A bootstrap USB flash drive has been prepared using a Windows workstation to load the initial configuration of a Palo Alto Networks firewall that was previously being used in a lab. The USB flash drive was formatted using file system FAT32 and the initial configuration is stored in a file named init-cfg txt. The firewall is currently running PAN-OS 10.0 and using a lab config.
The contents of init-cfg txt in the USB flash drive are as follows:
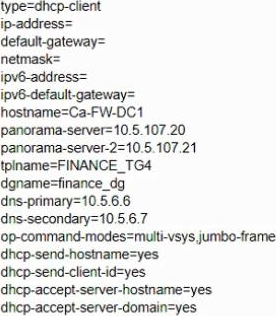
The USB flash drive has been inserted in the firewalls’ USB port, and the firewall has been restarted using command:> request resort system Upon restart, the firewall fails to begin the bootstrapping process. The failure is caused because
- A . Firewall must be in factory default state or have all private data deleted for bootstrapping
- B . The hostname is a required parameter, but it is missing in init-cfg txt
- C . The USB must be formatted using the ext3 file system, FAT32 is not supported
- D . PANOS version must be 91.x at a minimum but the firewall is running 10.0.x
- E . The bootstrap.xml file is a required file but it is missing
A
Explanation:
https://docs.paloaltonetworks.com/pan-os/8-1/pan-os-admin/firewall-administration/bootstrap-the-firewall/bootstrap-a-firewall-using-a-usb-flash-drive.html#id8378007f-d6e5-4f2d-84a4-5d50b0b3ad7d
Where is information about packet buffer protection logged?
- A . Alert entries are in the Alarms log. Entries for dropped traffic, discarded sessions, and blocked IP address are in the Threat log
- B . All entries are in the System log
- C . Alert entries are in the System log. Entries for dropped traffic, discarded sessions and blocked IP addresses are in the Threat log
- D . All entries are in the Alarms log
C
Explanation:
The Palo Alto Networks firewall generates various types of logs, each serving a specific purpose:
The System log records events related to the health and functionality of the firewall itself, including critical alerts. If the firewall detects issues that could potentially impact the network’s security, it creates an entry in the System log.
The Threat log is responsible for tracking potential security risks detected by the firewall, such as dropped traffic, discarded sessions, and blocked IP addresses. These threats can include viruses, spyware, data leakage, and other vulnerabilities that could compromise the network’s security.
To understand packet buffer protection activities, you would primarily look at these two logs. System logs would provide information about system-wide issues and alerts, while the Threat log would provide detailed information about threats that resulted in dropped traffic, discarded sessions, or blocked IP addresses.
An engineer troubleshooting a VPN issue needs to manually initiate a VPN tunnel from the CLI.
Which CLI command can the engineer use?
- A . test vpn flow
- B . test vpn Ike―sa
- C . test vpn tunnel
- D . test vpn gateway
An administrator wants multiple web servers In the DMZ to receive connections initiated from the internet. Traffic destined for 206.15.22.9 port 80/TCP needs to be forwarded to the server at 10.1.1.22.
Based on the image, which NAT rule will forward web-browsing traffic correctly?
A)
B)
C)
D)
- A . Option
- B . Option
- C . Option
- D . Option
B
Explanation:
https://docs.paloaltonetworks.com/pan-os/8-1/pan-os-admin/networking/nat/nat-configuration-examples/destination-nat-exampleone-to-one-mapping.html
A company is using wireless controllers to authenticate users.
Which source should be used for User-ID mappings?
- A . Syslog
- B . XFF headers
- C . server monitoring
- D . client probing
A
Explanation:
https://docs.paloaltonetworks.com/pan-os/10-2/pan-os-admin/user-id/user-id-overview
An engineer wants to configure aggregate interfaces to increase bandwidth and redundancy between the firewall and switch.
Which statement is correct about the configuration of the interfaces assigned to an aggregate interface group?
- A . They can have a different bandwidth.
- B . They can have a different interface type such as Layer 3 or Layer 2.
- C . They can have a different interface type from an aggregate interface group.
- D . They can have different hardware media such as the ability to mix fiber optic and copper.
D
Explanation:
https://docs.paloaltonetworks.com/pan-os/9-1/pan-os-admin/networking/configure-interfaces/configure-an-aggregate-interface-group
The administrator for a small company has recently enabled decryption on their Palo Alto Networks firewall using a self-signed root certificate. They have also created a Forward Trust and Forward Untrust certificate and set them as such
The admin has not yet installed the root certificate onto client systems
What effect would this have on decryption functionality?
- A . Decryption will function and there will be no effect to end users
- B . Decryption will not function because self-signed root certificates are not supported
- C . Decryption will not function until the certificate is installed on client systems
- D . Decryption will function but users will see certificate warnings for each SSL site they visit
D
Explanation:
https://knowledgebase.paloaltonetworks.com/KCSArticleDetail?id=kA10g000000ClEZCA0
An engineer is in the planning stages of deploying User-ID in a diverse directory services environment.
Which server OS platforms can be used for server monitoring with User-ID?
- A . Microsoft Terminal Server, Red Hat Linux, and Microsoft Active Directory
- B . Microsoft Active Directory, Red Hat Linux, and Microsoft Exchange
- C . Microsoft Exchange, Microsoft Active Directory, and Novell eDirectory
- D . Novell eDirectory, Microsoft Terminal Server, and Microsoft Active Directory
A
Explanation:
https://docs.paloaltonetworks.com/compatibility-matrix/user-id-agent/which-servers-can-the-user-id-agent-monitor
A company with already deployed Palo Alto firewalls has purchased their first Panorama server. The security team has already configured all firewalls with the Panorama IP address and added all the firewall serial numbers in Panorama.
What are the next steps to migrate configuration from the firewalls to Panorama?
- A . Use API calls to retrieve the configuration directly from the managed devices
- B . Export Named Configuration Snapshot on each firewall followed by Import Named Configuration Snapshot in Panorama
- C . import Device Configuration to Panorama followed by Export or Push Device Config Bundle
- D . Use the Firewall Migration plugin to retrieve the configuration directly from the managed devices
C
Explanation:
https://knowledgebase.paloaltonetworks.com/KCSArticleDetail?id=kA10g000000CloRCAS
After configuring HA in Active/Passive mode on a pair of firewalls the administrator gets a failed commit with the following details.
What are two explanations for this type of issue? (Choose two)
- A . The peer IP is not included in the permit list on Management Interface Settings
- B . The Backup Peer HA1 IP Address was not configured when the commit was issued
- C . Either management or a data-plane interface is used as HA1-backup
- D . One of the firewalls has gone into the suspended state
B,C
Explanation:
Cause The issue is seen when the HA1-backup is configured with either management (MGT) or an in-band interface. The "Backup Peer HA1 IP Address" is not configured:
https://knowledgebase.paloaltonetworks.com/KCSArticleDetail?id=kA14u0000008UmPCAU&lang=en_US%E2%80%A9
An administrator has two pairs of firewalls within the same subnet. Both pairs of firewalls have been configured to use High Availability mode with Active/Passive. The ARP tables for upstream routes display the same MAC address being shared for some of these firewalls.
What can be configured on one pair of firewalls to modify the MAC addresses so they are no longer in conflict?
- A . Configure a floating IP between the firewall pairs.
- B . Change the Group IDs in the High Availability settings to be different from the other firewall pair on the same subnet.
- C . Change the interface type on the interfaces that have conflicting MAC addresses from L3 to VLAN.
- D . On one pair of firewalls, run the CLI command: set network interface vlan arp.
C
Explanation:
https://knowledgebase.paloaltonetworks.com/KCSArticleDetail?id=kA10g000000Cm1OCA S
change the Group IDs in the High Availability settings to be different from the other firewall pair on the same subnet. This will prevent the MAC addresses from conflicting and allow the firewalls to properly route traffic. You can also configure a floating IP between the firewall pairs if necessary.
A network administrator configured a site-to-site VPN tunnel where the peer device will act as initiator None of the peer addresses are known
What can the administrator configure to establish the VPN connection?
- A . Set up certificate authentication.
- B . Use the Dynamic IP address type.
- C . Enable Passive Mode
- D . Configure the peer address as an FQDN.
An administrator needs to optimize traffic to prefer business-critical applications over non-critical applications QoS natively integrates with which feature to provide service quality?
- A . certificate revocation
- B . Content-ID
- C . App-ID8 9 B
- D . port inspection
C
Explanation:
QoS natively integrates with App-ID, which is a feature that identifies applications based on their unique characteristics and behaviors, regardless of port, protocol, encryption, or evasive tactics. By using App-ID, QoS can prioritize or limit traffic based on the application name, category, subcategory, technology, or risk level. Certificate revocation is a process of invalidating digital certificates that are no longer trusted or secure. Content-ID is a feature that scans content and data within allowed applications for threats and sensitive data. Port inspection is a method of identifying applications based on the TCP or UDP port numbers they use, which is not reliable or granular enough for QoS purposes.
