Refer to the exhibit.
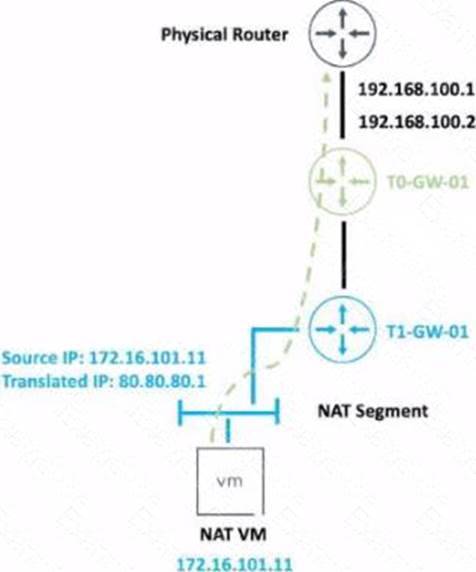
An administrator would like to change the private IP address of the NAT VM I72.l6.101.il to a public address of 80.80.80.1 as the packets leave the NAT-Segment network.
Which type of NAT solution should be implemented to achieve this?
- A . DNAT
- B . SNAT
- C . Reflexive NAT
- D . NAT64
B
Explanation:
SNAT stands for Source Network Address Translation. It is a type of NAT that translates the source IP
address of outgoing packets from a private address to a public address. SNAT is used to allow hosts in a private network to access the internet or other public networks1
In the exhibit, the administrator wants to change the private IP address of the NAT VM 172.16.101.11 to a public address of 80.80.80.1 as the packets leave the NAT-Segment network. This is an example of SNAT, as the source IP address is modified before the packets are sent to an external network. According to the VMware NSX 4.x Professional Exam Guide, SNAT is one of the topics covered in the exam objectives2
To learn more about SNAT and how to configure it in VMware NSX, you can refer to the following resources:
VMware NSX Documentation: NAT 3
VMware NSX 4.x Professional: NAT Configuration 4
VMware NSX 4.x Professional: NAT Troubleshooting 5
https://docs.vmware.com/en/VMware-NSX-T-Data-Center/3.2/administration/GUID-7AD2C384-4303-4D6C-A44A-DEF45AA18A92.html
Which two choices are solutions offered by the VMware NSX portfolio? (Choose two.)
- A . VMware Tanzu Kubernetes Grid
- B . VMware Tanzu Kubernetes Cluster
- C . VMware NSX Advanced Load Balancer
- D . VMware NSX Distributed IDS/IPS
- E . VMware Aria Automation
C, D
Explanation:
VMware NSX is a portfolio of networking and security solutions that enables consistent policy, operations, and automation across multiple cloud environments1
The VMware NSX portfolio includes the following solutions:
– VMware NSX Data Center: A platform for data center network virtualization and security that delivers a complete L2-L7 networking stack and overlay services for any workload1
– VMware NSX Cloud: A service that extends consistent networking and security to public clouds such as AWS and Azure1
– VMware NSX Advanced Load Balancer: A solution that provides load balancing, web application firewall, analytics, and monitoring for applications across any cloud12
– VMware NSX Distributed IDS/IPS: A feature that provides distributed intrusion detection and prevention for workloads across any cloud12
– VMware NSX Intelligence: A service that provides planning, observability, and intelligence for network and micro-segmentation1
– VMware NSX Federation: A capability that enables multi-site networking and security management with consistent policy and operational state synchronization1
– VMware NSX Service Mesh: A service that connects, secures, and monitors microservices across multiple clusters and clouds1
– VMware NSX for Horizon: A solution that delivers secure desktops and applications across any device, location, or network1
– VMware NSX for vSphere: A solution that provides network agility and security for vSphere environments with a built-in console in vCenter1
– VMware NSX-T Data Center: A platform for cloud-native applications that supports containers, Kubernetes, bare metal hosts, and multi-hypervisor environments1
VMware Tanzu Kubernetes Grid and VMware Tanzu Kubernetes Cluster are not part of the VMware NSX portfolio. They are solutions for running Kubernetes clusters on any cloud3
VMware Aria Automation is not a real product name. It is a fictional name that does not exist in the VMware portfolio.
https://blogs.vmware.com/networkvirtualization/2020/01/nsx-hero.html/
When a stateful service is enabled for the first lime on a Tier-0 Gateway, what happens on the NSX Edge node’
- A . SR is instantiated and automatically connected with DR.
- B . DR Is instantiated and automatically connected with SR.
- C . SR and DR Is instantiated but requites manual connection.
- D . SR and DR doesn’t need to be connected to provide any stateful services.
A
Explanation:
The answer is A. SR is instantiated and automatically connected with DR.
