Cisco 300-720 Securing Email with Cisco Email Security Appliance (SESA) Online Training
Cisco 300-720 Online Training
The questions for 300-720 were last updated at Dec 12,2025.
- Exam Code: 300-720
- Exam Name: Securing Email with Cisco Email Security Appliance (SESA)
- Certification Provider: Cisco
- Latest update: Dec 12,2025
Email encryption is configured on a Cisco ESA that uses CRES.
Which action is taken on a message when CRES is unavailable?
- A . It is requeued.
- B . It is sent in clear text.
- C . It is dropped and an error message is sent to the sender.
- D . It is encrypted by a Cisco encryption appliance.
Which two features of Cisco Email Security are added to a Sender Group to protect an organization against email threats? (Choose two.)
- A . NetFlow
- B . geolocation-based filtering
- C . heuristic-based filtering
- D . senderbase reputation filtering
- E . content disarm and reconstruction
Which two steps configure Forged Email Detection? (Choose two.)
- A . Configure a content dictionary with executive email addresses.
- B . Configure a filter to use the Forged Email Detection rule and dictionary.
- C . Configure a filter to check the Header From value against the Forged Email Detection dictionary.
- D . Enable Forged Email Detection on the Security Services page.
- E . Configure a content dictionary with friendly names.
What is the default behavior of any listener for TLS communication?
- A . preferred-verify
- B . off
- C . preferred
- D . required
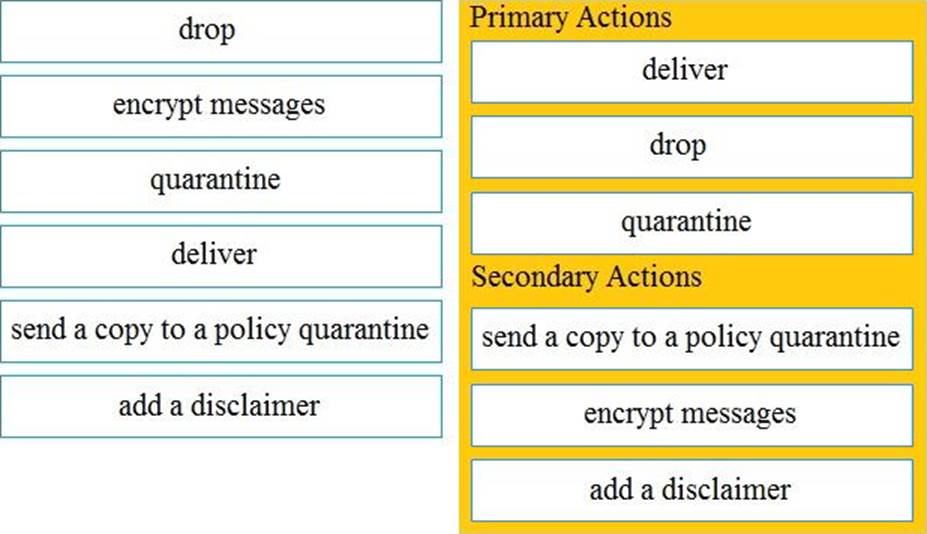
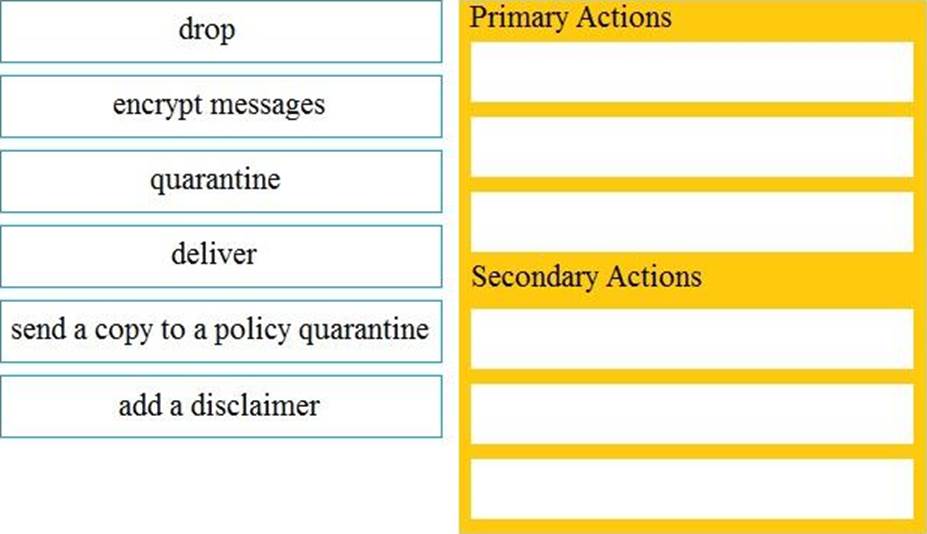
DRAG DROP
Drag and drop the Cisco ESA reactions to a possible DLP from the left onto the correct action types on the right.
Which two actions are configured on the Cisco ESA to query LDAP servers? (Choose two.)
- A . accept
- B . relay
- C . delay
- D . route
- E . reject
Which two statements about configuring message filters within the Cisco ESA are true? (Choose two.)
- A . The filters command executed from the CLI is used to configure the message filters.
- B . Message filters configuration within the web user interface is located within Incoming Content Filters.
- C . The filterconfig command executed from the CLI is used to configure message filters.
- D . Message filters can be configured only from the CLI.
- E . Message filters can be configured only from the web user interface.
What occurs when configuring separate incoming mail policies?
- A . message splintering
- B . message exceptions
- C . message detachment
- D . message aggregation
Which type of query must be configured when setting up the Spam Quarantine while merging notifications?
- A . Spam Quarantine Alias Routing Query
- B . Spam Quarantine Alias Consolidation Query
- C . Spam Quarantine Alias Authentication Query
- D . Spam Quarantine Alias Masquerading Query
Which two factors must be considered when message filter processing is configured? (Choose two.)
- A . message-filter order
- B . lateral processing
- C . structure of the combined packet
- D . mail policies
- E . MIME structure of the message
Latest 300-720 Dumps Valid Version with 93 Q&As
Latest And Valid Q&A | Instant Download | Once Fail, Full Refund