References:
✑ https://docs.paloaltonetworks.com/pan-os/9-1/pan-os-admin/quality-of-service/configure-qos
✑ https://docs.paloaltonetworks.com/pan-os/9-1/pan-os-admin/app-id
Which data flow describes redistribution of user mappings?
- A . User-ID agent to firewall
- B . firewall to firewall
- C . Domain Controller to User-ID agent
- D . User-ID agent to Panorama
B
Explanation:
https://www.paloaltonetworks.com/documentation/71/pan-os/pan-os/user-id/configure-firewalls-to-redistribute-user-mapping-information
https://docs.paloaltonetworks.com/pan-os/8-1/pan-os-admin/user-id/deploy-user-id-in-a-large-scale-network/redistribute-user-mappings-and-authentication-timestamps/firewall-deployment-for-user-id-redistribution.html#ide3661b46-4722-4936-bb9b-181679306809
A firewall administrator wants to avoid overflowing the company syslog server with traffic logs.
What should the administrator do to prevent the forwarding of DNS traffic logs to syslog?
- A . Disable logging on security rules allowing DNS.
- B . Go to the Log Forwarding profile used to forward traffic logs to syslog. Then, under traffic logs match list, create a new filter with application not equal to DNS.
- C . Create a security rule to deny DNS traffic with the syslog server in the destination
- D . Go to the Log Forwarding profile used to forward traffic logs to syslog. Then, under traffic logs match list, create a new filter with application equal to DNS.
B
Explanation:
A log forwarding profile defines which logs are forwarded to which destinations, such as syslog servers. By creating a filter with application not equal to DNS, the log forwarding profile will exclude DNS traffic logs from being forwarded to syslog. Disabling logging on security rules allowing DNS will prevent the firewall from generating any logs for DNS traffic, which may not be desirable. Creating a security rule to deny DNS traffic with the syslog server in the destination will block the communication between the firewall and the syslog server, which may affect other logs. Creating a filter with application equal to DNS will forward only DNS traffic logs to syslog, which is the opposite of what is required.
References:
✑ https://docs.paloaltonetworks.com/pan-os/9-1/pan-os-admin/monitoring/configure-log-forwarding
✑ https://docs.paloaltonetworks.com/network-security/security-policy/objects/log-forwarding
Which CLI command displays the physical media that are connected to ethernet1/8?
- A . > show system state filter-pretty sys.si.p8.stats
- B . > show system state filter-pretty sys.sl.p8.phy
- C . > show interface ethernet1/8
- D . > show system state filter-pretty sys.sl.p8.med
An internal system is not functioning. The firewall administrator has determined that the incorrect egress interface is being used. After looking at the configuration, the administrator believes that the firewall is not using a static route.
What are two reasons why the firewall might not use a static route? (Choose two.)
- A . no install on the route
- B . duplicate static route
- C . path monitoring on the static route
- D . disabling of the static route
A remote administrator needs firewall access on an untrusted interface.
Which two components are required on the firewall to configure certificate-based administrator authentication to the web Ul? (Choose two)
- A . client certificate
- B . certificate profile
- C . certificate authority (CA) certificate
- D . server certificate
DRAG DROP
An engineer is troubleshooting traffic routing through the virtual router. The firewall uses multiple routing protocols, and the engineer is trying to determine routing priority Match the default Administrative Distances for each routing protocol.
Explanation:
✑ Static
―Range is 10-240; default is 10.
✑ OSPF Internal ―Range is 10-240; default is 30.
✑ OSPF External
―Range is 10-240; default is 110.
✑ IBGP
―Range is 10-240; default is 200.
✑ EBGP
―Range is 10-240; default is 20.
✑ RIP
―Range is 10-240; default is 120.
https://docs.paloaltonetworks.com/pan-os/9-1/pan-os-admin/networking/virtual-routers
When configuring forward error correction (FEC) for PAN-OS SD-WAN, an administrator would turn on the feature inside which type of SD-WAN profile?
- A . Certificate profile
- B . Path Quality profile
- C . SD-WAN Interface profile
- D . Traffic Distribution profile
How can an administrator use the Panorama device-deployment option to update the apps and threat version of an HA pair of managed firewalls?
- A . Configure the firewall’s assigned template to download the content updates.
- B . Choose the download and install action for both members of the HA pair in the Schedule object.
- C . Switch context to the firewalls to start the download and install process.
- D . Download the apps to the primary; no further action is required.
B
Explanation:
https://docs.paloaltonetworks.com/panorama/10-2/panorama-admin/manage-firewalls/use-case-configure-firewalls-using-panorama/set-up-your-centralized-configuration-and-policies/add-the-managed-firewalls-and-deploy-updates
An administrator has configured OSPF with Advanced Routing enabled on a Palo Alto Networks firewall running PAN-OS 10.2. After OSPF was configured, the administrator noticed that OSPF routes were not being learned.
Which two actions could an administrator take to troubleshoot this issue? (Choose two.)
- A . Run the CLI command show advanced-routing ospf neighbor
- B . In the WebUl, view the Runtime Stats in the logical router.
- C . In the WebUl, view the Runtime Stats in the virtual router.
- D . Look for configuration problems in Network > virtual router > OSPF
What is a key step in implementing WildFire best practices?
- A . In a mission-critical network, increase the WildFire size limits to the maximum value.
- B . Configure the firewall to retrieve content updates every minute.
- C . In a security-first network, set the WildFire size limits to the minimum value.
- D . Ensure that a Threat Prevention subscription is active.
D
Explanation:
In the WildFire best practices linked below, the first step is to "… make sure that you have an active Threat Prevention subscription. Together, WildFire® and Threat Prevention enable comprehensive threat detection and prevention." https://docs.paloaltonetworks.com/wildfire/10-1/wildfire-admin/wildfire-deployment-best-practices/wildfire-best-practices.html
Which time determines how long the passive firewall will wait before taking over as the active firewall alter losing communications with the HA peer?
- A . Heartbeat Interval
- B . Additional Master Hold Up Time
- C . Promotion Hold Time
- D . Monitor Fall Hold Up Time
C
Explanation:
https://docs.paloaltonetworks.com/pan-os/9-1/pan-os-admin/high-availability/ha-concepts/ha-timers
How would an administrator monitor/capture traffic on the management interface of the Palo Alto Networks NGFW?
- A . Use the debug dataplane packet-diag set capture stage firewall file command.
- B . Enable all four stages of traffic capture (TX, RX, DROP, Firewall).
- C . Use the debug dataplane packet-diag set capture stage management file command.
- D . Use the tcpdump command.
D
Explanation:
Reference:
https://live.paloaltonetworks.com/t5/Learning-Articles/How-to-Run-a-Packet-Capture/ta-p/62390
https://docs.paloaltonetworks.com/pan-os/9-1/pan-os-admin/monitoring/take-packet-captures/take-a-packet-capture-on-the-management-interface.html
An engineer is pushing configuration from Panorama lo a managed firewall.
What happens when the pushed Panorama configuration has Address Object names that duplicate the Address Objects already configured on the firewall?
- A . The firewall rejects the pushed configuration, and the commit fails.
- B . The firewall renames the duplicate local objects with "-1" at the end signifying they are clones; it will update the references to the objects accordingly and fully commit the pushed configuration.
- C . The firewall fully commits all of the pushed configuration and overwrites its locally configured objects
- D . The firewall ignores only the pushed objects that have the same name as the locally configured objects, and it will commit the rest of the pushed configuration.
What happens when an A/P firewall cluster synchronizes IPsec tunnel security associations (SAs)?
- A . Phase 1 and Phase 2 SAs are synchronized over HA3 links.
- B . Phase 1 SAs are synchronized over HA1 links.
- C . Phase 2 SAs are synchronized over HA2 links.
- D . Phase 1 and Phase 2 SAs are synchronized over HA2 links.
A network administrator wants to deploy SSL Forward Proxy decryption.
What two attributes should a forward trust certificate have? (Choose two.)
- A . A subject alternative name
- B . A private key
- C . A server certificate
- D . A certificate authority (CA) certificate
B,D
Explanation:
When deploying SSL Forward Proxy decryption, a forward trust certificate must have a subject alternative name (SAN) and be a server certificate. SAN is an extension to the X.509 standard that allows multiple domain names to be protected by a single SSL/TLS certificate. It is used to identify the domain names or IP addresses that the certificate should be valid for. A private key is also required but it is not mentioned in the options. A certificate authority (CA) certificate is not required as the forward trust certificate itself is a CA certificate.
An engineer is creating a template and wants to use variables to standardize the configuration across a large number of devices Which Mo variable types can be defined? (Choose two.)
- A . Path group
- B . Zone
- C . IP netmask
- D . FQDN
Which configuration task is best for reducing load on the management plane?
- A . Disable logging on the default deny rule
- B . Enable session logging at start
- C . Disable pre-defined reports
- D . Set the URL filtering action to send alerts
Which statement best describes the Automated Commit Recovery feature?
