A customer has a G6 AHV cluster with 4x10GbE NICs on each node and the following configuration:
* Networking is set to default
* Only two NICs are connected
The customer receives the following critical message:
The NIC is disconnected from the switch, or the switchport is failing.
What should the consultant verify to resolve the issue?
- A . The NICs are configured for active-backup.
- B . The VLANs are configured correctly on the switch or tagged on the cluster.
- C . The other two 10GbE connections are removed from the default bond.
- D . The NICs are connected for balance-slb.
An administrator is performing a set of routine checks and notes that Prism Central is running with 4 vCPUs and 21 GB RAM. The organizations environment is based on two Nutanix clusters with 170 VMs plus a Legacy vSphere infrastructure. No manual changes have been done on Prism Central VM.
Which configuration justifies the current Prism Central configuration?
- A . Nutanix Move is running on Prism Central to import VMs from the Legacy Cluster.
- B . Prism Central was installed for Large Deployment environments.
- C . Prism Central is running on the legacy duster and requires more RAM.
- D . Nutanix Leapand Nutanix Flow have been enabled on Prism Central
Which Nutanix feature creation is described in the Knowledge Transfer?
- A . Calm Blueprints
- B . REST API
- C . Self Service Portal
- D . Data Protection Domain
A customer wants to expand an existing cluster with three additional nodes. After running the Foundation process on the new nodes, the customer realizes that the wrong IPs where used and the nodes are configured on a different network. The customer decides to create a new cluster instead.
Which method should be used to recreate the cluster?
- A . Log into IPMI and use cluster create command to create the cluster.
- B . Log into CVM and use cluster create command to create the cluster.
- C . Log into Hypervisor and use cluster create command to create the cluster.
- D . Foundation all nodes again and create the cluster.
A consultant is performing a Nutanix Cluster installation on Dell XC Core hardware. The consultant decides to use Foundation Portable for Mac to perform the installation. When the consultant arrives onsite, Foundation Portable is unable to locate the new nodes.
Which log should the consultant check to troubleshoot this issue?
- A . /home/nutanix/foundation/log
- B . ~/data/logs/foundation.out
- C . foundation.app/contents/resouces/log
- D . ~/data/logs/foundation
For several days, an administrator notices the following alerts:
• CVM NIC Speed Low Warning Alerts
• Warning Alerts of CVM NIC not performing at optimal speed
• CVM is disconnected from the network Critical Alert
• Network Visualization page shows excessive dropped packets on CVM/Host.
Which steps should be taken to determine which problem should be addressed first?
- A . • Access the Hardware Page to verifyresources are available
• Analyze ail CVM Speed Alerts in the Alerts/Events page
• Analyze output for the network and interface properties and connectivity issues - B . • Verify Host/CVM connectivity on the Network Visualization page
• Use toverify the bridge and bond configuration
• Review alerts/events page for the CVM disconnected error - C . • Review Alerts page for NIC speed alerts and alert timing
• Analyze the genesis.out log file for process failures
• Assess the NIC properties inthe Network Visualization > Host Properties page - D . • Restart networking services on the CVM
• Determine the current configuration of the affected CVM via output
• Access the Alerts/Events page for the CVM network connection failures
B
Explanation:
Ref: https://portal.nutanix.com/page/documents/kbs/details?targetId=kA00e000000CuaDCA S
A consultant is using the Foundation applet to create a cluster. During the process the consultant refreshes the progress bar web page and is concerned when nothing loads.
What should the consultant do to verify that Foundation has completed successfully?
- A . Return to the Foundation configuration page and start over.
- B . Update Java on the Foundation VM.
- C . Connect to any CVM IP address from a web browser.
- D . Restart the Foundation process.
After the migration, some SQL queries take longer to execute than prior to migration.
The following SQL best practices were applied while creating the SQL VM on Nutanix:
• 8 vDisks per SQL server VM
• Database and Log files on separate vDisk
• 2 TempDB database drives and 1 TempDB log drive
What should the administrator to do improve the SQL Server performance?
- A . Redistribute existing data by creating additional database file and enable autogrowth
- B . Create multiple TempDB data files and enable autogrowth
- C . Create multiple SQL log files and disable autogrowth
- D . Redistribute existing data by creating additional database files and disable autogrowth
After imaging the nodes and creating the cluster successfully, the consultant connects the cluster to the customer network. When logging into Prism, the events dashboard is full of errors.
What is causing the issue?
- A . The cluster was not stopped prior to connecting to the customer network.
- B . The Cluster Virtual IP Address (VIP) was not set up during the process.
- C . Foundation did not create the cluster successfully.
- D . The consultant did not run Nutanix Cluster Check (NCC..
