An administrator successfully installed Objects and was able to create a bucket.
When using the reference URL to access this Objects store, the administrator is unable to write data in the bucket when using an Active Directory account.
Which action should the administrator take to resolve this issue?
- A . Verify sharing policies at buckets level.
- B . Verify Access Keys for the user.
- C . Replace SSL Certificates at Objects store level.
- D . Reset Active Directory use’s password
B
Explanation:
If the administrator is unable to write data in the bucket using an Active Directory account, the issue is likely related to incorrect or missing access keys for the user. Access keys are required to authenticate and authorize access to the Objects store. The administrator should verify the access keys associated with the Active Directory account and ensure they are correctly configured.
An existing Objects bucket was created for backups with these parameters:
A) WORM policy of three years
B) Versioning policy of two years
C) Lifecycle policy of two years
The customer reports that the cluster is nearly full due to backups created during a recent crypto locker attack. The customer would like to automatically delete backups older than one year to free up space in the cluster.
How should the administrator change settings within Objects?
- A . Modify the existing bucket lifecycle policy from two years to one year.
- B . Create a new’ bucket with the lifecycle policy of one year.
- C . Create a new’ bucket with the WORM policy of two years.
- D . Modify the existing bucket WORM policy from three years to one year.
A
Explanation:
According to Nutanix documentation on unified storage (NCP-US) v6, to automatically delete backups older than one year, an administrator should modify the existing bucket lifecycle policy to set the expiration period to one year. Lifecycle policies enable administrators to automate the transition of objects to different storage classes and to expire them altogether. In this scenario, modifying the existing bucket lifecycle policy to shorten the expiration period to one year will ensure that backups older than one year are automatically deleted to free up space in the cluster. https://portal.nutanix.com/page/documents/details?targetId=Objects-v3_1:v31-lifecycle-policies-rule-c.html
An administrator has mapped a Volume Group named VGI to a VM, Due to changes in the application running inside the VM, two additional volumes are required. At the time of creation, the VM was assigned to a Protection Domain named PDI.
Which two steps should the administrator take to add the additional volumes to the VM while maintaining data protection? (Choose two.)
- A . Add the new vDisks to the same Consistency Group.
- B . Add two additional vDisks to VG1.
- C . Map the new vDisks as volumes to the VM.
- D . Manually update PD1to include the newly created vDisks.
B,C
Explanation:
To add additional volumes to the VM while maintaining data protection, the administrator should add two new vDisks to the Volume Group (VG1) and map the new vDisks as volumes to the VM. This will allow the VM to access the additional storage while keeping the data protected in the Protection Domain (PD1).
An administrator has mapped a Volume Group named VGI to a VM, Due to changes in the application running inside the VM, two additional volumes are required. At the time of creation, the VM was assigned to a Protection Domain named PDI.
Which two steps should the administrator take to add the additional volumes to the VM while maintaining data protection? (Choose two.)
- A . Add the new vDisks to the same Consistency Group.
- B . Add two additional vDisks to VG1.
- C . Map the new vDisks as volumes to the VM.
- D . Manually update PD1to include the newly created vDisks.
B,C
Explanation:
To add additional volumes to the VM while maintaining data protection, the administrator should add two new vDisks to the Volume Group (VG1) and map the new vDisks as volumes to the VM. This will allow the VM to access the additional storage while keeping the data protected in the Protection Domain (PD1).
63 TiB storage
The total target workload requests are:
5 Ghz CPU
10 GB RAM
40 TiB storage
What should be changed to have a good capacity runway at least for the next 6 months?
- A . Review storage capacity requested by the workload.
- B . Increase the storage capacity for physical nodes.
- C . Add new physical node to the configuration.
- D . Change the date of physical rode availability.
A
Explanation:
According to the Nutanix Support & Insights website1, capacity runway is an estimate of how long your cluster can support its current workload before running out of resources2. The exhibit shows that your cluster has a storage runway of only 1 month, which means you will run out of storage space soon. However, your CPU and memory runways are much longer (more than 2 years), which means you have plenty of CPU and memory resources available. Therefore, it might be possible to reduce the storage capacity requested by your workload or optimize your storage utilization to extend your storage runway. Alternatively, you could also increase the storage capacity for physical nodes or add new physical nodes to the configuration, but these options might be more costly and complex.