SR stands for Service Router and DR stands for Distributed Router. They are components of the NSX Edge node that provide different functions1
The SR is responsible for providing stateful services such as NAT, firewall, load balancing, VPN, and DHCP. The DR is responsible for providing distributed routing and switching between logical segments and the physical network1
When a stateful service is enabled for the first time on a Tier-0 Gateway, the NSX Edge node automatically creates an SR instance and connects it with the existing DR instance. This allows the stateful service to be applied to the traffic that passes through the SR before reaching the DR2
According to the VMware NSX 4.x Professional Exam Guide, understanding the SR and DR components and their functions is one of the exam objectives3
To learn more about the SR and DR components and how they work on the NSX Edge node, you can refer to the following resources:
– VMware NSX Documentation: NSX Edge Components 1
– VMware NSX 4.x Professional: NSX Edge Architecture
– VMware NSX 4.x Professional: NSX Edge Routing
A company Is deploying NSX micro-segmentation in their vSphere environment to secure a simple application composed of web. app, and database tiers.
The naming convention will be:
• WKS-WEB-SRV-XXX
• WKY-APP-SRR-XXX
• WKI-DB-SRR-XXX
What is the optimal way to group them to enforce security policies from NSX?
- A . Use Edge as a firewall between tiers.
- B . Do a service insertion to accomplish the task.
- C . Group all by means of tags membership.
- D . Create an Ethernet based security policy.
C
Explanation:
The answer is C. Group all by means of tags membership.
Tags are metadata that can be applied to physical servers, virtual machines, logical ports, and logical segments in NSX. Tags can be used for dynamic security group membership, which allows for granular and flexible enforcement of security policies based on various criteria1
In the scenario, the company is deploying NSX micro-segmentation to secure a simple application composed of web, app, and database tiers.
The naming convention will be:
– WKS-WEB-SRV-XXX
– WKY-APP-SRR-XXX
– WKI-DB-SRR-XXX
The optimal way to group them to enforce security policies from NSX is to use tags membership. For
example, the company can create three tags: Web, App, and DB, and assign them to the corresponding VMs based on their names. Then, the company can create three security groups: Web-SG, App-SG, and DB-SG, and use the tags as the membership criteria. Finally, the company can create and apply security policies to the security groups based on the desired rules and actions2
Using tags membership has several advantages over the other options:
– It is more scalable and dynamic than using Edge as a firewall between tiers. Edge firewall is a centralized solution that can create bottlenecks and performance issues when handling large amounts of traffic3
– It is more simple and efficient than doing a service insertion to accomplish the task. Service insertion is a feature that allows for integrating third-party services with NSX, such as antivirus or intrusion prevention systems. Service insertion is not necessary for basic micro-segmentation and can introduce additional complexity and overhead.
– It is more flexible and granular than creating an Ethernet based security policy. Ethernet based security policy is a type of policy that uses MAC addresses as the source or destination criteria. Ethernet based security policy is limited by the scope of layer 2 domains and does not support logical constructs such as segments or groups.
To learn more about tags membership and how to use it for micro-segmentation in NSX, you can refer to the following resources:
– VMware NSX Documentation: Security Tag 1
– VMware NSX Micro-segmentation Day 1: Chapter 4 – Security Policy Design 2
– VMware NSX 4.x Professional: Security Groups
– VMware NSX 4.x Professional: Security Policies
When collecting support bundles through NSX Manager, which files should be excluded for potentially containing sensitive information?
- A . Controller Files
- B . Management Files
- C . Core Files
- D . Audit Files
C
Explanation:
According to the VMware NSX Documentation1, core files and audit logs can contain sensitive information and should be excluded from the support bundle unless requested by VMware technical support. Controller files and management files are not mentioned as containing sensitive information.
Reference: 1: Support Bundle Collection Tool – VMware Docs
Core files and Audit logs might contain sensitive information such as passwords or encryption keys. https://docs.vmware.com/en/VMware-NSX/4.1/administration/GUID-73D9AF0D-4000-4EF2-AC66-6572AD1A0B30.html
Which three of the following describe the Border Gateway Routing Protocol (BGP) configuration on a Tier-0 Gateway? (Choose three.)
- A . Can be used as an Exterior Gateway Protocol.
- B . It supports a 4-byte autonomous system number.
- C . The network is divided into areas that are logical groups.
- D . EIGRP Is disabled by default.
- E . BGP is enabled by default.
ABD
Explanation:
A) Can be used as an Exterior Gateway Protocol. This is correct. BGP is a protocol that can be used to exchange routing information between different autonomous systems (AS). An AS is a network or a group of networks under a single administrative control. BGP can be used as an Exterior Gateway Protocol (EGP) to connect an AS to other ASes on the internet or other external networks1
B) It supports a 4-byte autonomous system number. This is correct. BGP supports both 2-byte and 4-byte AS numbers. A 2-byte AS number can range from 1 to 65535, while a 4-byte AS number can range from 65536 to 4294967295. NSX supports both 2-byte and 4-byte AS numbers for BGP configuration on a Tier-0 Gateway2
C) The network is divided into areas that are logical groups. This is incorrect. This statement describes OSPF, not BGP. OSPF is another routing protocol that operates within a single AS and divides the network into areas to reduce routing overhead and improve scalability. BGP does not use the concept of areas, but rather uses attributes, policies, and filters to control the routing decisions and traffic flow3
D) FIGRP Is disabled by default. This is correct. FIGRP stands for Fast Interior Gateway Routing Protocol, which is an enhanced version of IGRP, an obsolete routing protocol developed by Cisco. FIGRP is not supported by NSX and is disabled by default on a Tier-0 Gateway.