- A . It performs a connectivity check between the firewall and Panorama after every configuration commit on the firewall. It reverts the configuration changes on the firewall if the check fails.
- B . It restores the running configuration on a firewall and Panorama if the last configuration commit fails.
- C . It performs a connectivity check between the firewall and Panorama after every configuration commit on the firewall. It reverts the configuration changes on the firewall and on Panorama if the check fails.
- D . It restores the running configuration on a firewall if the last configuration commit fails.
A
Explanation:
https://docs.paloaltonetworks.com/panorama/10-2/panorama-admin/administer-panorama/enable-automated-commit-recovery
The Automated Commit Recovery feature enables the firewall to automatically revert to a previous configuration if a commit operation causes connectivity loss between the firewall and Panorama. The feature performs a connectivity check between the firewall and Panorama after every configuration commit on the firewall. If the check fails, the firewall reverts to the last known good configuration and restores connectivity with Panorama. The feature does not restore the running configuration on a firewall or Panorama if the last commit fails, as this would require manual intervention. The feature does not revert the configuration changes on Panorama, as Panorama is not affected by the commit operation on the firewall.
References:
https://docs.paloaltonetworks.com/pan-os/10-1/pan-os-new-features/panorama-features/automatic-panorama-connection-recovery
https://docs.paloaltonetworks.com/panorama/10-1/panorama-admin/administer-panorama/enable-automated-commit-recovery
An administrator creates an application-based security policy rule and commits the change to the firewall.
Which two methods should be used to identify the dependent applications for the respective rule? (Choose two.)
- A . Use the show predefined xpath <value> command and review the output.
- B . Review the App Dependency application list from the Commit Status view.
- C . Open the security policy rule and review the Depends On application list.
- D . Reference another application group containing similar applications.
B,C
Explanation:
These two methods allow the administrator to see the dependent applications for a security policy rule that uses application-based criteria. The App Dependency application list shows the applications that are required for the rule to function properly1. The Depends On application list shows the applications that are implicitly added to the rule based on the predefined dependencies2.
References:
1: https://docs.paloaltonetworks.com/pan-os/9-1/pan-os-new-features/app-id-features/simplified-application-dependency-workflow
2: https://docs.paloaltonetworks.com/pan-os/10-1/pan-os-admin/app-id/use-application-objects-in-policy/resolve-application-dependencies
What are two best practices for incorporating new and modified App-IDs? (Choose two)
- A . Configure a security policy rule to allow new App-lDs that might have network-wide impact
- B . Study the release notes and install new App-IDs if they are determined to have low impact
- C . Perform a Best Practice Assessment to evaluate the impact or the new or modified App-IDs
- D . Run the latest PAN-OS version in a supported release tree to have the best performance for the new App-IDs
A,B
Explanation:
https://docs.paloaltonetworks.com/pan-os/10-2/pan-os-upgrade/software-and-content-updates/best-practices-for-app-and-threat-content-updates/best-practices-security-first#id184AH00F06E
What happens, by default, when the GlobalProtect app fails to establish an IPSec tunnel to the GlobalProtect gateway?
- A . It stops the tunnel-establishment processing to the GlobalProtect gateway immediately.
- B . It tries to establish a tunnel to the GlobalProtect gateway using SSL/TLS.
- C . It keeps trying to establish an IPSec tunnel to the GlobalProtect gateway.
- D . It tries to establish a tunnel to the GlobalProtect portal using SSL/TLS.
B
Explanation:
https://knowledgebase.paloaltonetworks.com/KCSArticleDetail?id=kA10g000000ClfoCAC "Should the IPSec connection fail, VPN will fall back to SSL protocol."
The UDP-4501 protocol-port is used between which two GlobalProtect components?
- A . GlobalProtect app and GlobalProtect gateway
- B . GlobalProtect portal and GlobalProtect gateway
- C . GlobalProtect app and GlobalProtect satellite
- D . GlobalProtect app and GlobalProtect portal
A
Explanation:
UDP 4501 Used for IPSec tunnel connections between GlobalProtect apps and gateways. https://docs.paloaltonetworks.com/pan-os/8-1/pan-os-admin/firewall-administration/reference-port-number-usage/ports-used-for-globalprotect.html
Information Security is enforcing group-based policies by using security-event monitoring on Windows User-ID agents for IP-to-User mapping in the network. During the rollout, Information Security identified a gap for users authenticating to their VPN and wireless networks.
Root cause analysis showed that users were authenticating via RADIUS and that authentication events were not captured on the domain controllers that were being monitored Information Security found that authentication events existed on the Identity Management solution (IDM). There did not appear to be direct integration between PAN-OS and the IDM solution
How can Information Security extract and learn iP-to-user mapping information from authentication events for VPN and wireless users?
- A . Add domain controllers that might be missing to perform security-event monitoring for VPN and wireless users.
- B . Configure the integrated User-ID agent on PAN-OS to accept Syslog messages over TLS.
- C . Configure the User-ID XML API on PAN-OS firewalls to pull the authentication events directly from the IDM solution
- D . Configure the Windows User-ID agents to monitor the VPN concentrators and wireless controllers for IP-to-User mapping.
B
Explanation:
According to the Palo Alto Networks documentation1, the User-ID XML API is a feature that allows external systems to send user mapping information to the firewall or Panorama using XML messages over HTTPS. The User-ID XML API can be used to integrate with third-party identity management solutions (IDM) that can provide authentication events for VPN and wireless users. Therefore, the correct answer is C.
The other options are not effective or relevant for extracting and learning IP-to-user mapping information from authentication events for VPN and wireless users:
✑ Add domain controllers that might be missing to perform security-event monitoring for VPN and wireless users: This option would not help because the root cause analysis showed that authentication events were not captured on the domain controllers that were being monitored. Adding more domain controllers would not change this fact, unless they were configured to receive authentication events from RADIUS servers, which is not mentioned in the scenario.
✑ Configure the integrated User-ID agent on PAN-OS to accept Syslog messages over TLS: This option would not help because it assumes that the IDM solution can send Syslog messages over TLS, which is not mentioned in the scenario.
Moreover, Syslog messages are less reliable and secure than XML messages for user mapping information.
✑ Configure the Windows User-ID agents to monitor the VPN concentrators and wireless controllers for IP-to-User mapping: This option would not help because it assumes that the VPN concentrators and wireless controllers can provide IP-to-User mapping information, which is not mentioned in the scenario. Moreover, this option would require additional configuration and maintenance of Windows User-ID agents, which may not be feasible or scalable.
References: 1: https://docs.paloaltonetworks.com/pan-os/9-1/pan-os-admin/user-id/map-ip-addresses-to-users/send-user-mappings-to-user-id-using-the-xml-api
A super user is tasked with creating administrator accounts for three contractors. For compliance purposes, all three contractors will be working with different device-groups m their hierarchy to deploy policies and objects.
Which type of role-based access is most appropriate for this project?
- A . Create a Dynamic Admin with the Panorama Administrator role.
- B . Create a Device Group and Template Admin.
- C . Create a Custom Panorama Admin.
- D . Create a Dynamic Read only superuser
A network security administrator wants to enable Packet-Based Attack Protection in a Zone Protection profile.
What are two valid ways to enable Packet-Based Attack Protection? (Choose two.)
- A . ICMP Drop
- B . TCP Drop
- C . TCP Port Scan Block
- D . SYN Random Early Drop
An engineer must configure the Decryption Broker feature
Which Decryption Broker security chain supports bi-directional traffic flow?
- A . Layer 2 security chain
- B . Layer 3 security chain
- C . Transparent Bridge security chain
- D . Transparent Proxy security chain
B
Explanation:
Together, the primary and secondary interfaces form a pair of decryption forwarding interfaces. Only interfaces that you have enabled to be Decrypt Forward interfaces are displayed here. Your security chain type (Layer 3 or Transparent Bridge) and the traffic flow direction (unidirectional or bidirectional) determine which of the two interfaces forwards allowed, clear text traffic to the security chain, and which interface receives the traffic back from the security chain after it has undergone additional enforcement.
Which statement accurately describes service routes and virtual systems?
- A . Virtual systems that do not have specific service routes configured inherit the global service and service route settings for the firewall.
- B . Virtual systems can only use one interface for all global service and service routes of the firewall.
- C . Virtual systems cannot have dedicated service routes configured; and virtual systems always use the global service and service route settings for the firewall.
- D . The interface must be used for traffic to the required external services.
A
Explanation:
https://docs.paloaltonetworks.com/pan-os/10-2/pan-os-admin/virtual-systems/customize-service-routes-for-a-virtual-system "When a firewall is enabled for multiple virtual systems, the virtual systems inherit the global service and service route settings. For example, the firewall can use a shared email server to originate email alerts to all virtual systems. In some scenarios, you’d want to create different service routes for each virtual system."
An engineer must configure a new SSL decryption deployment.
Which profile or certificate is required before any traffic that matches an SSL decryption rule is decrypted?
- A . There must be a certificate with both the Forward Trust option and Forward Untrust option selected.