When completing the Linux Client iSCSI discovery process of the Nutanix cluster Volumes target, which action should an administrator complete first?
- A . Ensure the iSCSI is started.
- B . Restart iSCSI service on CVM.
- C . Discover the Volumes target.
- D . Establish connection to the Volumes target.
A
Explanation:
To use Nutanix Volumes with Linux clients, you must install and configure an iSCSI initiator on each client.” Therefore, the administrator should ensure that the Iscsi service is started on the Linux client before discovering or connecting to the Volumes target.
https://next.nutanix.com/installation-configuration-23/data-services-ip-iscsi-33804
An administrator is building a new application server and has decided to use post-process compression for the file server and inline compression for the database components.
The current environment has these characteristics:
Two Volume Groups named VGI and VG2.
A Storage Container named SCI with inline-compression.
A Storage Container named SC2 with post-process compression.
Which action should the administrator take to most efficiently satisfy this requirement?
- A . Wfithin VG1, create one vDisk in SC1 and one vDisk in Sc2.
- B . Within SC1, create one Wisk in VG1 and within SC2. create one Disk in VG2
- C . Wthin SC1, create one vDisk in VG1 and one vDisk in VG2,
- D . Writhin VG1, create one vDisk in SC1 and within VG2, create one vDisk in SC2.
D
Explanation:
Volume Groups (VGs) are collections of vDisks that can be attached to VMs1. vDisks are virtual disks that reside on Storage Containers2. Storage Containers are logical entities that provide storage services with different compression options3.
To use post-process compression for the file server and inline compression for the database components, you need to create two vDisks on different Storage Containers with different compression options. Then you need to attach those vDisks to different VGs.
https://next.nutanix.com/volumes-block-storage-171/configuration-for-volumes-vdisks-40537
Which Nutanix interface is used to deploy a new Files instance?
- A . Prism Element
- B . Prism Central
- C . Files Manager
- D . Life Cycle Manager
B
Explanation:
According to Nutanix Support & Insights1, Nutanix Files is a scale-out file storage solution that provides SMB and NFS file services to clients. Nutanix Files instances are composed of a set of VMs (called FSVMs) that run on Nutanix clusters.
According to Your Complete Guide to Nutanix Files Training Resources2, Prism Central is the interface used to deploy a new Files instance. Prism Central is a centralized management console that provides visibility and control across multiple Nutanix clusters and services.
An administrator has received multiple trouble tickets from users who are unable to access a particular Distributed share.
While troubleshooting, the administrator observes that data located on FSVM 3 can be accessed, but the data located on FSVMs 1 and 2 is inaccessible. The administrator receives this message when attempting to access data on FSVMs 1 and 2:
Network object not found
Both FSVM 1 and 2 nodes successfully reply to pings, and the administrator is able to access data via the node IP.
What must the administrator check as a next step?
- A . Check if all DNS records are created on the DNS server.
- B . Check if SM3v1 is enabled on FSVM node 1 and 2.
- C . Check ifkeberos_time_skewis logged on the client.
- D . Check if user permissions are configured correctly.
A
Explanation:
According to Nutanix Support & Insights1, a distributed share is a type of SMB share that distributes the hosting of top-level directories across FSVMs. To access a distributed share, you need to use a DNS name that resolves to all FSVMs in the cluster. If some DNS records are missing or incorrect, then some FSVMs may not be reachable by their DNS name, resulting in the network object not found error. This could explain why data located on FSVM 3 can be accessed, but data located on FSVMs 1 and 2 is inaccessible.
During a recent audit, the auditors discovered several shares that were unencrypted. To remediate the audit item, the administrator enabled Encrypt SMB3 Messages on the accounting, finance, and facilities shares. After encryption was enabled, several users have reported that they are no longer able to access the shares.
What is causing this issue?
- A . The users are accessing the shares from Windows 8 desktops.
- B . Advanced Encryption Standard 128 & 256 are disabled in Windows 7.
- C . Advanced Encryption Standard 128 & 256 are disabled in Linux or Mac OS.
- D . The users are accessing the shares from Linux desktops.
