Topic 1, Fabrikam, inc Case Study A
Overview:
Existing Environment
Fabrikam, Inc. is an engineering company that has offices throughout Europe. The company has a main office in London and three branch offices in Amsterdam Berlin, and Rome.
Active Directory Environment:
The network contains two Active Directory forests named corp.fabnkam.com and rd.fabrikam.com. There are no trust relationships between the forests. Corp.fabrikam.com is a production forest that contains identities used for internal user and computer authentication. Rd.fabrikam.com is used by the research and development (R&D) department only.
Network Infrastructure:
Each office contains at least one domain controller from the corp.fabrikam.com domain. The main office contains all the domain controllers for the rd.fabrikam.com forest.
All the offices have a high-speed connection to the Internet.
An existing application named WebApp1 is hosted in the data center of the London office. WebApp1 is used by customers to place and track orders. WebApp1 has a web tier that uses Microsoft Internet Information Services (IIS) and a database tier that runs Microsoft SQL Server 2016. The web tier and the database tier are deployed to virtual machines that run on Hyper-V.
The IT department currently uses a separate Hyper-V environment to test updates to WebApp1.
Fabrikam purchases all Microsoft licenses through a Microsoft Enterprise Agreement that includes Software Assurance.
Problem Statement:
The use of Web App1 is unpredictable. At peak times, users often report delays. Al other times, many resources for WebApp1 are underutilized.
Requirements:
Planned Changes:
Fabrikam plans to move most of its production workloads to Azure during the next few years.
As one of its first projects, the company plans to establish a hybrid identity model, facilitating an upcoming Microsoft Office 365 deployment
All R&D operations will remain on-premises.
Fabrikam plans to migrate the production and test instances of WebApp1 to Azure.
Technical Requirements:
Fabrikam identifies the following technical requirements:
• Web site content must be easily updated from a single point.
• User input must be minimized when provisioning new app instances.
• Whenever possible, existing on premises licenses must be used to reduce cost.
• Users must always authenticate by using their corp.fabrikam.com UPN identity.
• Any new deployments to Azure must be redundant in case an Azure region fails.
• Whenever possible, solutions must be deployed to Azure by using platform as a service (PaaS).
• An email distribution group named IT Support must be notified of any issues relating to the directory synchronization services.
• Directory synchronization between Azure Active Directory (Azure AD) and corp.fabhkam.com must not be affected by a link failure between Azure and the on premises network.
Database Requirements:
Fabrikam identifies the following database requirements:
• Database metrics for the production instance of WebApp1 must be available for analysis so that database administrators can optimize the performance settings.
• To avoid disrupting customer access, database downtime must be minimized when databases are migrated.
• Database backups must be retained for a minimum of seven years to meet compliance requirement
Security Requirements:
Fabrikam identifies the following security requirements:
* Company information including policies, templates, and data must be inaccessible to anyone outside the company
* Users on the on-premises network must be able to authenticate to corp.fabrikam.com if an Internet link fails.
* Administrators must be able authenticate to the Azure portal by using their corp.fabrikam.com credentials.
* All administrative access to the Azure portal must be secured by using multi-factor authentication.
* The testing of WebApp1 updates must not be visible to anyone outside the company.
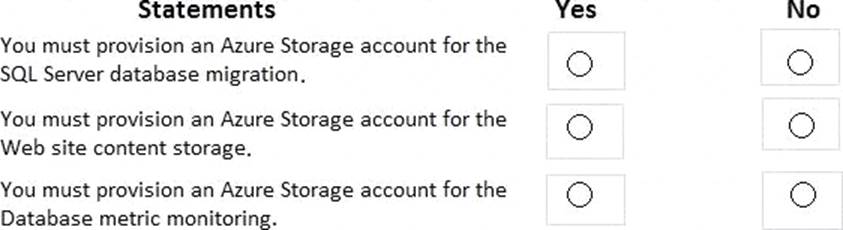
HOTSPOT
You are evaluating the components of the migration to Azure that require you to provision an Azure Storage account.
For each of the following statements, select Yes if the statement is true. Otherwise, select No. NOTE: Each correct selection is worth one point.
You need to recommend a strategy for the web tier of WebApp1. The solution must minimize What should you recommend?
- A . Create a runbook that resizes virtual machines automatically to a smaller size outside of business hours.
- B . Configure the Scale Up settings for a web app.
- C . Deploy a virtual machine scale set that scales out on a 75 percent CPU threshold.
- D . Configure the Scale Out settings for a web app.
You need to recommend a strategy for migrating the database content of WebApp1 to Azure.
What should you include in the recommendation?
- A . Use Azure Site Recovery to replicate the SQL servers to Azure.
- B . Use SQL Server transactional replication.
- C . Copy the BACPAC file that contains the Azure SQL database file to Azure Blob storage.
- D . Copy the VHD that contains the Azure SQL database files to Azure Blob storage
D
Explanation:
Before you upload a Windows virtual machine (VM) from on-premises to Azure, you must prepare the virtual hard disk (VHD or VHDX).
Scenario: WebApp1 has a web tier that uses Microsoft Internet Information Services (IIS) and a database tier that runs Microsoft SQL Server 2016. The web tier and the database tier are deployed to virtual machines that run on Hyper-V.
Reference:
https://docs.microsoft.com/en-us/azure/virtual-machines/windows/prepare-for-upload-vhd-image
You need to recommend a notification solution for the IT Support distribution group.
What should you include in the recommendation?
- A . Azure Network Watcher
- B . an action group
- C . a SendGrid account with advanced reporting
- D . Azure AD Connect Health
D
Explanation:
References: https://docs.microsoft.com/en-us/azure/active-directory/hybrid/how-to-connect-health-operations
You need to recommend a data storage strategy for WebApp1.
What should you include in in the recommendation?
- A . an Azure SQL Database elastic pool
- B . a vCore-baswl Azure SQL database
- C . an Azure virtual machine that runs SQL Server
- D . a fixed-size DTU AzureSQL database.
HOTSPOT
To meet the authentication requirements of Fabrikam, what should you include in the solution? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point.
HOTSPOT
You design a solution for the web tier of WebApp1 as shown in the exhibit.
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
Explanation:
Box 1: Yes
Any new deployments to Azure must be redundant in case an Azure region fails.