- B . A Decryption profile must be attached to the Security policy that the traffic matches.
- C . A Decryption profile must be attached to the Decryption policy that the traffic matches.
- D . There must be a certificate with only the Forward Trust option selected.
D
Explanation:
A certificate with only the Forward Trust option selected is required for SSL Forward Proxy decryption, which is the most common type of SSL decryption deployment1. A certificate with both the Forward Trust and Forward Untrust options selected is required for SSL Inbound Inspection decryption, which is less common2. A Decryption profile is not required before any traffic that matches an SSL decryption rule is decrypted, but it is recommended to apply one to control how the firewall handles traffic that cannot be decrypted3.
References:
1: https://docs.paloaltonetworks.com/pan-os/10-0/pan-os-admin/threat-prevention/decryption/decryption-concepts/ssl-forward-proxy
2: https://docs.paloaltonetworks.com/pan-os/10-0/pan-os-admin/threat-prevention/decryption/decryption-concepts/ssl-inbound-inspection
3: https://docs.paloaltonetworks.com/best-practices/10-1/decryption-best-practices/decryption-best-practices/deploy-ssl-decryption-using-best-practices
Which type of policy in Palo Alto Networks firewalls can use Device-ID as a match condition?
- A . NAT
- B . DOS protection
- C . QoS
- D . Tunnel inspection
Which GlobalProtect gateway selling is required to enable split-tunneling by access route, destination domain, and application?
- A . No Direct Access to local networks
- B . Tunnel mode
- C . iPSec mode
- D . Satellite mode
B
Explanation:
To enable split-tunneling by access route, destination domain, and application, you need to configure a split tunnel based on the domain and application on your GlobalProtect gateway2. This allows you to specify which domains and applications are included or excluded from the VPN tunnel.
An administrator is using Panorama to manage multiple firewalls. After upgrading all devices to the latest PAN-OS software, the administrator enables log forwarding from the firewalls to Panorama.
However, pre-existing logs from the firewalls are not appearing in Panorama.
Which action should be taken to enable the firewalls to send their pre-existing logs to Panorama?
- A . Export the log database.
- B . Use the import option to pull logs.
- C . Use the scp logdb export command.
- D . Use the ACC to consolidate the logs.
A
Explanation:
The import option allows the administrator to pull logs from the firewalls to Panorama. This option is useful when the firewalls have pre-existing logs that were not forwarded to Panorama before. The import option can be configured on Panorama by selecting Device > Log Collection > Import Logs.
References:
✑ https://docs.paloaltonetworks.com/panorama/9-1/panorama-admin/manage-log-collection/configure-log-forwarding-to-panorama/import-logs-from-firewalls-to-panorama.html
When planning to configure SSL Froward Proxy on a PA 5260, a user asks how SSL decryption can be implemented using phased approach in alignment with Palo Alto Networks best practices
What should you recommend?
- A . Enable SSL decryption for known malicious source IP addresses
- B . Enable SSL decryption for source users and known malicious URL categories
- C . Enable SSL decryption for malicious source users
- D . Enable SSL decryption for known malicious destination IP addresses
B
Explanation:
According to the Palo Alto Networks best practices, one of the ways to implement SSL decryption using a phased approach is to enable SSL decryption for source users and known malicious URL categories. This will allow you to block or alert on traffic that is likely to be malicious or risky, while minimizing the impact on legitimate traffic and user privacy.
References: https://docs.paloaltonetworks.com/best-practices/9-1/decryption-best-practices/decryption-best-practices/deploy-ssl-decryption-using-a-phased-approach
A company has recently migrated their branch office’s PA-220S to a centralized Panorama. This Panorama manages a number of PA-7000 Series and PA-5200 Series devices All device group and template configuration is managed solely within Panorama
They notice that commit times have drastically increased for the PA-220S after the migration
What can they do to reduce commit times?
- A . Disable "Share Unused Address and Service Objects with Devices" in Panorama Settings.
- B . Update the apps and threat version using device-deployment
- C . Perform a device group push using the "merge with device candidate config" option
- D . Use "export or push device config bundle" to ensure that the firewall is integrated with the Panorama config.
A
Explanation:
According to the Palo Alto Networks documentation1, disabling “Share Unused Address and Service Objects with Devices” in Panorama Settings is a possible solution to reduce commit times for firewalls managed by Panorama. This option prevents Panorama from pushing address and service objects that are not used in any policy rules to the firewalls, which can reduce the size of the configuration and improve the commit performance. Therefore, the correct answer is A.
The other options are not relevant or effective for reducing commit times:
✑ Update the apps and threat version using device-deployment: This option would not help because it is not related to the commit process. Updating the apps and threat version using device-deployment is a feature that allows Panorama to distribute content updates to firewalls without requiring a commit2.
✑ Perform a device group push using the “merge with device candidate config” option: This option would not help because it is not related to the commit performance. Performing a device group push using the “merge with device candidate config” option is a feature that allows Panorama to merge the local changes on a firewall with the Panorama configuration without overwriting them3.
✑ Use “export or push device config bundle” to ensure that the firewall is integrated with the Panorama config: This option would not help because it is not related to the commit performance. Using “export or push device config bundle” is a feature that allows Panorama to export or push a complete configuration bundle to a firewall, which can be useful for troubleshooting or migrating configurations4.
References:
1: https://knowledgebase.paloaltonetworks.com/KCSArticleDetail?id=kA10g000000CleLCAS
2: https://docs.paloaltonetworks.com/pan-os/9-1/pan-os-admin/firewall-administration/manage-firewalls/manage-content-updates-on-managed-firewalls/update-the-apps-and-threats-version-using-device-deployment
3: https://docs.paloaltonetworks.com/pan-os/9-1/pan-os-admin/firewall-administration/manage-firewalls/manage-firewall-configurations/perform-a-device-group-push-using-the-merge-with-device-candidate-config-option
4: https://docs.paloaltonetworks.com/pan-os/9-1/pan-os-admin/firewall-administration/manage-firewalls/manage-firewall-configurations/use-export-or-push-device-config-bundle-to-ensure-that-the-firewall-is-integrated-with-the-panorama-config
An engineer has been given approval to upgrade their environment 10 PAN-OS 10 2. The environment consists of both physical and virtual firewalls a virtual Panorama HA pair, and virtual log collectors
What is the recommended order when upgrading to PAN-OS 10.2?
- A . Upgrade Panorama, upgrade the log collectors, upgrade the firewalls
- B . Upgrade the firewalls upgrade log collectors, upgrade Panorama
- C . Upgrade the firewalls upgrade Panorama, upgrade the log collectors
- D . Upgrade the log collectors, upgrade the firewalls, upgrade Panorama
A
Explanation:
Make sure Panorama is running the same or a later PAN-OS version than you are upgrading to. You must upgrade Panorama and its Log Collectors to 10.2 before upgrading the managed firewalls to this version. In addition, when upgrading Log Collectors to 10.2, you must upgrade all Log Collectors at the same time due to changes in the logging infrastructure. https://docs.paloaltonetworks.com/pan-os/10-2/pan-os-upgrade/upgrade-pan-os/upgrade-the-firewall-pan-os/upgrade-firewalls-using-panorama
What is the best description of the HA4 Keep-Alive Threshold (ms)?
- A . the maximum interval between hello packets that are sent to verify that the HA functionality on the other firewall is operational.
- B . The time that a passive or active-secondary firewall will wait before taking over as the active or active-primary firewall
- C . the timeframe within which the firewall must receive keepalives from a cluster member to know that the cluster member is functional.
- D . The timeframe that the local firewall wait before going to Active state when another cluster member is preventing the cluster from fully synchronizing.
C
Explanation:
https://docs.paloaltonetworks.com/pan-os/10-2/pan-os-admin/high-availability/configure-ha-clustering
Which three items are import considerations during SD-WAN configuration planning? (Choose three.)
- A . link requirements
- B . the name of the ISP
- C . IP Addresses
- D . branch and hub locations
A,C,D
Explanation:
https://docs.paloaltonetworks.com/sd-wan/1-0/sd-wan-admin/sd-wan-overview/plan-sd-wan-configuration
A network security administrator wants to begin inspecting bulk user HTTPS traffic flows egressing out of the internet edge firewall.
Which certificate is the best choice to configure as an SSL Forward Trust certificate?
- A . A self-signed Certificate Authority certificate generated by the firewall
- B . A Machine Certificate for the firewall signed by the organization’s PKI
- C . A web server certificate signed by the organization’s PKI
- D . A subordinate Certificate Authority certificate signed by the organization’s PKI
D
Explanation:
https://docs.paloaltonetworks.com/pan-os/10-2/pan-os-admin/decryption/configure-ssl-forward-proxy
An administrator accidentally closed the commit window/screen before the commit was finished.
Which two options could the administrator use to verify the progress or success of that commit task? (Choose two.)
