Check Point 156-915.77 Check Point Certified Security Expert Update Blade Online Training
Check Point 156-915.77 Online Training
The questions for 156-915.77 were last updated at Dec 22,2025.
- Exam Code: 156-915.77
- Exam Name: Check Point Certified Security Expert Update Blade
- Certification Provider: Check Point
- Latest update: Dec 22,2025
What is not available for Express Reports compared to Standard Reports?
- A . Filter
- B . Period
- C . Content
- D . Schedule
Based on the following information, which of the statements below is TRUE?
A DLP Rule Base has the following conditions:
– Data Type = Large file (> 500KB)
– Source = My Organization
– Destination = Free Web Mails
– Protocol = Any
– Action = Ask User
All other rules are set to Detect. User Check is enabled and installed on all client machines.
- A . When a user uploads a 600 KB file to his Yahoo account via Web Mail (via his browser), he will be prompted by User Check
- B . When a user sends an e-mail with a small body and 5 attachments, each of 200 KB to, he will be prompted by User Check.
- C . When a user sends an e-mail with an attachment larger than 500 KB to, he will be prompted by User Check.
- D . When a user sends an e-mail with an attachment larger than 500KB to, he will be prompted by User Check.
Which of the following statements is FALSE about the DLP Software Blade and Active Directory (AD) or LDAP?
- A . When a user authenticates in the DLP Portal to view all his unhandled incidents, the portal authenticates the user using only AD/LDAP.
- B . Check Point User Check client authentication is based on AD.
- C . For SMTP traffic, each recipient e-mail address is translated using AD/LDAP to a user name and group that is checked vs. the destination column of the DLP rule base.
- D . For SMTP traffic, the sender e-mail address is translated using AD/LDAP to a user name and group that is checked vs. the source column of the DLP rule base.
You are running R71 and using the new IPS Software Blade. To maintain the highest level of security, you are doing IPS updates regularly.
What kind of problems can be caused by the automatic updates?
- A . None; updates will not add any new security checks causing problematic behavior on the systems.
- B . None, all new updates will be implemented in Detect only mode to avoid unwanted traffic interruptions. They have to be activated manually later.
- C . None, all the checks will be activated from the beginning, but will only detect attacks and not disturb any non-malicious traffic in the network.
- D . All checks will be activated from the beginning and might cause unwanted traffic outage due to false positives of the new checks and non-RFC compliant self-written applications.
Which of the following deployment scenarios CANNOT be managed by Check Point QoS?
- A . Two lines connected to a single router, and the router is connected directly to the Gateway
