- All Exams Instant Download
Which of the following describes the method that was used to compromise the laptop?
A security analyst is investigating an incident to determine what an attacker was able to do on a compromised laptop.
The analyst reviews the following SIEM log:
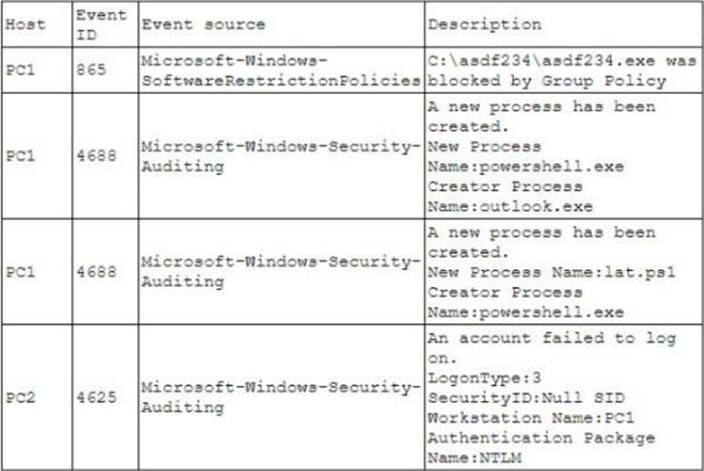
Which of the following describes the method that was used to compromise the laptop?
A . An attacker was able to move laterally from PC1 to PC2 using a pass-the-hash attack
B . An attacker was able to bypass application whitelisting by emailing a spreadsheet attachment with an embedded PowerShell in the file
C . An attacker was able to install malware to the CAasdf234 folder and use it to gam administrator nights and launch Outlook
D . An attacker was able to phish user credentials successfully from an Outlook user profile
Answer: A
Latest SY0-601 Dumps Valid Version with 396 Q&As
Latest And Valid Q&A | Instant Download | Once Fail, Full Refund
Subscribe
Login
0 Comments
Inline Feedbacks
View all comments