Traffic Manager uses DNS to direct client requests to the most appropriate service endpoint based on a traffic-routing method and the health of the endpoints. An endpoint is any Internet-facing service hosted inside or outside of Azure. Traffic Manager provides a range of traffic-routing methods and endpoint monitoring options to suit different application needs and automatic failover models. Traffic Manager is resilient to failure, including the failure of an entire Azure region.
Box 2: Yes
Recent changes in Azure brought some significant changes in autoscaling options for Azure Web Apps (i.e. Azure App Service to be precise as scaling happens on App Service plan level and has effect on all Web Apps running in that App Service plan).
Box 3: No
Traffic Manager provides a range of traffic-routing methods and endpoint monitoring options to suit different application needs and automatic failover models. Traffic Manager is resilient to failure, including the failure of an entire Azure region.
You need to recommend a solution to meet the database retention requirement.
What should you recommend?
- A . Configure a long-term retention policy for the database.
- B . Configure Azure Site Recovery.
- C . Configure geo replication of the database.
- D . Use automatic Azure SQL Database backups.
What should you include in the identity management strategy to support the planned changes?
- A . Move all the domain controllers from corp.fabrikam.com to virtual networks in Azure.
- B . Deploy domain controllers for corp.fabrikam.com to virtual networks in Azure.
- C . Deploy a new Azure AD tenant for the authentication of new R&D projects.
- D . Deploy domain controllers for the rd.fabrikam.com forest to virtual networks in Azure.
B
Explanation:
Directory synchronization between Azure Active Directory (Azure AD) and corp.fabrikam.com must not be affected by a link failure between Azure and the on-premises network. (This requires domain controllers in Azure)
Users on the on-premises network must be able to authenticate to corp.fabrikam.com if an Internet link fails. (This requires domain controllers on-premises)
Topic 2, Contoso, Ltd Case Study B
Overview
Contoso,Ltd is a US-base finance service company that has a main office New York and an office in San Francisco.
Payment Processing Query System
Contoso hosts a business critical payment processing system in its New York data center. The system has three tiers a front-end web app a middle -tier API and a back end data store implemented as a Microsoft SQL Server 2014 database All servers run Windows Server 2012 R2.
The front -end and middle net components are hosted by using Microsoft Internet Inform-non Services (IK) The application rode is written in C# and middle- tier API uses the Entity framework to communicate the SQL Server database. Maintenance of the database e performed by using SQL Server Ago-
The database is currently J IB and is not expected to grow beyond 3 TB.
The payment processing system has the following compliance related requirement
• Encrypt data in transit and at test. Only the front-end and middle-tier components must be able to access the encryption keys that protect the date store.
• Keep backups of the two separate physical locations that are at last 200 miles apart and can be restored for op to seven years.
• Support blocking inbound and outbound traffic based on the source IP address, the description IP address, and the port number
• Collect Windows security logs from all the middle-tier servers and retain the log for a period of seven years,
• Inspect inbound and outbound traffic from the from-end tier by using highly available network appliances.
• Only allow all access to all the tiers from the internal network of Contoso.
Tape backups ate configured by using an on-premises deployment or Microsoft System Center Data protection Manager (DPMX and then shaped ofsite for long term storage
Historical Transaction Query System
Contoso recently migrate a business-Critical workload to Azure. The workload contains a NET web server for querying the historical transaction data residing in azure Table Storage. The NET service is accessible from a client app that was developed in-house and on the client computer in the New Your office. The data in the storage is 50 GB and is not except to increase.
Information Security Requirement
The IT security team wants to ensure that identity management n performed by using Active Directory.
Password hashes must be stored on premises only.
Access to all business-critical systems must rely on Active Directory credentials. Any suspicious authentication attempts must trigger multi-factor authentication prompt automatically Legitimate users must be able to authenticate successfully by using multi-factor authentication.
Planned Changes
Contoso plans to implement the following changes:
* Migrate the payment processing system to Azure.
* Migrate the historical transaction data to Azure Cosmos DB to address the performance issues.
Migration Requirements
Contoso identifies the following general migration requirements:
Infrastructure services must remain available if a region or a data center fails. Failover must occur without any administrative intervention
• Whenever possible. Azure managed serves must be used to management overhead
• Whenever possible, costs must be minimized.
Contoso identifies the following requirements for the payment processing system:
• If a data center fails, ensure that the payment processing system remains available without any administrative intervention. The middle-tier and the web front end must continue to operate without any additional configurations-
• If that the number of compute nodes of the from -end and the middle tiers of the payment processing system can increase or decrease automatically based on CPU utilization.
• Ensure that each tier of the payment processing system is subject to a Service level Agreement (SLA) of 9959 percent availability
• Minimize the effort required to modify the middle tier API and the back-end tier of the payment processing system.
• Generate alerts when unauthorized login attempts occur on the middle-tier virtual machines.
• Insure that the payment processing system preserves its current compliance status.
• Host the middle tier of the payment processing system on a virtual machine.
Contoso identifies the following requirements for the historical transaction query system:
• Minimize the use of on-premises infrastructure service.
• Minimize the effort required to modify the .NET web service querying Azure Cosmos DB.
• If a region fails, ensure that the historical transaction query system remains available without any administrative intervention.
Current Issue
The Contoso IT team discovers poor performance of the historical transaction query as the queries frequently cause table scans.
Information Security Requirements
The IT security team wants to ensure that identity management is performed by using Active Directory.
Password hashes must be stored on-premises only.
Access to all business-critical systems must rely on Active Directory credentials. Any suspicious authentication attempts must trigger a multi-factor authentication prompt automatically. legitimate users must be able to authenticate successfully by using multi-factor authentication.
HOTSPOT
You need to recommend a solution for configuring the Azure Multi-Factor Authentication (MFA) settings.
What should you include in the recommendation? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point.
Explanation:
References:
https://docs.microsoft.com/en-us/azure/active-directory/identity-protection/howto-sign-in-risk-policy
https://docs.microsoft.com/en-us/azure/active-directory/identity-protection/howto-mfa-policy
HOTSPOT
You need to recommend a solution for the users at Contoso to authenticate to the cloud-based services and the Azure AD-integrated applications.
What should you include in the recommendation? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point.
