Microsoft SC-900 Microsoft Security Compliance and Identity Fundamentals Online Training
Microsoft SC-900 Online Training
The questions for SC-900 were last updated at Dec 19,2025.
- Exam Code: SC-900
- Exam Name: Microsoft Security Compliance and Identity Fundamentals
- Certification Provider: Microsoft
- Latest update: Dec 19,2025
HOTSPOT
For each of the following statements, select Yes if the statement is true. Otherwise, select No. NOTE: Each correct selection is worth one point.

HOTSPOT
For each of the following statements, select Yes if the statement is true. Otherwise, select No. NOTE: Each correct selection is worth one point.

Which three authentication methods does Windows Hello for Business support? Each correct answer presents a complete solution. NOTE: Each correct selection is worth one point.
- A . fingerprint
- B . facial recognition
- C . PIN
- D . email verification
- E . security question
What feature in Microsoft Defender for Endpoint provides the first line of defense against cyberthreats by reducing the attack surface?
- A . automated remediation
- B . automated investigation
- C . advanced hunting
- D . network protection
Which two types of resources can be protected by using Azure Firewall? Each correct answer presents a complete solution. NOTE: Each correct selection is worth one point.
- A . Azure virtual machines
- B . Azure Active Directory (Azure AD) users
- C . Microsoft Exchange Online inboxes
- D . Azure virtual networks
- E . Microsoft SharePoint Online sites
You plan to implement a security strategy and place multiple layers of defense throughout a network infrastructure.
Which security methodology does this represent?
- A . threat modeling
- B . identity as the security perimeter
- C . defense in depth
- D . the shared responsibility model
HOTSPOT
For each of the following statements, select Yes if the statement is true. Otherwise, select No. NOTE: Each correct selection is worth one point.

Latest SC-900 Dumps Valid Version with 46 Q&As
Latest And Valid Q&A | Instant Download | Once Fail, Full Refund





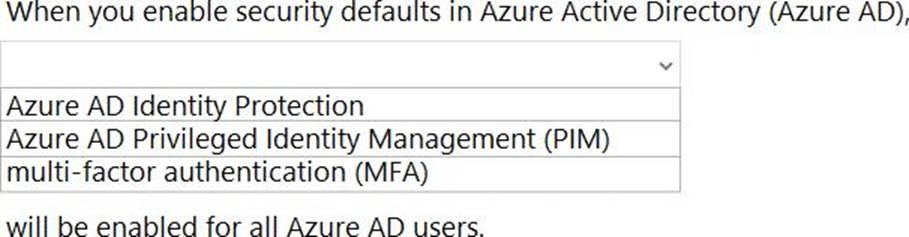
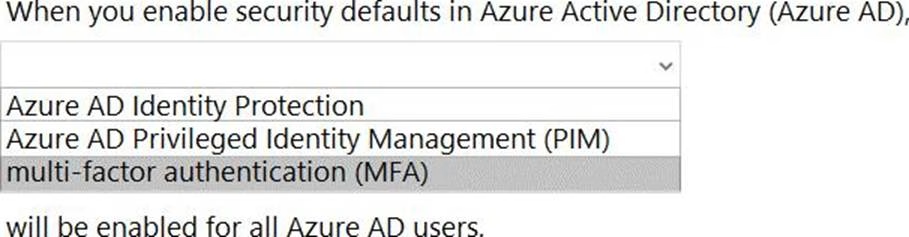

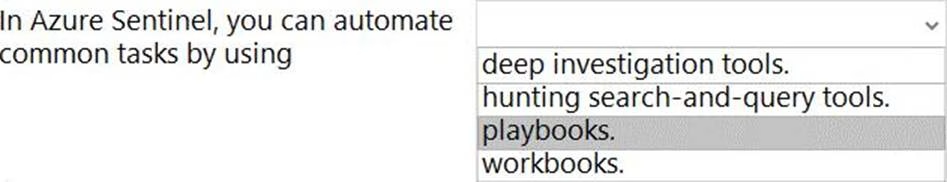


Question 68 is A,D:
Azure Firewall is a cloud-native, stateful firewall service that provides network-level protection for resources in your Azure Virtual Network (VNet). It can:
Question 51 is yes, yes, no:
Private key is used by the signer to create the digital signature.
Public key is used by others to verify the signature’s authenticity.
The private key must be kept secret and is never used for verification — only for signing.
Question 41 is 3x yes:
Encryption: Sensitivity labels can apply encryption to protect documents and emails.
Headers and Footers: Labels can insert custom headers and footers into Word, Excel, and PowerPoint files.
Watermarks: Labels can apply visual markings such as watermarks to both documents and emails.
Question 14 is A:
Azure AD Privileged Identity Management (PIM) allows you to manage, control, and monitor access to important resources in Azure AD, Azure, and other Microsoft Online Services. One of its key features is just-in-time (JIT) access, which enables users to activate privileged roles for a limited time, such as a two-hour window, to complete administrative tasks.