Cisco 300-206 Implementing Cisco Edge Network Security Solutions Online Training
Cisco 300-206 Online Training
The questions for 300-206 were last updated at Mar 01,2026.
- Exam Code: 300-206
- Exam Name: Implementing Cisco Edge Network Security Solutions
- Certification Provider: Cisco
- Latest update: Mar 01,2026
An engineer has downloaded the database files for botnet traffic filtering on an ASA.
Where are these database files stored?
- A . flash memory
- B . SSD drive
- C . ROMMON
- D . running memory
Which benefit of using centralized management to manage a Cisco IronPort ESA is true?
- A . It reduces licensing cost
- B . It requires no initial setup
- C . It requires a light client on managed devices
- D . It reduces administration time
A company is concerned with valid time sources and has asked for NTP authentication to be configured. Multiple NTP sources are on the network.
Which configuration is required on the client device to authenticate and synchronize with an NTP source?
- A . trusted key
- B . stratum hash
- C . SSL
- D . certificate preshared key
Which statement about the behavior of the Cisco ASA firewall is true?
- A . The Cisco ASA is not seen as a router hop to connect devices in routed mode
- B . All Cisco ASA interfaces are on different subnets in transparent mode
- C . The Cisco ASA clears the running configuration when changing firewall modes
- D . The Cisco ASA blocks ARP inspection packets in transparent mode
An engineering team is working diligently to achieve the fastest possible throughput on a Cisco ASA
deployment within the data center without sacrificing high availability or flexibility.
Which type of architecture accomplishes this goal?
- A . multiple mode, transparent contexts
- B . single mode, transparent contexts
- C . multiple mode, routed contexts
- D . single mode, routed contexts
Which action can be taken as a preventive measure against VLAN hopping attacks?
- A . Configure an uplink to another switch as access port
- B . Set an unused VLAN as native VLAN on a trunk port
- C . Limit number of MAC addresses on a trunk port
- D . Configure port security on all switch ports
An engineer is asked to configure SNMP Version 3 with authentication and encryption of each SNMP packet.
Which SNMP V3 mode must be configured to meet that requirement?
- A . priv
- B . auth
- C . pub
- D . encr
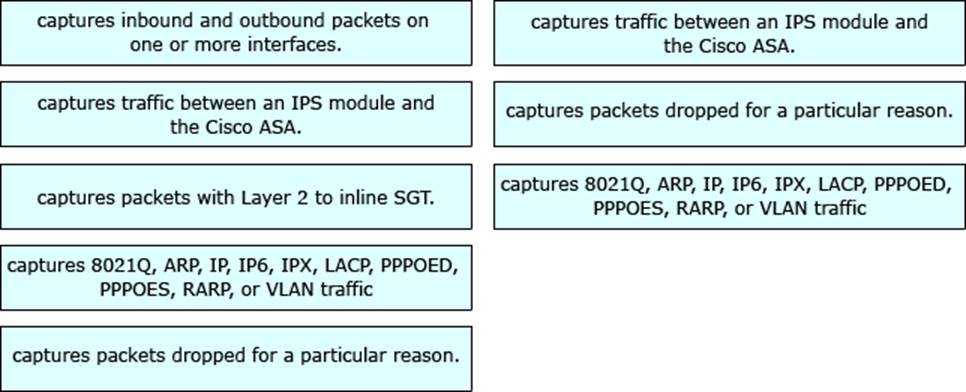
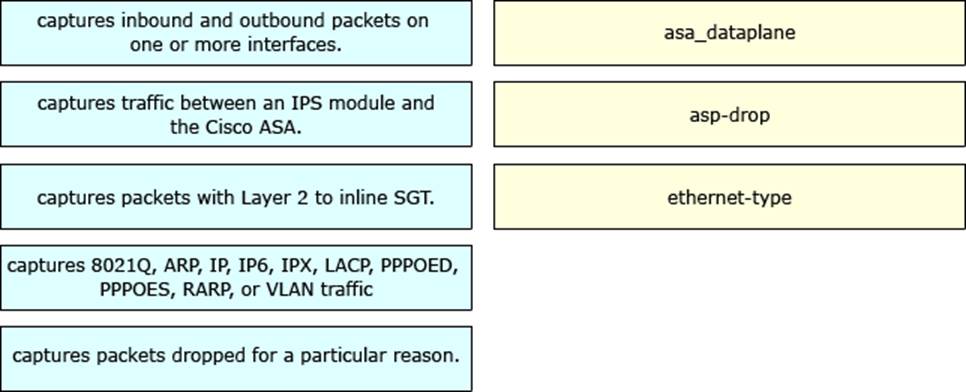
DRAG DROP
Drag and drop the function on the left onto the matching packet capture configuration types on the right. Not all options are used.
An engineer is adding devices to Cisco Prime Infrastructure using Discovery and wants to use Web Services Management Agent for configuring devices.
Which credential setting must be used?
- A . SNMPv2 Credential
- B . SNMPv3 Cred tial
- C . Telnet Credential
- D . SSH Credential
A hacker is sniffing network traffic from a Cisco Catalyst switch on a company network.
Which three pieces of information can be obtained from intercepted Cisco Discovery Protocol traffic? (Choose three.)
- A . routing protocol
- B . encapsulation type
- C . bridge ID
- D . hardware platform
- E . VTP domain
- F . interface MAC address
Latest 300-206 Dumps Valid Version with 376 Q&As
Latest And Valid Q&A | Instant Download | Once Fail, Full Refund