Cisco 350-201 Performing CyberOps Using Core Security Technologies (CBRCOR) Online Training
Cisco 350-201 Online Training
The questions for 350-201 were last updated at Mar 02,2026.
- Exam Code: 350-201
- Exam Name: Performing CyberOps Using Core Security Technologies (CBRCOR)
- Certification Provider: Cisco
- Latest update: Mar 02,2026
What is a principle of Infrastructure as Code?
- A . System maintenance is delegated to software systems
- B . Comprehensive initial designs support robust systems
- C . Scripts and manual configurations work together to ensure repeatable routines
- D . System downtime is grouped and scheduled across the infrastructure
A company’s web server availability was breached by a DDoS attack and was offline for 3 hours because it was not deemed a critical asset in the incident response playbook. Leadership has requested a risk assessment of the asset. An analyst conducted the risk assessment using the threat sources, events, and vulnerabilities .
Which additional element is needed to calculate the risk?
- A . assessment scope
- B . event severity and likelihood
- C . incident response playbook
- D . risk model framework
Refer to the exhibit.
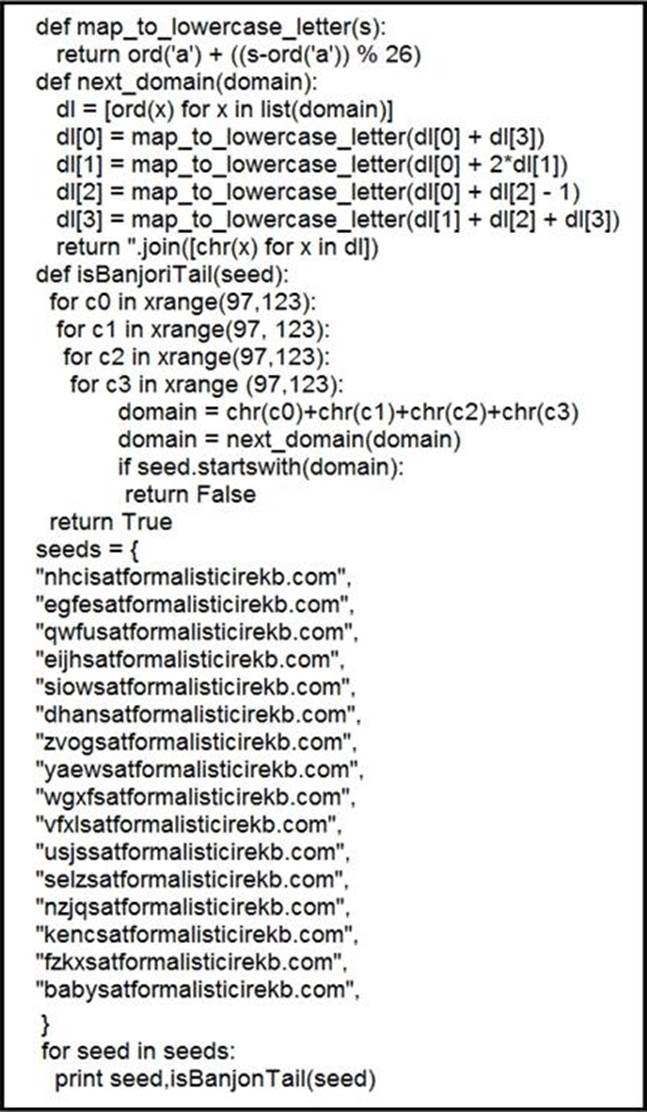
What results from this script?
- A . Seeds for existing domains are checked
- B . A search is conducted for additional seeds
- C . Domains are compared to seed rules
- D . A list of domains as seeds is blocked
After a recent malware incident, the forensic investigator is gathering details to identify the breach and causes. The investigator has isolated the affected workstation .
What is the next step that should be taken in this investigation?
- A . Analyze the applications and services running on the affected workstation.
- B . Compare workstation configuration and asset configuration policy to identify gaps.
- C . Inspect registry entries for recently executed files.
- D . Review audit logs for privilege escalation events.
Which action should be taken when the HTTP response code 301 is received from a web application?
- A . Update the cached header metadata.
- B . Confirm the resource’s location.
- C . Increase the allowed user limit.
- D . Modify the session timeout setting.
How is a SIEM tool used?
- A . To collect security data from authentication failures and cyber attacks and forward it for analysis
- B . To search and compare security data against acceptance standards and generate reports for analysis
- C . To compare security alerts against configured scenarios and trigger system responses
- D . To collect and analyze security data from network devices and servers and produce alerts
A security expert is investigating a breach that resulted in a $32 million loss from customer accounts. Hackers were able to steal API keys and two-factor codes due to a vulnerability that was introduced in a new code a few weeks before the attack .
Which step was missed that would have prevented this breach?
- A . use of the Nmap tool to identify the vulnerability when the new code was deployed
- B . implementation of a firewall and intrusion detection system
- C . implementation of an endpoint protection system
- D . use of SecDevOps to detect the vulnerability during development
A SOC team is informed that a UK-based user will be traveling between three countries over the next 60 days.
Having the names of the 3 destination countries and the user’s working hours, what must the analyst do next to detect an abnormal behavior?
- A . Create a rule triggered by 3 failed VPN connection attempts in an 8-hour period
- B . Create a rule triggered by 1 successful VPN connection from any nondestination country
- C . Create a rule triggered by multiple successful VPN connections from the destination countries
- D . Analyze the logs from all countries related to this user during the traveling period
A SOC analyst is notified by the network monitoring tool that there are unusual types of internal traffic on IP subnet 103.861.2117.0/24. The analyst discovers unexplained encrypted data files on a computer system that belongs on that specific subnet .
What is the cause of the issue?
- A . DDoS attack
- B . phishing attack
- C . virus outbreak
- D . malware outbreak
An API developer is improving an application code to prevent DDoS attacks. The solution needs to accommodate instances of a large number of API requests coming for legitimate purposes from trustworthy services .
Which solution should be implemented?
- A . Restrict the number of requests based on a calculation of daily averages. If the limit is exceeded, temporarily block access from the IP address and return a 402 HTTP error code.
- B . Implement REST API Security Essentials solution to automatically mitigate limit exhaustion. If the limit is exceeded, temporarily block access from the service and return a 409 HTTP error code.
- C . Increase a limit of replies in a given interval for each API. If the limit is exceeded, block access from the API key permanently and return a 450 HTTP error code.
- D . Apply a limit to the number of requests in a given time interval for each API. If the rate is exceeded, block access from the API key temporarily and return a 429 HTTP error code.
Latest 350-201 Dumps Valid Version with 139 Q&As
Latest And Valid Q&A | Instant Download | Once Fail, Full Refund