After uploading a hypervisor ISO during the Foundation process, a consultant sees a message that the MD5 sum for the hypervisor is not found in the Whitelist file.
Which step should the consultant take next to resolve this issue?
- A . Download the hypervisor ISO again from the vendor website.
- B . Restart the Foundation process and upload the hypervisor again.
- C . Download the latest hypervisor ISO whitelist file from Nutanix portal.
- D . Check the hypervisor version in the Nutanix Compatibility Matrix.
A customer wants to know the details of network validation testing.
Where can the consultant find this information?
- A . Handover checklist
- B . Test plan
- C . Operations Guides
- D . As-Built Guide
A customer wants to use NIC teaming on an ESXi host using a vSphere Standard Switch configured with the Route based on physical NIC load load balancing option. The customer does not see the option when editing the Teaming and Failover settings for the switch.
How should the consultant resolve this issue?
- A . Change the load balancing option on the switch.
- B . Add a vSphere Distributed Switch
- C . Add another physical NIC to the team.
- D . Install a vCenter server to manage the switch
A consultant is onsite with a customer running Foundation VM (FVM) and discovers that there is no connectivity between the FVM and their laptop.
The consultant verifies the following:
* The consultant’s laptop and Nutanix nodes are plugged into a flat switch.
* The laptop, switch and nodes are plugged into supported power supplies.
* The laptop network adapters and FVM are configured with their corresponding IP addresses.
What is the cause for the connectivity failure to the FVM?
- A . The switch is not plugged into the power supply.
- B . Desktop Firewall is blocking ping requests.
- C . Network cables are not connected.
- D . Laptop WiFi configured to use DHCP.
An administrator has a custom backup application that requires a 2TB disk and runs in Windows. Throughput is considerably lower than expected.
The application was installed on a VM with the following configuration:
• Four vCPUs with one core/vCPU
• 4GB of Memory
• One 50GB vDisk for the Windows installation
• One 2TB vDisk for the application
What is the recommended configuration change to improve throughput?
- A . Increase the number of cores per vCPU
- B . Increase the vCPUs assigned to the VM
- C . Span the 2TB disk across four vDisks
- D . Add 4GB of memory to the VM
A consultant runs the Foundation Applet and discovers all the nodes. The consultant wants to use the latest version of Foundation for imaging for support purposes and to cover the latest hardware and software hypervisor support.
What should the consultant do to upgrade Foundation on a node?
- A . Use crash cart and manually upgrade Foundation files on one node.
- B . Use latest version of Foundation to reimage all the nodes.
- C . Use the Foundation VM to upgrade Foundation on all nodes.
- D . Use the Foundation Applet to upgrade Foundation on a single node.
An administrator needs to initiate a new VDI project within a couple of months. Prism Central reports there are no storage resources to accommodate such workloads.
The administrator sees many powered-off VMs and has the authority to delete test VMs powered off at least for 30 days. Test VMs belong to the Test category.
Using Prism Central, which steps are required to identify the correct VMs tobe deleted?
- A . Use Capacity Runway to filter by Test and Powered-off VMs
- B . Filter VMs list, choose Test category and Inactive under Efficiency
- C . Create a new Scenario selecting Test VMs. filter by uptime
- D . Create a new Project selecting Test VMs,sorting by power state
A customer has NearSync configured. When the administrator tries to restore a snapshot from 3 minutes ago, it is not available. The snapshots are happening at15-minute intervals instead of at the 5-minute configured interval. When the protection domain was initially set up, the snapshots were happening at the expected 5-minute interval.
What should the customer do to enable the snapshots to happen at the expected interval?
- A . Utilize Metro Availability to meet this requirement
- B . Change the protection domain to use Async DR
- C . Fix a connectivity issue because the protection domain reverted to Async
- D . Configure the protection domain to take snapshots on15-minute intervals
An administrator is deploying an application that requires maximum I/O throughput for scratch data. The administrator is concerned that the throughput requirement is greater than what can be provided by asingle cluster node.
What should the administrator do to meet this requirement?
- A . Create a volume group with several virtual disks and attach to the VM
- B . Create a volume group with one virtual disk attached to the VM
- C . Create a virtual disk attached tothe VM’s PCI interface
- D . Create several virtual disks attached to the VM’s virtual SCSI controller
A
Explanation:
Ref: https://next.nutanix.com/community-blog-40/scaling-up-vm-storage-performance-on-ahv-volume-group-load-balancer-28063
A consultant is preparing to add new nodes into an existing cluster. The current cluster AOS version is 5.8. The new expansion node is currently running AOS 5.9 code. The cluster must continue to run at its current AOS version.
Which method can be used to successfully add the node?
- A . Upgrade the cluster to 5.9 and add the node through Prism Element.
- B . Use Prism Element to Expand the cluster and select the re-image option.