HOTSPOT
You need to recommend a solution for the data store of the historical transaction query system.
What should you include in the recommendation? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point.
You need to recommend a solution for protecting the content of the back-end tier of the payment processing system.
What should you include in the recommendations?
- A . Always Encrypted with deterministic encryption
- B . Transparent Date Encryption (TDE)
- C . Azure Storage Service Encryption
- D . Always Encrypted with randomized encryption
HOTSPOT
You need to recommend a solution for data of the historical transaction query system.
What should you include in the recommendation? To answer, Select the appropriate or options in the answer area. NOTE: Each correct selection is worth one point
You need to recommend a solution for the network configuration of the front-end tier of the payment processing.
What should you include in the recommendation?
- A . Azure Application Gateway
- B . Traffic Manager
- C . a Standard Load Balancer
- D . a Basic load Balancer
C
Explanation:
Scenario:
✑ Ensure that the number of compute nodes of the front-end and the middle tiers of the payment processing system can increase or decrease automatically based on CPU utilization.
✑ Ensure that each tier of the payment processing system is subject to a Service Level Agreement (SLA) of 99.99 percent availability.
With Azure Load Balancer, you can scale your applications and create high availability for your services. Load Balancer supports inbound and outbound scenarios, provides low latency and high throughput, and scales up to millions of flows for all TCP and UDP applications.
Azure Load Balancer is available in two SKUs: Basic and Standard. There are differences in scale, features, and pricing. Standard SLA guarantees a 99.99% for data path with two healthy virtual machines. Basic SLA does not exist.
Reference: https://docs.microsoft.com/en-us/azure/load-balancer/load-balancer-overview
You need to recommend a solution for implementing the back-end tier of the payment processing system in Azure.
What should you include in the recommendation?
- A . an Azure SQL Database managed instance
- B . a SQL Server database on an Azure virtual machine
- C . an Azure SQL Database single database
- D . an Azure SQL Database elastic pool
HOTSPOT
You need to recommend a solution for the user at Contoso to authenticate to the cloud-based sconces and the Azure AD-integrated application.
What should you include in the recommendation? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point.
You need to recommend a compute solution for the middle tier of the payment processing
system.
What should you include in the recommendation?
- A . Azure Kubernetes Service (AKS)
- B . virtual machine scale sets
- C . availability sets
- D . App Service Environments (ASEs)
You need to recommend a disaster recovery solution for the back-end tier of the payment processing system.
What should you include in the recommendation?
- A . Always On Failover Cluster Instances
- B . active geo-replication
- C . Azure Site Recovery
- D . an auto-failover group
D
Explanation:
References: https://docs.microsoft.com/en-us/azure/sql-database/sql-database-auto-failover-group
You need to recommend a backup solution for the data store of the payment processing system.
What should you include in the recommendation?
- A . Microsoft System Center Data Protection Manager (DPM)
- B . Azure Backup Server
- C . Azure SQL long-term backup retention
- D . Azure Managed Disks
C
Explanation:
Reference: https://docs.microsoft.com/en-us/azure/sql-database/sql-database-long-term-backup-retention-configure
HOTSPOT
You need to design a solution for securing access to the historical transaction data.
What should you include in the solution? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point.
You need to recommend a solution for protecting the content of the payment processing system.
What should you include in the recommendation?
- A . Transparent Data Encryption (TDE)
- B . Azure Storage Service Encryption
- C . Always Encrypted with randomized encryption
- D . Always Encrypted with deterministic encryption
You need to recommend a solution for the collection of security logs the middle tier of the payment processing system.
What should you include in the recommendation?
- A . Azure Notification Hubs
- B . the Azure Diagnostics agent
- C . Azure Event Hubs
- D . the Azure Log Analytics agent
D
Explanation:
References: https://docs.microsoft.com/en-us/azure/azure-monitor/platform/diagnostics-extension-overview
You need to recommend a backup solution for the data store of the payment processing.
What should you include in the recommendation?
- A . Microsoft System Center Data Protection Manager (DPM)
- B . long-term retention
- C . a Recovery Services vault
- D . Azure Backup Server
B
Explanation:
References: https://docs.microsoft.com/en-us/azure/sql-database/sql-database-long-term-backup-retention-configure
You need to recommend a high-availability solution for the middle tier of the payment processing system.
What should you include in the recommendation?
- A . availability zones
- B . an availability set
- C . the Premium App Service plan
- D . the Isolated App Server plan
Topic 3, Misc Questions
HOTSPOT
You plan to deploy a network-intensive application to several Azure virtual machines.
You need to recommend a solution that meets the following requirements:
✑ Minimizes the use of the virtual machine processors to transfer data
✑ Minimizes network latency
Which virtual machine size and feature should you use? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point.
Explanation:
References: https://docs.microsoft.com/en-us/azure/virtual-machines/windows/sizes-hpc#h-series
HOTSPOT
You configure the Diagnostics settings for an Azure SQL database as shown in the following exhibit.
Use the drop-down menus to select the answer choice that completes each statement based on the information presented in the graphic. NOTE: Each correct selection is worth one point.
You deploy an Azure virtual machine that runs an ASP.NET application. The application will be accessed from the internet by the users at your company.
You need to recommend a solution to ensure that the users are pre-authenticated by using their Azure Active Directory (Azure AD) account before they can connect to the ASP.NET application
What should you include in the recommendation?
- A . an Azure AD enterprise application
- B . Azure Traffic Manager
- C . a public Azure Load Balancer
- D . Azure Application Gateway
A
Explanation:
You can manage service principals in the Azure portal through the Enterprise Applications experience. Service principals are what govern an application connecting to Azure AD and can be considered the instance of the application in your directory.
Reference: https://docs.microsoft.com/en-us/azure/active-directory/develop/active-directory-how-applications-are-added
DRAG DROP
Your company identifies the following business continuity and disaster recovery objectives for virtual machines that host sales, finance, and reporting application in the company’s on-premises data center.
• The finance application requires that data be retained for seven years. In the event of a disaster, the application must be able to run from Azure. The recovery in objective (RTO) is 10 minutes,
• The reporting application must be able to recover point in-time data al a daily granularity. The RTO is eight hours.
• The sales application must be able to fail over to second on-premises data center.
You need to recommend which Azure services meet the business community and disaster recovery objectives. The solution must minimize costs.