E) BGP is enabled by default. This is incorrect. BGP is not enabled by default on a Tier-0 Gateway. To enable BGP, you need to configure the local AS number and the BGP neighbors on the Tier-0 Gateway using the NSX Manager UI or API.
To learn more about BGP configuration on a Tier-0 Gateway in NSX, you can refer to the following resources:
VMware NSX Documentation: Configure BGP 1
VMware NSX 4.x Professional: BGP Configuration
VMware NSX 4.x Professional: BGP Troubleshooting
Which three NSX Edge components are used for North-South Malware Prevention? (Choose three.)
- A . Thin Agent
- B . RAPID
- C . Security Hub
- D . IDS/IPS
- E . Security Analyzer
- F . Reputation Service
BCD
Explanation:
https://docs.vmware.com/en/VMware-NSX/4.1/administration/GUID-69DF70C2-1769-4858-97E7-B757CAED08F0.html#:~:text=On%20the%20north%2Dsouth%20traffic,Guest%20Introspection%20(GI)%20platform.
The main components on the edge node for north-south malware prevention perform the following functions:
• IDS/IPS engine: Extracts files and relays events and data to the security hub North-south malware prevention uses the file extraction features of the IDS/IPS engine that runs on NSX Edge for north-south traffic.
• Security hub: Collects file events, obtains verdicts for known files, sends files for local and cloud-based analysis, and sends information to the security analyzer
• RAPID: Provides local analysis of the file
• ASDS Cache: Caches reputation and verdicts of known files
Which two statements are true about IDS Signatures? (Choose two.)
- A . Users can upload their own IDS signature definitions.
- B . An IDS signature contains data used to identify known exploits and vulnerabilities.
- C . An IDS signature contains data used to identify the creator of known exploits and vulnerabilities.
- D . IDS signatures can be High Risk, Suspicious, Low Risk and Trustworthy.
- E . An IDS signature contains a set of instructions that determine which traffic is analyzed.
BE
Explanation:
According to the Network Bachelor article1, an IDS signature contains data used to identify an attacker’s attempt to exploit a known vulnerability in both the operating system and applications. This implies that statement B is true. According to the VMware NSX Documentation2, IDS/IPS Profiles are used to group signatures, which can then be applied to select applications and traffic. This implies that statement E is true. Statement A is false because users cannot upload their own IDS signature definitions, they have to use the ones provided by VMware or Trustwave3. Statement C is false because an IDS signature does not contain data used to identify the creator of known exploits and vulnerabilities, only the exploits and vulnerabilities themselves. Statement D is false because IDS signatures are classified into one of the following severity categories: Critical, High, Medium, Low, or Informational1.
Reference: 3: Distributed IDS/IPS Settings and Signatures – VMware Docs 2: Distributed IDS/IPS –
VMware Docs 1: NSX-T: Exploring Distributed IDS – Network Bachelor
Which NSX CLI command is used to change the authentication policy for local users?
- A . Set cli-timeout
- B . Get auth-policy minimum-password-length
- C . Set hardening- policy
- D . Set auth-policy
D
Explanation:
According to the VMware NSX Documentation4, the set auth-policy command is used to change the authentication policy settings for local users, such as password length, lockout period, and maximum authentication failures. The other commands are either used to view the authentication policy settings (B), change the CLI session timeout (A), or change the hardening policy settings ©.
Reference: 4: Authentication Policy Settings – VMware Docs https://docs.vmware.com/en/VMware-NSX/4.1/administration/GUID-99BAED85-D754-4589-9050-72A1AB528C10.html
Which statement is true about an alarm in a Suppressed state?
- A . An alarm can be suppressed for a specific duration in seconds.
- B . An alarm can be suppressed for a specific duration in days.
- C . An alarm can be suppressed for a specific duration in minutes.
- D . An alarm can be suppressed for a specific duration in hours.
D
Explanation:
An alarm can be suppressed for a specific duration in hours.
According to the VMware NSX documentation, an alarm can be in one of the following states: Open, Acknowledged, Suppressed, or Resolved12
An alarm in a Suppressed state means that the status reporting for this alarm has been disabled by the user for a user-specified duration12
When a user moves an alarm into a Suppressed state, they are prompted to specify the duration in hours. After the specified duration passes, the alarm state reverts to Open. However, if the system determines the condition has been corrected, the alarm state changes to Resolved13
To learn more about how to manage alarm states in NSX, you can refer to the following resources:
VMware NSX Documentation: Managing Alarm States 1
VMware NSX Documentation: View Alarm Information 2
VMware NSX Intelligence Documentation: Manage NSX Intelligence Alarm States 3 https://docs.vmware.com/en/VMware-NSX-Intelligence/1.2/user-guide/GUID-EBD3C5A8-F9AB-4A22-BA40-92D61850C1E6.html
How is the RouterLink port created between a Tier-1 Gateway and Tler-0 Gateway?
- A . Manually create a Logical Switch and connect to bother Tler-1 and Tier-0 Gateways.
- B . Automatically created when Tler-1 is created.