- C . Use the CLI and enter cluster add-node node-serial=”node_serial”.
- D . Use Prism Element, which will downgrade the node by default during the node add process.
An administrator is concerned that Prism will be inaccessible if Active Directory is unable to process logins .
Which method should the administrator use to access the cluster in the event of this type of outage?
- A . Manage the cluster by using the "nutanix" user on the Prism leader CVM
- B . Create and use an emergency local account on the cluster
- C . Deploy an Active Directory server locally on the cluster
- D . Manage the cluster remotely by downloading ncli to a remote workstation
An administrator configure Active Directory (AD) authentication for their Nutanix environment. When login in using an AD user account, the login process takes more than one minute to complete. No delay occurs when logging a local account.
What should the administrator confirm to resolve this issue?
- A . The user search base for the group is configuredcorrectly
- B . The domain controller being used is configured as a global catalog server.
- C . Active directory lookups are configured to use Non-Recursive mode.
- D . The service Account Username is correct for the domain.
A customer has a four-node cluster and is using Volume Groups to provide storage services to a SQL cluster.
In the event of a CVM failure in the cluster, what is the expected IO path of the volume group’s iSCSI targets?
- A . vDisk directed at failure CVM are redirected to Data Services IP until CVM is reconnected
- B . vDisk directed to CVM that failed to disconnect and will not reconnect without manual intervention
- C . vDisk directed to failed CVM are redirected to another CVM and automatically reconnect
- D . vDisk directed at failed CVM will disconnect and reconnect when the failed CVM comes back online
An administrator is implementing a VDI solution. The workload will be a series of persistent desktops in a dedicated storage container within a four-node cluster. Storage optimizations should be set on the dedicated storage container to give optimal performance including during a node failure event.
Which storage optimizations should the administrator set to meet the requirements?
- A . Compression, Deduplication, and Erasure Coding
- B . Deduplication and Erasure Coding
- C . Compression and Deduplication
- D . Compression only
For a new AHV cluster installation, a customer has 20 NX-8155-G6 nodes with quad port SFP NICs.
The customer wants to meet the following guidelines:
* Take advantage of all available 10GbE links
* Achieve maximum throughput per VM
* Use of redundant ToR switches
* Fastest reconvergence during link failure
How should the load balancing be configured on the host?
- A . ovs-vsctl set port br0-up bond_mode=balance-slb
ovs-vsctl set port br0-up other_config:bond-rebalance-interval=30000
ovs-vsctl set port br0 tag=10 - B . ovs-vsctl set port br0-up bond_mode=active-backup
ovs-vsctl set port br0-up other_config:bond-rebalance-interval=30000 - C . ovs-vsctl set port br0-up bond_mode=balance-slb
- D . ovs-vsctl set port br0-up other_config:lacp-fallback-ab=true
ovs-vsctl set port br0-up lacp=active
ovs-vsctl set port br0-up bond_mode=balance-tcp
An administrator has a VM that consumes large amounts of storage and has the following characteristics:
• Create large / sequential writes
• Data must be kept for years
• Data is normally only accessed at the end of the year to run report
The administrator decides to use Erasure Coding to save space.
Which feature should the administrator utilize to save space for this VM?
- A . Inline Compression
- B . Flash Mode
- C . CacheDedup
- D . Post-Process Compression
A consultant is running the Foundation VM using desktop virtualization software. No nodes are discovered.
What should the consultant verify first?
- A . NAT
- B . Host-only Adapter
- C . Bridged Adapter
- D . Internal Network
An administrator is deploying a new application to a Nutanix Enterprise Cloud. The application requires a security to prevent unauthorized access. The application also uses many non-standard ports that are unique to it. Security should not be changed for existing applications.
What should the administrator do to meet these requirement?
- A . Use existing categories for the VMs. and create new security policies to use the existing categories.
- B . Use existing categories for the VMs and modify existing security policies to include the specific port.
- C . Create new categories for the VMs, and create new security policies that include the new categories.
- D . Create new categories for the VMs, and modify existing security policies to include the new categories.
A consultant is deploying a two-node cluster at a remote branch office.
Which component must be available to complete cluster configuration?
- A . Prism Central
- B . Witness VM
- C . Remote Site
- D . Protection Domain
While preparing for a new four-node cluster installation, the consultant has a Tech Review Call with the customer.
The hardware is as follows:
* 4 nodes in 1 Block
* 8 x 10 GbE Ports
* 4 x 1 GbE IPMI Ports
* Adequate Ethernet ports are available
* Ethernet cables are correct and available
* Adequate rack space is available
Which remaining item must be confirmed as available onsite?