What should you recommend for each application? To answer, drag the appropriate services to the correct application. Each service may be used owe. More than once not at an You may need to drag the spin bar between panes or scroll 10 view content.
Explanation:
1) Sales: Azure Site Recovery only
2) Finance: Azure Site Recovery and Azure Backup
3) Reporting: Azure Backup only
DRAG DROP
You are designing a virtual machine that will run Microsoft SQL Server and will contain two data disks. The first data disk will store log files, and the second data disk will store data. Both disks are P40 managed disks.
You need to recommend a caching policy for each disk. The policy must provide the best overall performance for the virtual machine.
Which caching policy should you recommend for each disk? To answer, drag the appropriate policies to the correct disks. Each policy may be used once, more than once, or not at all. You may need to drag the split bar between panes or scroll to view content. NOTE: Each correct selection is worth one point.
Explanation:
References: https://docs.microsoft.com/en-us/azure/virtual-machines/windows/sql/virtual-machines-windows-sql-performance
You have an on-premises Hyper-V cluster. The cluster contains Hyper-V hosts that run Windows Server 2016 Datacenter. The hosts are licensed under a Microsoft Enterprise Agreement that has Software Assurance.
The Hyper-V cluster hosts 3 virtual machines that run Windows Server 2012 R2. Each virtual machine runs a different workload. The workloads have predictable consumption patterns.
You plan to replace the virtual machines with Azure virtual machines that run Windows
Server 2016. The virtual machines will be sized according to the consumption pattern of each workload.
You need to recommend a solution to minimize the compute costs of the Azure virtual machines.
Which two recommendations should you include in the solution? Each correct answer presents part of the solution. NOTE: Each correct selection is worth one point.
- A . Purchase Azure Reserved Virtual Machine Instances for the Azure virtual machines
- B . Create a virtual machine scale set that uses autoscaling
- C . Configure a spending limit in the Azure account center
- D . Create a lab in Azure DevTest Labs and place the Azure virtual machines in the lab
- E . Activate Azure Hybrid Benefit for the Azure virtual machines
A,E
Explanation:
Reference:
https://azure.microsoft.com/en-us/pricing/reserved-vm-instances/
https://docs.microsoft.com/en-us/azure/virtual-machines/windows/hybrid-use-benefit-licensing
HOTSPOT
You plan to deploy logical Azure SQL Database servers to the East US Azure region and the West US Azure region. Each server will contain 20 databases. Each database will be accessed by a different user who resides in a different on-premises location. The databases will be configured to use active geo-replication.
You need to recommend a solution that meets the following requirements:
✑ Restricts user access to each database
✑ Restricts network access to each database based on each user’s respective location
✑ Ensures that the databases remain accessible from client applications if the local Azure region fails
What should you include in the recommendation? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point.
Transact SQL
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
Your company has deployed several virtual machines (VMs) on-premises and to Azure.
Azure ExpressRoute has been deployed and configured for on-premises to Azure connectivity.
Several VMs are exhibiting network connectivity issues.
You need to analyze the network traffic to determine whether packets are being allowed or denied to the VMs.
Solution: Install and configure the Microsoft Monitoring Agent and the Dependency Agent on all VMs. Use the Wire Data solution in Azure Monitor to analyze the network traffic.
Does the solution meet the goal?
- A . Yes
- B . No
DRAG DROP
Your company has users who work remotely from laptops.
You plan to move some of the applications accessed by the remote users to Azure virtual machines. The users will access the applications in Azure by using a point-to-site VPN connection. You will use certificates generated from an on-premises-based certification authority (CA).
You need to recommend which certificates are required for the deployment.
What should you include in the recommendation? To answer, drag the appropriate certificates to the correct targets. Each certificate may be used once, more than once, or not at all. You may need to drag the split bar between panes or scroll to view content. NOTE: Each correct selection is worth one point.
Your company wants to use an Azure Active Directory (Azure AD) hybrid identity solution.
You need to ensure that users can authenticate if the internet connection to the on-premises Active Directory is unavailable. The solution must minimize authentication prompts for the users.
What should you include in the solution?
- A . an Active Directory Federation Services (AD FS) server
- B . pass-through authentication and Azure AD Seamless Single Sign-On (Azure AD Seamless SSO)
- C . password hash synchronization and Azure AD Seamless Single Sign-On (Azure AD Seamless SSO)
C
Explanation:
With Password hash synchronization + Seamless SSO the authentication is in the cloud.
Reference: https://docs.microsoft.com/en-us/azure/active-directory/hybrid/choose-ad-authn
You have 100 Microsoft SQL Server integration Services (SSIS) packages that are configured to use 10 on-premises SQL Server databases as their destinations.
You plan to migrate the 10 on-premises databases to Azure SQL Database
You need to recommend a solution to host the SSlS packages in Azure. The solution must ensure that the packages can target the SQL Database instances as their destinations.
What should you include in the recommendation?
- A . SQL Server Migration Assistant (SSMA)
- B . Azure Data Catalog
- C . Data Migration Assistant
- D . Azure Data Factory
The developers at your company are building a containerized Python Django app.
You need to recommend platform to host the app.
The solution must meet the following requirements:
✑ Support autoscaling.
✑ Support continuous deployment from an Azure Container Registry.
✑ Provide built-in functionality to authenticate app users by using Azure Active Directory (Azure AD).
Which platform should you include in the recommendation?
- A . Azure Container instances
- B . an Azure App Service instance that uses containers
- C . Azure Kubernetes Service (AKS)
C
Explanation:
To keep up with application demands in Azure Kubernetes Service (AKS), you may need to adjust the number of nodes that run your workloads. The cluster autoscaler component can watch for pods in your cluster that can’t be scheduled because of resource constraints.
When issues are detected, the number of nodes in a node pool is increased to meet the application demand.
Azure Container Registry is a private registry for hosting container images. It integrates well with orchestrators like Azure Container Service, including Docker Swarm, DC/OS, and the new Azure Kubernetes service.
Moreover, ACR provides capabilities such as Azure Active Directory-based authentication, webhook support, and delete operations.
Reference:
https://docs.microsoft.com/en-us/azure/aks/cluster-autoscaler
https://medium.com/velotio-perspectives/continuous-deployment-with-azure-kubernetes-service-azurecontainer-registry-jenkins-ca337940151b
Your company purchases an app named App1.