- C . Manually create a Segment and connect to both Titrr-1 and Tier-0 Gateways.
- D . Automatically created when Tier-t Is connected with Tier-0 from NSX UI.
D
Explanation:
According to the VMware NSX 4.x Professional documents and tutorials, a RouterLink port is a logical port that connects a Tier-1 gateway to a Tier-0 gateway. This port is automatically created when a Tier-1 gateway is associated with a Tier-0 gateway from the NSX UI or API. The RouterLink port enables routing between the two gateways and carries all the routing protocols and traffic. There is no need to manually create a logical switch or segment for this purpose1.
What are three NSX Manager roles? (Choose three.)
- A . master
- B . cloud
- C . zookeepet
- D . manager
- E . policy
- F . controller
DEF
Explanation:
According to the VMware NSX 4.x Professional documents and tutorials, an NSX Manager is a standalone appliance that hosts the API services, the management plane, control plane, and policy management. The NSX Manager has three built-in roles: policy, manager, and controller2. The policy role handles the declarative configuration of the system and translates it into desired state for the manager role. The manager role receives and validates the configuration from the policy role and stores it in a distributed persistent database. The manager role also publishes the configuration to the central control plane. The controller role implements the central control plane that computes the network state based on the configuration and topology information3. The other roles (master, cloud, and zookeeper) are not valid NSX Manager roles.
What are two valid options when configuring the scope of a distributed firewall rule? (Choose two.)
- A . DFW
- B . Tier-1 Gateway
- C . Segment
- D . Segment Port
- E . Group
AE
Explanation:
A group is a logical construct that represents a collection of objects in NSX, such as segments, segment ports, virtual machines, IP addresses, MAC addresses, tags, or security policies. A group can be used to define dynamic membership criteria based on various attributes or filters. A group can also be used as the scope of a distributed firewall rule, which means that the rule will apply to all the traffic that matches the group membership criteria32
Reference:
https://docs.vmware.com/en/VMware-NSX-T-Data-Center/3.2/administration/GUID-41CC06DF-1CD4-4233-B43E-492A9A3AD5F6.html https://docs.vmware.com/en/VMware-NSX-Data-Center-for-vSphere/6.4/com.vmware.nsx.admin.doc/GUID-D44C8923-992F-4695-B9C0-5CC271679D09.html
Which two statements are true for IPSec VPN? (Choose two.)
- A . VPNs can be configured on the command line Interface on the NSX manager.
- B . IPSec VPN services can be configured at Tler-0 and Tler-1 gateways.
- C . IPSec VPNs use the DPDK accelerated performance library.
- D . Dynamic routing Is supported for any IPSec mode In NSX.
BC
Explanation:
According to the VMware NSX 4.x Professional documents and tutorials, IPSec VPN secures traffic flowing between two networks connected over a public network through IPSec gateways called endpoints. NSX Edge supports a policy-based or a route-based IPSec VPN. Beginning with NSX-T Data Center 2.5, IPSec VPN services are supported on both Tier-0 and Tier-1 gateways1. NSX Edge also leverages the DPDK accelerated performance library to optimize the performance of IPSec VPN2. https://docs.vmware.com/en/VMware-NSX/4.0/administration/GUID-7D9F7199-E51B-478B-A8BC-58AD5BBAA0F6.html
Which two logical router components span across all transport nodes? (Choose two.)
- A . SFRVICE_ROUTER_TJER0
- B . TIERO_DISTRI BUTE D_ ROUTER
- C . DISTRIBUTED_R0UTER_TIER1
- D . DISTRIBUTED_ROUTER_TIER0
- E . SERVICE_ROUTER_TIERl
CD
Explanation:
https://docs.vmware.com/en/VMware-Validated-Design/5.0.1/com.vmware.vvd.sddc-nsxt-design.doc/GUID-74141ABD-C9AF-4A92-8338-092CD67EB56E.html
https://www.hydra1303.com/nsx-t-routing-part-i#:~:text=Logical%20routing%20in%20NSX%2DT,using%20static%20routes%20or%20BGP
https://www.delltechnologies.com/asset/en-us/products/converged-infrastructure/technical-support/docu96042.pdf
An NSX administrator wants to create a Tler-0 Gateway to support equal cost multi-path (ECMP) routing.
Which failover detection protocol must be used to meet this requirement?
- A . Bidirectional Forwarding Detection (BFD)
- B . Virtual Router Redundancy Protocol (VRRP)
- C . Beacon Probing (BP)
- D . Host Standby Router Protocol (HSRP)
A
Explanation:
According to the VMware NSX 4.x Professional documents and tutorials, BFD is a failover detection protocol that provides fast and reliable detection of link failures between two routing devices. BFD can be used with ECMP routing to monitor the health of the ECMP paths and trigger a route change in case of a failure12. BFD is supported by both BGP and OSPF routing protocols in NSX-T3. BFD can also be configured with different timers to achieve different detection times3.
HOTSPOT
Refer to the exhibit.
An administrator configured NSX Advanced Load Balancer to load balance the production web server traffic, but the end users are unable to access the production website by using the VIP address.
Which of the following Tier-1 gateway route advertisement settings needs to be enabled to resolve the problem? Mark the correct answer by clicking on the image.