- A . System Logs
- B . Task Manager
- C . Traffic Logs
- D . Configuration Logs
A,B
Explanation:
Based on the screenshots above, and with no configuration inside the Template Stack itself, what access will the device permit on its Management port?
- A . The firewall will allow HTTP, Telnet, HTTPS, SSH, and Ping from IP addresses defined as $permitted-subnet-2.
- B . The firewall will allow HTTP, Telnet, HTTPS, SSH, and Ping from IP addresses defined as $permitted-subnet-l and Spermitted-subnet-2.
- C . The firewall will allow HTTP, Telnet, HTTPS, SSH, and Ping from IP addresses defined as $permitted-subnet-l.
- D . The firewall will allow HTTP, Telnet, SNMP, HTTPS, SSH, and Ping from IP addresses defined as $permitted-subnet-l and $permitted-subnet-2.
An engineer receives reports from users that applications are not working and that websites are only partially loading in an asymmetric environment. After investigating, the engineer observes the flow_tcp_non_syn_drop counter increasing in the show counters global output.
Which troubleshooting command should the engineer use to work around this issue?
- A . set deviceconfig setting tcp asymmetric-path drop
- B . set deviceconfig setting session tcp-reject-non-syn no
- C . set session tcp-reject-non-syn yes
- D . set deviceconfig setting tcp asymmetric-path bypass
An administrator wants to grant read-only access to all firewall settings, except administrator accounts, to a new-hire colleague in the IT department.
Which dynamic role does the administrator assign to the new-hire colleague?
- A . Device administrator (read-only)
- B . System administrator (read-only)
- C . Firewall administrator (read-only)
- D . Superuser (read-only)
Which feature of Panorama allows an administrator to create a single network configuration that can be reused repeatedly for large-scale deployments even if values of configured objects, such as routes and interface addresses, change?
- A . Template stacks
- B . Template variables
- C . The Shared device group
- D . A device group
B
Explanation:
Template variables are placeholders that you can use in a template or a template stack to represent values that differ across firewalls, such as IP addresses, hostnames, or interface names. Template variables allow you to create a single network configuration that can be reused repeatedly for large-scale deployments even if values of configured objects change 1. Option A is incorrect because template stacks are used to group multiple templates together and apply them to firewalls or device groups. Template stacks do not allow you to use variables for different values2. Option C is incorrect because the Shared device group is used to push policies and objects that are common across all firewalls managed by Panorama. The Shared device group does not allow you to use variables for different values3. Option D is incorrect because a device group is used to group firewalls that require similar policies and objects. A device group does not allow you to use variables for different values3.
An administrator connected a new fiber cable and transceiver to interface Ethernetl/l on a Palo Alto Networks firewall. However, the link does not seem to be coming up.
If an administrator were to troubleshoot, how would they confirm the transceiver type, tx-power, rx-power, vendor name, and part number via the CLI?
- A . show system state filter sw.dev.interface.config
- B . show chassis status slot s1
- C . show system state filter-pretty sys.s1.*
- D . show system state filter ethernet1/1
C
Explanation:
According to the Palo Alto Networks documentation1, the command show system state filter displays the current state of the system and allows you to filter the output by a specific keyword. The keyword ethernet1/1 matches the interface name that the administrator wants to troubleshoot. The output of this command will show information about the transceiver type, tx-power, rx-power, vendor name, and part number for that interface2. Therefore, the correct answer is D.
References:
1: https://docs.paloaltonetworks.com/pan-os/9-1/pan-os-cli-quick-start/use-the-cli/find-a-command
2: https://knowledgebase.paloaltonetworks.com/KCSArticleDetail?id=kA10g000000ClFmCAK
You need to allow users to access the office-suite applications of their choice.
How should you configure the firewall to allow access to any office-suite application?
- A . Create an Application Group and add Office 365, Evernote Google Docs and Libre Office
- B . Create an Application Group and add business-systems to it.
- C . Create an Application Filter and name it Office Programs, then filter it on the office programs subcategory.
- D . Create an Application Filter and name it Office Programs then filter on the business-systems category.
C
Explanation:
According to the Palo Alto Networks documentation, “Application filters enable you to create groups of applications based on specific characteristics such as subcategory, technology, risk factor, and so on. You can then use these groups in Security policy rules to allow or block access to the applications. For example, you can create an application filter that includes all applications in the office-programs subcategory and use it in a Security policy rule to allow access to any office-suite application.”
References: https://docs.paloaltonetworks.com/pan-os/10-2/pan-os-admin/app-id/manage-applications-in-a-policy/use-application-filters-in-policy
You have upgraded Panorama to 10.2 and need to upgrade six Log Collectors.
When upgrading Log Collectors to 10.2, you must do what?
- A . Upgrade the Log Collectors one at a time.
- B . Add Panorama Administrators to each Managed Collector.
- C . Add a Global Authentication Profile to each Managed Collector.
- D . Upgrade all the Log Collectors at the same time.
Which DoS Protection Profile detects and prevents session exhaustion attacks against specific destinations?
- A . Resource Protection
- B . TCP Port Scan Protection
- C . Packet Based Attack Protection
- D . Packet Buffer Protection
A
Explanation:
According to the documentation, resource protection detects and prevents session exhaustion attacks against specific destinations. This type of attack uses a large number of hosts to establish as many fully established sessions as possible to consume all of a system’s resources. Resource protection defines the maximum number of concurrent connections for a destination IP address or zone. References: 1 Security Profile: DoS Protection Profile – Palo Alto Networks
https://docs.paloaltonetworks.com/network-security/security-policy/security-profiles/security-profile-dos-protection-profile
An administrator is attempting to create policies tor deployment of a device group and template stack. When creating the policies, the zone drop down list does not include the required zone.
What must the administrator do to correct this issue?
- A . Specify the target device as the master device in the device group
- B . Enable "Share Unused Address and Service Objects with Devices" in Panorama settings
- C . Add the template as a reference template in the device group
- D . Add a firewall to both the device group and the template
Refer to the image.
An administrator is tasked with correcting an NTP service configuration for firewalls that cannot use the Global template NTP servers. The administrator needs to change the IP address to a preferable server for this template stack but cannot impact other template stacks.
How can the issue be corrected?
- A . Override the value on the NYCFW template.
- B . Override a template value using a template stack variable.
- C . Override the value on the Global template.
- D . Enable "objects defined in ancestors will take higher precedence" under Panorama settings.
B
Explanation:
Both templates and template stacks support variables. Variables allow you to create placeholder objects with their value specified in the template or template stack based on your configuration needs. Create a template or template stack variable to replace IP addresses, Group IDs, and interfaces in your configurations. https://docs.paloaltonetworks.com/panorama/10-0/panorama-admin/manage-firewalls/manage-templates-and-template-stacks/override-a-template-setting.html
In a Panorama template which three types of objects are configurable? (Choose three)
- A . certificate profiles
- B . HIP objects
- C . QoS profiles
- D . security profiles
- E . interface management profiles
A,C,E
Explanation:
https://docs.paloaltonetworks.com/panorama/9-1/panorama-admin/manage-firewalls/use-case-configure-firewalls-using-panorama/set-up-your-centralized-configuration-and-policies/use-templates-to-administer-a-base-configuration
An engineer configures SSL decryption in order to have more visibility to the internal users’ traffic when it is regressing the firewall.
Which three types of interfaces support SSL Forward Proxy? (Choose three.)
- A . High availability (HA)
- B . Layer 2
- C . Virtual Wire
- D . Tap
- E . Layer 3
An ISP manages a Palo Alto Networks firewall with multiple virtual systems for its tenants.
Where on this firewall can the ISP configure unique service routes for different tenants?
- A . Setup > Services > Virtual Systems > Set Location > Service Route Configuration > Inherit Global Service Route Configuration
- B . Setup > Services > Global > Service Route Configuration > Customize
- C . Setup > Services > Virtual Systems > Set Location > Service Route Configuration >
Customize - D . Setup > Services > Global > Service Route Configuration > Use Management Interface for all
C
Explanation:
The best option for the ISP to configure unique service routes for different tenants is to use the Setup > Services > Virtual Systems > Set Location > Service Route Configuration > Customize option on the firewall. This option allows the ISP to customize the service routes for each virtual system that represents a tenant. A service route is the path from the interface to the service on a server, such as DNS, email, or Panorama. By customizing the service routes for each virtual system, the ISP can ensure that each tenant uses a different interface or IP address to access these services1. Option A is incorrect because it is used to inherit the global service route configuration for a virtual system, not to customize it. Option B is incorrect because it is used to customize the global service route configuration for all virtual systems, not for a specific one. Option D is incorrect because it is used to use the management interface for all service routes, not to customize them1.
When using SSH keys for CLI authentication for firewall administration, which method is used for authorization?
- A . Local
- B . LDAP
- C . Kerberos
- D . Radius
A
Explanation:
When using SSH keys for CLI authentication for firewall administration, the method used for authorization is local. This is described in the Palo Alto Networks PCNSE Study Guide in Chapter 4: Authentication and Authorization, under the section "CLI Authentication with SSH Keys":
"SSH keys use public key cryptography to authenticate users, but they do not provide a mechanism for authorization. Therefore, when using SSH keys for CLI authentication, authorization is always performed locally on the firewall."