- A . Crash Cart
- B . Fibre Channel switches
- C . Redundant 208v power
- D . Redundant 110v power
An organization is running a Nutanix Cluster based on AOS 5.10.x and VMware vSphere 6.7. Currently, the CVM network is segmented and Storage only nodes not present.
A new security project based on NSX is coming. VMware Distributed Virtual Switches are required. The administrator needs to prepare the environment for the new project.
Which step should the administrator use to initiate the project?
- A . Enable Nutanix Flow at the Prism Central Level
- B . Manually disable CVM network Segmentation
- C . Convert storage only nodes into vSphere nodes
- D . Enable Jumbo Frames to accommodate network frames
After deploying an AHV cluster connected to Cisco Nexus 9k switches, unexpected network behavior is observed. The consultant needs to rule out physical network mis-cabling without returning to the datacenter.
Which command from the host should the consultant run?
- A . show lldp neighbors
- B . show cdp neighbors
- C . show interfaces
- D . lldpctl
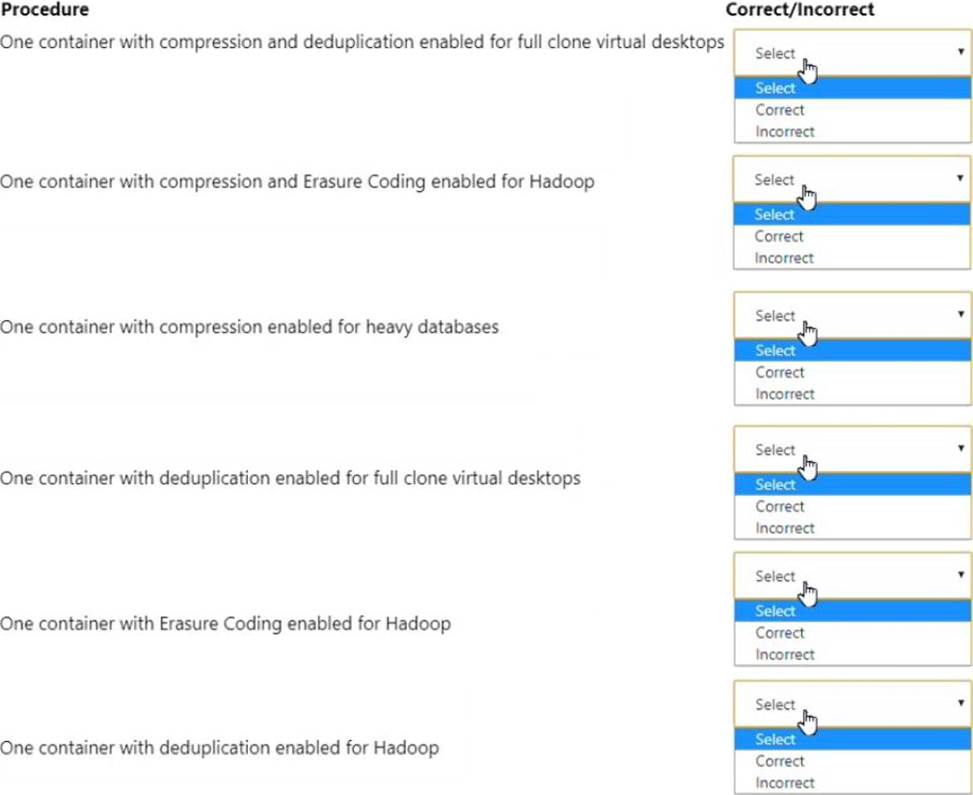
HOTSPOT
An administrator is configuring an All Flash cluster to support the following workloads:
• Full clone virtual desktops
• Hadoop
• Write heavy databases
Which three correct configuration options should the administrator use to meet the item requirements? (Choose three.)
For each procedure, indicate whether it is a correct or incorrect procedure that must be configured to meet the item requirements using the drop-down option.
A consultant is unable to install virtualization software on a laptop.
Which two versions of Foundation can be used to resolve this issue? (Choose two.)
- A . Foundation VM
- B . Foundation Portable
- C . Foundation Central
- D . Foundation Applet
An administrator is using Nutanix Move to migrate a Windows VM from ESXi to AHV.
Automated guest preparation is failing with an error:
Account has UAC enabled error
The administrator is using the local built-in administrator account for the Windows VM Admin approval mode must remain enabled.
What should the administrator do to continue with the migration with Nutanix Move?
- A . Use a Domain Admin account for the Windows VM
- B . Reboot the Windows VM and try the migration again
- C . Follow manual VM preparation guidelines
- D . Place Windows VM in Maintenance Mode
C
Explanation: https://next.nutanix.com/move-application-migration-19/nutanix-xtract-validation-failed-user-must-belong-in-a-group-with-restore-files-and-directories-security-policy-31303
A VM does not have enough resources for the demand, which leads to performance bottlenecks.
