What are the three pillars of observability in DevOps? (Choose three.)
- A . traces
- B . errors
- C . metrics
- D . versions
- E . logs
A,C,E
Explanation:
https://www.dynatrace.com/resources/ebooks/three-pillars-of-observability/#:~:text=Observability%20is%20divided%20into%20three,called%20three%2 0pillars%20of%20observability.
What are three version control processes? (Choose three.)
- A . Subversion
- B . version
- C . Perforce
- D . revision
- E . Git
A customer was running a traditional application with the data being provided by an NetApp ONTAP NFSv3 export. The customer is now migrating that same application to run with a container in a Kubernetes environment using NetApp Trident.
In this scenario, how would the customer ensure that the new container-based application has access to the same data?
- A . Use the rsync command to copy the data to a worker node in the Kubernetes cluster and allow the kubelet to auto-discover the storage for the container.
- B . Import the volume using the tridentcti command and provide the corresponding persistent volume claim YAML.
- C . Define a backend YAML in Trident and use the kubectl command to create the backend in the Trident namespace.
- D . Define the connection information for the NFSv3 export in the storage class object and then reference the storage class in the persistent volume claim.
You are deploying persistent storage for Kubernetes with NetApp Trident.
In this scenario, what are the two objects that you must create? (Choose two.)
- A . Trident virtual storage pool
- B . Trident backend
- C . Kubemetes StorageCIass
- D . Trident volume
Using Astra Control, which three steps must be completed to protect your Kubernetes-based applications? (Choose three.)
- A . Set the snapshot retention.
- B . Set the snapshot schedule.
- C . Copy the protection. YAML file to the/etc/ directory.
- D . Choose the application to protect.
- E . Install the appropriate application agent
Your customer is running their Kafka and Spark applications inside a Kubernetes cluster. They want to create a single backup policy within Astra to automate the backup of both applications and all their related Kubernetes objects at the same time.
Which method in Kubernetes should be used to accomplish this task?
- A . Create a Helm chart that deploys Kafka and Spark and their related objects to multiple namespaces.
- B . Put the applications and their objects in a single namespace, or label all the objects with a single label that Astra can recognize.
- C . Create a Kubernetes custom resource definition that includes all of the objects that Astra needs to treat as a single entity.
- D . Use a single Trident-based StorageClass to provision all storage for Kafka and Spark.
Your organization is adopting DevOps techniques to accelerate the release times of your product. The organization wants to have more communication between teams, quick iterations, and a better method for training work in progress.
In this scenario, which three methodologies would you recommend? (Choose three.)
- A . waterfall
- B . agile
- C . kanban
- D . scrum
- E . iterative
You are using REST APIs to deploy and manage storage that is provided by NetApp Cloud Volumes ONTAP in Microsoft Azure. You have written a Python script that contains a POST request to the following URL: http://localhost/occm/api/azure/vsa/working-environments. However, you receive a 401 response failure message that indicates that the user is not authenticated.
In this scenario, which two steps must you perform to communicate with an endpoint? (Choose two.)
- A . Call an API endpoint with the JWT access token.
- B . Acquire a JWT access token from the OAuth token endpoint.
- C . Call an API endpoint with the refresh token.
- D . Acquire a refresh token from the OAuth token endpoint.
You have an AFF A400 system with NetApp ONTAP 9.8 installed. You want to configure the NetApp Cloud Tiering service to tier data to AWS object storage. The communication between your cluster and the AWS cloud needs to be encrypted. You have installed the FabricPool license, but your ONTAP cluster cannot reach the S3 bucket.
Which two configurations are causing the error? (Choose two.)
- A . You have not configured the TLS encryption.
- B . You have not configured your firewall to allow outbound traffic on port 443.
- C . You have not configured a LIF with a public IP address.
- D . You have not configured a LIF with the intercluster role.
What are two stages in the DevOps lifecycle? (Choose two.)
- A . plan
- B . architect
- C . operate
- D . destroy
You are asked to provision storage for a development team to make use of NetApp Trident in their Kubernetes environment. You want to ensure that Trident will not be able to exhaust the storage system resources.
In this scenario, which two actions would you take to satisfy the requirements? (Choose
two.)
- A . Limit the maximum volume count.
- B . Limit the available data LIFs.
- C . Use a shared SVM.
- D . Limit the maximum volume size.
You are researching different automation frameworks. One of the main features that you are seeking is the ability to provide an end state of what a particular environment should look like versus needing to define each step that is required to get to the end state.