A customer is replacing their legacy remote access VPN solution The current solution is in place to secure only internet egress for the connected clients Prisma Access has been selected to replace the current remote access VPN solution During onboarding the following options and licenses were selected and enabled
– Prisma Access for Remote Networks 300Mbps
– Prisma Access for Mobile Users 1500 Users
– Cortex Data Lake 2TB
– Trusted Zones trust
– Untrusted Zones untrust
– Parent Device Group shared
How can you configure Prisma Access to provide the same level of access as the current VPN solution?
- A . Configure mobile users with trust-to-untrust Security policy rules to allow the desired traffic outbound to the internet
- B . Configure mobile users with a service connection and trust-to-trust Security policy rules to allow the desired traffic outbound to the internet
- C . Configure remote networks with a service connection and trust-to-untrust Security policy rules to allow the desired traffic outbound to the internet
- D . Configure remote networks with trust-to-trust Security policy rules to allow the desired traffic outbound to the internet
A
Explanation:
To provide the same level of access as the current VPN solution, which is to secure only Internet egress for the connected clients, you can configure mobile users with trust-to-untrust Security policy rules to allow the desired traffic outbound to the Internet. This way, the mobile users will be assigned an IP address from a pool that belongs to the trust zone, and they will be able to access the Internet through Prisma Access using a gateway that belongs to the untrust zone1. You do not need to configure a service connection for this scenario, as a service connection is used to enable access between mobile users and
remote networks or private apps2. You also do not need to configure trust-to-trust Security policy rules, as they are used to enable access between mobile users and other trusted resources3.
References:
1: https://docs.paloaltonetworks.com/prisma/prisma-access/prisma-access-panorama-admin/prepare-the-prisma-access-infrastructure/service-connection-overview/create-a-service-connection-to-enable-access-between-users-and-networks
2: https://docs.paloaltonetworks.com/prisma/prisma-access/prisma-access-cloud-managed-admin/prisma-access-service-connections
3: https://docs.paloaltonetworks.com/prisma/prisma-access/prisma-access-cloud-managed-admin/prisma-access-mobile-users/mobile-users-globalprotect/globalprotect-features-for-prisma-access.html
Which profile generates a packet threat type found in threat logs?
- A . Zone Protection
- B . WildFire
- C . Anti-Spyware
- D . Antivirus
A
Explanation:
"Threat/Content Type (subtype) Subtype of threat log." "packet―Packet-based attack protection triggered by a Zone Protection profile." https://docs.paloaltonetworks.com/pan-os/10-2/pan-os-admin/monitoring/use-syslog-for-monitoring/syslog-field-descriptions/threat-log-fields https://docs.paloaltonetworks.com/pan-os/10-1/pan-os-admin/monitoring/use-syslog-for-monitoring/syslog-field-descriptions/threat-log-fields packet―Packet-based attack protection triggered by a Zone Protection profile.
An engineer reviews high availability (HA) settings to understand a recent HA failover event. Review the screenshot below.
Which timer determines the frequency at which the HA peers exchange messages in the form of an ICMP (ping)
- A . Hello Interval
- B . Promotion Hold Time
- C . Heartbeat Interval
- D . Monitor Fail Hold Up Time
B
Explanation:
The heartbeat interval determines the frequency at which the HA peers exchange messages in the form of an ICMP (ping). The default value is 1000 milliseconds (1 second). The heartbeat interval is used to detect failures and trigger failover in an HA pair1
. The other options are not correct. The hello interval determines the frequency at which the HA peers exchange messages in the form of an HA packet. The default value is 3000 milliseconds (3 seconds). The hello interval is used to establish and maintain HA connectivity2. The promotion hold time determines the amount of time that a passive firewall waits before it becomes active after detecting a failure on the active firewall. The default value is 5000 milliseconds (5 seconds)3. The monitor fail hold up time determines
the amount of time that a firewall waits before it declares a monitor failure after detecting a link down event on an interface. The default value is 2000 milliseconds (2 seconds)4.
References: 1: https://docs.paloaltonetworks.com/pan-os/10-2/pan-os-admin/high-availability/ha-concepts/ha-timers
2: https://docs.paloaltonetworks.com/pan-os/10-2/pan-os-admin/high-availability/ha-concepts/ha-timers
3: https://docs.paloaltonetworks.com/pan-os/10-2/pan-os-admin/high-availability/ha-concepts/ha-timers
4:
https://docs.paloaltonetworks.com/pan-os/10-2/pan-os-admin/high-availability/ha-concepts/ha-timers
Where can an administrator see both the management-plane and data-plane CPU utilization in the WebUI?
- A . System Resources widget
- B . System Logs widget
- C . Session Browser
- D . General Information widget
A
Explanation:
The System Resources widget of the Exadata WebUI, displays a real-time overview of the various resources like CPU, Memory, and I/O usage across the entire Exadata Database Machine. It shows the usage of both management-plane and data-plane CPU utilization.
System Resources Widget Displays the Management CPU usage, Data Plane usage, and the Session Count (the number of sessions established through the firewall or Panorama). https://docs.paloaltonetworks.com/pan-os/9-1/pan-os-web-interface-help/dashboard/dashboard-widgets.html
An administrator can not see any Traffic logs from the Palo Alto Networks NGFW in Panorama reports. The configuration problem seems to be on the firewall.
Which settings, if configured incorrectly, most likely would stop only Traffic logs from being sent from the NGFW to Panorama?
A)
B)
C)
D)
- A . Option A
- B . Option B
- C . Option C
- D . Option D
Review the information below. A firewall engineer creates a U-NAT rule to allow users in the trust zone access to a server in the same zone by using an external, public NAT IP for that server.
Given the rule below, what change should be made to make sure the NAT works as expected?
- A . Change destination NAT zone to Trust_L3.
- B . Change destination translation to Dynamic IP (with session distribution) using firewall ethI/2 address.
- C . Change Source NAT zone to Untrust_L3.
- D . Add source Translation to translate original source IP to the firewall eth1/2 interface
translation.
What are two best practices for incorporating new and modified App-IDs? (Choose two.)
- A . Run the latest PAN-OS version in a supported release tree to have the best performance for the new App-IDs
- B . Configure a security policy rule to allow new App-IDs that might have network-wide impact
- C . Perform a Best Practice Assessment to evaluate the impact of the new or modified App-IDs
- D . Study the release notes and install new App-IDs if they are determined to have low impact
Based on the graphic which statement accurately describes the output shown in the Server Monitoring panel?
- A . The User-ID agent is connected to a domain controller labeled lab-client
- B . The host lab-client has been found by a domain controller
- C . The host lab-client has been found by the User-ID agent.
- D . The User-ID aaent is connected to the firewall labeled lab-client
A
Explanation:
According to the Palo Alto Networks documentation, the Server Monitoring panel displays the status of the servers that the User-ID agent monitors for user mapping information. The graphic shows that the User-ID agent is connected to a server with the IP address 10.1.1.10 and the name lab-client, which is a domain controller (DC) according to the Type column. Therefore, the correct answer is A.
The other options are inaccurate or incorrect based on the graphic:
✑ The host lab-client has been found by a domain controller: This option is inaccurate because lab-client is not a host, but a domain controller itself. The graphic does not show any information about hosts being found by domain controllers.
✑ The host lab-client has been found by the User-ID agent: This option is incorrect because lab-client is not a host, but a domain controller itself. The graphic shows that the User-ID agent is connected to lab-client, not that it has found it.
✑ The User-ID agent is connected to the firewall labeled lab-client: This option is incorrect because lab-client is not a firewall, but a domain controller. The graphic shows that the User-ID agent is connected to lab-client as a server, not as a firewall.
References: https://docs.paloaltonetworks.com/pan-os/9-1/pan-os-web-interface-help/user-identification/device-user-identification-user-id-agents/user-id-agent-monitoring/server-monitoring
An engineer is tasked with configuring SSL forward proxy for traffic going to external sites.
Which of the following statements is consistent with SSL decryption best practices?
- A . The forward trust certificate should not be stored on an HSM.
- B . The forward untrust certificate should be signed by a certificate authority that is trusted by the clients.
- C . Check both the Forward Trust and Forward Untrust boxes when adding a certificate for use with SSL decryption
- D . The forward untrust certificate should not be signed by a Trusted Root CA
B
Explanation:
According to the PCNSE Study Guide1, SSL forward proxy is a feature that allows the firewall to decrypt and inspect SSL traffic going to external sites. The firewall acts as a proxy between the client and the server, generating a certificate on the fly for each site.
The best practices for configuring SSL forward proxy are23:
✑ Use a forward trust certificate that is signed by a certificate authority (CA) that is trusted by the clients. This certificate is used to sign certificates for sites that have valid certificates from trusted CAs. The clients will not see any certificate errors if they trust the forward trust certificate.