The VM is exhibiting one or more of following baseline values, based on the past 30 days:
• CPU usage > 90% (moderate), 95% (high)
• CPU ready time > 5%, 10%
• Memory usage > 90%, 95%
• Memory swap rate > 0Kbps (no moderate value).
Which type of VM is being described?
- A . Constrained VM
- B . Bully VM
- C . Inactive VM
- D . Over-provisioned VM
In a 20-node ESXi deployment, the customer needs additional resiliency to survive the loss of two nodes concurrently.
Which configuration should the consultant use to ensure that the appropriate resources are available?
- A . Storage reservation for 10%; HA admission control for 10%, cluster RF3
- B . Storage reservation for 5%; HA admission control for 5%, cluster RF2
- C . Storage reservation for 5%; HA admission control for 5%, cluster RF3
- D . Storage reservation for 10%; HA admission control for 10%, cluster RF2
An administrator needs to create and start five new VMs for a Data Analytics Project (OLAP).
The VM Profile is as follows:
• vCPU:4
• vRAM: 64 GB
• vDisk: 1.5 TB
Each of the four nodes of the Nutanix cluster has the following:
• 24 vCPU. 20% overall usage
• 192 GB RAM, 60% overall usage
• 2xl920GBSSD
• 4x 2 TB HDD
At cluster level, there is a single RF2 container that is 30% utilized and has an extent store capacity of 13.5 TB.
Which component requires administrator attention?
- A . Physical RAM, because it is not enough to power on all of the new VMs.
- B . Physical Cores, because they are not enough to power on all of the new VMs.
- C . Storage, because the capacity is not enough to create VMs.
- D . Flash Tier because it is not enough to accommodate the workloads.
An administrator receives an alert in Prism indicating that interface eth2, on an AHV host is receiving many CRC errors.
After togging into the problematic host, the following command is run to show the indicated output:
What is causing this issue?
- A . Incorrect link speeds on the switch
- B . The interface is incorrectly configured with Jumbo Frames
- C . A misconfigured bond
- D . A physical layer network problem
B
Explanation: Ref:
rx_crc_errors are caused either by faults in layer 1 (in the past, we have seen failed twinax cables and incorrect types of fibre being used), or issues with jumbo frames on the network. In an environment with 10Gig switches that use cut-through forwarding (Cisco Nexus, Arista, Cisco devices using IOS default to Store and Forward switching), any packets that come into the switch will get forwarded out the destination interface once the switch has read the destination MAC address. If that packet has an MTU over what is configured on the interface, it will cut off the packet at the designated MTU, causing the server to receive a malformed packet, which will throw a CRC error.
If you have a layer 1 issue, you will see rx_crc_errors, not on all but one or two nodes.
Refer to the exhibit.
After performing ESXi to AHV conversion on a cluster, the alerts shown in the exhibit display on Prism .
What should the administrator do to resolve this issue efficiently?
- A . Remove the VMs. create a new Protection Domain, and add VMs to it
- B . Remove VMs from the Protection Domain and add them back in.
- C . Delete the Protection Domain, create a new Protection Domain, and add the VMs to it
- D . Create a new Protection Domain and add the VMs to rt.
An administrator is updating disk firmware using LCM and receives the following message:
“there have been 10 or more cluster services restarts within 15 minutes in the Controller VM”
The message appears as each drive is upgraded.
What is the reason this message is being generated?
- A . A node has been rebalanced
- B . A drive has been reformatted
- C . A node has been rebooted
- D . A drive has been ejected
C
Explanation:
Ref: https://portal.nutanix.com/page/documents/kbs/details?targetId=kA032000000TT8DCA W
A guest VM is reported to have poor storage performance. It has an I/O profile of 80%read.
20% write, and the HDDs form more than 50% of the read source.
What should an administrator do to resolve this issue?
- A . Increase SSD capacity
- B . Increase the OPLOG
- C . Increase the write cache
- D . Use HDDs with higher RPM
A
Explanation:
Ref: https://portal.nutanix.com/page/documents/solutions/details?targetId=BP-2126-SAS-on-Nutanix:BP-2126-SAS-on-Nutanix
While creating an image placement policy on the organizations AOS 5.15-based Nutanix cluster, the administrator wants to ensure there are no restrictions on using the selected images on clusters outside of the identified set.
What type of Policy Enforcement must the administrator choose?
- A . Soft
- B . Internal
- C . Hard
- D . External
A three-node cluster has a Nutanix Files instance with three FSVMs.
What happens after a node failure?
- A . The affected FSVM will get live-migrated to another node.
- B . The affected FSVM will not be restarted on another node due to its agent VM setting.
- C . The affected FSVM will not be restarted on another node due to its VM-to-VM anti-
affinity settings. - D . The affected FSVM will be restarted on another node.
