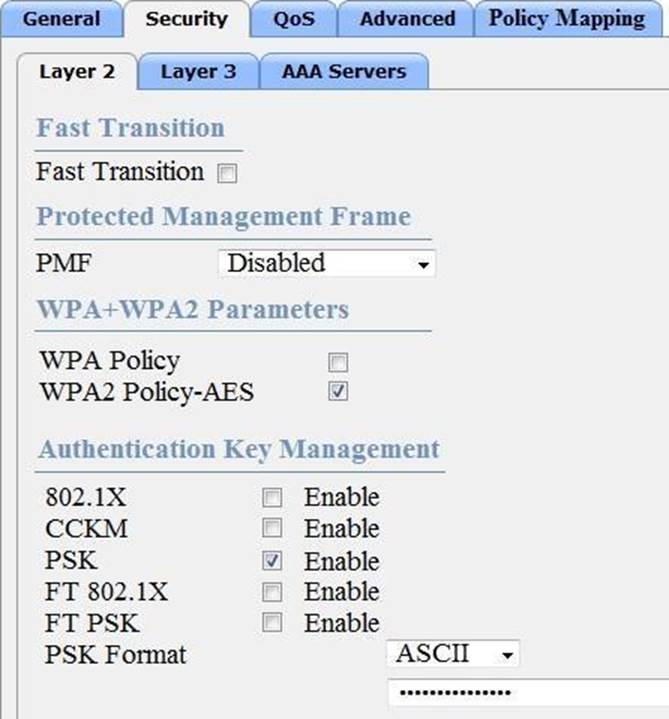
Based on the configuration in this WLAN security setting.
Which method can a client use to authenticate to the network?
- A . text string
- B . username and password
- C . certificate
- D . RADIUS token
Refer to the exhibit.

A network engineer configures OSPF and reviews the router configuration.
Which interface or interface or interface are able to establish OSPF adjacency?
- A . GigabitEthemet0/1 and GigabitEthernet0/1.40
- B . only GigabitEthernet0/1
- C . only GigabttEthernet0/0
- D . Gigabit Ethernet0/0 and GigabitEthemet0/1
Refer to the exhibit.
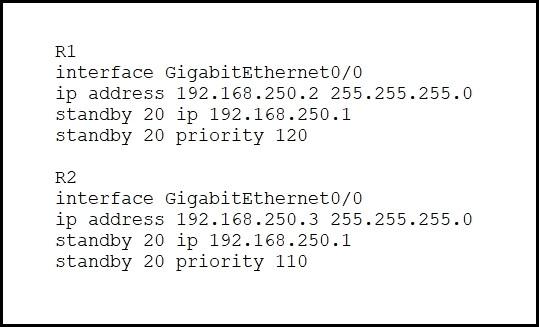
What are two effects of this configuration? (Choose two.)
- A . R1 becomes the active router.
- B . R1 becomes the standby router.
- C . If R2 goes down, R1 becomes active but reverts to standby when R2 comes back online.
- D . If R1 goes down. R2 becomes active and remains the active device when R1 comes back online.
- E . If R1 goes down, R2 becomes active but reverts to standby when R1 comes back online.
Refer to the exhibit.

