- All Exams Instant Download
Which of the following is the BEST step for the analyst to lake next in this situation?
While investigating reports or issues with a web server, a security analyst attempts to log in remotely and recedes the following message:
![]()
The analyst accesses the server console, and the following console messages are displayed:
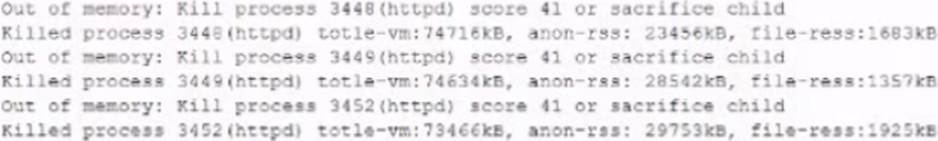
The analyst is also unable to log in on the console.
While reviewing network captures for the server, the analyst sees many packets with the following signature:
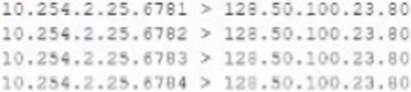
Which of the following is the BEST step for the analyst to lake next in this situation?
A . Load the network captures into a protocol analyzer to further investigate the communication with 128.30.100.23, as this may be a botnet command server
B. After ensuring network captures from the server are saved isolate the server from the network take a memory snapshot, reboot and log in to do further analysis.
C. Corporate data is being exfilltrated from the server Reboot the server and log in to see if it contains any sensitive data.
D. Cryptomining malware is running on the server and utilizing an CPU and memory. Reboot the server and disable any cron Jobs or startup scripts that start the mining software.
Answer: D
Explanation:
Cryptomining malware, or cryptojacking, is a type of malware that hides on a device and uses its computing resources to mine for valuable online currencies like Bitcoin. Cryptomining malware can cause performance issues, increased energy consumption, overheating, or hardware damage1
The analyst encountered cryptomining malware on the web server, as indicated by the following signs:
✑ The analyst was unable to log in remotely or on the console, as the malware blocked access to prevent detection or removal.
✑ The console messages showed that the server was running out of memory and CPU resources, as the malware consumed all available resources for mining.
✑ The network captures showed many packets with a signature of “Stratum”, which is a protocol used for communication between miners and mining pools2
The best step for the analyst to take next is to reboot the server and disable any cron jobs or startup scripts that start the mining software. This can help stop the mining activity and restore access to the server. The analyst should also scan the server for any other traces of malware and remove them.
Reference: 1 Cryptojacking C What is it, and how does it work? | Malwarebytes 2 Stratum (mining protocol) – Bitcoin Wiki
Latest CS0-002 Dumps Valid Version with 220 Q&As
Latest And Valid Q&A | Instant Download | Once Fail, Full Refund
Subscribe
Login
0 Comments
Inline Feedbacks
View all comments