D
Explanation:
Ref: https://portal.nutanix.com/page/documents/details?targetId=Files-v3_6:fil-files-high-availability-c.html
An administrator receives reports that VDI desktop performance in an 8-nodeNutanix VDI environment is poor. Opening applications takes between 1 and 2 minutes.
When investigating the issue, the following conditions are found:
• Cluster memory utilization: 80%
• Cluster SSD utilization: 70%
• Average VM CPU Wait Time: 11% • CVM CPU utilization: 75%
Which action should be taken to improve VDI performance?
- A . Increase the amount of SSD storage in the cluster.
- B . Add memory to the nodes in the cluster.
- C . Add CPU resources to the cluster.
- D . Increase the number of vCPU cores allocated to the CVM.
After a recent installation using a flat switch, a consultant notices issues migrating the Nutanix nodes to the customer’s network. The customer states that they are using VLANs on the production switch but not on the dedicated switch for IPMI. The customer does not require a manual configuration of the host and CVM.
What network changes need to be made to correct the issues?
- A . Us untagged VLANs for the CVM and host and trunk mode for IPMI.
- B . Use Native VLANs for the CVM and host and access mode for IPMI.
- C . Use tagged VLANs for the CVM and host and access mode for IPMI.
- D . Use Native VLANs for the CVM and host and trunk mode for IPMI.
A customer is deploying Nutanix AHV clusters over hundreds of remote sites worldwide. Prism Central will be used to centrally manage all clusters. Customer security policy requires the use of MS Active Directory (AD). groups to authenticate all network devices.
Which method should be consultant use to meet the requirements?
- A . Integrate AD authentication on all CVMs.
- B . Integrate AD authentication on Prism Central Only.
- C . Proxy Prism Element traffic through Prism Central.
- D . Integrate AD authentication on all Prism Element Clusters.
A customer buys ultimate licensing and wants to use the built-in Nutanix software encryption on their new AHV cluster. The customer needs to create three storage containers and asks the consultant to complete the process as fast as possible.
In which order should the cluster be deployed?
- A . Create Cluster -> Install License Key -> Encrypt Cluster -> Create Storage Containers
- B . Create Cluster -> Install License Key -> Create Storage Containers -> Encrypt Cluster
- C . Create Cluster -> Encrypt Cluster -> Install License Key -> Create Storage Containers
- D . Create Cluster -> Create Storage Containers -> Encrypt Cluster -> Install License Key
An administrator needs to deploy an application with a large amount of data connected via Nutanix Volumes.
Which two actions should the administrator take when designing the Volume Group? (Choose two.)
- A . Use multiple subnets for iSCSI traffic
- B . Enable RSS (Receive Side Scaling)
- C . Enable thick provisioning on the Volume Group(s)
- D . Distribute workload across multiple virtual disks
To prepare for a new Nutanix installation, a consultant downloads the Foundation VM, imports the VM to their Desktop Virtualization Solution, and powers on the VM. The IPv4 static address on the host workstation and the Foundation VM have been configured, but pings between them fail.
Which two troubleshooting steps should the consultant perform? (Choose two.)
- A . Remove and re-import the Foundation VM to ensure the virtual NIC is set to Host-Only.
- B . Verify the virtual NIC in the Foundation VM is bound to the correct physical Host adapter.
- C . Confirm the IP addresses and subnet masks are correct.
- D . Verify the virtual NIC in the Foundation VM is bound to the correct wireless network adapter.
Microsegmentation was recently enabled in a Nutanix environment. The administrator wants to leverage Prism Central to create a policy that will block all traffic, regardless of direction, between two groups of VMs identified by their category.
Which policy should be used to meet this requirement?
- A . A Quarantine Policy
- B . AnIsolation Environment Policy
- C . An Application Security Policy
- D . A Whitehst-Based Policy
An administrator is configuring software only. Data-at-Rest Encryption on their Nutanix cluster. They are planning to deploy a third-party key management server (KMS).
Where should this server be hosted?
- A . As a single VM on the Nutanix cluster
- B . On hardware external to the Nutanix duster
- C . As a clustered VM setup on the Nutanix cluster
- D . As a single VM deployed on the host that contains the Prism leader CVM
Refer to the exhibit.
An administrator logged into Prism Element, notices the following in the home dashboard, and showing the exhibit.
Which action should the administrator take next?
- A . Configure the fqdn for the hosts indicated
- B . Troubleshoot the zookeeper server issue
- C . Re-run NCC specifying data_resiliency_check
- D . Check the hardware page for disk failures
After finishing foundation on an AHV cluster, a consultant is preparing to plug into the customer network given the following set of requirements:
* All network traffic on trunks is tagged
* Customer is using LACP
* A native VLAN is not in use
Which set of commands should the consultant use to ensure cluster connectivity on customer equipment?