To mark the correct answer by clicking on the image, you can click on the toggle switch next to All LB VIP Routes to turn it on. The switch should change from gray to blue, indicating that the option is enabled. See the image below for reference:
Which TraceFlow traffic type should an NSX administrator use tor validating connectivity between App and DB virtual machines that reside on different segments?
- A . Multicast
- B . Unicast
- C . Anycast
- D . Broadcast
B
Explanation:
Unicast is the traffic type that an NSX administrator should use for validating connectivity between App and DB virtual machines that reside on different segments. According to the VMware documentation1, unicast traffic is the traffic type that is used to send a packet from one source to one destination. Unicast traffic is the most common type of traffic in a network, and it is used for applications such as web browsing, email, file transfer, and so on2. To perform a traceflow with unicast traffic, the NSX administrator needs to specify the source and destination IP addresses, and optionally the protocol and related parameters1. The traceflow will show the path of the packet across the network and any observations or errors along the way3. The other options are incorrect because they are not suitable for validating connectivity between two specific virtual machines. Multicast traffic is the traffic type that is used to send a packet from one source to multiple destinations simultaneously2. Multicast traffic is used for applications such as video streaming, online gaming, and group communication4. To perform a traceflow with multicast traffic, the NSX administrator needs to specify the source IP address and the destination multicast IP address1. Broadcast traffic is the traffic type that is used to send a packet from one source to all devices on the same subnet2. Broadcast traffic is used for applications such as ARP, DHCP, and network discovery. To perform a traceflow with broadcast traffic, the NSX administrator needs to specify the source IP address and the destination MAC address as FF:FF:FF:FF:FF:FF1. Anycast traffic is not a valid option, as it is not supported by NSX Traceflow. Anycast traffic is a traffic type that is used to send a packet from one source to the nearest or best destination among a group of devices that share the same IP address. Anycast traffic is used for applications such as DNS, CDN, and load balancing.
Which command is used to set the NSX Manager’s logging-level to debug mode for troubleshooting?
- A . Set service manager log-level debug
- B . Set service manager logging-level debug
- C . Set service nsx-manager log-level debug
- D . Set service nsx-manager logging-level debug
B
Explanation:
According to the VMware Knowledge Base article 1, the CLI command to set the log level of the NSX Manager to debug mode is set service manager logging-level debug. This command can be used when the NSX UI is inaccessible or when troubleshooting issues with the NSX Manager1. The other commands are incorrect because they either use a wrong syntax or a wrong service name. The NSX Manager service name is manager, not nsx-manager2. The log level parameter is logging-level, not log-level3.
https://kb.vmware.com/s/article/55868
Which two built-in VMware tools will help Identify the cause of packet loss on VLAN Segments? (Choose two.)
- A . Flow Monitoring
- B . Packet Capture
- C . Live Flow
- D . Activity Monitoring
- E . Traceflow
BE
Explanation:
According to the VMware NSX Documentation1, Packet Capture and Traceflow are two built-in VMware tools that can help identify the cause of packet loss on VLAN segments.
Packet Capture allows you to capture packets on a specific interface or segment and analyze them using tools such as Wireshark or tcpdump. Packet Capture can help you diagnose network issues such as misconfigured MTU, incorrect VLAN tags, or firewall drops.
Traceflow allows you to inject synthetic packets into the network and trace their path from source to destination. Traceflow can help you verify connectivity, routing, and firewall rules between virtual machines or segments. Traceflow can also show you where packets are dropped or modified along the way.
What should an NSX administrator check to verify that VMware Identity Manager Integration Is successful?
- A . From VMware Identity Manager the status of the remote access application must be green.
- B . From the NSX UI the status of the VMware Identity Manager Integration must be "Enabled".
- C . From the NSX CLI the status of the VMware Identity Manager Integration must be "Configured".
- D . From the NSX UI the URI in the address bar must have "locaNfatse" part of it.
B
Explanation:
From the NSX UI the status of the VMware Identity Manager Integration must be “Enabled”. According to the VMware NSX Documentation1, after configuring VMware Identity Manager integration, you can validate the functionality by checking the status of the integration in the NSX UI. The status should be “Enabled” if the integration is successful. The other options are either incorrect or not relevant.
What is the VMware recommended way to deploy a virtual NSX Edge Node?
- A . Through the OVF command line tool
- B . Through the vSphere Web Client
- C . Through automated or Interactive mode using an ISO
- D . Through the NSXUI
D
Explanation:
Through the NSX UI. According to the VMware NSX Documentation2, you can deploy NSX Edge nodes as virtual appliances through the NSX UI by clicking Add Edge Node and providing the required information. The other options are either outdated or not applicable for virtual NSX Edge nodes. https://docs.vmware.com/en/VMware-NSX/4.1/installation/GUID-E9A01C68-93E7-4140-B306-19CD6806199F.html
HOTSPOT
Refer to the exhibit.
Which two items must be configured to enable OSPF for the Tler-0 Gateway in the Image? Mark your answers by clicking twice on the image.