C
Explanation:
The issue causing the users to be unable to access the shares after enabling encryption (Encrypt SMB3 Messages) is likely related to the fact that Advanced Encryption Standard 128 & 256 are disabled in Linux or Mac OS. These operating systems may not have the required encryption standards enabled by default, leading to compatibility issues with the encrypted shares. Enabling the appropriate encryption standards on Linux or Mac OS should resolve the issue
An administrator has deployed an SMB v3 Files cluster, but needs to make the cluster able to support Multi-protocol access,
Which protocol will be native?
- A . NFS
- B . S3
- C . SMB
- D . cifs
C
Explanation:
According to the Nutanix Files SMB Migration Guide1, Nutanix Files supports SMB protocol V2 and V31. SMB is a native protocol for Nutanix Files that allows file sharing between Windows clients and servers1.
While preparing for migrating data from a legacy storage environment to a new Files scale-out file server, the administrator make the following notes:
Requirements:
Number of home directories: 4000
Number of Departmental shares: 1
Everyone is permitted to accessing it
All users use the same Departmental share
The administrator deploys Files using the following configuration:
Number of FSVMs: 3
VCPU & RAM/FSVM: 4VCPU,12GB
One Distributed share with SSR & ABE enabled for the Home Directories
One Standard share for the Departmental share
Does this configuration satisfy the project’s requirements?
- A . No, the project needs two distributedShare4 FSVMs. 6 vCPU & 326B RAM
- B . Yes, the listed configuration elements satisfy the requirements.
- C . No, the project needs two distributed 4 FSVMs, 24 vcpu & 128GB RAM
- D . No, the project needs 4 FSVMs 4 vCPU & 12GB RAM.
B
Explanation:
According to the scenario, the administrator is preparing to migrate data from a legacy storage environment to a new Files scale-out file server in a way that meets the following requirements:
✑ Number of home directories: 4000
✑ Number of Departmental shares: 1 ✑ Everyone is permitted to access it
✑ All users use the same Departmental share
The administrator deploys Files using the following configuration:
✑ Number of FSVMs: 3
✑ VCPU & RAM/FSVM: 4VCPU, 12GB
✑ One Distributed share with SSR & ABE enabled for the Home Directories ✑ One Standard share for the Departmental share
Based on this configuration, it appears that the project’s requirements are satisfied. The configuration provides a Distributed share for the home directories, which is recommended when there is a large number of files or directories, and this will distribute the load across multiple FSVMs. Note that everyone is permitted to access it.
In addition, the configuration provides a Standard share for the Departmental share, and since all users use the same Departmental share, this will not create any performance issues. Therefore, the correct answer is B, ‘Yes, the listed configuration elements satisfy the requirements’.
A CIO has been reviewing the corporate BCDR plan. In this review, the CIO has noticed that they are replicating their Files deployments using the built in Files DR capabilities that are configured out of the box.
Upon further investigation, the CIO has identified that there are no granular share replications between their Files deployments and has requested the administrator to take an initiative and implement a granular Files Share recovery model.
Which Files capability should the administrator configure in order to be able to failover only certain shares?
- A . Data Lens
- B . Smart DR
- C . Smart Tiering
- D . NC2 on AWS
B
Explanation:
Smart DR enables granular recovery of individual file shares in Nutanix Files by replicating data at the share level. This allows for more fine-grained control over the failover process and ensures that only critical data is recovered in the event of a disaster or outage.
Files Smart DR is a feature that allows you to replicate between Files instances, either on-premises or running on Nutanix Cloud Clusters on AWS1. With Files Smart DR, you can configure granular share replication, which means you can select which shares to replicate and which ones to exclude1. Therefore, the correct answer to your question is B. Smart DR.
Files Smart DR also supports replicating snapshots between the source share and its target, which can help with data recovery and compliance2. Additionally, Files Smart DR is the mechanism by which Files will support disaster recovery in the Nutanix Xi cloud3.
Which administrator action within Files will enable the monitoring of users’ files for malware and viruses?
- A . Install antivirus on a server and mount the share for scan.
- B . Connect to an ICAP server.
- C . Install ClamAV on each FSVM,
- D . Leave the threat detection to the local machine’s antivirus application.