- A . change_cvm_vlan 0
ovs-vsctl set port br0 tag=0 ovs-vsctl set port br0-up bond_mode=balance-tcp B.
change_cvm_vlan 10
ovs-vsctl set port br0 tag=10 ovs-vsctl set port br0-up bond_mode=balance-tcp C.
change_cvm_vlan 0
ovs~vsctl set port br0 tag=0
ovs~vsctl set port br0-up bond_mode=active-backup D.
change_cvm_vlan 10
ovs-vsctl set port br0 tag=10
ovs-vsctl set port br0-up bond_mode=balance-slb
An administrator migrates a VM onto a new Nutanix cluster.
After the migration, the administrator observes the following conditions:
• Cluster memory utilization: 64%
• Cluster CPU utilization: 19%
• Cluster storage utilization: 32%
• Average VM CPU utilization: 25%
• Average VM CPU ready%: 24%
• Average VM memory utilization: 60%
Which two changes should the administrator make to improve VM performance? (Choose two.)
- A . Add more memory to the VMs.
- B . Reduce the number of vCPUs assigned to VMs.
- C . Replace high core count CPUs with high clock rate CPUs. (also can be but is physical invas)
- D . Reduce the number of VMs on the hosts.
B,D
Explanation:
refhttp://www.joshodgers.com/tag/cpu-ready/
An administrator needs to migrate workloads from a Nutanix cluster running VMware ESXi to Nutanix AHV. The migration process needs to be completed in multiple VM groups and support roll back in caseany problems are found during user acceptance testing.
Which action should the administrator perform?
- A . Use Cross Hypervisor DR to replicate VMs from ESXi to AHV
- B . Use VMware Converter
- C . Use Nutanix one-click cluster conversion from ESXi to AHV
- D . Usestorage live migration
C
Explanation: Ref: https://next.nutanix.com/installation-configuration-23/convert-existing-nutanix-vmware-cluster-to-nutanix-only-37600
A customer is running out of storage in an ESXi cluster. The customer wants to add storage without paying for an additional hypervisor license.
Which option should the consultant recommend to meet the requirement?
- A . Convert the cluster to AHV to support storage-only node requirements.
- B . Select the storage-only checkbox during Foundation and then expand the cluster in Prism.
- C . Buy a new node to meet the requirements of the storage-only node specifications.
- D . Edit the factory_config.json file to configure the node as storage-only and then expand the cluster in Prism
A VDI environment based on AHV Cluster is not performing well. The current environment is using only one bridge (Bridge0). The administrator needs to verify if nodes are using all network cards associated to Bridge0.
Which two menus should be used to check the current configuration? (Choose two.)
- A . Network Configuration item in Settings menu
- B . Host view in Network menu
- C . Host NICs tab in Hardware menu
- D . I/O Metrics tab in VM menu
A consultant successfully installs the Foundation VM on a laptop and needs to ensure the VM can communicate externally.
Which two configuration changes should the consultant make next? (Choose two.)
- A . Ensure the vNIC is set to bridged adapter.
- B . Configure the static IP address through the desktop virtualization software.
- C . Open terminal and configure via ifconfig command.
- D . Run the set_foundation_ip_address application on the VM desktop.
An administrator is responsible for the following Nutanix Enterprise Cloud environment:
• A central datacenter with a 20-node cluster with 1.5PB of storage
• Five remote sites each with a 4-node cluster with 200TB storage
The remote sites are connected to the datacenter via 1GB links with an average latency of 6 ms RTT .
What is the minimum RPO the administrator can achieve for this environment?
- A . 0 minutes
- B . 15 minutes
- C . 1 hour
- D . 6 hours
B
Explanation:
Ref: https://support-portal.nutanix.com/page/documents/details?targetId=Web-Console-Guide-Prism-v5_10:wc-protection-domain-wc-c.html
A customer with a four-node RF2 cluster is adding application VMs to their system. After adding these VMs, the Prism dashboard shows 81% storage utilization.
What is the consequence of running the cluster at 81% storage utilization?
- A . The customer has the ability to add more VMs up to the 100% storage utilization.
- B . There is available capacity in the storage fabric and the cluster is resilient.
- C . Node failure is imminent due to storage utilization.
- D . The cluster is not resilient in the storage fabric
D
Explanation: https://next.nutanix.com/how-it-works-22/recommended-maximum-storage-utilization-37234
An administrator receives an error indicating that the CVMs in the cluster are not syncing to any NTP servers.
An investigation of the issue finds:
• The NTP servers are configured in Prism
• The time on all CVMs is the same
• Both the CVMs and AHV hosts are configured for the UTC time zone.