You need to recommend a solution 10 ensure that App 1 can read and modify access reviews.
What should you recommend?
- A . From the Azure Active Directory admin center, register App1. and then delegate permissions to the Microsoft Graph API.
- B . From the Azure Active Directory admin center, register App1. from the Access control (IAM) blade, delegate permissions.
- C . From API Management services, publish the API of App1. and then delegate
permissions to the Microsoft Graph API. - D . From API Management services, publish the API of App1 From the Access control (IAM) blade, delegate permissions.
B
Explanation:
The app must be registered. You can register the application in the Azure Active Directory admin center.
The Azure AD access reviews feature has an API in the Microsoft Graph endpoint.
You can register an Azure AD application and set it up for permissions to call the access reviews API in Graph.
Reference: https://docs.microsoft.com/en-us/azure/active-directory/develop/quickstart-register-app
You need to design a highly available Azure SQL database that meets the following requirements:
• Failover between replicas of the database must occur without any data loss.
• The database must remain available In the event of a zone outage.
• Costs must be minimized.
Which deployment option should you use?
- A . Azure SQL Database Hyperscale
- B . Azure SQL Database Premium
- C . Azure SQL Database Serverless
- D . Azure SQL Database Managed Instance General Purpose
HOTSPOT
You plan to deploy the backup policy shown in the following exhibit.
Use the drop-down menus to select the answer choice that completes each statement based on the information presented in the graphic. NOTE: Each correct selection is worth one point.
You have 500 Azure web apps in the same Azure region. The apps use a premium Azure Key vault for authentication. A developer reports that some authentication requests are being throttled.
You need 10 recommend a solution to increase the available throughput of the key vault the solution must minimize costs.
What should you recommend?
- A . Increase me number of key vaults in the subscription
- B . Configure geo-replication.
- C . Change the pacing tier.
- D . Configure load balancing for the apps.
You use Azure Application Insights.
You plan to use continuous export.
You need to store Application Insights data for five years.
Which Azure service should you use?
- A . Azure Backup
- B . Azure SQL Database
- C . Azure Storage
- D . Azure Monitor Logs
HOTSPOT
You have a virtual machine scale set named SS1.
You configure autoscaling as shown in the following exhibit.
You configure the scale out and scale in rules to have a duration of 10 minutes and a cool down time of 10 minutes.
Use the drop-down menus to select the answer choice that answers each question based on the information presented in the graphic. NOTE: Each correct selection is worth one point.
Explanation:
Box 1: 20 Minutes. 10 minutes cool down time after the last scale-up plus 10 minutes duration equals 20 minutes.
Box 2: 9 virtual machines. 30% does not match the scale in requirement of less than 25% so the number of virtual machines will not change.
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
You are designing an Azure solution for a company that has four departments. Each department will deploy several Azure app services and Azure SQL databases.
You need to recommend a solution to report the costs for each department to deploy the app services and the databases. The solution must provide a consolidated view for cost reporting that displays cost broken down by department.
Solution: Place all resources in the same resource group. Assign tags to each resource.
Does the solution meet the goal?
- A . Yes
- B . No
B
Explanation:
Instead, create a resources group for each resource type. Assign tags to each resource
Note: Tags enable you to retrieve related resources from different resource groups. This approach is helpful when you need to organize resources for billing or management.
Reference: https://docs.microsoft.com/en-us/azure/azure-resource-manager/resource-group-using-tags
Your company plans to publish APIs for its services by using Azure API Management.
You discover that service responses include the AspNet-Version header.
You need to recommend a solution to remove AspNet-Version from the response of the published APIs.
What should you include in the recommendation?
- A . a new product
- B . a modification to the URL scheme
- C . a new policy
C
Explanation:
References: https://docs.microsoft.com/en-us/azure/api-management/transform-api
Note: This question is part of series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
Your company has an on-premises Active Directory Domain Services (AD DS) domain and an established Azure Active Directory (Azure AD) environment.
Your company would like users to be automatically signed in to cloud apps when they are on their corporate desktops that are connected to the corporate network.
You need to enable single sign-on (SSO) for company users.
Solution: Install and configure an Azure AD Connect server to use password hash synchronization and select the Enable single sign-on option.
Does the solution meet the goal?
- A . Yes
- B . No
A
Explanation:
Azure Active Directory Seamless Single Sign-On (Azure AD Seamless SSO) automatically signs users in when they are on their corporate devices connected to your corporate network. When enabled, users don’t need to type in their passwords to sign in to Azure AD, and usually, even type in their usernames. This feature provides your users easy access to your cloud-based applications without needing any additional on-premises components.
Seamless SSO can be combined with either the Password Hash Synchronization or Pass-through Authentication sign-in methods.
Reference: https://docs.microsoft.com/en-us/azure/active-directory/hybrid/how-to-connect-sso
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
Your company plans to deploy various Azure App Service instances that will use Azure SQL databases. The App Service instances will be deployed at the same time as the Azure SQL databases.
The company has a regulatory requirement to deploy the App Service instances only to specific Azure regions. The resources for the App Service instances must reside in the same region.
You need to recommend a solution to meet the regulatory requirement.
Solution: You recommend using the Regulatory compliance dashboard in Azure Security Center.
Does this meet the goal?
- A . Yes
- B . No
B
Explanation:
The Regulatory compliance dashboard in Azure Security Center is not used for regional compliance.
Note: Instead Azure Resource Policy Definitions can be used which can be applied to a specific Resource Group with the App Service instances.
Note 2: In the Azure Security Center regulatory compliance blade, you can get an overview of key portions of your compliance posture with respect to a set of supported standards. Currently supported standards are Azure CIS, PCI DSS 3.2, ISO 27001, and SOC TSP.
Reference:
https://docs.microsoft.com/en-us/azure/governance/policy/overview
https://azure.microsoft.com/en-us/blog/regulatory-compliance-dashboard-in-azure-security-center-now-available/
You are designing a microservices architecture that will be hosted in an Azure Kubernetes Service (AKS) cluster. Apps that will consume the microservices will be hosted on Azure virtual machines. The virtual machines and the AKS cluster will reside on the same virtual network.