B
Explanation:
ICAP stands for internet content adaption protocol and it is a standard protocol that allows you to integrate file servers with security products. Nutanix Files supports third-party vendors that use ICAP servers to scan files for malware and viruses. https://www.nutanix.com/sg/support-services/training-certification/certifications/certification-details-nutanix-certified-professional-unified-storage-v6
An administrator needs to analyze data created by a custom application, which writes data into an SMB share hosted on Files. This application uses custom-built file extensions such as .zyx, . zzz,theadministrator needs to provide a collapsed view of space usage, number of files, and changes within a given time frame.
How should the administrator provide the required information?
- A . Go to Files, select the share used by the application and point to Usage View.
- B . Add a new’ file category in File Analytics and use File Distribution View,
- C . Configure SNMP server with Nutanix MIBS and use Excel to analyze traps.
- D . Create a File Server Resource Manager MMC and use File Screens,
B
Explanation:
According to File Auditing and Analytics for your Nutanix Files Enterprise Cloud1, File Analytics is a feature that captures real-time user audit data and file metadata for Nutanix Files environments. It allows you to create custom reports based on various criteria such as file type, size, owner, access time, etc.
According to Nutanix Files 3.8 and File Analytics 3.0 | Nutanix Community2, File Analytics allows you to add new file categories based on custom file extensions such as .zyx or .zzz. You can then use File Distribution View to see a collapsed view of space usage, number of files, and changes within a given time frame for each file category.
Therefore, if the administrator needs to analyze data created by a custom application that uses custom-built file extensions such as .zyx or .zzz, they can add a new file category in File Analytics and use File Distribution View to provide the required information.
The Compliance department would like the administrator to have the ability to revert documents to previous versions.
How should the administrator facilitate this request?
- A . Configure Protection snapshots on the File Server.
- B . Enable Self-Service Restore on the Share/Export.
- C . Configure Protection snapshots on the Share/Export.
- D . Enable Self-Service Restore on the File Server
C
Explanation:
Protection snapshots are external snapshots that can be used to recover the file server cluster or individual files and folders1. They can be created through a protection domain schedule or via a user-initiated one-time snapshot of the protection domain1. By configuring protection snapshots on the share/export, the administrator can enable self-service restore for users to revert documents to previous versions2. https://portal.nutanix.com/page/documents/solutions/details?targetId=TN-2041-Nutanix-Files%3ATN-2041-Nutanix-Files
A developer has finished developing a new eCommerce site that is broken out into several different Kubernetes pods. In order to promote the new application to production, a storage location for static content that the site uses needs to be defined in the file.
Application requirements:
versioning
WORM
Replication
Which solution should the administrator choose?
- A . Objects
- B . Volumes
- C . Files with SMB
- D . Files with NFS
A
Explanation:
Object storage is a good fit for applications that require versioning, replication, and a write-once-read-many (WORM) access model. Since eCommerce sites
often store a large amount of unstructured data such as images, videos, and other multimedia content, object storage can provide a scalable, cost-effective, and highly available solution.
Object storage is also a good fit for Kubernetes-based applications that use microservices architecture, as objects can be accessed from multiple pods at the same time, without the need for complex file system sharing. Additionally, object storage can be easily integrated with Kubernetes using operators or API calls.
On the other hand, while volumes and file storage solutions such as SMB and NFS can also store static content, they may not be the best fit for the given application requirements. Volumes are often limited in terms of scalability and replication, while file storage solutions may not provide the same level of versioning and WORM capabilities as object storage. As a result, the best solution for the given application requirements is Object storage.
Note that the exact implementation and configuration of the object storage solution may vary based on factors such as performance, availability, and security requirements. https://next.nutanix.com/community-blog-154/maintaining-compliance-with-worm-for-nutanix-objects-33239
Refer the exhibit.
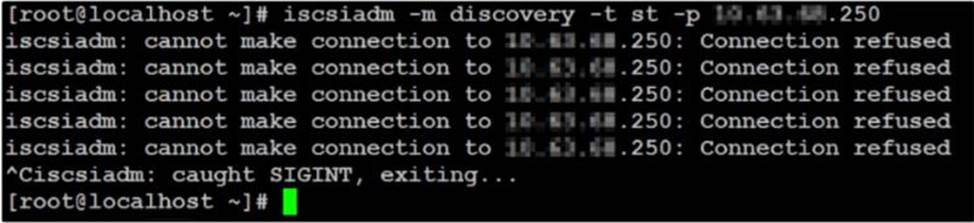
An administrator has received a support request indicating that after an update and reboot Of a Linux VM, the VM is no longer able to access the Volume Groups (VG) assigned to it.