Which two steps can be taken to troubleshoot this issue? (Choose two.)
- A . Confirm that the NTP servers are reachable from the CVMs.
- B . Restart genesis on all CVMs.
- C . On a CVM. run the command a Hash ntpq -pn.
- D . Restart the chronos service on all CVMs.
A,C
Explanation:
Ref: https://portal.nutanix.com/page/documents/kbs/details?targetId=kA032000000bmjeCAA#Review_ntpq
A customer needs a DR solution designed around the following requirements:
• There are 8 ms of latency between Sites A and B
• The administrator needs the shortest RPO/RTO possible
• Application consistent snapshots are required
• Use of NutanixVSS
Which Data Protection Method should be used?
- A . Async
- B . Metro Availability
- C . Near Sync
- D . Cloud Connect
C
Explanation:
Ref: https://portal.nutanix.com/page/documents/details?targetId=Prism-Element-Data-Protection-Guide-v5_18:wc-dr-application-consistent-snapshots-wc-r.html
After installation, network ports are properly configured with the default active-backup bonding.
One 10GbE port goes to switch 1. Another 10GbE port goes to switch 2. A consultant tests failover by manually pulling one of the cables and notices it is taking too much time to failover, which is causing excessive packet loss.
What should the consultant enable to resolve this issue?
- A . LACP on switch
- B . PAgP
- C . Portfast
- D . Jumbo frames
During a technical call with a customer, it is identified that this installation will be software only on Dell servers. The out-of-band management interfaces will not be given IP addresses until the consultant is onsite.
Which Foundation method should be used for this type of installation?
- A . Bare metal using iDRAC MAC addresses.
- B . Bare metal using LAN MAC addresses.
- C . Bare metal using block serial numbers.
- D . Bare metal using node serial numbers.
An administrator is deploying a three-tier application on a Nutanix Enterprise Cloud consisting of web, application, and database VMs. Traffic between the servers must be limited to specific services/ports. There is an application layer firewall VM deployed on one host in the cluster.
In which way should the administrator meet this requirement?
- A . Create a network for each type of VM, and use policy-based routing to control the traffic flow
- B . Configure a security policy and service chain redirecting the server traffic through the firewall
- C . Separate the web. application and database VMs on to dedicated VLANs
- D . Categorize the VMs in Prism Central and utilize Flow to set a security policy
An administrator is deploying an application using Nutanix Volumes. After configuring the volume group and connecting the guest’s iSCSI initiator to the volume group, they begin performance testing.
The administrator learns that performance on the virtual disk attached to the iSCSI initiator is far less than that of a virtual disk connected directly to the VM.
Which situation is causing this condition?
- A . The VM’s iSCSI traffic is being routed to the data services IP subnet
- B . The performance test is generating small block random 10.
- C . The duster data services IP address is a bottleneck, shared with other iSCSI traffic
- D . Data Locality ensures that VM attached disks are always faster than iSCSI volumes.
A consultant needs to verify the make and model of the systems that will be imaged with Foundation. The consultant does not have the Bill of Materials (BOM) available to review.
When should the consultant verify the make and model to prepare for the cluster deployment?
- A . During the Foundation Process
- B . While conducting the Tech Review Call
- C . Upon arriving on-site
- D . When reviewing the Statement of Work (SOW)
Refer to the exhibit.
An administrator notices a critical alert on the Metro Availability Protection Domain
What is causing this alert?
- A . Metro Availability Protection domain is active on the remote site.
- B . VMware Site Recovery Manager is handling a failover event
- C . Metro Availability did not fail over and caused an outage.
- D . vSphere moved VMs to the remote container, and the VMs must be moved back.
A
Explanation:
Ref: https://www.vvlsystems.com/wp-content/uploads/2016/11/BP-2009_Metro_Availability.pdf
An administrator has a 32-node hybrid cluster with CPU, RAM and storage utilization of 80%. A database VM is configured with VM Flash.
What is causing this IO latency?
- A . Controller VM is experiencing high CPU ready time.
- B . Curator scans causes by ILM constantly moving data.
- C . VM Flash Mode reduces SSD tier capacity for VMs.
- D . Database VM is experiencing high CPU ready time.
A company needs to replicate their VMs to a remote site and must have an RPO of less than 1 hour.
When creating a protection domain, what should an administrator do to meet this requirement?
- A . Enable Async Replication with an RPO of 60 minutes
- B . Enable Near-Sync Replication with an RPO of 15 minutes
- C . Enable Entity Sync on the designated VMs
- D . Enable Availability Zones and send the VM to multiple targets
A
Explanation:
Ref: https://portal.nutanix.com/page/documents/details?targetId=Web-Console-Guide-Prism-v5_10:sto-pd-guidelines-r.html