Topic 1, Fabrikam, Case Study
Overview
This is a case study. Case studies are not timed separately. You can use as much exam time as you would like to complete each there may be additional case studies and sections on this exam. You must manage you’re your time to ensure that you are able to complete all included on this exam in the time provided.
To answer the questions included in a case study, you will need In reference information that is provided in the case study. Case studies might contain exhibits and other resources that provide more information about the scenario that is described In the case study. Each question is independent of the other questions in this case study.
At the end of this case study, a review screen will appear. This screen allows you to review your answers and to make changes before you move to the next section of the exam. After you begin a new section, you cannot return to this section.
To start the case study
To display the first question in this case study, click the Next button. Use the buttons in the left pane to explore the content of the case study before you answer the questions. Clicking these buttons displays information such as business requirements, existing environment, and problem statements. If the case study has an All Information tab. note that the information displayed is identical to the information displayed on the subsequent tabs. When you are ready to answer a question, click the Question button to return to the question.
Cloud Environment
Fabrikam has a Microsoft 365 tenant that contains the following resources:
• An Azure Active Directory (Azure AD) tenant that syncs to an on-premises Active Directory domain named corp.fabrikam.com
• Microsoft Cloud App Security connectors configured for all supported cloud applications used by the company
Some users have company Dropbox accounts.
Compliance Configuration
Fabrikam has the following in the Microsoft 365 compliance center:
* A data loss prevention (DLP) policy is configured. The policy displays a tooltip to users. Users can provide a business justification to override a DLP policy violation.
* The Azure information Protection unified labeling scanner is installed and configured. * A sensitivity label named Fabrikam Confidential is configured.
An existing third-party records management system is managed by the compliance department.
Human Resources (HR) Management System
The HR department has an Azure SQL. database that contains employee information.
Each employee has a unique 12-character alphanumeric ID. The database contains confidential employed attributes including payroll information, date of birth, and personal contact details.
On-premises Environment
You have an on premises file server that runs Windows Server 2019 and stores Microsoft Office documents in a shared folder named Data.
All end-user computers are joined to the corp.fabrinkam.com domain and run a third-party antimalware application.
Sales Contracts
Users in the sales department receive draft sales contracts from customers by email. The sales contracts are written by the customers and are not in a standard format.
Employment Applications
Employment applications and resumes are received by HR department managers and stored in either mailboxes, Microsoft SharePoint Online sites, OneDrive for Business folders, or Microsoft Teams channels.
The employment application form is downloaded from SharePoint Online and a serial number is assigned to each application. the resumes are written by the applications and in any format.
HR Requirements
You need to create a DLP policy that will notify the HR department of a DLP policy violation if a document that contains confidential employee attributes is shared externally. The DLP policy must use an Exact Data Match (EDM) classification derived from a CSV export of the HR department database.
The HR department identifies the following requirements for handling employment applications:
* Resumes must be identified automatically based on similarities to other resumes received in the past
* Employment applications and resumes must be deleted automatically two years after the applications are received.
* Documents and emails that contain an application serial number must be identified automatically and marked as an employment application.
Sales Requirements
A sensitivity label named Sales Contract must be applied automatically to all draft and finalized sales contracts.
Compliance Requirements
Fabrikam identifies the following compliance requirements:
• All DLP policies must be applied to computers that run Windows 10, with the least possible changes to the computers.
• Users in the compliance department must view the justification provided when a user receives a tooltip notification for a DLP violation.
• If a document that has the Fabrikam Confidential sensitivity label applied is uploaded to Dropbox. the file must be deleted automatically. – The Fabrikam Confidential sensitivity label must be applied to existing Microsoft Word documents in the Data shared folder that have a document footer containing the following string: Company use only.
• Users must be able to manually select that email messages are sent encrypted. The encryption will use Office 365 Message Encryption (OME) v2. Any email containing an attachment that has the Fabrikam Confidential sensitivity label applied must be encrypted automatically by using OME.
• Existing policies configured in the third-party records management system must be replaced by using Records management in the Microsoft 365 compliance center. The compliance department plans to export the existing policies, and then produce a CSV file that contains matching labels and policies that are compatible with records management in Microsoft 365. The CSV file must be used to configure records management in Microsoft 365.
Executive Requirements
You must be able to restore all email received by Fabrikam executives for up to three years after an email is received, even if the email was deleted permanently.
HOTSPOT
You need to implement a solution to encrypt email. The solution must meet the compliance requirements.
What should you create in the Exchange admin center and the Microsoft 36.S compliance center? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point.
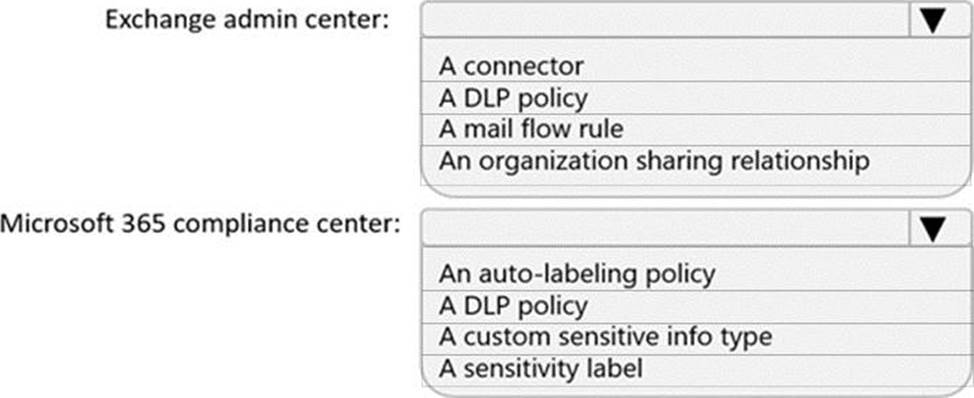
Explanation:
Users must be able to manually select that email messages are sent encrypted. The encryption will use Office 365 Message Encryption (OME) v2. Any email containing an attachment that has the Fabrikam Confidential sensitivity label applied must be encrypted automatically by using OME.
Reference: https://docs.microsoft.com/en-us/microsoft-365/compliance/ome-sensitive-info-types?view=o365-worldwide
You need to recommend a solution to configuration the Microsoft 365 Records management settings by using the CSV file must meet the compliance requirements.
What should you recommend?
- A . From the Microsoft 365 compliance center, import the CSV file to a file plan.
- B . Use EdmUploadAgent.exe to upload a hash of the CSV to a datastore.
- C . Use a PowerShell command that pipes the import csv cmdlet to the New-RetentionPolicy cmdlet.
- D . Use a PowerShell command that pipes the import-csv cmdlet to the New-Label cmdlet.
A
Explanation:
Reference: https://docs.microsoft.com/en-us/microsoft-365/compliance/file-plan-manager?view=o365-worldwide#import-retention-labels-into-your-file-plan
You need to implement a solution that meets the compliance requirements for the Windows 10 computers.
Which two actions should you perform? Each correct answer presents part of the solution. NOTE: Each coned selection is worth one point.
