Check Point 156-915.77 Check Point Certified Security Expert Update Blade Online Training
Check Point 156-915.77 Online Training
The questions for 156-915.77 were last updated at Dec 21,2025.
- Exam Code: 156-915.77
- Exam Name: Check Point Certified Security Expert Update Blade
- Certification Provider: Check Point
- Latest update: Dec 21,2025
What is used to validate a digital certificate?
- A . S/MIME
- B . CRL
- C . IPsec
- D . PKCS
Which statement defines Public Key Infrastructure? Security is provided:
- A . by Certificate Authorities, digital certificates, and two-way symmetric-key encryption.
- B . by Certificate Authorities, digital certificates, and public key encryption.
- C . via both private and public keys, without the use of digital Certificates.
- D . by authentication.
Match the VPN-related terms with their definitions:
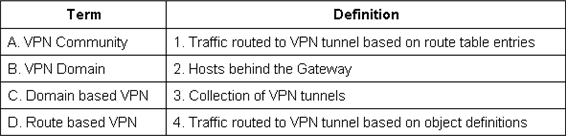
- A . A-3, B-2, C-1, D-4
- B . A-3, B-4, C-1, D-2
- C . A-3, B-2, C-4, D-1
- D . A-2, B-3, C-4, D-1
You want to establish a VPN, using certificates. Your VPN will exchange certificates with an external partner.
Which of the following activities should you do first?
- A . Manually import your partner’s Access Control List.
- B . Manually import your partner’s Certificate Revocation List.
- C . Exchange exported CA keys and use them to create a new server object to represent your partner’s Certificate Authority (CA).
- D . Create a new logical-server object to represent your partner’s CA.
You want VPN traffic to match packets from internal interfaces. You also want the traffic to exit the Security Gateway bound for all site-to-site VPN Communities, including Remote Access Communities.
How should you configure the VPN match rule?
- A . Communities > Communities
- B . internal_clear > All_GwToGw
- C . internal_clear > All_communities
- D . Internal_clear > External_Clear
Which of the following statements is FALSE regarding OSPF configuration on Secure Platform Pro?
- A . router ospf 1 creates the Router ID for the Security Gateway and should be the same ID for all Gateways.
- B . router ospf 1 creates the Router ID for the Security Gateway and should be different for all Gateways.
- C . router ospf 1 creates an OSPF routing instance and this process ID should be different for each Security Gateway.
- D . router ospf 1 creates an OSPF routing instance and this process ID should be the same on all Gateways.
If you need strong protection for the encryption of user data, what option would be the BEST choice?
- A . When you need strong encryption, IPSec is not the best choice. SSL VPN’s are a better choice.
- B . Use Daffier-Hellman for key construction and pre-shared keys for Quick Mode. Choose SHA in Quick Mode and encrypt with AES. Use AH protocol. Switch to Aggressive Mode.
- C . Disable Differ-Hellman by using stronger certificate based key-derivation. Use AES-256 bit on all encrypted channels and add PFS to Quick Mode. Use double encryption by implementing AH and ESP as protocols.
- D . Use certificates for Phase 1, SHA for all hashes, AES for all encryption and PFS, and use ESP protocol.
Review the following list of actions that Security Gateway R76 can take when it controls packets. The Policy Package has been configured for Simplified Mode VPN. Select the response below that includes the available actions:
- A . Accept, Drop, Encrypt, Session Auth
- B . Accept, Drop, Reject, Client Auth
- C . Accept, Hold, Reject, Proxy
- D . Accept, Reject, Encrypt, Drop
Your organization maintains several IKE VPN’s. Executives in your organization want to know which mechanism Security Gateway R76 uses to guarantee the authenticity and integrity of messages.
Which technology should you explain to the executives?
- A . Digital signatures
- B . Certificate Revocation Lists
- C . Key-exchange protocols
- D . Application Intelligence
There are times when you want to use Link Selection to manage high-traffic VPN connections.
With Link Selection you can:
- A . Probe links for availability.
- B . Use links based on Day/Time.
- C . Assign links to specific VPN communities.
- D . Use links based on authentication method.
Latest 156-915.77 Dumps Valid Version with 846 Q&As
Latest And Valid Q&A | Instant Download | Once Fail, Full Refund

