Cisco 200-201 Understanding Cisco Cybersecurity Operations Fundamentals (CBROPS) Online Training
Cisco 200-201 Online Training
The questions for 200-201 were last updated at Jan 31,2026.
- Exam Code: 200-201
- Exam Name: Understanding Cisco Cybersecurity Operations Fundamentals (CBROPS)
- Certification Provider: Cisco
- Latest update: Jan 31,2026
An engineer receives a security alert that traffic with a known TOR exit node has occurred on the network.
What is the impact of this traffic?
- A . ransomware communicating after infection
- B . users downloading copyrighted content
- C . data exfiltration
- D . user circumvention of the firewall
What is an example of social engineering attacks?
- A . receiving an unexpected email from an unknown person with an attachment from someone in the same company
- B . receiving an email from human resources requesting a visit to their secure website to update contact information
- C . sending a verbal request to an administrator who knows how to change an account password
- D . receiving an invitation to the department’s weekly WebEx meeting
Refer to the exhibit.

What is occurring in this network?
- A . ARP cache poisoning
- B . DNS cache poisoning
- C . MAC address table overflow
- D . MAC flooding attack
Which data format is the most efficient to build a baseline of traffic seen over an extended period of time?
- A . syslog messages
- B . full packet capture
- C . NetFlow
- D . firewall event logs
Which action prevents buffer overflow attacks?
- A . variable randomization
- B . using web based applications
- C . input sanitization
- D . using a Linux operating system
Which type of attack occurs when an attacker is successful in eavesdropping on a conversation between two IP phones?
- A . known-plaintext
- B . replay
- C . dictionary
- D . man-in-the-middle
Refer to the exhibit.
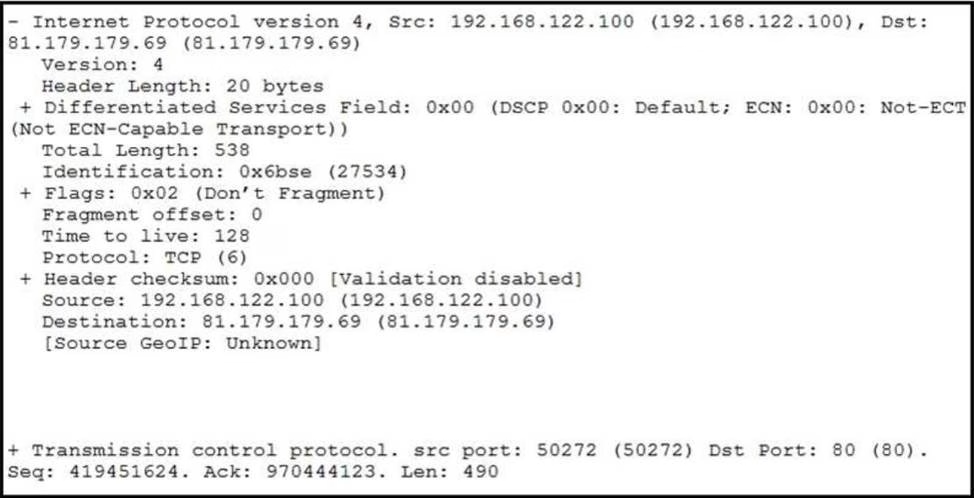
What should be interpreted from this packet capture?
- A . 81.179.179.69 is sending a packet from port 80 to port 50272 of IP address 192.168.122.100 using UDP protocol.
- B . 192.168.122.100 is sending a packet from port 50272 to port 80 of IP address 81.179.179.69 using TCP protocol.
- C . 192.168.122.100 is sending a packet from port 80 to port 50272 of IP address 81.179.179.69 using UDP protocol.
- D . 81.179.179.69 is sending a packet from port 50272 to port 80 of IP address 192.168.122.100 using TCP UDP protocol.
What are the two characteristics of the full packet captures? (Choose two.)
- A . Identifying network loops and collision domains.
- B . Troubleshooting the cause of security and performance issues.
- C . Reassembling fragmented traffic from raw data.
- D . Detecting common hardware faults and identify faulty assets.
- E . Providing a historical record of a network transaction.
Refer to the exhibit.
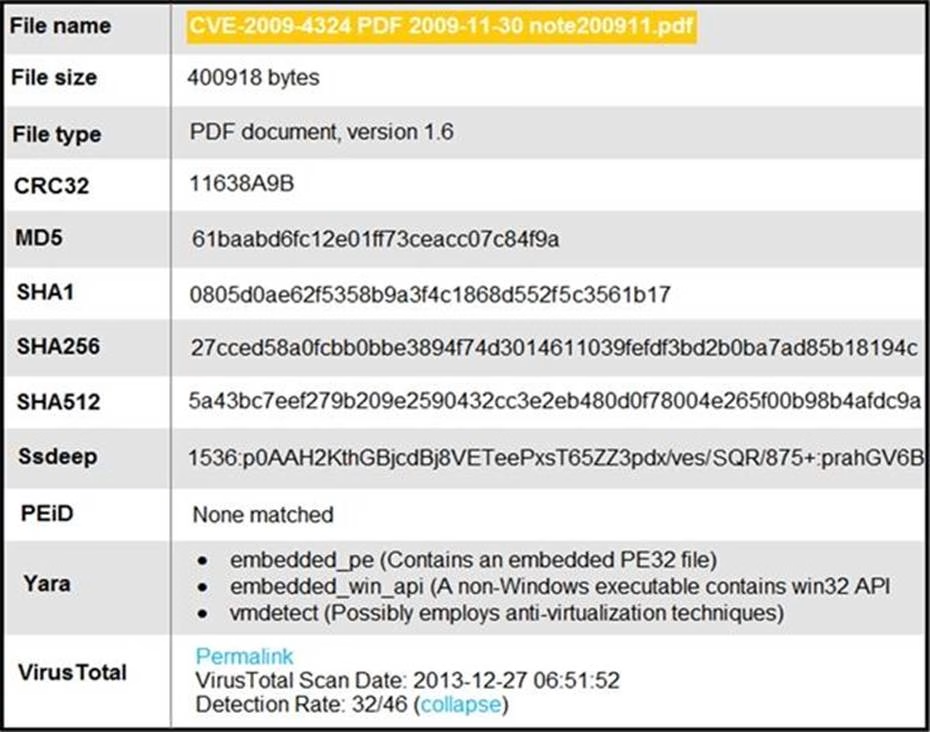
An engineer is analyzing this Cuckoo Sandbox report for a PDF file that has been downloaded from an email.
What is the state of this file?
- A . The file has an embedded executable and was matched by PEiD threat signatures for further analysis.
- B . The file has an embedded non-Windows executable but no suspicious features are identified.
- C . The file has an embedded Windows 32 executable and the Yara field lists suspicious features for further analysis.
- D . The file was matched by PEiD threat signatures but no suspicious features are identified since the signature list is up to date.
DRAG DROP
Drag and drop the technology on the left onto the data type the technology provides on the right.

Latest 200-201 Dumps Valid Version with 154 Q&As
Latest And Valid Q&A | Instant Download | Once Fail, Full Refund