What does the snippet of code achieve?
- A . It creates a temporary connection to a Cisco Nexus device and retrieves a token to be used for API calls.
- B . It opens a tunnel and encapsulates the login information, if the host key is correct.
- C . It opens an ncclient connection to a Cisco Nexus device and maintains it for the duration of the context.
- D . It creates an SSH connection using the SSH key that is stored, and the password is ignored.
What is one fact about Cisco SD-Access wireless network deployments?
- A . The access point is part of the fabric underlay
- B . The WLC is part of the fabric underlay
- C . The access point is part the fabric overlay
- D . The wireless client is part of the fabric overlay
Refer to the Exhibit.
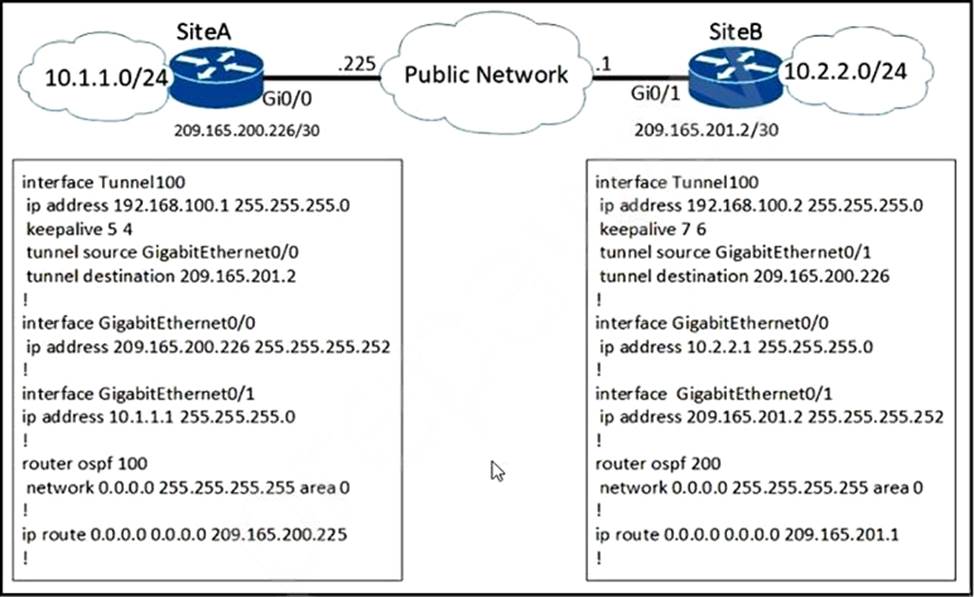
A network engineer configures a new GRE tunnel and enters the show run command.
What does the output verify?
- A . The tunnel will be established and work as expected
- B . The tunnel destination will be known via the tunnel interface
- C . The tunnel keepalive is configured incorrectly because they must match on both sites
- D . The default MTU of the tunnel interface is 1500 byte.
Refer to the Exhibit.
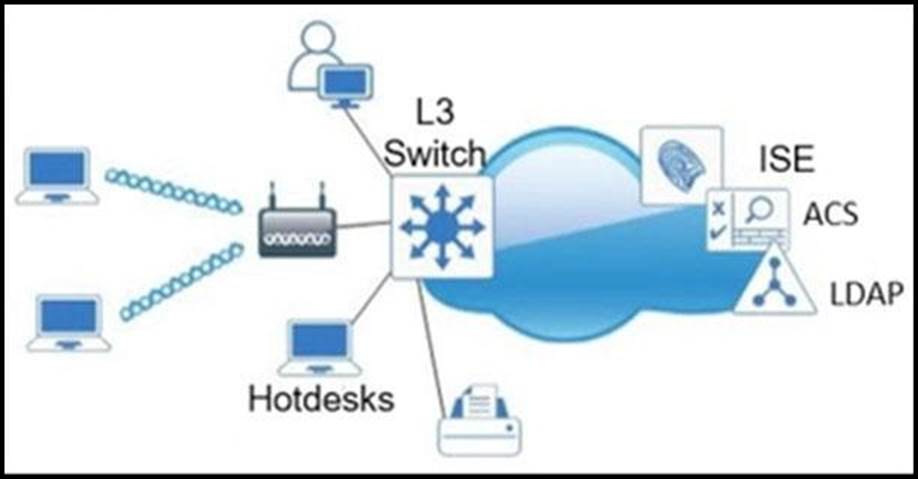
Which single security feature is recommended to provide Network Access Control in the enterprise?
- A . MAB
- B . 802.1X
- C . WebAuth
- D . port security sticky MAC
Latest 350-401 Dumps Valid Version with 404 Q&As
Latest And Valid Q&A | Instant Download | Once Fail, Full Refund


Question 91 has a wrong answer marked s correct. The answer is B.
BPDU filter is the only option to block BPDUs while not going inte err disabled when a BPDU is received.
https://www.exam4training.com/which-command-set-must-be-configured-on-switch1-to-achieve-the-following-results-on-port-fa0-1/
https://www.cisco.com/en/US/docs/switches/metro/me3600x_3800x/trash/swstpopt.html#:~:text=The%20BPDU%20filtering%20feature%20can,bpdufilter%20default%20global%20configuration%20command.