- A . Deploy a Microsoft 36S Endpoint data loss prevention (Endpoint DLP) configuration package to the computers.
- B . Configure hybrid Azure AD join for all the computers.
- C . Configure the Microsoft Intune device enrollment settings.
- D . Configure a compliance policy in Microsoft Intune.
- E . Enroll the computers in Microsoft Defender for Endpoint protection.
BE
Explanation:
Reference: https://docs.microsoft.com/en-us/microsoft-365/compliance/endpoint-dlp-getting-started?view=o365-worldwide
You need to recommend a solution that meets the executive requirements.
What should you recommend?
- A . From the Microsoft 365 compliance center, create a retention policy.
- B . From the Exchange admin center, enable archive mailboxes.
- C . From the Microsoft 365 compliance center, create a retention label.
- D . From the Microsoft 365 compliance center, create a DLP policy.
C
Explanation:
Reference: https://docs.microsoft.com/en-us/microsoft-365/compliance/create-apply-retention-labels?view=o365-worldwide
DRAG DROP
You need to recommend a solution that meets the sales requirements.
Which three actions should you perform in sequence? To answer, move the appropriate actions from the list of actions to the answer area and arrange them in the correct order.
Explanation:
Reference: https://docs.microsoft.com/en-us/microsoft-365/compliance/classifier-get-started-with?view=o365-worldwide
You need to recommend a solution that meets the compliance requirements for protecting the documents in the Data shared folder.
What should you recommend?
- A . From the Microsoft 365 compliance center, configure a DLP policy.
- B . From the Microsoft 365 compliance center, configure a Content Search query.
- C . From the Microsoft 365 compliance center, configure an auto-labeling policy.
- D . From Azure Information Protection, configure a content scan job.
D
Explanation:
Reference: https://docs.microsoft.com/en-us/azure/information-protection/deploy-aip-scanner
You need to recommend a solution that meets the Data Loss Prevention requirements for the HR department.
Which three actions should you perform? Each correct answer presents part of the solution. NOTE: Each correct selection is worth one point. (Choose three.)
- A . Schedule EdmUploadAgent.exe to hash and upload a data file that contains employee information.
- B . Create a sensitive info type rule package that contains the EDM classification.
- C . Define the sensitive information database schema in the XML format.
- D . Create a sensitive info type rule package that contains regular expressions.
- E . Define the sensitive information database schema in the CSV format.
ABC
Explanation:
Reference: https://docs.microsoft.com/en-us/microsoft-365/compliance/create-custom-sensitive-information-types-withexact-data-match-based-classification?view=o365-worldwide
You need to recommend a solution that meets the compliance requirements for viewing DLP tooltip justifications.
What should you recommend?
- A . Instruct the compliance department users to review the False positive and override report.
- B . Configure a Microsoft Power Automate workflow to route DLP notification emails to the compliance department.
- C . Instruct the compliance department users to review the DLP incidents report.
- D . Configure an Azure logic app to route DLP notification emails to the compliance department.
A
Explanation:
Reference: https://docs.microsoft.com/en-us/microsoft-365/compliance/view-the-dlp-reports?view=o365-worldwide
You need to recommend a solution that meets the compliance requirements for Dropbox.
What should you recommend?
- A . Create a DLP policy that applies to Cloud App Security.
- B . Edit an existing retention label that enforces the item deletion settings.
- C . Create a retention label that enforces the item deletion settings.
- D . Create a DLP policy that applies to devices.
A
Explanation:
Reference: https://docs.microsoft.com/en-us/microsoft-365/compliance/dlp-use-policies-non-microsoft-cloud-apps?view=o365-worldwide
HOTSPOT
You need to recommend an information governance solution that meets the HR requirements for handling employment applications and resumes.
What is the minimum number of information governance solution components that you should create? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point.
Explanation:
Reference: https://docs.microsoft.com/en-us/microsoft-365/compliance/apply-retention-labels-automatically?view=o365-worldwide
You need to recommend a solution that meets the compliance requirements for protecting the documents in the Data shared folder.
What should you configure in the Microsoft Purview compliance portal?
- A . a content scan job
- B . a Content Search query
- C . an auto-labeling policy
- D . a DLP policy
You need to recommend a solution that meets the compliance requirements for Dropbox.
What should you recommend?
- A . Create a DLP policy that applies to devices.
- B . Create a file policy in Microsoft Defender for Cloud Apps that uses the built-in DLP inspection method.
- C . Create a retention label that enforces the item deletion settings.
- D . Edit an existing retention label that enforces the item deletion settings.
Topic 2, Contoso Case Study
Overview
Contoso, Ltd. is a consulting company that has a main office in Montreal and three branch offices in Seattle, Boston, and Johannesburg.
Microsoft 365 Environment
Contoso has a Microsoft 365 FS tenant the tenant contains the administrative user accounts shown in the following table.
Users store data In the following locations:
• SharePoint sites
• OneDrive accounts
• Exchange email
• Exchange public folders
• Teams chats
• Teams channel messages
When users in the research department create documents, they must add a 10-dig>t project code to each document. Project codes that start with the digits 999 are confidential.
SharePoint Online Environment
Contoso has four Microsoft SharePoint Online sites named Site1. Site2. Site3. and Site4.
Site2 contains the files shown in the following table.
Two users named User1 and User2 are assigned roles for Site2 as shown in the following table.
Sile3 stores documents related to the company’s projects. The documents are organized In a folder hierarchy based on the project.
Slte4 has the following two retention policies applied:
• Name: SitetKetentionPolicy1
• Locations to apply the policy: Site4
• Delete items older than:2 years
• Delete content based on: When items were created
• Name: Site4RetentionPolicy2
• Locations to apply the policy. Sile4
• Retain items for a specific period: 4 years
• Start the retention period based on: When items were created
• At the end of the retention period: Do nothing
Problem Statements
Management at Contoso is concerned about data leaks. On several occasions, confidential research departments were leaked.
Planned Changes
Contoso plans to create the following data loss prevention (DLP) policy:
• Name: DLPpolicy1
• Locations to apply the policy; Site2
• Conditions:
• Content contains any of these sensitive info types: SWIF F Code
• Instance count: 2 to any
• Actions: Restrict access to the content
Technical Requirements
Contoso must meet the following technical requirements:
• All administrative users must be able to review DLP reports.
• Whenever possible, the principle of least privilege must be used.
• For all users, all Microsoft 365 data must be retained for at least one year.
• Confidential documents must be detected and protected by using Microsoft 365.
• Site1 documents that include credit card numbers must be labeled automatically.
• All administrative users must be able to create Microsoft 365 sensitivity labels.
• After a project is complete, the documents in Site3 that relate to the project must be retained for 10 years
You need to meet the technical requirements for the Site3 documents.
What should you create?