You need to design a solution to expose the microservices to the consumer apps.
The solution must meet the following requirements:
• Ingress access to the microservices must be restricted to a single private IP address and protected by using mutual TLS authentication.
• The number of incoming microservice calls must be rate-limited.
• Costs must be minimized.
What should you include in the solution?
- A . Azure API Management Premium tier with virtual network connection
- B . Azure Front Door with Azure Web Application Firewall (WAF)
- C . Azure API Management Standard tier with a service endpoint
- D . Azure App Gateway with Azure Web Application Firewall (WAF)
A
Explanation:
One option is to deploy APIM (API Management) inside the cluster VNet.
The AKS cluster and the applications that consume the microservices might reside within the same VNet, hence there is no reason to expose the cluster publicly as all API traffic will remain within the VNet. For these scenarios, you can deploy API Management into the cluster VNet. API Management Premium tier supports VNet deployment.
Reference: https://docs.microsoft.com/en-us/azure/api-management/api-management-kubernetes
HOTSPOT
You have an on-premises file server that stores 2 TB of data files.
You plan to move the data files to Azure Blob storage in the Central Europe region.
You need to recommend a storage account type to store the data files and a replication solution for the storage account.
The solution must meet the following requirements:
✑ Be available if a single Azure datacenter fails.
✑ Support storage tiers.
✑ Minimize cost.
What should you recommend? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point.
Explanation:
Box 1: Blob storage
Blob storage supports storage tiers
Note: Azure offers three storage tiers to store data in blob storage: Hot Access tier, Cool Access tier, and Archive tier. These tiers target data at different stages of its lifecycle and offer cost-effective storage options for different use cases.
Box 2: Zone-redundant storage (ZRS)
Data in an Azure Storage account is always replicated three times in the primary region.
Azure Storage offers two options for how your data is replicated in the primary region:
✑ Zone-redundant storage (ZRS) copies your data synchronously across three Azure availability zones in the primary region.
✑ Locally redundant storage (LRS) copies your data synchronously three times within a single physical location in the primary region. LRS is the least expensive replication option, but is not recommended for applications requiring high availability.
References: https://cloud.netapp.com/blog/storage-tiers-in-azure-blob-storage-find-the-best-for-your-data
HOTSPOT
You are designing an access policy for the sales department at your company.
Occasionally, the developers at the company must stop, start, and restart Azure virtual machines. The development team changes often.
You need to recommend a solution to provide the developers with the required access to the virtual machines.
The solution must meet the following requirements:
✑ Provide permissions only when needed.
✑ Use the principle of least privilege.
✑ Minimize costs.
What should you include in the recommendation? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point.
Your company has 300 virtual machines hosted in a VMware environment. The virtual machines vary in size and have various utilization levels.
You plan to move all the virtual machines to Azure.
You need to recommend how many and what size Azure virtual machines will be required to move the current workloads to Azure. The solution must minimize administrative effort.
What should you use to make the recommendation?
- A . Azure Cost Management
- B . Azure Pricing calculator
- C . Azure Migrate
- D . Azure Advisor
A company has a hybrid ASP.NET Web API application that is based on a software as a service (SaaS) offering.
Users report general issues with the data. You advise the company to implement live monitoring and use ad hoc queries on stored JSON data. You also advise the company to set up smart alerting to detect anomalies in the data.
You need to recommend a solution to set up smart alerting.
What should you recommend?
- A . Azure Application Insights and Azure Monitor Logs
- B . Azure Site Recovery and Azure Monitor Logs
- C . Azure Data Lake Analytics and Azure Monitor Logs
- D . Azure Security Center and Azure Data Lake Store
A
Explanation:
https://docs.microsoft.com/en-us/azure/azure-monitor/app/proactive-failure-diagnostics
Application Insights can be used for smart alerting to detect anomalies, whilst Azure Monitor Logs can be used for the live monitoring and use of adhoc queries on stored JSON data
https://docs.microsoft.com/en-us/azure/azure-monitor/app/app-insights-overview
https://docs.microsoft.com/en-us/azure/azure-monitor/platform/data-sources-json
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
You have an Azure Storage account that contains two 1-GB data files named File1 and File2. The data files are set to use the archive access tier.
You need to ensure that File1 is accessible immediately when a retrieval request is initiated.
Solution: For File1, you set Access tier to Hot.
Does this meet the goal?
- A . Yes
- B . No
A
Explanation:
The hot access tier has higher storage costs than cool and archive tiers, but the lowest access costs. Example usage scenarios for the hot access tier include:
✑ Data that’s in active use or expected to be accessed (read from and written to) frequently.
✑ Data that’s staged for processing and eventual migration to the cool access tier.
Reference: https://docs.microsoft.com/en-us/azure/storage/blobs/storage-blob-storage-tiers
You have an Azure Storage account that contains the data shown in the following exhibit.
You need to identify which files can be accessed immediately from the storage account.
Which files should you identify?
- A . File1. bin only
- B . File2.bin only
- C . File3.bin only
- D . File1.bin and File2.bin only
- E . File1.bin File2.bin File3.bin
D
Explanation:
Hot – Optimized for storing data that is accessed frequently. Cool – Optimized for storing data that is infrequently accessed and stored for at least 30 days.
Archive – Optimized for storing data that is rarely accessed and stored for at least 180 days with flexible latency requirements (on the order of hours).
Note: Lease state of the blob. Possible values: available|leased|expired|breaking|broken
Reference: https://docs.microsoft.com/en-us/azure/storage/blobs/storage-blob-storage-tiers
DRAG DROP
You are designing a network connectivity strategy for a new Azure subscription.
You identify the following requirements:
✑ The Azure virtual machines on a subnet named Subnet1 must be accessible only from the computers in your London office.
✑ Engineers require access to the Azure virtual machine on a subnet named Subnet2 over the Internet on a specific TCP/IP management port.
✑ The Azure virtual machines in the West Europe Azure region must be able to communicate on all ports to the Azure virtual machines in the North Europe Azure region.
You need to recommend which components must be used to meet the requirements. The solution must minimize costs and administrative effort whenever possible.
What should you include in the recommendation? To answer, drag the appropriate components to the correct requirements. Each component may be used once, more than once, or not at all. You may need to drag the split bar between panes or scroll to view content. NOTE: Each correct selection is worth one point.
