- All Exams Instant Download
Which of the following actions should the security analyst take?
A security analyst investigate a report from an employee in the human resources (HR) department who is issues with Internal access.
When the security analyst pull the UTM logs for the IP addresses in the HR group, the following activity is shown:
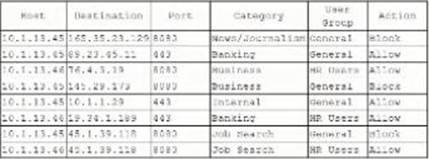
Which of the following actions should the security analyst take?
A . Ensure the HR employee is in the appropriate user group
B . Allow port 8080 on the UTM for all outgoing traffic
C . Disable the proxy settings on the HR employee’s device.
D . Edit the last line Of the ACL On the UTM lo: allow any any.
Answer: A
Latest SY0-501 Dumps Valid Version with 1130 Q&As
Latest And Valid Q&A | Instant Download | Once Fail, Full Refund
Subscribe
Login
0 Comments
Inline Feedbacks
View all comments