- A . a retention label policy and a retention label that uses an event
- B . a sensitive info type that uses a dictionary and a sensitivity label
- C . a sensitive info type that uses a regular expression and a sensitivity label
- D . a retention policy that has Only delete items when they reach a certain age selected
A
Explanation:
Reference: https://docs.microsoft.com/en-us/microsoft-365/compliance/event-driven-retention?view=o365-worldwide
HOTSPOT
For each of the following statements, select Yes if the statement is true. Otherwise, select No. NOTE: Each correct selection is worth is worth one point.
Explanation:
Reference: https://docs.microsoft.com/en-us/microsoft-365/compliance/retention?view=o365-worldwide
HOTSPOT
You need to meet the technical requirements for the confidential documents.
What should you created first, and what should you use for the detection method? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point.
Explanation:
Reference: https://docs.microsoft.com/en-us/microsoft-365/compliance/create-a-custom-sensitive-information-type?view=o365-worldwide
You need to meet the technical requirements for the creation of the sensitivity labels.
Which administrative users are currently missing the Sensitivity label administrator role?
- A . Admin1 only
- B . Admm1, Admin2, Admin4, and Admin5 only
- C . Admin 1. Admin2, and Admin3 only
- D . Admin 1 and Admin5 only
- E . Admin 1 and Admin4 only
HOTSPOT
How many files in Site2 will be visible to User1 and User2 after you turn on DLPpolicy1? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point.
Explanation:
Reference: https://social.technet.microsoft.com/wiki/contents/articles/36527.implement-data-loss-prevention-dlp-in-sharepoint-online.aspx
You need to meet the technical requirements for the creation of the sensitivity labels.
To which user or users must you grant the Sensitivity label administrator role?
- A . Admin1, Admin2, Admin4, and Admin5 only
- B . Admin1, Admin2, and Admin3 only
- C . Admin1 only
- D . Admin1 and Admin4 only
- E . Admin1 and Admin5 only
D
Explanation:
Compliance Data Administrator, Compliance Administrator, and Security Administrator already have the
required permissions to create the labels.
Reference: https://docs.microsoft.com/en-us/microsoft-365/compliance/get-started-with-sensitivity-labels?view=o365-
worldwide#permissions-required-to-create-and-manage-sensitivity-labels
You are evaluating the technical requirements for the DLP reports.
Which user can currently view the DLP reports?
- A . Admin4
- B . Admin1
- C . Admin5
- D . Admin2
- E . Admin3
HOTSPOT
You are reviewing policies for the SharePoint Online environment.
For each of the following statements, select Yes if the statement is true. Otherwise, select No. NOTE: Each correct selection is worth one point.
Explanation:
Reference: https://docs.microsoft.com/en-us/microsoft-365/compliance/retention?view=o365-worldwide
DRAG DROP
You need to meet the technical requirements for the Site1 documents.
Which three actions should you perform in sequence? To answer, move the appropriate actions from the list of actions to the answer area and arrange them in the correct order.
Explanation:
Reference: https://docs.microsoft.com/en-us/microsoft-365/compliance/apply-sensitivity-label-automatically?view=o365-worldwide#how-to-configure-auto-labeling-policies-for-sharepoint-onedrive-and-exchange
Topic 3, Misc. Questions
You have a data loss prevention (DLP) policy that applies to the Devices location. The policy protects documents that contain States passport numbers.
Users reports that they cannot upload documents to a travel management website because of the policy.
You need to ensure that the users can upload the documents to the travel management website. The solution must prevent the protected content from being uploaded to other locations.
Which Microsoft 365 Endpoint data loss prevention (Endpoint DLP) setting should you configure?
- A . Unallowed apps
- B . File path exclusions
- C . Service domains
- D . Unallowed browsers
C
Explanation:
You can control whether sensitive files protected by your policies can be uploaded to specific service domains from Microsoft Edge.
If the list mode is set to Block, then user will not be able to upload sensitive items to those domains. When an upload action is blocked because an item matches a DLP policy, DLP will either generate a warning or block the upload of the sensitive item.
If the list mode is set to Allow, then users will be able to upload sensitive items only to those domains, and upload access to all other domains is not allowed.
Reference: https://docs.microsoft.com/en-us/microsoft-365/compliance/endpoint-dlp-using?view=o365-worldwide
You create a data loss prevention (DLP) policy.
The Advanced DLP rules page is shown in the Rules exhibit.
The Review your settings page is shown in the review exhibit.
You need to review the potential impact of enabling the policy without applying the actions.
What should you do?
- A . Edit the policy, remove all the actions in DLP rule 1, and select I’d like to test it out first.
- B . Edit the policy, remove the Restrict access to the content and Send incident report to Administrator actions,
and then select Yes, turn it on right away. - C . Edit the policy, remove all the actions in DLP rule 1, and select Yes, turn it on right away.
- D . Edit the policy, and then select I’d like to test it out first.
D
Explanation:
Reference: https://docs.microsoft.com/en-us/microsoft-365/compliance/create-a-dlp-policy-from-a-template?view=o365-worldwide
You are planning a data loss prevention (DLP) solution that will apply to computers that run Windows 10.
You need to ensure that when users attempt to copy a file that contains sensitive information to a USB storage device, the following requirements are met:
* If the users are members of a group named Group1, the users must be allowed to copy the file, and an event must be recorded in the audit log.
* All other users must be blocked from copying the file.
What should you create?
- A . one DLP policy that contains one DLP rule
- B . two DLP policies that each contains one DLP rule
- C . one DLP policy that contains two DLP rules
HOTSPOT
You have a data loss prevention (DLP) policy that has the advanced DLP rules shown in the following table.
You need to identify which rules will apply when content matches multiple advanced DLP rules.
Which rules should you identify? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point.
Explanation:
Reference: https://docs.microsoft.com/en-us/microsoft-365/compliance/data-loss-prevention-policies?view=o365-worldwide
You have a data loss prevention (DLP) policy configured for endpoints as shown in the following exhibit.
From a computer named Computer1, 3 user can sometimes upload files to cloud services and sometimes cannot. Other users experience the same issue.
What are two possible causes of the issue? Each correct answer presents a complete solution. NOTE: Each correct selection is worth one point.
- A . The Access by unallowed apps action is set to Audit only.
- B . The computers are NOT onboarded to the Microsoft 365 compliance center.
- C . The Copy to clipboard action is set to Audit only.
- D . There are file path exclusions in the Microsoft 365 Endpoint data loss prevention (Endpoint DIP) settings.
- E . The unallowed browsers in the Microsoft 365 Endpoint data loss prevention (Endpoint DLP) settings are NOT configured.
You need to provide a user with the ability to view data loss prevention (DLP) alerts in the Microsoft 365 compliance center. The solution must use the principle of least privilege.
Which role should you assign to the use?
- A . Compliance data administrator
- B . Security operator
- C . Security reader
- D . Compliance administrator
C
Explanation:
Reference: https://docs.microsoft.com/en-us/microsoft-365/compliance/dlp-configure-view-alerts-policies?view=o365-worldwide
You need to be alerted when users share sensitive documents from Microsoft OneDrive to any users outside your company.
What should you do?
- A . From the Microsoft 365 compliance center, create a data loss prevention (DLP) policy.