DRAG DROP
Your on-premises network contains a server named Server1 that runs an ASP.NET application named App1.
You have a hybrid deployment of Azure Active Directory (Azure AD).
You need to recommend a solution to ensure that users sign in by using their Azure AD account and Azure Multi-Factor Authentication (MFA) when they connect to App1 from the internet.
Which three Azure services should you recommend be deployed and configured in sequence? To answer, move the appropriate services from the list of services to the answer area and arrange them in the correct order.
AD Enterprise Application
AD Conditional access policy
DRAG DROP
A company has an existing web application that runs on virtual machines (VMs) in Azure.
You need to ensure that the application is protected from SQL injection attempts and uses a layer-7 load balancer. The solution must minimize disruption to the code for the existing web application.
What should you recommend? To answer, drag the appropriate values to the correct items. Each value may be used once, more than once, or not at all. You may need to drag the split bar between panes or scroll to view content. NOTE: Each correct selection is worth one point.
Explanation:
Box 1: Azure Application Gateway
Azure Application Gateway provides an application delivery controller (ADC) as a service. It offers various layer 7 load-balancing capabilities for your applications.
Box 2: Web Application Firwewall (WAF)
Application Gateway web application firewall (WAF) protects web applications from common vulnerabilities and exploits.
This is done through rules that are defined based on the OWASP core rule sets 3.0 or 2.2.9.
There are rules that detects SQL injection attacks.
References:
https://docs.microsoft.com/en-us/azure/application-gateway/application-gateway-faq
https://docs.microsoft.com/en-us/azure/application-gateway/waf-overview
You are designing a microservices architecture that will support a web application.
The solution must meet the following requirements:
✑ Allow independent upgrades to each microservice
✑ Deploy the solution on-premises and to Azure
✑ Set policies for performing automatic repairs to the microservices
✑ Support low-latency and hyper-scale operations
You need to recommend a technology.
What should you recommend?
- A . Azure Service Fabric
- B . Azure Container Service
- C . Azure Container Instance
- D . Azure Virtual Machine Scale Set
A
Explanation:
https://docs.microsoft.com/en-us/azure/service-fabric/service-fabric-overview
You are designing an Azure web app that will use Azure Active Directory (Azure AD) for authentication.
You need to recommend a solution to provide users from multiple Azure AD tenants with access to App1. The solution must ensure that the users use Azure Multi-Factor Authentication (MFA) when they connect to App1.
Which two types of objects should you include in the recommendation? Each correct answer presents part of the solution. NOTE: Each correct selection is worth one point.
- A . Azure AD managed identities
- B . an identity Experience Framework policy
- C . Azure AD conditional access policies
- D . a Microsoft intune app protection policy
- E . an Azure application security group
- F . Azure AD guest accounts
A,C
Explanation:
https://docs.microsoft.com/en-us/azure/active-directory/develop/v2-conditional-access-dev-guide
https://docs.microsoft.com/en-us/azure/active-directory/conditional-access/howto-conditional-access-policy-azure-management
You need to recommend a data storage solution that meets the following requirements:
• Ensures that applications can access the data by using a REST connection
• Hosts 20 independent tables of varying sizes and usage patterns
• Automatically replicates the data to a second Azure region
• Minimizes costs
What should you recommend?
- A . an Azure SQL Database that uses active geo-replication
- B . tables in an Azure Storage account that use geo-redundant storage (GRS)
- C . tables in an Azure Storage account that use read-access geo-redundant storage (RA-GRS)
- D . an Azure SQL Database elastic database pool that uses active geo-replication
You manage an Azure environment for a company. The environment has over 25,000 licensed users and 100 mission-critical applications. You need to recommend a solution that provides advanced user threat detection and remediation strategies.
What should you recommend?
- A . Azure Active Directory (Azure AD) Identity Protection
- B . Azure Active Directory Federation Services (AD FS)
- C . Azure Active Directory (Azure AD) authentication
- D . Microsoft Identity Manager
- E . Azure Active Directory (Azure AD) Connect
HOTSPOT
Your on-premises network contains a file server named Server1 that stores 500 GB of data.
You need to use Azure Data Factory to copy the data from Server1 to Azure Storage.
You add a new data factory.
What should you do next? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point.
Explanation:
Box 1: Install a self-hosted integration runtime
The Integration Runtime is a customer-managed data integration infrastructure used by Azure Data Factory to provide data integration capabilities across different network environments.
Box 2: Create a pipeline
With ADF, existing data processing services can be composed into data pipelines that are highly available and managed in the cloud. These data pipelines can be scheduled to ingest, prepare, transform, analyze, and publish data, and ADF manages and orchestrates the complex data and processing dependencies
References: https://docs.microsoft.com/en-us/azure/machine-learning/team-data-science-process/move-sql-azure-adf
You have an Azure subscription that contains a storage account.
An application sometimes writes duplicate files to the storage account.
You have a PowerShell script that identifies and deletes duplicate files in the storage account. Currently, the script is run manually after approval from the operations manager.
You need to recommend a serverless solution that performs the following actions:
✑ Runs the script once an hour to identify whether duplicate files exist
✑ Sends an email notification to the operations manager requesting approval to delete the duplicate files
✑ Processes an email response from the operations manager specifying whether the deletion was approved
✑ Runs the script if the deletion was approved
What should you include in the recommendation?
- A . Azure Logic Apps and Azure Functions
- B . Azure Pipelines and Azure Service Fabric
- C . Azure Logic Apps and Azure Event Grid
- D . Azure Functions and Azure Batch
A
Explanation:
You can schedule a powershell script with Azure Logic Apps.
When you want to run code that performs a specific job in your logic apps, you can create your own function by using Azure Functions. This service helps you create Node.js, C#, and F# functions so you don’t have to build a complete app or infrastructure to run code. You can also call logic apps from inside Azure functions. Azure Functions provides serverless computing in the cloud and is useful for performing tasks such as these examples:
Reference: https://docs.microsoft.com/en-us/azure/logic-apps/logic-apps-azure-functions
You have 100 servers that run Windows Server 2012 R2 and host Microsoft SQL Server 2012 R2 instances.
The instances host databases that have the following characteristics:
✑ The largest database is currently 3 TB. None of the databases will ever exceed 4 TB.
