- All Exams Instant Download
Which of the following BEST describes the method used by each tool?
A security analyst is evaluating two vulnerability management tools for possible use in an organization. The analyst set up each of the tools according to the respective vendor’s instructions and generated a report of vulnerabilities that ran against the same target server.
Tool A reported the following:
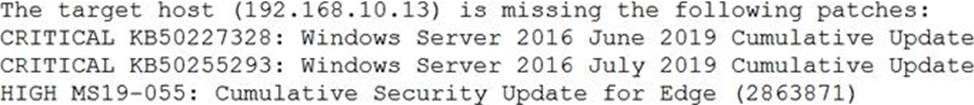
Tool B reported the following:

Which of the following BEST describes the method used by each tool? (Choose two.)
A . Tool A is agent based.
B . Tool A used fuzzing logic to test vulnerabilities.
C . Tool A is unauthenticated.
D . Tool B utilized machine learning technology.
E . Tool B is agent based.
F . Tool B is unauthenticated.
Answer: CE
Latest CS0-002 Dumps Valid Version with 220 Q&As
Latest And Valid Q&A | Instant Download | Once Fail, Full Refund
Subscribe
Login
0 Comments
Inline Feedbacks
View all comments