- B . From the Azure portal, create an Azure Active Directory (Azure Al)) Identity Protection policy.
- C . From the Microsoft 36h compliance? center, create an insider risk policy.
- D . From the Microsoft 365 compliance center, start a data investigation.
A
Explanation:
Reference: https://docs.microsoft.com/en-us/microsoft-365/compliance/dlp-learn-about-dlp?view=o365-worldwide
Your company has a Microsoft 365 tenant that uses a domain named contoso.com.
You are implementing data loss prevention (DLP).
The company’s default browser is Microsoft Edge.
During a recent audit, you discover that some users use Firefox and Google Chrome browsers to upload files labeled as Confidential to a third-party Microsoft SharePoint Online site that has a URL of https://m365x076709.sharepoint.com. Users are blocked from uploading the confidential files to the site from Microsoft Edge.
You need to ensure that the users cannot upload files labeled as Confidential from Firefox and Google Chrome to any cloud services.
Which two actions should you perform? Each correct answer presents part of the solution. NOTE: Each correct selection is worth one point. (Choose two.)
- A . From the Microsoft 365 Endpoint data loss prevention (Endpoint) DLP settings, add m365x076709.sharepoint.com as a blocked service domain.
- B . Create a DLP policy that applies to the Devices location.
- C . From the Microsoft 365 Endpoint data loss prevention (Endpoint DLP) settings, add Firefox and Google Chrome to the unallowed browsers list.
- D . From the Microsoft 365 compliance center, onboard the devices.
- E . From the Microsoft 365 Endpoint data loss prevention (Endpoint) DLP settings, add contoso.com as an allowed service domain.
CD
Explanation:
Reference: https://docs.microsoft.com/en-us/microsoft-365/compliance/endpoint-dlp-learn-about?view=o365-worldwide
You need to create a retention policy to retain all the files from Microsoft Teams channel conversations and private chats.
Which two locations should you select in the retention policy? Each correct answer present part of the solution. NOTE: Each correct selection is worth one point.
- A . Team channel messages
- B . OneDrive accounts
- C . SharePoint sites
- D . Exchange email
- E . Office 365 groups
- F . Team chats
BC
Explanation:
Reference: https://support.microsoft.com/en-us/office/file-storage-in-teams-df5cc0a5-d1bb-414c-8870-46c6eb76686a
HOTSPOT
You create a retention label policy named Contoso_policy that contains the following labels.
✑ 10 years then delete
✑ 5 years then delete
✑ Do not retain
Contoso_Policy is applied to content In Microsoft Sharepoint Online sites.
After a couple of days, yon discover the following messages on the Properties page of the label policy.
* Statue Off (Error)
* It’s taking longer than expected to deploy the policy
You need to reinitiate the policy.
How should you complete the command? To answer, select the appropriate options in the; answer area. NOTE: Each correct selection is worth one point.
Explanation:
Reference: https://docs.microsoft.com/en-us/powershell/module/exchange/set-retentioncompliancepolicy?view=exchange-ps
You have a Microsoft 365 tenant.
All Microsoft OneDrive for Business content is retained roe five years.
A user named User1 left your company a year ago, after which the account of User 1 was deleted from Azure Active Directory (Azure AD)
You need to recover an important file that was stored in the OneDrive of User1.
What should you use?
- A . the Restore-SPODeletedSite PowerShell cmdlet
- B . the OneDrive recycle bin
- C . the Restore-ADObject PowerShell cmdlet
- D . Deleted users in the Microsoft 365 admin center
B
Explanation:
Reference:
https://docs.microsoft.com/en-us/onedrive/set-retention
https://docs.microsoft.com/en-us/onedrive/retention-and-deletion
HOTSPOT
You have a Microsoft 365 tenant that uses a domain named canstoso.com.
A user named User1 leaves your company. The mailbox of User1 is placed on Litigation Hold, and then the account of User1 is deleted from Azure Active Directory (Azure AD).
You need to copy the content of the User1 mailbox to a folder in the existing mailbox of another user named User2.
How should you complete the PowerShell command? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point.
Explanation:
Reference: https://docs.microsoft.com/en-us/microsoft-365/compliance/restore-an-inactive-mailbox?view=o365-worldwide
HOTSPOT
You have the retention label policy shown in the Policy exhibit. (Click the Policy tab.)
Users apply the retention label policy to files and set the asset ID as shown in the following table.
On December 1, 2020, you create the event shown in the Event exhibit. (Click the Event tab.)
For each of the following statements, select Yes if the statement is true. Otherwise, select No. NOTE: Each correct selection is worth one point.
HOTSPOT
At the end of a project you upload project documents to a Microsoft SharePoint Online library that contains many fifes.
Files that have the following naming format must be labeled as Project I
• aei_AA989.docx
• bd_WSOgadocx
• cei_DLF112-docx
• ebc_QQ4S4.docx
• ecc_BB565.docx
You plan to create an auto-apply retention label policy.
What should you use to identify the files, and which regular expression should you use? To answer, select the appropriate options in the answer area.
Explanation:
Box 1 = a retention label
Box 2 = [a-z]{3}[_][A-Z][d]{3}.docx
Your company manufactures parts that are each assigned a unique 12-character alphanumeric serial number. Emails between the company and its customers refer in the serial number.
You need to ensure that ail Microsoft Exchange Online emails containing the serial numbers are retained for five years.
Which three objects should you create? Each correct answer presents part of the solution. NOTE: Each correct selection is worth one point.
- A . a trainable classifier
- B . a sensitive info type
- C . a retention polity
- D . a data loss prevention (DLP) policy
- E . an auto-labeling policy
- F . a retention label
- G . a sensitivity label
BFE
Explanation:
Reference:
https://docs.microsoft.com/en-us/microsoft-365/compliance/sensitive-information-type-learn-about?view=o365-worldwide
https://docs.microsoft.com/en-us/microsoft-365/compliance/apply-sensitivity-label-automatically?view=o365-worldwide
https://docs.microsoft.com/en-us/microsoft-365/compliance/retention?view=o365-worldwide
You receive an email that contains a list of words that will be used few a sensitive information type.
You need to create a file that can be used as the source of a keyword dictionary.
In which format should you save the list?
- A . an XLSX file that contains one word in each cell of the first row
- B . a ISV file that contains words separated by tabs
- C . a JSON file that that an element tor each word
- D . a text file that has one word on each line
D
Explanation:
Keyword dictionaries can be created either from a text file or from csv file.
Note:
There are several versions of this question in the exam.
The question has two possible correct answers:
✑ a CSV file that contains words separated by commas
✑ a text file that has one word on each line
Other incorrect answer options you may see on the exam include the following:
✑ a TSV file that contains words separated by tabs
✑ a DOCX file that has one word on each line
✑ an XML file that contains a keyword tag for each word
Reference: https://docs.microsoft.com/en-us/microsoft-365/compliance/create-a-keyword-dictionary?view=o365-worldwide
HOTSPOT
You plan to create a custom trainable classifier based on an organizational form template.