✑ Use a forward untrust certificate that is not signed by a trusted CA. This certificate is used to sign certificates for sites that have invalid or untrusted certificates. The clients will see certificate errors if they do not trust the forward untrust certificate.
This helps alert users of potential risks and prevent man-in-the-middle attacks.
✑ Do not store the forward trust or untrust certificates on an HSM (hardware security module). The HSM does not support on-the-fly signing of certificates, which is required for SSL forward proxy.
An engineer is tasked with configuring SSL forward proxy for traffic going to external sites.
Which of the following statements is consistent with SSL decryption best practices?
- A . The forward trust certificate should not be stored on an HSM.
- B . The forward untrust certificate should be signed by a certificate authority that is trusted by the clients.
- C . Check both the Forward Trust and Forward Untrust boxes when adding a certificate for use with SSL decryption
- D . The forward untrust certificate should not be signed by a Trusted Root CA
B
Explanation:
According to the PCNSE Study Guide1, SSL forward proxy is a feature that allows the firewall to decrypt and inspect SSL traffic going to external sites. The firewall acts as a proxy between the client and the server, generating a certificate on the fly for each site.
The best practices for configuring SSL forward proxy are23:
✑ Use a forward trust certificate that is signed by a certificate authority (CA) that is trusted by the clients. This certificate is used to sign certificates for sites that have valid certificates from trusted CAs. The clients will not see any certificate errors if they trust the forward trust certificate.
✑ Use a forward untrust certificate that is not signed by a trusted CA. This certificate is used to sign certificates for sites that have invalid or untrusted certificates. The clients will see certificate errors if they do not trust the forward untrust certificate.
This helps alert users of potential risks and prevent man-in-the-middle attacks.
✑ Do not store the forward trust or untrust certificates on an HSM (hardware security module). The HSM does not support on-the-fly signing of certificates, which is required for SSL forward proxy.
DRAG DROP
Match each GlobalProtect component to the purpose of that component
Explanation:
The GlobalProtect portal provides the management functions for your GlobalProtect infrastructure
The GlobalProtect gateways provide security enforcement for traffic from GlobalProtect apps
The GlobalProtect app software runs on endpoints and enables access to your network resources
A company is looking to increase redundancy in their network.
Which interface type could help accomplish this?
- A . Layer 2
- B . Virtual wire
- C . Tap
- D . Aggregate ethernet
D
Explanation:
An aggregate group increases the bandwidth between peers by load balancing traffic across the combined interfaces. It also provides redundancy https://docs.paloaltonetworks.com/pan-os/10-1/pan-os-networking-admin/configure-interfaces/configure-an-aggregate-interface-group#id9c0f5a8b-0aad-4be5-821d-ef9d7c11a88d
A firewall administrator notices that many Host Sweep scan attacks are being allowed through the firewall sourced from the outside zone.
What should the firewall administrator do to mitigate this type of attack?
- A . Create a DOS Protection profile with SYN Flood protection enabled and apply it to all rules allowing traffic from the outside zone
- B . Enable packet buffer protection in the outside zone.
- C . Create a Security rule to deny all ICMP traffic from the outside zone.
- D . Create a Zone Protection profile, enable reconnaissance protection, set action to Block, and apply it to the outside zone.
D
Explanation:
https://docs.paloaltonetworks.com/pan-os/10-2/pan-os-admin/zone-protection-and-dos-protection/configure-zone-protection-to-increase-network-security/configure-reconnaissance-protection
Where is Palo Alto Networks Device Telemetry data stored on a firewall with a device certificate installed?
- A . Cortex Data Lake
- B . Panorama
- C . On Palo Alto Networks Update Servers
- D . M600 Log Collectors
The firewall identifies a popular application as an unKnown-tcp.
Which two options are available to identify the application? (Choose two.)
- A . Create a custom application.
- B . Submit an App-ID request to Palo Alto Networks.
- C . Create a custom object for the application server.
- D . Create a Security policy to identify the custom application.
A,B
Explanation:
You can create a custom app: https://docs.paloaltonetworks.com/pan-os/9-1/pan-os-admin/app-id/use-application-objects-in-policy/create-a-custom-application or submit a request to PAN https://www.paloaltonetworks.com/blog/submit-an-application/
Which source is the most reliable for collecting User-ID user mapping?
- A . GlobalProtect
- B . Microsoft Active Directory
- C . Microsoft Exchange
- D . Syslog Listener
A
Explanation:
User-ID is a feature that enables you to identify and control users on your network based on their usernames instead of their IP addresses1. User mapping is the process of mapping IP addresses to usernames using various sources of information1. The most reliable source for collecting User-ID user mapping is GlobalProtect2.
GlobalProtect is a solution that provides secure access to your network and resources from anywhere. GlobalProtect agents on endpoints send user mapping information directly to the firewall or Panorama, which eliminates the need for probing other sources2 . GlobalProtect also supports dynamic IP address changes and roaming users2.
A customer wants to set up a VLAN interface for a Layer 2 Ethernet port.
Which two mandatory options are used to configure a VLAN interface? (Choose two.)
- A . Virtual router
- B . Security zone
- C . ARP entries
- D . Netflow Profile
A,B
Explanation:
Reference:
https://www.paloaltonetworks.com/documentation/80/pan-os/web-interface-help/network/network-interfaces/pa-7000-series- layer-2-interface#idd2bcaacc-54b9-4ec9-a1dd-8064499f5b9d
https://knowledgebase.paloaltonetworks.com/KCSArticleDetail?id=kA10g000000ClRqCAK
VLAN interface is not necessary but in this scenarion we assume it is. Create VLAN object, VLAN interface and VLAN Zone. Attach VLAN interface to VLAN object together with two
L2 interfaces then attach VLAN interface to virtual router. Without VLAN interface you can pass traffic between interfaces on the same network and with VLAN interface you can route traffic to other networks.
Which three items are import considerations during SD-WAN configuration planning? (Choose three.)
- A . link requirements
- B . the name of the ISP
- C . IP Addresses
- D . branch and hub locations
A,C,D
Explanation:
https://docs.paloaltonetworks.com/sd-wan/1-0/sd-wan-admin/sd-wan-overview/plan-sd-wan-configuration
An administrator needs to assign a specific DNS server to one firewall within a device group.
Where would the administrator go to edit a template variable at the device level?
- A . Variable CSV export under Panorama > templates
- B . PDF Export under Panorama > templates
- C . Manage variables under Panorama > templates
- D . Managed Devices > Device Association
A
Explanation:
To edit a template variable at the device level, you need to go to Manage variables under Panorama > templates. This allows you to override the default value of a variable for a specific device or device group. For example, you can assign a specific DNS server to one firewall within a device group by editing the ${dns-primary} variable for that device.
References: https://docs.paloaltonetworks.com/panorama/10-1/panorama-admin/manage-firewalls/manage-templates/use-template-variables.html
An engineer manages a high availability network and requires fast failover of the routing protocols. The engineer decides to implement BFD.
Which three dynamic routing protocols support BFD? (Choose three.)
- A . OSPF
- B . RIP
- C . BGP
- D . IGRP
- E . OSPFv3 virtual link
An engineer is deploying multiple firewalls with common configuration in Panorama.
What are two benefits of using nested device groups? (Choose two.)
- A . Inherit settings from the Shared group
- B . Inherit IPSec crypto profiles
- C . Inherit all Security policy rules and objects
- D . Inherit parent Security policy rules and objects
A company requires that a specific set of ciphers be used when remotely managing their
Palo Alto Networks appliances.
Which profile should be configured in order to achieve this?
- A . SSH Service profile
- B . SSL/TLS Service profile
- C . Decryption profile
- D . Certificate profile
Refer to the exhibit.
An organization has Palo Alto Networks NGFWs that send logs to remote monitoring and security management platforms. The network team has reported excessive traffic on the corporate WAN.
How could the Palo Alto Networks NGFW administrator reduce WAN traffic while maintaining support for all the existing monitoring/security platforms?
- A . Forward logs from firewalls only to Panorama and have Panorama forward logs to other external services
- B . Configure log compression and optimization features on all remote firewalls
- C . Any configuration on an M-500 would address the insufficient bandwidth concerns
- D . Forward logs from external sources to Panorama for correlation, and from Panorama send them to the NGFW
A
Explanation:
Forwarding logs from firewalls only to Panorama and having Panorama forward logs to other external services is the best option for the administrator to reduce WAN traffic while maintaining support for all the existing monitoring/security platforms. This option minimizes the number of log forwarding destinations on each firewall and consolidates log forwarding on Panorama. Panorama can forward logs to external destinations such as syslog servers, email servers, SNMP trap receivers, HTTP servers, or AutoFocus1. Option B is incorrect because configuring log compression and optimization features on all remote firewalls may reduce the size of log files but does not reduce the number of log forwarding destinations. Option C is incorrect because any configuration on an M-500 would not address the insufficient bandwidth concerns. An M-500 is a dedicated log collector that can store logs from multiple firewalls and Panorama appliances. However, it does not reduce the WAN traffic generated by log forwarding2. Option D is incorrect because forwarding logs from external sources to Panorama for correlation, and from Panorama send them to the NGFW does not reduce WAN traffic while maintaining support for all the existing monitoring/security platforms. This option would increase the WAN traffic by sending logs back and forth between Panorama and the NGFW1.
