- All Exams Instant Download
Which of the following should be the administrator’s NEXT step to detect if there is a rogue system without impacting availability?
While reviewing the wireless router, the systems administrator of a small business determines someone is spoofing the MAC address of an authorized device.
Given the table below:
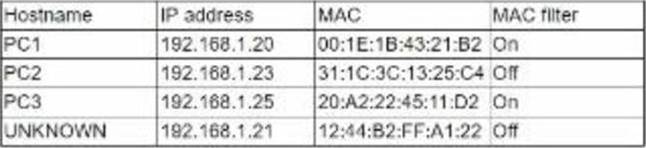
Which of the following should be the administrator’s NEXT step to detect if there is a rogue system without impacting availability?
A . Conduct a ping sweep.
B . Physically check each system,
C . Deny Internet access to the "UNKNOWN" hostname.
D . Apply MAC filtering,
Answer: D
Latest SY0-601 Dumps Valid Version with 396 Q&As
Latest And Valid Q&A | Instant Download | Once Fail, Full Refund
Subscribe
Login
0 Comments
Inline Feedbacks
View all comments