- B . Two lines connected to separate routers, and each router is connected to separate interfaces on the Gateway
- C . One LAN line and one DMZ line connected to separate Gateway interfaces
- D . Two lines connected directly to the Gateway through a hub
Given the following protection detailed and the enforcing gateways list, is the Tool many DNS queries with the RD flag set protection enabled on the Gateway R76?
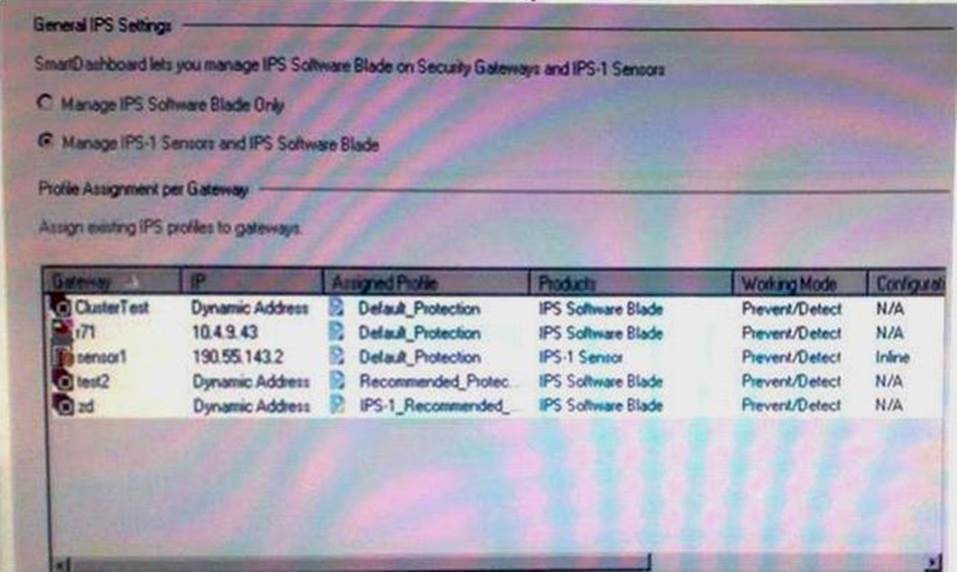
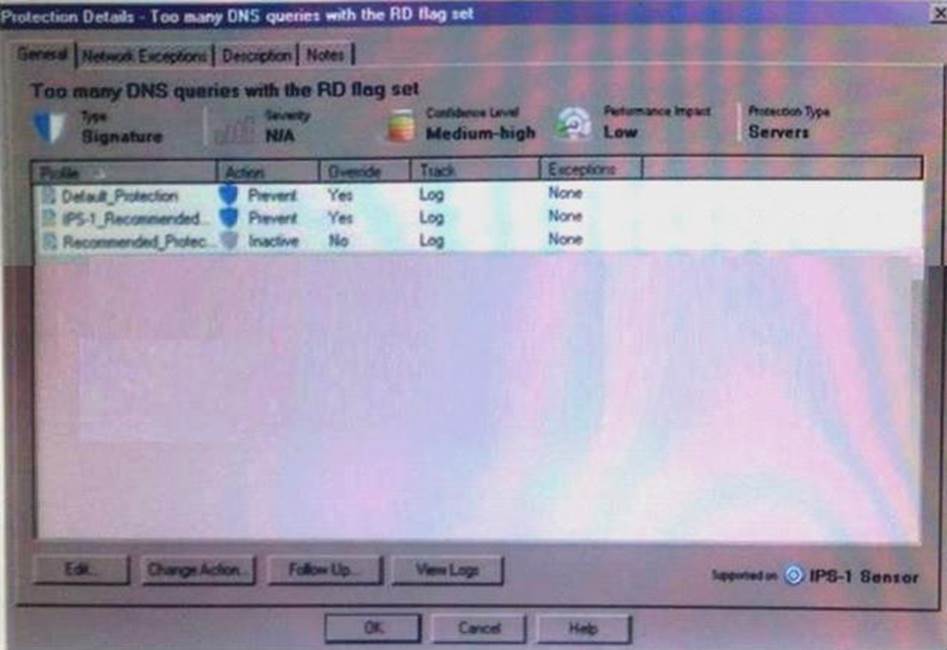
Please choose the answer with the correct justification.
- A . yes because it is set to prevent on the Default_Protrction, which R76 gateway has applied.
- B . No because the protection is only supported on IPS-1 Sensor
- C . No enough information to determine one way or other
- D . No, because the Too many DNS queries with the flag set protection is not a valid protection in R76
Which technology is responsible for assembling packet streams and passing ordered data to the protocol parsers in IPS?
- A . Pattern Matcher
- B . Content Management Infrastructure
- C . Accelerated INSPECT
- D . Packet Streaming Layer
You configure a Check Point QoS Rule Base with two rules: an H.323 rule with a weight of 10, and the Default Rule with a weight of 10. The H.323 rule includes a per-connection guarantee of 384 Kbps. and a per-connection limit of 512 Kbps. The per-connection guarantee is for four connections, and no additional connections are allowed in the Action properties.
If traffic is passing through the QoS Module matches both rules, which of the following statements is TRUE?
- A . Each H.323 connection will receive at least 512 Kbps of bandwidth.
- B . The H.323 rule will consume no more than 2048 Kbps of available bandwidth.
- C . 50% of available bandwidth will be allocated to the Default Rule.
- D . Neither rule will be allocated more than 10% of available bandwidth.
Which of the following is the default port for Management Portal?
- A . 4434
- B . 443
- C . 444
- D . 4433
How is Smart Workflow enabled?
- A . In Smart View Monitor, click on Smart Workflow / Enable Smart Workflow. The Enabling Smart Workflow wizard launches and prompts for Smart Workflow Operation Mode. Once a mode is selected, the wizard finishes.
- B . In Smart View Tracker, click on Smart Workflow / Enable Smart Workflow. The Enabling Smart Workflow wizard launches and prompts for Smart Workflow Operation Mode Once a mode is selected, the wizard finishes.
- C . In Smart Dashboard, click on Smart Workflow / Enable Smart Workflow The Enabling Smart Workflow wizard launches and prompts for Smart Workflow Operation Mode. Once a mode is selected, the wizard finishes.
- D . In Smart Event, click on Smart Workflow/ Enable Smart Workflow. The Enabling Smart Workflow wizard launches and prompts for Smart Workflow Operation Mode. Once a mode is selected, the wizard finishes.
Latest 156-915.77 Dumps Valid Version with 846 Q&As
Latest And Valid Q&A | Instant Download | Once Fail, Full Refund