When the administrator investigates the issue, the error message shown in the exhibit is displayed.
What are two possible reasons for the behavior? (Choose two.)
- A . The newiscsiadmbinary is not compatible with the version.
- B . The administrator has a mistake wheninputtingthe data services IP.
- C . Afirewallrule ispreventing theclient to access the x.x.x.250 IP.
- D . Theclient’s IQNis no longer in the whitelist of the affected VG
B,D
Explanation:
iscsiadm is a command-line tool that allows you to manage iSCSI connections and devices. The error message shown in the exhibit indicates that there is a problem with connecting to the iSCSI target at x.x.x.250. https://stackoverflow.com/questions/29954195/error-message-from-iscsiadm-while-trying-to-connect-to-a-iscsi-drive
Nutanix volume groups are collections of vDisks that can be exposed to virtual machines or physical hosts using iSCSI protocol. Nutanix volume groups have a whitelist feature that allows you to specify which clients can access them. https://portal.nutanix.com/page/documents/solutions/details?targetId=BP-2049-Nutanix-Volumes:BP-2049-Nutanix-Volumes
✑ B. The administrator has a mistake when inputting the data services IP. This could cause the iscsiadm command to fail to discover or login to the iSCSI target at x.x.x.250. The administrator should verify that they have entered the correct data services IP for the Nutanix volume group.
✑ D. The client’s IQN is no longer in the whitelist of the affected VG. This could cause the iSCSI target to reject or ignore the connection request from the client. The administrator should check that they have added or updated the client’s IQN in the whitelist of the Nutanix volume group.
An administrator needs to ensure objects in a bucket expire after a certain period of time.
Which Objects feature will satisfy this requirement?
- A . WORM bucket
- B . Object versioning
- C . Lifecycle polices
- D . Protection policies
C
Explanation:
According to Nutanix documentation on unified storage (NCP-US) v6, Lifecycle policies enable administrators to ensure that objects in a bucket expire after a certain period of time. You can set rules to automate the transition of objects to different storage classes or to expire them altogether. This feature helps to manage storage costs by reducing the need to manually manage data retention policies for individual objects in a bucket.
Lifecycle policies allow you to define rules for automatically deleting or archiving objects in a bucket after a certain period of time1. This feature can help you reduce storage costs and manage data retention.
An administrator needs to deploy Files Analytics (FA). After logging into the Prism management console using personal credentials, the administrator is not able to deploy the Virtual Appliance.
What action is needed to resolve this issue?
- A . Download the FA Virtual Appliance.
- B . Move FA to another storage container.
- C . Perform FA deployment in Prism Central,
- D . Deploy FA using the Prism admin useraccount.
D
Explanation:
To resolve the issue of not being able to deploy the Files Analytics (FA) Virtual Appliance after logging into the Prism management console using personal credentials, the administrator should deploy FA using the Prism admin user account. The Prism admin user account typically has the necessary privileges and permissions to perform administrative tasks, including deploying virtual appliances such as FA.
A two-VM Oracle RAC cluster was recently configured with Linux Red Hat using a Nutanix Volume Group. At the time Of performing the failover tests Of simulating a failure in each Of the three Nutanix cluster nodes, the cluster administrator noticed that tile virtual machines Of the RAC cluster do not come up and the failover fails.
The administrator must to follow the best practices from Nutanix to construct the RAC
cluster using AHV.
What should the administrator Veri’/ in the Steps performed to configure the RAC cluster to prevent this situation from occurring again?
- A . In the step for attach the volume group to the RAC VMs, he must create it with anattribute of shared = true
- B . useAntiaffinityrules to prevent multiple Oracle RAC nodes in the same RAC cluster fromrunning on same Nutanix node
- C . Changethe disk timeout to 60 (default 30) in the disk parameters for each linux device
- D . VM-host affinityrulesCan be Set up forRACVMS to definewhere theyCan runwithinthecluster
A
Explanation:
https://www.nutanix.com/architecture
Nutanix volume groups are collections of vDisks that can be exposed to virtual machines or physical hosts using iSCSI protocol. Nutanix volume groups have a shared attribute that allows multiple VMs to access them concurrently.