You need to identity which role based access control (RBAC) role is required to create the trainable classifier and where to classifier. The solution must use the principle of least privilege.
What should you identify? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point.
Explanation:
Reference: https://docs.microsoft.com/en-us/microsoft-365/compliance/classifier-get-started-with?view=o365-worldwide#prepare-for-a-custom-trainable-classifier
You plan to implement sensitivity labels for Microsoft Teams.
You need to ensure that you can view and apply sensitivity labels to new Microsoft Teams sites.
What should you do first?
- A . Run the Set-sposite cmdlet.
- B . Configure the EnableMTPLabels Azure Active Directory (Azure AD) setting.
- C . Create a new sensitivity label scoped to Groups & sites.
- D . Run the Execute-AzureAdLabelSync cmdtet.
C
Explanation:
Reference: https://docs.microsoft.com/en-us/microsoft-365/compliance/sensitivity-labels-teams-groups-sites?view=o365-worldwide
DRAG DROP
You have a Microsoft 365 tenant that uses data loss prevention (DLP).
You have a custom employee information form named Template 1.docx.
You need to create a classification rule package based on the document fingerprint of Templatel.docx.
Which three actions should you perform in sequence? To answer, move the appropriate actions from the list of actions to the answer area and arrange them in the correct order.
Your company has a Microsoft 365 tenant that uses a domain named contoso.
The company uses Microsoft Office 365 Message Encryption (OMI) to encrypt email sent to users in fabrikam.com.
A user named User1 erroneously sends an email to user2@fabrikam
You need to disable user2@fabrikam.com from accessing the email.
What should you do?
- A . Run the New-ComplianceSearchAction cmdlet.
- B . Instruct User1 to delete the email from her Sent Items folder from Microsoft Outlook.
- C . Run the Get-MessageTrace Cmdlet.
- D . Run the Set-OMEMessageRevocation Cmdlet.
- E . instruct User1 to select Remove external access from Microsoft Outlook on the web.
HOTSPOT
You are implementing Microsoft Office 365 Message Encryption (OME) for a Microsoft 365 tenant named contoso.com.
You need to meet the following requirements:
• All email to a domain named fabhkam.com must be encrypted automatically.
• Encrypted emails must expire seven days after they are sent-
What should you configure for each requirement? To answer, select the appropriate options NOTE: Each correct selection is worth one point.
Explanation:
Reference:
https://docs.microsoft.com/en-us/microsoft-365/compliance/email-encryption?view=o365-worldwide
https://docs.microsoft.com/en-us/microsoft-365/compliance/ome-advanced-expiration?view=o365-worldwide
You create a custom sensitive info type that uses Exact Data Match (EDM).
You plan to periodically update and upload the data used for EDM.
What is the maximum frequency with which the data can be uploaded?
- A . twice per hour
- B . once every 48 hours
- C . twice per day
- D . twice per week
- E . once every six hours
HOTSPOT
You plan to create a custom sensitive information type that will use Exact Data Match (EDM).
You need to identify what to upload to Microsoft 365, and which tool to use for the upload.
What should you identify? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point.
HOTSPOT
You plan to implement a sensitive information type based on a trainable classifier. The sensitive information type will identify employment contracts.
You need to copy the required files to Microsoft SharePoint Online folders to train the classifier.
What should you use to seed content and test the classifier? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point.
Explanation:
Reference: https://docs.microsoft.com/en-us/microsoft-365/compliance/classifier-get-started-with?view=o365-worldwide
Your company has a Microsoft 365 tenant.
The company performs annual employee assessments. The assessment results are recorded in a document named Assessment I cmplatc.docx that is created by using Microsoft Word template. Copies of the employee assessments are sent to employees and their managers. The assessment copies are stored in mailboxes, Microsoft SharePoint Online sites, and OneDrive for Business folders. A copy of each assessment is also stored in a SharePoint Online folder named Assessments.
You need to create a data loss prevention (DLP) policy that prevents the employee assessments from being emailed to external users. You will use a document fingerprint to identify the assessment documents.
What should you include in the solution?
- A . Create a fingerprint of AssessmentTemplate.docx.
- B . Create a sensitive info type that uses Exact Data Match (EDM).
- C . Create a fingerprint of TOO sample documents in the Assessments folder.
- D . Import 100 sample documents from the Assessments folder to a seed folder.
A
Explanation:
Reference: https://docs.microsoft.com/en-us/microsoft-365/compliance/document-fingerprinting?view=o365-worldwide
You have a Microsoft 365 tenant that uses trainable classifiers.
You are creating a custom trainable classifier.
You collect 300 sample file types from various geographical locations to use as seed content. Some of the file samples are encrypted.
You organize the files into categories as shown in the following table.
Which file categories can be used as seed content?
- A . Category4 and Category5 only
- B . Category4 and Category6 only
- C . Category3. and Category5 only
- D . Category1 and Category3 only
C
Explanation:
Reference:
https://docs.microsoft.com/en-us/microsoft-365/compliance/classifier-get-started-with?view=o365-worldwide
https://docs.microsoft.com/en-us/sharepoint/technical-reference/default-crawled-file-name-extensions-andparsed-file-types
You have a Microsoft 365 tenant that uses the following sensitivity labels:
* Confidential
* Internal
* External
The labels are published by using a label policy named Policy1.
Users report that Microsoft Office for the wen apps do not display the Sensitivity button. The Sensitivity button appears in Microsoft 365 Apps that are installed locally.
You need to ensure that the users can apply sensitivity labels to content when they use Office for the web apps.
Solution: You modify the publishing settings of Policy1.
Does the meet the goal?
- A . Yes
- B . No
You have a Microsoft 365 tenant that uses the following sensitivity labels:
* Confidential
* Internal
* External
The labels are published by using a label policy named Policy1.
Users report that Microsoft Office for the wen apps do not display the Sensitivity button. The Sensitivity button appears in Microsoft 365 Apps that are installed locally.
You need to ensure that the users can apply sensitivity labels to content when they use Office for the web apps.
Solution: You modify the scope of the Confidential label.
Does this meet the goal?
- A . Yes
- B . No
You have a Microsoft 365 tenant that uses the following sensitivity labels:
* Confidential
* Internal
* External
The labels are published by using a label policy named Policy1.
Users report that Microsoft Office for the wen apps do not display the Sensitivity button. The Sensitivity button appears in Microsoft 365 Apps that are installed locally.
You need to ensure that the users can apply sensitivity labels to content when they use Office for the web apps.
Solution: You run the Execute-AzureAdLabelSync cmdlet.
Does this meet the goal?
- A . Yes
- B . No
You implement Microsoft 365 Endpoint data loss prevention (Endpoint DLP).
You have computers that run Windows 10 and have Microsoft 365 Apps installed. The computers are joined to Azure Active Directory (Azure AD).
You need to ensure that Endpoint DLP policies can protect content on the computers.
Solution: You onboard the computers to Microsoft Defender fur Endpoint.
Does this meet the goal?
- A . Yes
- B . No
You implement Microsoft 365 Endpoint data loss prevention (Endpoint DLP).