To mark your answers by clicking twice on the image, you can double-click on the toggle switch next to OSPF to turn it on. The switch should change from gray to blue, indicating that the option is enabled. Then, you can double-click on the Set button next to Area Definition to add an area definition. A pop-up window should appear where you can specify the area ID and type.
HOTSPOT
Refer to the exhibit.
Which two items must be configured to enable OSPF for the Tler-0 Gateway in the Image? Mark your answers by clicking twice on the image.
To mark your answers by clicking twice on the image, you can double-click on the toggle switch next to OSPF to turn it on. The switch should change from gray to blue, indicating that the option is enabled. Then, you can double-click on the Set button next to Area Definition to add an area definition. A pop-up window should appear where you can specify the area ID and type.
Which three DHCP Services are supported by NSX? (Choose three.)
- A . Gateway DHCP
- B . Port DHCP per VNF
- C . Segment DHCP
- D . VRF DHCP Server
- E . DHCP Relay
ACE
Explanation:
According to the VMware NSX Documentation1, NSX-T Data Center supports the following types of
DHCP configuration on a segment:
Local DHCP server: This option creates a local DHCP server that has an IP address on the segment and provides dynamic IP assignment service only to the VMs that are attached to the segment. Gateway DHCP server: This option is attached to a tier-0 or tier-1 gateway and provides DHCP service to the networks (overlay segments) that are directly connected to the gateway and configured to use a gateway DHCP server.
DHCP Relay: This option relays the DHCP client requests to the external DHCP servers that can be in any subnet, outside the SDDC, or in the physical network. https://docs.vmware.com/en/VMware-NSX/4.0/administration/GUID-486C1281-C6CF-47EC-B2A2-0ECFCC4A68CE.html
Where in the NSX UI would an administrator set the time attribute for a time-based Gateway Firewall rule?
- A . The option to set time-based rule is a clock Icon in the rule.
- B . The option to set time based rule is a field in the rule Itself.
- C . There Is no option in the NSX UI. It must be done via command line interface.
- D . The option to set time-based rule is a clock Icon in the policy.
D
Explanation:
According to the VMware documentation1, the clock icon appears on the firewall policy section that you want to have a time window. By clicking the clock icon, you can create or select a time window that applies to all the rules in that policy section. The other options are incorrect because they either do not exist or are not related to the time-based rule feature. There is no option to set a time-based rule in the rule itself, as it is a policy-level setting. There is also an option to set a time-based rule in the NSX UI, so it does not require using the command line interface. https://docs.vmware.com/en/VMware-NSX/4.1/administration/GUID-8572496E-A60E-48C3-A016-4A081AC80BE7.html
What can the administrator use to identify overlay segments in an NSX environment if troubleshooting is required?
- A . VNI ID
- B . Segment ID
- C . Geneve ID
- D . VIAN ID
A
Explanation:
According to the VMware NSX Documentation1, a segment is mapped to a unique Geneve segment that is distributed across the ESXi hosts in a transport zone. The Geneve segment uses a virtual network identifier (VNI) as an overlay network identifier. The VNI ID can be used to identify overlay segments in an NSX environment if troubleshooting is required.
Which two BGP configuration parameters can be configured in the VRF Lite gateways? (Choose two.)
- A . Graceful Restart
- B . BGP Neighbors
- C . Local AS
- D . Route Distribution
- E . Route Aggregation
BE
Explanation:
Route Aggregation and and D) BGP neighbours are available when configuring BGP in a VRF. "Route distribution" does not exist, what you can do is a "Route Re-Distribution" via BGP. https://docs.vmware.com/en/VMware-NSX/4.1/administration/GUID-4CB5796A-1CED-4F0E-ADE0-72BF7B3F762C.html
An NSX administrator would like to export syslog events that capture messages related to NSX host preparation events.
Which message ID (msgld) should be used in the syslog export configuration command as a filler?
- A . MONISTORING
- B . SYSTEM
- C . GROUPING
- D . FABRIC
D
Explanation:
According to the VMware NSX Documentation2, the FABRIC message ID (msgld) captures messages related to NSX host preparation events, such as installation, upgrade, or uninstallation of NSX components on ESXi hosts.
The syslog export configuration command for NSX host preparation events would look something like this:
set service syslog export FABRIC
The other options are either incorrect or not relevant for NSX host preparation events. MONITORING captures messages related to NSX monitoring features, such as alarms and system events2. SYSTEM captures messages related to NSX system events, such as login, logout, or configuration changes2. GROUPING captures messages related to NSX grouping objects, such as security groups, security tags, or IP sets2.
Which three data collection sources are used by NSX Network Detection and Response to create correlations/Intrusion campaigns? (Choose three.)
- A . Files and anti-malware (lie events from the NSX Edge nodes and the Security Analyzer
- B . East-West anti-malware events from the ESXi hosts
- C . Distributed Firewall flow data from the ESXi hosts
- D . IDS/IPS events from the ESXi hosts and NSX Edge nodes
- E . Suspicious Traffic Detection events from NSX Intelligence
ADE
Explanation:
The correct answers are A. Files and anti-malware (file) events from the NSX Edge nodes and the Security Analyzer, D. IDS/IPS events from the ESXi hosts and NSX Edge nodes, and E. Suspicious Traffic Detection events from NSX Intelligence. According to the VMware NSX Documentation3, these are the three data collection sources that are used by NSX Network Detection and Response to create correlations/intrusion campaigns.
