Cisco 350-401 Implementing and Operating Cisco Enterprise Network Core Technologies (ENCOR) Online Training
Cisco 350-401 Online Training
The questions for 350-401 were last updated at Jan 28,2026.
- Exam Code: 350-401
- Exam Name: Implementing and Operating Cisco Enterprise Network Core Technologies (ENCOR)
- Certification Provider: Cisco
- Latest update: Jan 28,2026
Refer to the exhibit.
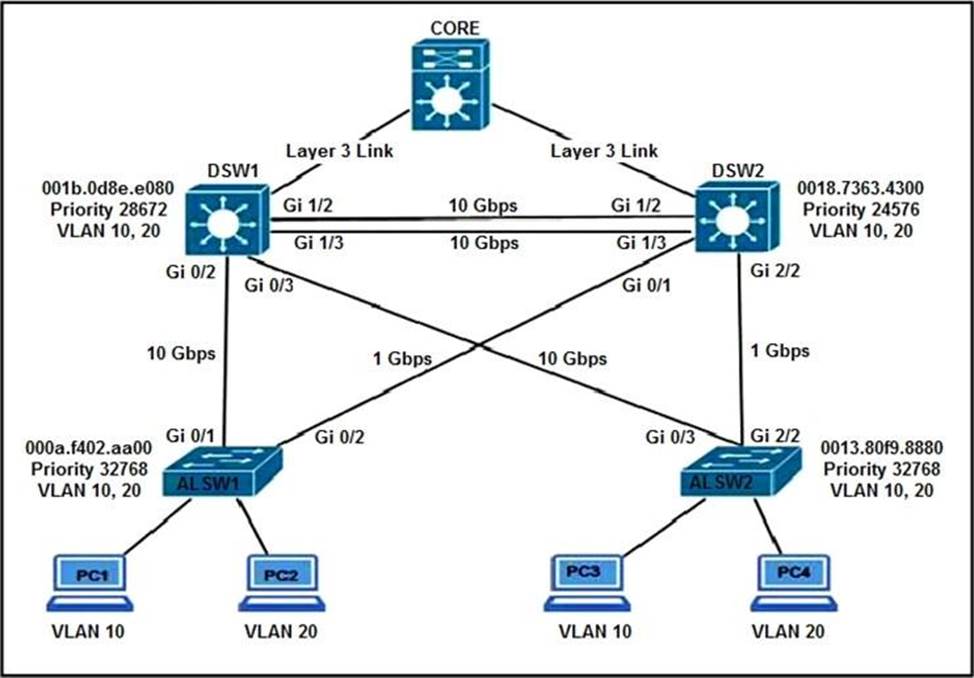
All switches are configured with the default port priority value.
Which two commands ensure that traffic from PC1 is forwarded over Gi1/3 trunk port between DWS1 and DSW2? (Choose two)
- A . DSW2(config-if)#spanning-tree port-priority 16
- B . DSW2(config)#interface gi1/3
- C . DSW1(config-if)#spanning-tree port-priority 0
- D . DSW1(config) #interface gi1/3
- E . DSW2(config-if)#spanning-tree port-priority 128
Which two items are found in YANG data models? (Choose two.)
- A . HTTP return codes
- B . rpc statements
- C . JSON schema
- D . container statements
- E . XML schema
Which element enables communication between guest VMs within a virtualized environment?
- A . hypervisor
- B . vSwitch
- C . virtual router
- D . pNIC
Refer to the exhibit.
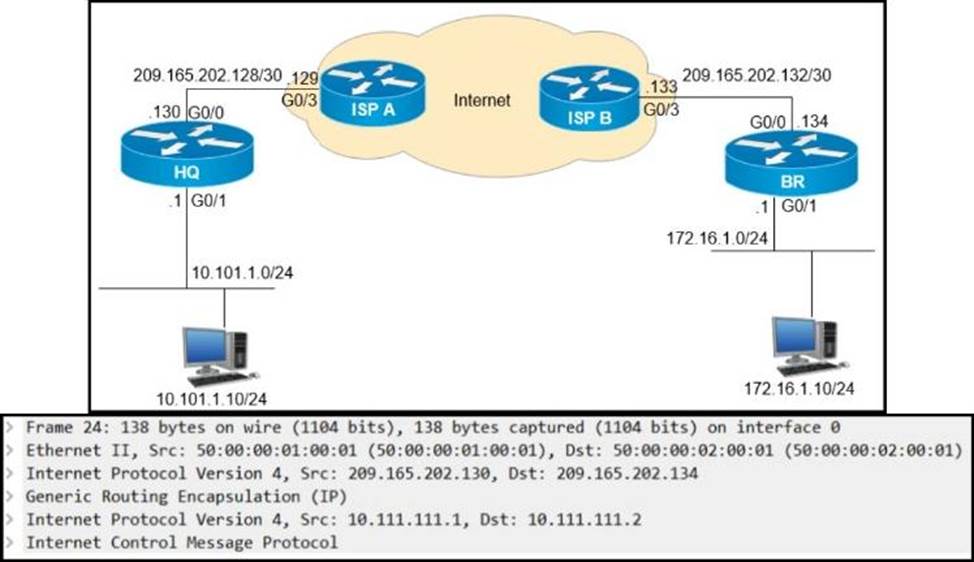
A GRE tunnel has been created between HO and BR routers.