In the step for attach the volume group to the RAC VMs, he must create it with an attribute of shared = true. This is because if the volume group is not created with shared = true, then only one VM can access it at a time, which would prevent Oracle RAC from working properly.
A corporate compliance team has asked an administrator to stop using default passwords in the environment. The administrator needs to update the password used on the FSVM.
In which order should the administrator change the FSVM’s default password?
Task Step
Step 1
Step 2
step 3
Step 4
Select
Log onto a file server VM via SSH
Change the password
Respond to the prompts, providing the current and new Nutanix user password
Repeat the steps on the remaining FSVMs
A company decided to switch their existing Windows file server to a new Files instance. After successfully deploying Files. an administrator now needs to plan to reduce the impact of any potential outage. As the source file server resides across the WAN from the destination file server over an unreliable network connection.
The administrator needs to ensure there is minimal impact to data already copied, should a network outage occur.
How should the administrator meet this requirement?
- A . use Microsoft DFS-R to replicate the files.
- B . use a method allowing files to be copied in restartable mode.
- C . use rsync in incremental copy mode.
- D . Check where the data cog failed and restart from that location.
C
Explanation:
To update the password used on the FSVM (File Server VM), the administrator should follow the steps in the specified order. By logging onto each FSVM via SSH, changing the password, and repeating the steps for all FSVMs, the administrator can ensure that the default passwords are replaced with secure passwords.
Which setting should the administrator apply to a newly-created Objects bucket to ensure the requirements are met?
- A . Configure a Lifecycle Policy to overwrite one-year old data in the bucket.
- B . Apply an Object versioning policy with one-year retention.
- C . Configure the bucket WORM policy with a one-year retention,
- D . Apply a bucket Lifecycle Policy with a one-year expiration.
A company’s IT security policy requires that all network traffic must be secure, and no web browser certificate error warnings should be accepted by end users.
An administrator is tasked with configuring Objects so that it uses a certificate from an internal Certificate Authority (CA),
How should the administrator configure Objects to meet the security policy?
- A . Import the Private key and certificate files from the internal CA.
- B . Import the Private key with Subject Alternate Name of the company donmain.
- C . Regenerate the self-signed certificate with RSA 2048 as the bit type
- D . Regenerate the CSR and download certificates from the internal CA
A
Explanation:
To meet the security policy requirements, the administrator should import the Private key and certificate files from the internal CA into Objects. This ensures that Objects uses a certificate signed by the internal CA, eliminating web browser certificate error warnings and ensuring secure network traffic
A company has a number of thin clients which need to boot over the network. The company is using Volumes for this project.
Which component is needed to meet this requirement? (Choose two.)
- A . A compatibleEthernetadapter per client
- B . VM-attached VG with client iSCSIInitiator.
- C . A DHCP server pointing to the Nutanixcluster.
- D . A client with MPIO access to the VG
A,C
Explanation:
According to the Boot Over ISCSI article1, to boot an operating system over iSCSI for physical servers using Nutanix Volumes, you need to configure the network adapter BIOS settings to enable this feature1. You also need a DHCP server pointing to the Nutanix cluster that provides the iSCSI LUN1.
Based on this information, the components that are needed to meet this requirement are A. A compatible Ethernet adapter per client and C. A DHCP server pointing to the Nutanix cluster.
An administratorreceivea warning message concerning a file server hosted in a 3-node cluster. On the Files Console Dashboard tab, the file server displays a warning to recommend performance optimization,
How should the administrator resolve this issue?
- A . Increase the CVM’s CPU and RAM.
- B . Scale up the FSVM’5 resources.
- C . Scale out adding a new FSVM in the cluster.
- D . Apply the recommendation to rebalance,
D
Explanation:
Nutanix Files can automatically rebalance data across FSVMs to optimize performance and capacity utilization. You can also manually trigger a rebalance from the Files Console Dashboard tab by clicking on Apply Recommendation.https://next.nutanix.com/community-blog-154/nutanix-files-4-0-new-features-performance-improvements-40544