You have computers that run Windows 10 and have Microsoft 365 Apps installed. The computers are joined to Azure Active Directory (Azure AD).
You need to ensure that Endpoint DLP policies can protect content on the computers.
Solution: You enroll the computers in Microsoft intune.
Does this meet the goal?
- A . Yes
- B . No
B
Explanation:
Reference: https://docs.microsoft.com/en-us/microsoft-365/compliance/endpoint-dlp-getting-started?view=o365-worldwide
You implement Microsoft 365 Endpoint data loss prevention (Endpoint DLP).
You have computers that run Windows 10 and have Microsoft 365 Apps installed. The computers are joined to Azure Active Directory (Azure AD).
You need to ensure that Endpoint DLP policies can protect content on the computers.
Solution: You deploy the unified labeling client to the computers.
Does this meet the goal?
- A . Yes
- B . No
B
Explanation:
Reference: https://docs.microsoft.com/en-us/microsoft-365/compliance/endpoint-dlp-getting-started?view=o365-worldwide
You create three sensitivity labels named Sensitivity1, Sensitivity2, and Sensitivity3 and perform the following actions:
Publish Sensitivity1.
Create an auto-labeling policy for Sensitivity2.
You plan to create a file policy named Policy1 in Microsoft Cloud App Security.
Which sensitivity labels can you apply to Microsoft SharePoint Online in Policy1?
- A . Sensitivity1 only
- B . Sensitivity1, Sensitivity2, and Sensitivity3
- C . Sensitivity2 only
- D . Sensitivity1 and Sensitivity2 only
D
Explanation:
Reference:
https://docs.microsoft.com/en-us/microsoft-365/compliance/apply-sensitivity-label-automatically?view=o365-worldwide
https://docs.microsoft.com/en-us/cloud-app-security/azip-integration
You have a Microsoft OneDrive for Business folder that contains the files shown in the following table.
In Microsoft Cloud App Security, you create a file policy to automatically apply a classification.
What is the effect of applying the policy?
- A . The policy will apply to only the .docx and .txt files. The policy will classify the files within 24 hours.
- B . The policy will apply to all the files. The policy will classify only 100 files daily.
- C . The policy will apply to only the .docx files. The policy will classify only 100 files daily.
- D . The policy will apply to only the .docx and .txt files. The policy will classify the files immediately.
C
Explanation:
Reference: https://docs.microsoft.com/en-us/cloud-app-security/azip-integration
HOTSPOT
You have a Microsoft 365 tenant named contoso.com that contains two users named User1 and User2. The tenant uses Microsoft Office 365 Message Encryption (OME).
User1 plans to send emails that contain attachments as shown in the following table.
User2 plans to send emails that contain attachments as shown in the following table.
For which emails will the attachments be protected? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point.
Explanation:
Reference:
https://support.microsoft.com/en-gb/office/introduction-to-irm-for-email-messages-bb643d33-4a3f-4ac7-9770-fd50d95f58dc?ui=en-us&rs=en-gb&ad=gb#FileTypesforIRM
https://docs.microsoft.com/en-us/microsoft-365/compliance/ome?view=o365-worldwide
https://docs.microsoft.com/en-us/office365/servicedescriptions/exchange-online-service-description/exchange-online-limits#message-limits-1
HOTSPOT
You use project codes that have a format of three alphabetical characters that represent the project
type, followed by three digits, for example Abc123.
You need to create a new sensitive info type for the project codes.
How should you configure the regular expression to detect the content? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point.
Explanation:
Reference: https://joannecklein.com/2018/08/07/build-and-use-custom-sensitive-information-types-in-office-365/
HOTSPOT
You have a Microsoft SharePoint Online site named Site1 and a sensitivity label named Sensitivity1.
Sensitivity1 adds a watermark and a header to content.
You create a policy to automatically apply Sensitivity1 to emails in Microsoft Exchange Online and Site1.
How will Sensitivity1 mark matching emails and Site1 documents? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point.
Explanation:
Reference: https://docs.microsoft.com/en-us/microsoft-365/compliance/sensitivity-labels?view=o365-worldwide
HOTSPOT
You need to implement an information compliance policy to meet the following requirements:
Documents that contain passport numbers from the United States, Germany, Australia, and Japan must be identified automatically.
When a user attempts to send an email or an attachment that contains a passport number, the user must receive a tooltip in Microsoft Outlook.
Users must be blocked from using Microsoft SharePoint Online or OneDrive for Business to share a document that contains a passport number.
What is the minimum number of sensitivity labels and auto-labeling policies you should create? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point.
Explanation:
Reference: https://docs.microsoft.com/en-us/microsoft-365/compliance/get-started-with-sensitivity-labels?view=o365-worldwide
HOTSPOT
You have a Microsoft 365 E5 tenant.
You create sensitivity labels as shown in the Sensitivity Labels exhibit.
The Confidential/External sensitivity label is configured to encrypt files and emails when applied to content.
The sensitivity labels are published as shown in the Published exhibit.
For each of the following statements, select Yes if the statement is true. Otherwise, select No. NOTE: Each correct selection is worth one point.
Explanation:
Reference: https://docs.microsoft.com/en-us/microsoft-365/compliance/sensitivity-labels?view=o365-worldwide
You are implementing a data classification solution.
The research department at your company requires that documents containing programming code be labeled as Confidential. The department provides samples of the code from its document library. The solution must minimize administrative effort.
What should you do?
- A . Create a custom classifier.
- B . Create a sensitive info type that uses Exact Data Match (EDM).
- C . Use the source code classifier.
- D . Create a sensitive info type that uses a regular expression.
C
Explanation:
Reference: https://docs.microsoft.com/en-us/microsoft-365/compliance/classifier-learn-about?view=o365-worldwide
You have a new Microsoft 365 tenant.
You need to ensure that custom trainable classifiers can be created in the tenant.
To which role should you be assigned to perform the configuration?
- A . Security administrator
- B . Security operator
- C . Global administrator
- D . Compliance administrator
D
Explanation:
Reference: https://docs.microsoft.com/en-us/microsoft-365/compliance/classifier-get-started-with?view=o365-worldwide
You need to automatically apply a sensitivity label to documents that contain information about your company’s network including computer names, IP addresses, and configuration information.
Which two objects should you use? Each correct answer presents part of the solution. NOTE: Each correct selection is worth one point. (Choose two.)
- A . an Information protection auto-labeling policy
- B . a custom trainable classifier
- C . a sensitive info type that uses a regular expression
- D . a data loss prevention (DLP) policy
- E . a sensitive info type that uses keywords
- F . a sensitivity label that has auto-labeling
AB
Explanation:
Reference:
https://docs.microsoft.com/en-us/microsoft-365/compliance/classifier-learn-about?view=o365-worldwide
https://docs.microsoft.com/en-us/microsoft-365/compliance/apply-sensitivity-label-automatically?view=o365-worldwide
You are creating a custom trainable classifier to identify organizational product codes referenced in Microsoft 365 content.
You identify 300 files to use as seed content.