An administrator is troubleshooting why video traffic is not being properly classified.
If this traffic does not match any QoS classes, what default class is assigned?
- A . 1
- B . 2
- C . 3
- D . 4
A network security administrator has an environment with multiple forms of authentication. There is a network access control system in place that authenticates and restricts access for wireless users, multiple Windows domain controllers, and an MDM solution for company-provided smartphones. All of these devices have their authentication events logged.
Given the information, what is the best choice for deploying User-ID to ensure maximum coverage?
- A . Syslog listener
- B . agentless User-ID with redistribution
- C . standalone User-ID agent
- D . captive portal
An engineer is designing a deployment of multi-vsys firewalls.
What must be taken into consideration when designing the device group structure?
- A . Multiple vsys and firewalls can be assigned to a device group, and a multi-vsys firewall must have all its vsys in a single device group.
- B . Only one vsys or one firewall can be assigned to a device group, except for a multi-vsys firewall, which must have all its vsys in a single device group.
- C . Multiple vsys and firewalls can be assigned to a device group, and a multi-vsys firewall can have each vsys in a different device group.
- D . Only one vsys or one firewall can be assigned to a device group, and a multi-vsys firewall can have each vsys in a different device group.
Which log type would provide information about traffic blocked by a Zone Protection profile?
- A . Data Filtering
- B . IP-Tag
- C . Traffic
- D . Threat
D
Explanation:
https://knowledgebase.paloaltonetworks.com/KCSArticleDetail?id=kA10g000000Clm9CAC Zone Protection profile is a set of security policies that you can apply to an interface or zone to protect it from reconnaissance, flooding, brute force, and other types of attacks. The log type that would provide information about traffic blocked by a Zone Protection profile is Threat4. This log type records events such as packet-based attacks, spyware, viruses, vulnerability exploits, and URL filtering.
A company wants to install a PA-3060 firewall between two core switches on a VLAN trunk link. They need to assign each VLAN to its own zone and to assign untagged (native) traffic to its own zone which options differentiates multiple VLAN into separate zones?
- A . Create V-Wire objects with two V-Wire interfaces and define a range of "0-4096 in the "Tag Allowed" field of the V-Wire object.
- B . Create V-Wire objects with two V-Wire subinterfaces and assign only a single VLAN ID to the Tag Allowed" field of the V-Wire object. Repeat for every additional VLAN and use a VLAN ID of 0 for untagged traffic. Assign each interface/sub interface to a unique zone.
- C . Create Layer 3 subinterfaces that are each assigned to a single VLAN ID and a common virtual router. The physical Layer 3 interface would handle untagged traffic. Assign each interface/subinterface tA. unique zone. Do not assign any interface an IP address.
- D . Create VLAN objects for each VLAN and assign VLAN interfaces matching each VLAN ID. Repeat for every additional VLAN and use a VLAN ID of 0 for untagged traffic. Assign each interface/sub interface to a unique zone.
B
Explanation:
https://docs.paloaltonetworks.com/pan-os/9-0/pan-os-admin/networking/configure-interfaces/virtual-wire-interfaces/vlan-tagged-traffic
Virtual wire interfaces by default allow all untagged traffic. You can, however, use a virtual wire to connect two interfaces and configure either interface to block or allow traffic based on the virtual LAN (VLAN) tags. VLAN tag 0 indicates untagged traffic.You can also create multiple subinterfaces, add them into different zones, and then classify traffic according to a VLAN tag or a combination of a VLAN tag with IP classifiers (address, range, or subnet) to apply granular policy control for specific VLAN tags or for VLAN tags from a specific source IP address, range, or subnet.
An administrator notices that an interface configuration has been overridden locally on a firewall. They require all configuration to be managed from Panorama and overrides are not allowed.
What is one way the administrator can meet this requirement?
- A . Perform a commit force from the CLI of the firewall.
- B . Perform a template commit push from Panorama using the "Force Template Values" option.
- C . Perform a device-group commit push from Panorama using the "Include Device and Network Templates" option.
- D . Reload the running configuration and perform a Firewall local commit.
B
Explanation:
This option will overwrite any local configuration on the firewall with the template configuration from Panorama1. Performing a commit force from the CLI of the firewall will not remove the local override2. Performing a device-group commit push from Panorama using the “Include Device and Network Templates” option will not remove the local override 3. Reloading the running configuration and performing a Firewall local commit will not remove the local override.
References:
1: https://docs.paloaltonetworks.com/panorama/10-1/panorama-admin/manage-firewalls/manage-templates-and-template-stacks/force-template-values
2: https://docs.paloaltonetworks.com/pan-os/10-1/pan-os-cli-quick-start/use-the-cli/commit-changes
3: https://docs.paloaltonetworks.com/panorama/10-1/panorama-admin/manage-firewalls/manage-device-groups/push-policy-and-configuration-to-firewalls : https://docs.paloaltonetworks.com/pan-os/10-1/pan-os-admin/firewall-administration/manage-firewall-configurations/revert-to-a-previous-configuration
What can you use with Global Protect to assign user-specific client certificates to each GlobalProtect user?
- A . SSL/TLS Service profile
- B . Certificate profile
- C . SCEP
- D . OCSP Responder
C
Explanation:
If you have a Simple Certificate Enrollment Protocol (SCEP) server in your enterprise PKI, you can configure a SCEP profile to automate the generation and distribution of unique client certificates. https://docs.paloaltonetworks.com/pan-os/10-2/pan-os-admin/certificate-management/obtain-certificates/deploy-certificates-using-scep
A firewall engineer reviews the PAN-OS GlobalProtect application and sees that it implicitly uses web-browsing and depends on SSL.
When creating a new rule, what is needed to allow the application to resolve dependencies?
- A . Add SSL and web-browsing applications to the same rule.
- B . Add web-browsing application to the same rule.
- C . Add SSL application to the same rule.
- D . SSL and web-browsing must both be explicitly allowed.
What can be used to create dynamic address groups?
- A . dynamic address
- B . region objects
- C . tags
- D . FODN addresses
C
Explanation:
https://docs.paloaltonetworks.com/pan-os/10-2/pan-os-admin/policy/monitor-changes-in-the-virtual-environment/use-dynamic-address-groups-in-policy
An administrator is configuring SSL decryption and needs 10 ensure that all certificates for both SSL Inbound inspection and SSL Forward Proxy are installed properly on the firewall.
When certificates are being imported to the firewall for these purposes, which three certificates require a private key? (Choose three.)
- A . Forward Untrust certificate
- B . Forward Trust certificate
- C . Enterprise Root CA certificate
- D . End-entity (leaf) certificate
- E . Intermediate certificate(s)
A,B,D
Explanation:
This is discussed in the Palo Alto Networks PCNSE Study Guide in Chapter 9: Decryption, under the section "SSL Forward Proxy and Inbound Inspection Certificates":
"When importing SSL decryption certificates, you need to provide private keys for the forward trust, forward untrust, and end-entity (leaf) certificates. You do not need to provide private keys for the root CA and intermediate certificates."
An administrator has configured a pair of firewalls using high availability in Active/Passive mode. Path Monitoring has been enabled with a Failure Condition of "any." A path group is configured with Failure Condition of "all" and contains a destination IP of 8.8.8.8 and 4.2.2.2 with a Ping Interval of 500ms and a Ping count of 3.
Which scenario will cause the Active firewall to fail over?
- A . IP address 8.8.8.8 is unreachable for 1 second.
- B . IP addresses 8.8.8.8 and 4.2.2.2 are unreachable for 1 second.
- C . IP addresses 8.8.8.8 and 4.2.2.2 are unreachable for 2 seconds
- D . IP address 4.2.2.2 is unreachable for 2 seconds.
Given the screenshot, how did the firewall handle the traffic?
- A . Traffic was allowed by policy but denied by profile as encrypted.
- B . Traffic was allowed by policy but denied by profile as a threat.
- C . Traffic was allowed by profile but denied by policy as a threat.
- D . Traffic was allowed by policy but denied by profile as a nonstandard port.
B
Explanation:
The screenshot shows the threat log which records the traffic that matches a threat signature or is blocked by a security profile. The log entry indicates that the traffic was allowed by the security policy rule “Allow-All” but was denied by the vulnerability protection profile “strict” as a threat. The threat name is “Microsoft Windows SMBv1 Multiple Vulnerabilities (MS17-010: EternalBlue)” and the action is “reset-both” which means that the firewall reset both the client and server connections.
References: https://docs.paloaltonetworks.com/pan-os/10-2/pan-os-admin/monitoring/use-syslog-for-monitoring/syslog-field-descriptions/threat-log-fields