- All Exams Instant Download
Which of the following attack strategies should be prioritized from the scan results above?
A penetration tester identifies the following findings during an external vulnerability scan:
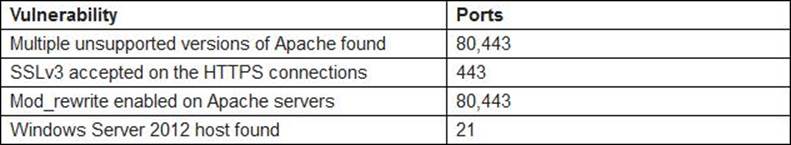
Which of the following attack strategies should be prioritized from the scan results above?
A . Obsolete software may contain exploitable components
B . Weak password management practices may be employed
C . Cryptographically weak protocols may be intercepted
D . Web server configurations may reveal sensitive information
Answer: C
Latest PT0-001 Dumps Valid Version with 248 Q&As
Latest And Valid Q&A | Instant Download | Once Fail, Full Refund
Subscribe
Login
0 Comments
Inline Feedbacks
View all comments