Where should you store the seed content?
- A . a Microsoft SharePoint Online folder
- B . a Microsoft OneDrive for Business folder
- C . an Azure file share
- D . Microsoft Exchange Online shared mailbox
A
Explanation:
Reference: https://docs.microsoft.com/en-us/microsoft-365/compliance/classifier-get-started-with?view=o365-worldwide
Each product group at your company must show a distinct product logo in encrypted emails instead of the standard Microsoft Office 365 logo.
What should you do to create the branding templates?
- A . Create a Transport rule.
- B . Create an RMS template.
- C . Run the Set-IRMConfiguration cmdlet.
- D . Run the New-OMEConfiguration cmdlet.
D
Explanation:
Reference: https://docs.microsoft.com/en-us/microsoft-365/compliance/add-your-organization-brand-to-encryptedmessages?view=o365-worldwide
HOTSPOT
You create a data loss prevention (DLP) policy that meets the following requirements:
Prevents guest users from accessing a sensitive document shared during a Microsoft Teams chat Prevents guest users from accessing a sensitive document stored in a Microsoft Teams channel
Which location should you select for each requirement? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point.
Explanation
Reference:
https://docs.microsoft.com/en-us/microsoft-365/compliance/dlp-microsoft-teams?view=o365-worldwide
https://docs.microsoft.com/en-us/microsoftteams/sharepoint-onedrive-interact
You are configuring a data loss prevention (DLP) policy to report when credit card data is found on a Windows 10 device joined to Azure Active Directory (Azure AD).
You plan to use information from the policy to restrict the ability to copy the sensitive data to the clipboard.
What should you configure in the policy rule?
- A . the incident report
- B . an action
- C . user notifications
- D . user overrides
D
Explanation:
Reference: https://docs.microsoft.com/en-us/microsoft-365/compliance/endpoint-dlp-using?view=o365-worldwide
HOTSPOT
You have a Microsoft 365 E5 tenant.
Data loss prevention (DLP) policies are applied to Exchange email, SharePoint sites, and OneDrive accounts locations.
You need to use PowerShell to retrieve a summary of the DLP rule matches from the last seven days.
Which PowerShell module and cmdlet should you use? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point.
Explanation:
Reference: https://docs.microsoft.com/en-us/powershell/module/exchange/get-dlpdetectionsreport?view=exchange-ps
HOTSPOT
You plan to implement Microsoft 365 Endpoint data loss prevention (Endpoint DLP).
You need to identify which end user activities can be audited on the endpoints, and which activities can be restricted on the endpoints.
What should you identify for each activity? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point.
Explanation:
Reference: https://docs.microsoft.com/en-us/microsoft-365/compliance/endpoint-dlp-learn-about?view=o365-worldwide
You have a Microsoft 365 E5 tenant and the Windows 10 devices shown in the following table.
To which devices can you apply Microsoft 365 Endpoint data loss prevention (Endpoint DLP) settings?
- A . Device1, Device3, and Device4 only
- B . Device1, Device2, Device3, and Device4
- C . Device1 and Device2 only
- D . Device1 and Device3 only
- E . Device1 only
C
Explanation:
Reference: https://docs.microsoft.com/en-us/microsoft-365/compliance/endpoint-dlp-getting-started?view=o365-worldwide
HOTSPOT
You have a Microsoft SharePoint Online site that contains the following files.
Users are assigned roles for the site as shown in the following table.
Which files can User1 and User2 view? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point.
Explanation:
Reference: https://social.technet.microsoft.com/wiki/contents/articles/36527.implement-data-loss-prevention-dlp-in-sharepoint-online.aspx
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
You implement Microsoft 365 Endpoint data loss prevention (Endpoint DLP).
You have computers that run Windows 10 and have Microsoft 365 Apps installed. The computers are joined to Azure Active Directory (Azure AD).
You need to ensure that Endpoint DLP policies can protect content on the computers.
Solution: You onboard the computers to Microsoft Defender for Endpoint.
Does this meet the goal?
- A . Yes
- B . No
A
Explanation:
Reference: https://docs.microsoft.com/en-us/microsoft-365/compliance/endpoint-dlp-getting-started?view=o365-worldwide
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
You are configuring a file policy in Microsoft Cloud App Security.
You need to configure the policy to apply to all files. Alerts must be sent to every file owner who is affected by the policy. The policy must scan for credit card numbers, and alerts must be sent to the Microsoft Teams site of the affected department.
Solution: You use the Data Classification service inspection method and send alerts as email.
Does this meet the goal?
- A . Yes
- B . No
B
Explanation:
Reference:
https://docs.microsoft.com/en-us/cloud-app-security/dcs-inspection
https://docs.microsoft.com/en-us/cloud-app-security/data-protection-policies
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
You are configuring a file policy in Microsoft Cloud App Security.
You need to configure the policy to apply to all files. Alerts must be sent to every file owner who is affected by the policy. The policy must scan for credit card numbers, and alerts must be sent to the Microsoft Teams site of the affected department.
Solution: You use the Data Classification service inspection method and send alerts to Microsoft Power Automate.
Does this meet the goal?
- A . Yes
- B . No
B
Explanation:
Reference:
https://docs.microsoft.com/en-us/cloud-app-security/dcs-inspection
https://docs.microsoft.com/en-us/cloud-app-security/data-protection-policies
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
You are configuring a file policy in Microsoft Cloud App Security.
You need to configure the policy to apply to all files. Alerts must be sent to every file owner who is affected by the policy. The policy must scan for credit card numbers, and alerts must be sent to the Microsoft Teams site of the affected department.
Solution: You use the Build-in DLP inspection method and send alerts to Microsoft Power Automate.
Does this meet the goal?
- A . Yes
- B . No
B
Explanation:
Reference:
https://docs.microsoft.com/en-us/cloud-app-security/dcs-inspection
https://docs.microsoft.com/en-us/cloud-app-security/data-protection-policies
In Microsoft Exchange Online, you have a retention policy named Policy1 that applies a retention tag named Tag1.
You plan to remove Tag1 from Policy1.
What will occur when you remove the tag from Policy1?
- A . The content will remain tagged and the Managed Folder Assistant will process Tag1.
- B . Tag1 will be removed if Policy1 applied the tag to the content.
- C . The content will remain tagged, but the Managed Folder Assistant will ignore Tag1.
A
Explanation:
Reference: https://docs.microsoft.com/en-us/exchange/security-and-compliance/messaging-records-management/retention-tags-and-policies#removing-or-deleting-a-retention-tag-from-a-retention-policy
DRAG DROP
You have a Microsoft 365 tenant.
A new regulatory requirement states that all documents containing a patent ID be labeled, retained for 10 years, and then deleted. The policy used to apply the retention settings must never be disabled or deleted by anyone.
You need to implement the regulatory requirement.
Which three actions should you perform in sequence? To answer, move the appropriate actions from the list of actions to the answer area and arrange them in the correct order. (Choose three.)