The other options are incorrect or not supported by NSX Network Detection and Response. East-West anti-malware events from the ESXi hosts are not collected by NSX Network Detection and Response3. Distributed Firewall flow data from the ESXi hosts are not used for correlation/intrusion campaigns by NSX Network Detection and Response3.
DRAG DROP
Sort the rule processing steps of the Distributed Firewall. Order responses from left to right.
– Packet arrives at vfilter connection table. If matching entry in the table, process the packet.
– If connection table has no match, compare the packet to the rule table.
– If the packet matches source, destination, service, profile and applied to fields, apply the action defined.
– If the rule table action is allow, create an entry in the connection table and forward the packet.
– If the rule table action is reject or deny, take that action.
This order is based on the description of how the Distributed Firewall works in the web search results1. The first step is to check if there is an existing connection entry for the packet in the vfilter connection table, which is a cache of flow entries for rules with an allow action. If there is a match, the packet is processed according to the connection entry. If there is no match, the packet is compared to the rule table, which contains all the security policy rules. The rules are evaluated from top to bottom until a match is found. The match criteria include source, destination, service, profile and applied to fields. The action defined by the matching rule is applied to the packet. The action can be allow, reject or deny. If the action is allow, a new connection entry is created for the packet and the packet is forwarded to its destination. If the action is reject or deny, the packet is dropped and an ICMP message or a TCP reset message is sent back to the source.
Which VMware GUI tool is used to identify problems in a physical network?
- A . VMware Aria Automation
- B . VMware Aria Orchestrator
- C . VMware Site Recovery Manager
- D . VMware Aria Operations Networks
D
Explanation:
According to the web search results, VMware Aria Operations Networks (formerly vRealize Network Insight) is a network monitoring tool that can help monitor, discover and analyze networks and applications across clouds1. It can also provide enhanced troubleshooting and visibility for physical and virtual networks2.
The other options are either incorrect or not relevant for identifying problems in a physical network. VMware Aria Automation is a cloud automation platform that can help automate the delivery of IT services. VMware Aria Orchestrator is a cloud orchestration tool that can help automate workflows and integrate with other systems. VMware Site Recovery Manager is a disaster recovery solution that can help protect and recover virtual machines from site failures.
DRAG DROP
Refer to the exhibits.
Drag and drop the NSX graphic element icons on the left found in an NSX Intelligence visualization graph to Its correct description on the right.
Explanation:
https://docs.vmware.com/en/VMware-NSX-Intelligence/4.0/user-guide/GUID-DC78552B-2CC4-410D-A6C9-3FE0DCEE545B.html
An NSX administrator has deployed a single NSX Manager node and will be adding two additional nodes to form a 3-node NSX Management Cluster for a production environment. The administrator will deploy these two additional nodes and Cluster VIP using the NSX UI.
What two are the prerequisites for this configuration? (Choose two.)
- A . All nodes must be in separate subnets.
- B . The cluster configuration must be completed using API.
- C . NSX Manager must reside on a Windows Server.
- D . All nodes must be in the same subnet.
- E . A compute manager must be configured.
DE
Explanation:
According to the VMware NSX Documentation, these are the prerequisites for adding nodes to an NSX Management Cluster using the NSX UI:
All nodes must be in the same subnet and have IP connectivity with each other.
A compute manager must be configured and associated with the NSX Manager node.
The NSX Manager node must have a valid license.
The NSX Manager node must have a valid certificate.
Which two choices are use cases for Distributed Intrusion Detection? (Choose two.)
- A . Use agentless antivirus with Guest Introspection.
- B . Quarantine workloads based on vulnerabilities.
- C . Identify risk and reputation of accessed websites.
- D . Gain Insight about micro-segmentation traffic flows.
- E . Identify security vulnerabilities in the workloads.
BE
Explanation:
According to the VMware NSX Documentation, these are two of the use cases for Distributed Intrusion Detection, which is a feature of NSX Network Detection and Response:
Quarantine workloads based on vulnerabilities: You can use Distributed Intrusion Detection to detect vulnerabilities in your workloads and apply quarantine actions to isolate them from the network until they are remediated.
Identify security vulnerabilities in the workloads: You can use Distributed Intrusion Detection to scan your workloads for known vulnerabilities and generate reports that show the severity, impact, and remediation steps for each vulnerability.
When configuring OSPF on a Tler-0 Gateway, which three of the following must match in order to establish a neighbor relationship with an upstream router? (Choose three.)
- A . Naming convention
- B . MTU of the Uplink
- C . Subnet mask
- D . Address of the neighbor
- E . Protocol and Port
- F . Area ID
BCF
Explanation:
according to the VMware NSX Documentation, these are the three parameters that must match in order to establish an OSPF neighbor relationship with an upstream router on a tier-0 gateway: MTU of the Uplink: The maximum transmission unit (MTU) of the uplink interface must match the MTU of the upstream router interface. Otherwise, OSPF packets may be fragmented or dropped, causing neighbor adjacency issues.
