Which of the following steps should the security analyst take FIRST?
A security analyst observes the following while looking through network traffic in a company’s cloud log:
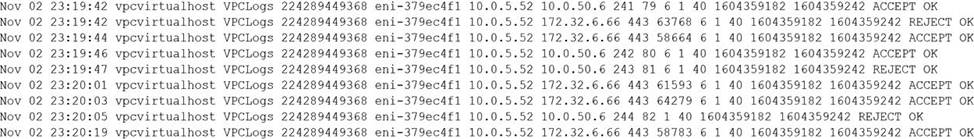
Which of the following steps should the security analyst take FIRST?
A . Quarantine 10.0.5.52 and run a malware scan against the host.
B . Access 10.0.5.52 via EDR and identify processes that have network connections.
C . Isolate 10.0.50.6 via security groups.
D . Investigate web logs on 10.0.50.6 to determine if this is normal traffic.
Answer: D
Latest CAS-004 Dumps Valid Version with 128 Q&As
Latest And Valid Q&A | Instant Download | Once Fail, Full Refund
Subscribe
Login
0 Comments
Inline Feedbacks
View all comments

