- All Exams Instant Download
Which of the following is the BEST method to help an attacker gain internal access to the affected machine?
A penetration tester discovered a vulnerability that provides the ability to upload to a path via directory traversal.
Some of the files that were discovered through this vulnerability are:
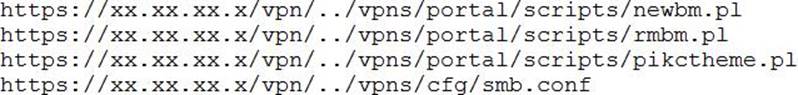
Which of the following is the BEST method to help an attacker gain internal access to the affected machine?
A . Edit the discovered file with one line of code for remote callback
B . Download .pl files and look for usernames and passwords
C . Edit the smb.conf file and upload it to the server
D . Download the smb.conf file and look at configurations
Answer: C
Latest PT0-002 Dumps Valid Version with 110 Q&As
Latest And Valid Q&A | Instant Download | Once Fail, Full Refund
Subscribe
Login
0 Comments
Inline Feedbacks
View all comments