Subnet mask: The subnet mask of the uplink interface must match the subnet mask of the upstream router interface. Otherwise, OSPF packets may not reach the correct destination or be rejected by
the upstream router.
Area ID: The area ID of the uplink interface must match the area ID of the upstream router interface. Otherwise, OSPF packets may be ignored or discarded by the upstream router. https://www.computernetworkingnotes.com/ccna-study-guide/ospf-neighborship-condition-and-requirement.html
Which two of the following features are supported for the Standard NSX Application Platform Deployment? (Choose two.)
- A . NSX Intrusion Detection and Prevention
- B . NSX Intelligence
- C . NSX Network Detection and Response
- D . NSX Malware Prevention Metrics
- E . NSX Intrinsic Security
CD
Explanation:
The NSX Application Platform Deployment features are divided into three form factors: Evaluation, Standard, and Advanced. Each form factor determines which NSX features can be activated or installed on the platform1. The Evaluation form factor supports only NSX Intelligence, which provides network visibility and analytics for NSX-T environments2. The Standard form factor supports both NSX Intelligence and NSX Network Detection and Response, which provides network threat detection and response capabilities for NSX-T environments3. The Advanced form factor supports all four features: NSX Intelligence, NSX Network Detection and Response, NSX Malware Prevention, and NSX Metrics1.
https://docs.vmware.com/en/VMware-NSX-T-Data-Center/3.2/nsx-application-platform/GUID-85CD2728-8081-45CE-9A4A-D72F49779D6A.html
What needs to be configured on a Tler-0 Gateway lo make NSX Edge Services available to a VM on a VLAN-backed logical switch?
- A . Downlink Interface
- B . VLAN Uplink
- C . Loopback Router Port
- D . Service Interface
D
Explanation:
The service interface is a special-purpose port to enable services for mainly VLAN-based networks. North-south service insertion is another use case that requires a service interface to connect a partner appliance and redirect north-south traffic for partner services. Service interfaces are supported on both active-standby Tier-0 logical routers and Tier-1 routers. Firewall, NAT, and VPNs are supported on this interface. The service interface is also a downlink
Which troubleshooting step will resolve an error with code 1001 during the configuration of a time-based firewall rule?
- A . Reinstalling the NSX VIBs on the ESXi host.
- B . Restarting the NTPservice on the ESXi host.
- C . Changing the lime zone on the ESXi host.
- D . Reconfiguring the ESXI host with a local NTP server.
B
Explanation:
According to the web search results, error code 1001 is related to a time synchronization issue between the ESXi host and the NSX Manager. This can cause problems when configuring a time-based firewall rule, which requires the ESXi host and the NSX Manager to have the same time zone and NTP server settings. To resolve this error, you need to restart the NTP service on the ESXi host to synchronize the time with the NSX Manager. You can use the following command to restart the NTP service on the ESXi host:
/etc/init.d/ntpd restart
The other options are not valid solutions for this error. Reinstalling the NSX VIBs on the ESXi host will not fix the time synchronization issue. Changing the time zone on the ESXi host may cause more discrepancies with the NSX Manager. Reconfiguring the ESXi host with a local NTP server may not be compatible with the NSX Manager’s NTP server.
NSX improves the security of today’s modern workloads by preventing lateral movement, which feature of NSX can be used to achieve this?
- A . Network Segmentation
- B . Virtual Security Zones
- C . Edge Firewalling
- D . Dynamic Routing
A
Explanation:
According to the web search results, network segmentation is a feature of NSX that improves the security of today’s modern workloads by preventing lateral movement. Lateral movement is a technique used by attackers to move from one compromised system to another within a network, exploiting vulnerabilities or credentials. Network segmentation prevents lateral movement by dividing a network into smaller segments or zones, each with its own security policies and controls. This way, if one segment is compromised, the attacker cannot access other segments or resources.
NSX enables network segmentation by using micro-segmentation, which applies granular firewall rules at the virtual machine level, regardless of the physical network topology.
A customer has a network where BGP has been enabled and the BGP neighbor is configured on the Tier-0 Gateway.
An NSX administrator used the get gateways command to retrieve this Information:
Which two commands must be executed to check BGP neighbor status? (Choose two.)
- A . vrf 1
- B . vrf 4
- C . sa-nexedge-01(tier1_sr> get bgp neighbor
- D . sa-nexedge-01(tier0_sr> get bgp neighbor
- E . sa-nexedge-01(tier1_dr)> get bgp neighbor
- F . vrf 3
DF
Explanation:
BGP will be configured on the T0 SR. Connect to the VRF for the T0 SR and run get bgp neighbor once connected to it. https://docs.vmware.com/en/VMware-Validated-Design/5.1/sddc-deployment-of-vmware-nsx-t-workload-domains-with-multiple-availability-zones/GUID-8BD4228A-75C6-4C60-80B4-538D4297E11A.html
For the BGP configuration on NSX-T, the Tier-0 Service Router (SR) is typically where BGP is configured. To check the BGP neighbor status:
Connect to the VRF for the T0 SR, which is VRF 3 based on the provided output.
Run the command to get BGP neighbor status once connected to it.