In this scenario, which keyword should you be looking for as you research various automation frameworks?
- A . RESTful
- B . declarative
- C . interrogative
- D . imperative
You are working with your development team to automate the deployment of Cloud Volumes ONTAP instances across various hyperscalers. The developers are asking you for specific RESTful API calls and other details to facilitate the automation.
In this scenario, which two links would you provide to them? (Choose two.)
- A . the link to the API documentation on cloud.netapp.com
- B . the link to the Swagger interface found on the connector instance
- C . the link to the Swagger interface found on cloud.netapp.com
- D . the link to the API documentation on readthedocs.io
Click the Exhibit button.
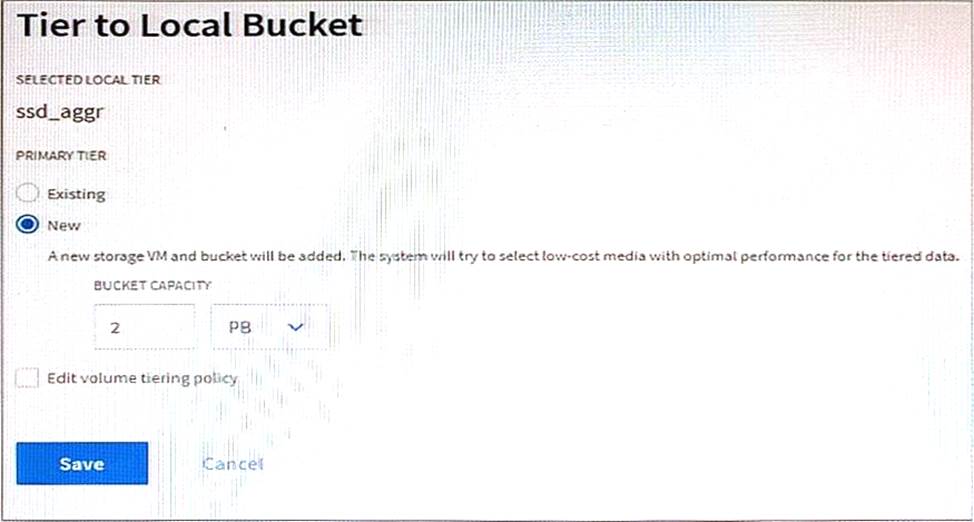
You are configuring a FabricPool aggregate as shown in the exhibit.
In this scenario, where is the S3 bucket created?
- A . AWS
- B . StorageGRID
- C . NetApp ONTAP
- D . Azure
You have a StorageGRID solution with 1 PB of object data. All data is geographically distributed and erasure coded across three sites. You are asked to create a new information lifecycle management (ILM) policy that will keep a full copy of the grid in Amazon S3.
In this scenario, which component must be configured for the ILM policy?
- A . archive node
- B . additional 1 PB license
- C . Cloud Storage Pool
- D . Cassandra database
You are creating an Ansible playbook to deploy a NetApp ONTAP cluster. You want to take advantage of a loop to automate the creation of several volumes.
What would accomplish this task?
A)
B)
C)
D)
- A . Option A
- B . Option B
- C . Option C
- D . Option D
Your customer is using Astra Control Service to back up applications. They require a consistent copy of the data that also captures data in flight.
Which two applications will Astra support in this scenario? (Choose two.)
- A . ksqIDB
- B . Jenkins
- C . Argo CD
- D . PostgreSQL
You have a hybrid storage environment with on-premises ONTAP 9.8 clusters and Cloud Volumes ONTAP for AWS 9-8 clusters. You have a requirement to automatically discover, map, and classify your data.
In this scenario, which NetApp service satisfies this requirement?
- A . Cloud Data Sense
- B . Cloud Secure
- C . Cloud Volume Service
- D . Cloud Sync
A team compiles a group of artifacts locally. The team decides to allow an automatic process to deploy the compiled artifacts to a production server.
In this scenario, which step was skipped in the DevOps process?
- A . continuous builds
- B . continuous delivery
- C . continuous integration
- D . continuous deployment
You have a 4-node AFF A800 cluster that is serving file data. You are required to replicate copies of the data volumes directly to Amazon S3.
In this scenario, which two NetApp tools satisfy this requirement? (Choose two.)
- A . Cloud Sync
- B . XCP
- C . FabricPool
- D . SnapMirror Cloud