Cisco 300-215 Conducting Forensic Analysis and Incident Response Using Cisco CyberOps Technologies (CBRFIR) Online Training
Cisco 300-215 Online Training
The questions for 300-215 were last updated at Jan 23,2026.
- Exam Code: 300-215
- Exam Name: Conducting Forensic Analysis and Incident Response Using Cisco CyberOps Technologies (CBRFIR)
- Certification Provider: Cisco
- Latest update: Jan 23,2026
An investigator is analyzing an attack in which malicious files were loaded on the network and were undetected. Several of the images received during the attack include repetitive patterns.
Which anti-forensic technique was used?
- A . spoofing
- B . obfuscation
- C . tunneling
- D . steganography
A security team detected an above-average amount of inbound tcp/135 connection attempts from unidentified senders. The security team is responding based on their incident response playbook.
Which two elements are part of the eradication phase for this incident? (Choose two.)
- A . anti-malware software
- B . data and workload isolation
- C . centralized user management
- D . intrusion prevention system
- E . enterprise block listing solution
Which tool conducts memory analysis?
- A . MemDump
- B . Sysinternals Autoruns
- C . Volatility
- D . Memoryze
Refer to the exhibit.
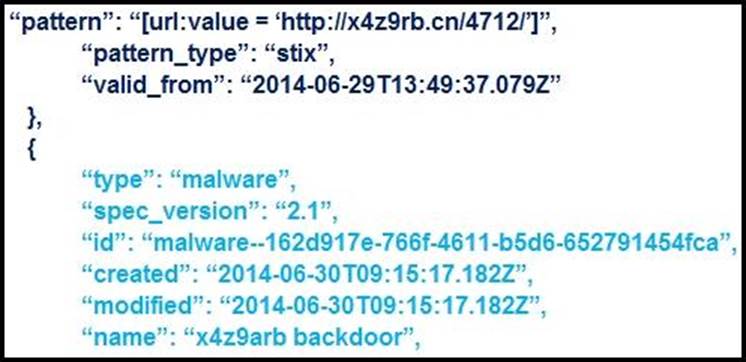
What is the IOC threat and URL in this STIX JSON snippet?
- A . malware; ‘http://x4z9arb.cn/4712/’
- B . malware; x4z9arb backdoor
- C . x4z9arb backdoor; http://x4z9arb.cn/4712/
- D . malware; malware–162d917e-766f-4611-b5d6-652791454fca
- E . stix; ‘http://x4z9arb.cn/4712/’
Refer to the exhibit.
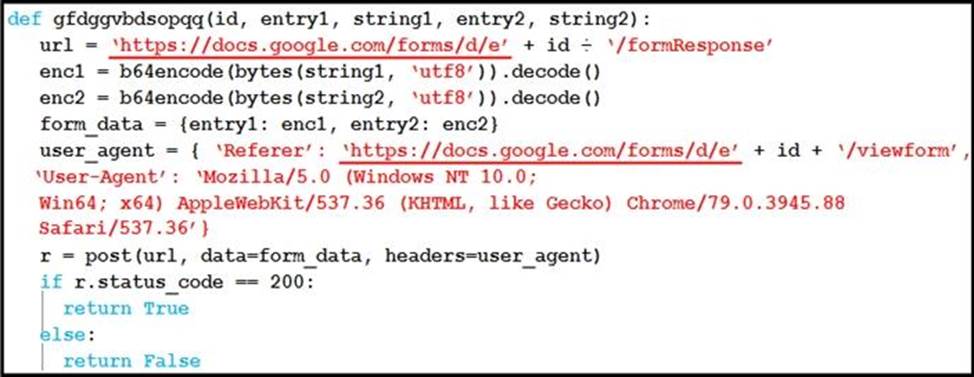
Which type of code is being used?
- A . Shell
- B . VBScript
- C . BASH
- D . Python
Latest 300-215 Dumps Valid Version with 59 Q&As
Latest And Valid Q&A | Instant Download | Once Fail, Full Refund

