Cisco 200-201 Understanding Cisco Cybersecurity Operations Fundamentals (CBROPS) Online Training
Cisco 200-201 Online Training
The questions for 200-201 were last updated at Jan 31,2026.
- Exam Code: 200-201
- Exam Name: Understanding Cisco Cybersecurity Operations Fundamentals (CBROPS)
- Certification Provider: Cisco
- Latest update: Jan 31,2026
During which phase of the forensic process is data that is related to a specific event labeled and recorded to preserve its integrity?
- A . examination
- B . investigation
- C . collection
- D . reporting
Which step in the incident response process researches an attacking host through logs in a SIEM?
- A . detection and analysis
- B . preparation
- C . eradication
- D . containment
A malicious file has been identified in a sandbox analysis tool.
Which piece of information is needed to search for additional downloads of this file by other hosts?
- A . file header type
- B . file size
- C . file name
- D . file hash value
Refer to the exhibit.
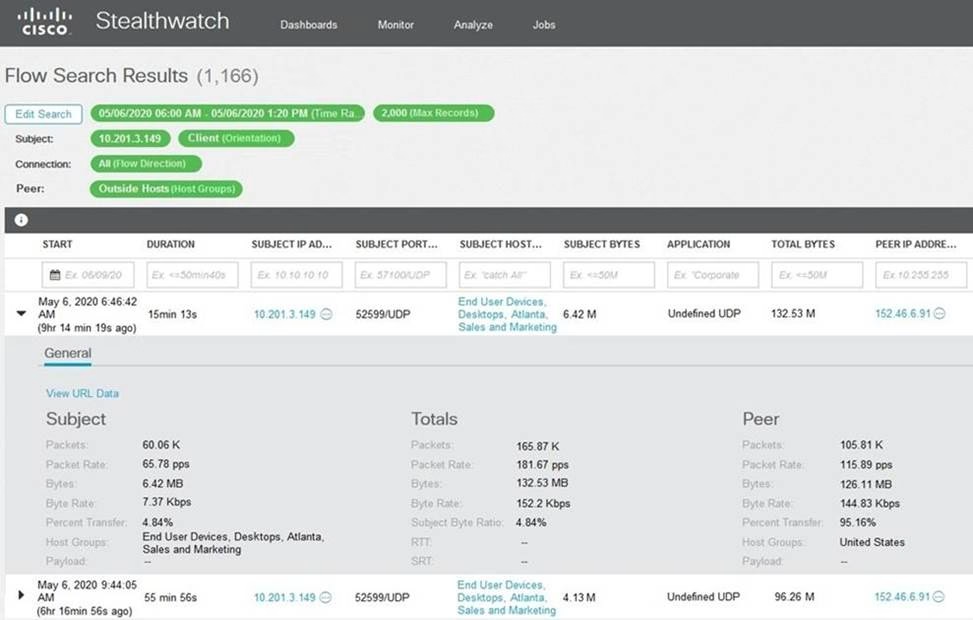
What is the potential threat identified in this Stealthwatch dashboard?
- A . Host 10.201.3.149 is sending data to 152.46.6.91 using TCP/443.
- B . Host 152.46.6.91 is being identified as a watchlist country for data transfer.
- C . Traffic to 152.46.6.149 is being denied by an Advanced Network Control policy.
- D . Host 10.201.3.149 is receiving almost 19 times more data than is being sent to host 152.46.6.91.
Refer to the exhibit.
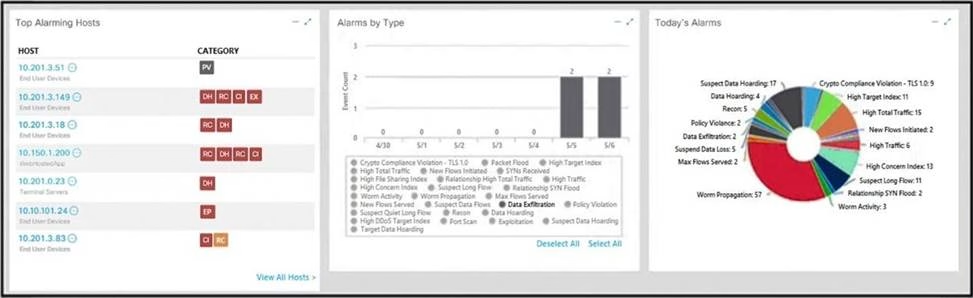
What is the potential threat identified in this Stealthwatch dashboard?
- A . A policy violation is active for host 10.10.101.24.
- B . A host on the network is sending a DDoS attack to another inside host.
- C . There are two active data exfiltration alerts.
- D . A policy violation is active for host 10.201.3.149.
Which security technology allows only a set of pre-approved applications to run on a system?
- A . application-level blacklisting
- B . host-based IPS
- C . application-level whitelisting
- D . antivirus
An investigator is examining a copy of an ISO file that is stored in CDFS format.
What type of evidence is this file?
- A . data from a CD copied using Mac-based system
- B . data from a CD copied using Linux system
- C . data from a DVD copied using Windows system
- D . data from a CD copied using Windows
Which piece of information is needed for attribution in an investigation?
- A . proxy logs showing the source RFC 1918 IP addresses
- B . RDP allowed from the Internet
- C . known threat actor behavior
- D . 802.1x RADIUS authentication pass arid fail logs
What does cyber attribution identify in an investigation?
- A . cause of an attack
- B . exploit of an attack
- C . vulnerabilities exploited
- D . threat actors of an attack
A security engineer has a video of a suspect entering a data center that was captured on the same day that files in the same data center were transferred to a competitor.
Which type of evidence is this?
- A . best evidence
- B . prima facie evidence
- C . indirect evidence
- D . physical evidence
Latest 200-201 Dumps Valid Version with 154 Q&As
Latest And Valid Q&A | Instant Download | Once Fail, Full Refund