What is the tunnel IP on the HQ router?
- A . 10.111.111.1
- B . 10.111.111.2
- C . 209.165.202.130
- D . 209.165.202.134
Which function does a fabric edge node perform in an SD-Access deployment?
- A . Connects the SD-Access fabric to another fabric or external Layer 3 networks
- B . Connects endpoints to the fabric and forwards their traffic
- C . Provides reachability border nodes in the fabric underlay
- D . Encapsulates end-user data traffic into LISP.
Which access point mode allows a supported AP to function like a WLAN client would, associating and identifying client connectivity issues?
- A . client mode
- B . SE-connect mode
- C . sensor mode
- D . sniffer mode
What is the structure of a JSON web token?
- A . three parts separated by dots: header payload, and signature
- B . header and payload
- C . three parts separated by dots: version header and signature
- D . payload and signature
Which technology does VXLAN use to provide segmentation for Layer 2 and Layer 3 traffic?
- A . bridge domain
- B . VLAN
- C . VRF
- D . VNI
An engineer must protect their company against ransom ware attacks.
Which solution allows the engineer to block the execution stage and prevent file encryption?
- A . Use Cisco AMP deployment with the Malicious Activity Protection engineer enabled.
- B . Use Cisco AMP deployment with the Exploit Prevention engine enabled.
- C . Use Cisco Firepower and block traffic to TOR networks.
- D . Use Cisco Firepower with Intrusion Policy and snort rules blocking SMB exploitation.
Refer to the exhibit.
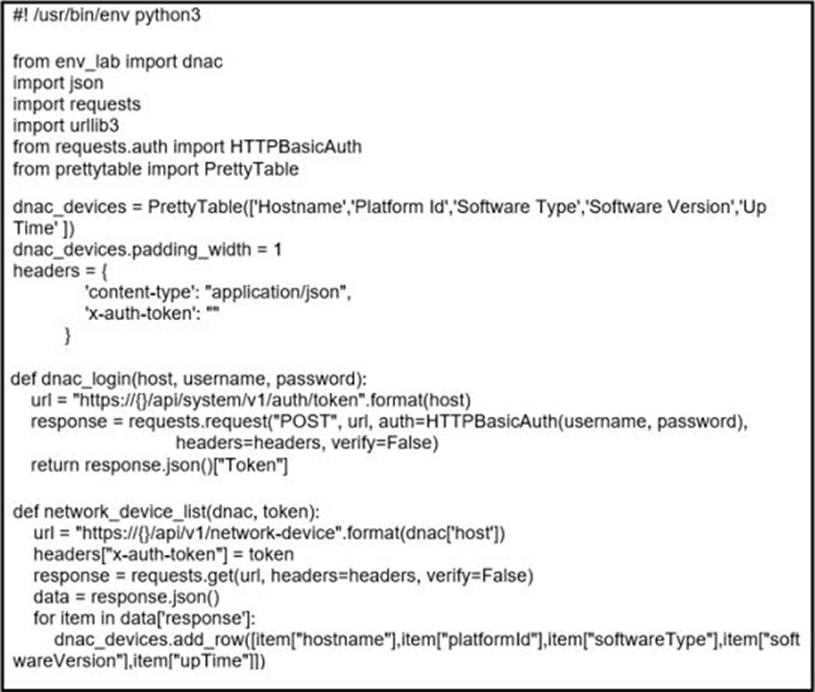
Which code results in the working Python script displaying a list of network devices from the Cisco DNA Center?
A)
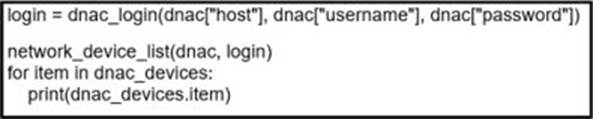
B)

C)
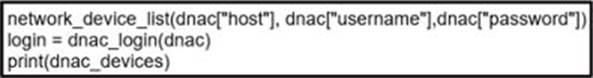
D)
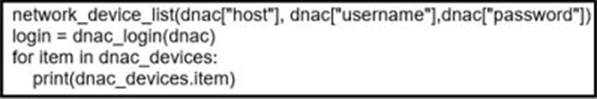
- A . Option A
- B . Option B
- C . Option C
- D . Option D
Latest 350-401 Dumps Valid Version with 404 Q&As
Latest And Valid Q&A | Instant Download | Once Fail, Full Refund


Question 91 has a wrong answer marked s correct. The answer is B.
BPDU filter is the only option to block BPDUs while not going inte err disabled when a BPDU is received.
https://www.exam4training.com/which-command-set-must-be-configured-on-switch1-to-achieve-the-following-results-on-port-fa0-1/
https://www.cisco.com/en/US/docs/switches/metro/me3600x_3800x/trash/swstpopt.html#:~:text=The%20BPDU%20filtering%20feature%20can,bpdufilter%20default%20global%20configuration%20command.