Explanation:
Reference:
https://docs.microsoft.com/en-us/microsoft-365/compliance/retention?view=o365-worldwide
https://docs.microsoft.com/en-us/microsoft-365/compliance/retention-preservation-lock?view=o365-worldwide
You have a Microsoft SharePoint Online site that contains employee contracts in a document library named Contracts.
The contracts must be treated as records in accordance with your company’s records management policy.
You need to implement a solution to automatically mark all the contracts as records when they are uploaded to Contracts.
Which two actions should you perform? Each correct answer presents part of the solution. NOTE: Each correct selection is worth one point. (Choose two.)
- A . Create a sensitivity label.
- B . Create a retention label.
- C . Configure a default label on the Contracts document library.
- D . Create a retention policy.
- E . Create a SharePoint Records Center.
- F . Create a retention lock.
BC
Explanation:
Reference: https://docs.microsoft.com/en-us/microsoft-365/compliance/create-apply-retention-labels?view=o365-worldwide
You need to create a retention policy to delete content after seven years from the following locations:
✑ Exchange email
✑ SharePoint sites
✑ OneDrive accounts
✑ Office 365 groups
✑ Teams channel messages
✑ Teams chats
What is the minimum number of retention policies that you should create?
- A . 1
- B . 2
- C . 3
- D . 4
A
Explanation:
Reference: https://docs.microsoft.com/en-us/microsoft-365/compliance/retention?view=o365-worldwide
HOTSPOT
You create a retention policy as shown in the following exhibit.
A user named User1 deletes a file named File1.docx from a Microsoft SharePoint Online site named Site1.
A user named User2 deletes an email and empties the Deleted Items folder in Microsoft Outlook.
Where is the content retained one year after deletion? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point.
Explanation:
Reference: https://docs.microsoft.com/en-us/microsoft-365/compliance/retention?view=o365-worldwide
You have a Microsoft 365 tenant that uses records management.
You use a retention label to mark legal files stored in a Microsoft SharePoint Online document library as
regulatory records.
What can you do to the legal files?
- A . Remove the retention label of the files.
- B . Edit the properties of the files.
- C . Move the files to a different folder within the document library.
- D . Delete the content from the files.
C
Explanation:
Reference: https://docs.microsoft.com/en-us/microsoft-365/compliance/records-management?view=o365-worldwide#records
You have a Microsoft 365 tenant that contains the users shown in the following table.
You configure a retention label to trigger a disposition review at the end of the retention period.
Which users can access the Disposition tab in the Microsoft 365 compliance center to review the content?
- A . User1 only
- B . User2 only
- C . User3 only
- D . User1 and User3
- E . User3 and User4
C
Explanation:
Reference: https://docs.microsoft.com/en-us/microsoft-365/security/office-365-security/permissions-in-the-security-andcompliance-center?view=o365-worldwide
HOTSPOT
While creating a retention label, you discover that the following options are missing:
✑ Mark items as a record
✑ Mark items as a regulatory record
You need to ensure that the options are available when you create retention labels in the Microsoft 365 compliance center.
How should you complete the PowerShell script? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point.
Explanation:
Reference:
https://docs.microsoft.com/en-us/microsoft-365/compliance/declare-records?view=o365-worldwide
https://docs.microsoft.com/en-us/powershell/exchange/connect-to-scc-powershell?view=exchange-ps
You need to ensure that documents in a Microsoft SharePoint Online site that contain a reference to Project Alpha are retained for two years, and then deleted.
Which two objects should you create? Each correct answer presents part of the solution. NOTE: Each correct selection is worth one point. (Choose two.)
- A . a retention policy
- B . an auto-apply label policy
- C . a sensitive info type
- D . a retention label
- E . a sensitivity label
- F . a publishing label policy
BD
Explanation:
Reference: https://docs.microsoft.com/en-us/microsoft-365/compliance/apply-retention-labels-automatically?view=o365Worldwide
You are configuring a retention label named Label1 as shown in the following exhibit.
You need to ensure that documents that have Label1 applied are deleted three years after the end of your company’s fiscal year.
What should you do?
- A . Create a new event type.
- B . Select Only delete items when they reach a certain age.
- C . Modify the Retention period setting.
- D . Set At the ends of the retention period to Trigger a disposition review.
A
Explanation:
https://docs.microsoft.com/en-us/microsoft-365/compliance/event-driven-retention?view=o365-worldwide
HOTSPOT
You enable archive mailboxes for all the users at your company.
The Default MRM Policy is shown in the MRM exhibit.
A Microsoft 365 retention label policy is shown in the Label Policy exhibit.
You need to identify the following:
✑ How many years until an email is archived?
✑ What should you modify to change the retention period for archiving?
What should you identify? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point.
Explanation:
Reference: https://docs.microsoft.com/en-us/microsoft-365/compliance/retention?view=o365-worldwide#the-principles-of-retention-or-what-takes-precedence
You have a Microsoft 365 tenant.
You have a Microsoft SharePoint Online site that contains employment contracts in a folder named EmploymentContracts. All the files in EmploymentContracts are marked as records.
You need to recommend a process to ensure that when a record is updated, the previous version of the record is kept as a version of the updated record.
What should you recommend?
- A . Upload an updated file plan that contains the record definition.
- B . Unlock the record, modify the record, and then lock the record.
- C . Create a copy of the record and enter a version in the file metadata.
- D . Create a new label policy associated to an event that will apply to the record.
B
Explanation:
Reference: https://docs.microsoft.com/en-us/microsoft-365/compliance/record-versioning?view=o365-worldwide
You need to meet the retention requirement for the users’ Microsoft 365 data.
What is the minimum number of retention policies that you should use?
- A . 1
- B . 2
- C . 3
- D . 4
- E . 6
A
Explanation:
Reference: https://docs.microsoft.com/en-us/microsoft-365/compliance/retention?view=o365-worldwide
A user reports that she can no longer access a Microsoft Excel file named Northwind Customer Data.xlsx.
From the Cloud App Security portal, you discover the alert shown in the exhibit.
You restore the file from quarantine.
You need to prevent files that match the policy from being quarantined. Files that match the policy must generate an alert.
What should you do?
- A . Modify the policy template.
- B . Assign the Global reader role to the file owners.
- C . Exclude file matching by using a regular expression.
- D . Update the governance action.
D
Explanation:
Reference: https://docs.microsoft.com/en-us/cloud-app-security/data-protection-policies#create-a-new-file-policy
HOTSPOT
You create a sensitivity label as shown in the Sensitivity Label exhibit.
You create an auto-labeling policy as shown in the Auto Labeling Policy exhibit.
A user sends the following email:
From: user1@contoso.com
To: user2@fabrikam.com
Subject: Address List
Message Body:
Here are the lists that you requested.
Attachments:
<<File1.docx>>
<<File2.xml>>
Both attachments contain lists of IP addresses.
For each of the following statements, select Yes if the statement is true. Otherwise, select No. NOTE: Each correct selection is worth one point.
Explanation:
Reference: https://docs.microsoft.com/en-us/microsoft-365/compliance/apply-sensitivity-label-automatically?view=o365-worldwide