✑ Stored procedures are implemented by using CLR.
You plan to move all the data from SQL Server to Azure.
You need to recommend an Azure service to host the databases.
The solution must meet the following requirements:
✑ Whenever possible, minimize management overhead for the migrated databases.
✑ Minimize the number of database changes required to facilitate the migration.
✑ Ensure that users can authenticate by using their Active Directory credentials.
What should you include in the recommendation?
- A . Azure SQL Database single databases
- B . Azure SQL Database Managed Instance
- C . Azure SQL Database elastic pools
- D . SQL Server 2016 on Azure virtual machines
B
Explanation:
References: https://docs.microsoft.com/en-us/azure/sql-database/sql-database-managed-instance
Your company, named Contoso, Ltd, implements several Azure logic apps that have HTTP triggers: The logic apps provide access to an on-premises web service.
Contoso establishes a partnership with another company named Fabrikam, Inc.
Fabrikam does not have an existing Azure Active Directory (Azure AD) tenant and uses third-party OAuth 2.0 identity management to authenticate its users.
Developers at Fabrikam plan to use a subset of the logics apps to build applications that will integrate with the on-premises web service of Contoso.
You need to design a solution to provide the Fabrikam developers with access to the logic apps.
The solution must meet the following requirements:
✑ Requests to the logic apps from the developers must be limited to lower rates than the requests from the users at Contoso.
✑ The developers must be able to rely on their existing OAuth 2.0 provider to gain access to the logic apps.
✑ The solution must NOT require changes to the logic apps.
✑ The solution must NOT use Azure AD guest accounts.
What should you include in the solution?
- A . Azure AD business-to-business (B2B)
- B . Azure Front Door
- C . Azure API Management
- D . Azure AD Application Proxy
C
Explanation:
API Management helps organizations publish APIs to external, partner, and internal developers to unlock the potential of their data and services.
You can secure API Management using the OAuth 2.0 client credentials flow.
Reference: https://docs.microsoft.com/en-us/azure/api-management/api-management-key-concepts
HOTSPOT
You have an Azure Active Directory (Azure AD) tenant.
You plan to use Azure Monitor to monitor user sign-ins and generate alerts based on specific user sign-in events.
You need to recommend a solution to trigger the alerts based on the events.
What should you include in the recommendation? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point.
Explanation:
Box 1: An Azure Log Analytics workspace
To be able to create an alert we send the Azure AD logs to An Azure Log Analytics workspace.
Note: You can forward your AAD logs and events to either an Azure Storage Account, an Azure Event Hub, Log Analytics, or a combination of all of these.
Box 2: Log
Ensure Resource Type is an analytics source like Log Analytics or Application Insights and signal type as Log.
You have an Azure Active Directory (Azure AD) tenant named contoso.com that contains several administrative user accounts. You need to recommend a solution to identify which administrative user accounts have NOT signed in during the previous 30 days.
Which service should you include in the recommendation?
- A . Azure AD Identity Protection
- B . Azure AD Privileged identity Management (PIM)
- C . Azure Advisor
- D . Azure Activity log
B
Explanation:
https://docs.microsoft.com/en-us/azure/active-directory/privileged-identity-management/pim-how-to-use-audit-log?tabs=new
You have multiple Anne deployments.
You plan to implement Azure Blueprints.
Which artifact types can be added to a blueprint?
- A . Policy assignment Resource group, Role assignment virtual machines, and virtual networks only
- B . Subscriptions. tenants. Resource group, and Key vault only
- C . Subscriptions. tenants. Resource group, and Azure Active Directory only
- D . Azure Resource Manager template (Subscription). Policy assignment Resource group, and Role assignment only
You have an on-premises network to which you deploy a virtual appliance.
You plan to deploy several Azure virtual machines and connect the on-premises network to Azure by using a Site-to-Site connection.
All network traffic that will be directed from the Azure virtual machines to a specific subnet must flow through the virtual appliance.
You need to recommend solutions to manage network traffic.
Which two options should you recommend? Each correct answer presents a complete solution.
- A . Configure Azure Traffic Manager.
- B . Implement an Azure virtual network.
- C . Implement Azure ExpressRoute.
- D . Configure a routing table.
C,D
Explanation:
Connectivity can be from an any-to-any (IP VPN) network, a point-to-point Ethernet network, or a virtual cross-connection through a connectivity provider at a co-location facility. ExpressRoute connections do not go over the public Internet. This allows ExpressRoute connections to offer more reliability, faster speeds, lower latencies, and higher security than typical connections over the Internet.
Reference:
https://docs.microsoft.com/en-us/azure/vpn-gateway/vpn-gateway-forced-tunneling-rm
https://docs.microsoft.com/en-us/azure/expressroute/expressroute-introduction
HOTSPOT
You are building an application that will run in a virtual machine (VM). The application will use Azure Managed Identity.
The application uses Azure Key Vault, Azure SQL Database, and Azure Cosmos DB.
You need to ensure the application can use secure credentials to access these services.
Which authentication method should you recommend? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point.
Explanation:
Note: Managed identities for Azure resources is the new name for the service formerly known as Managed Service Identity (MSI).
HOTSPOT
You plan to create an Azure environment that will contain a root management group and 10 child management groups. Each child management group will contain five Azure subscriptions. You plan to have between 10 and 30 resource groups in each subscription.
You need to design an Azure governance solution.
The solution must meet the following requirements:
• Use Azure Blueprints to control governance across all the subscriptions and resource groups.
• Ensure that Blueprints-based configurations are consistent across all the subscriptions and resource groups.
• Minimize the number of blueprint definitions and assignments.
What should you include in the solution? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point.
Explanation:
HOTSPOT
You plan to create an Azure environment that will contain a root management group and 10 child management groups. Each child management group will contain five Azure subscriptions. You plan to have between 10 and 30 resource groups in each subscription.
You need to design an Azure governance solution.
The solution must meet the following requirements:
• Use Azure Blueprints to control governance across all the subscriptions and resource groups.
• Ensure that Blueprints-based configurations are consistent across all the subscriptions and resource groups.
• Minimize the number of blueprint definitions and assignments.
What should you include in the solution? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point.
Explanation:
HOTSPOT
You plan to create an Azure environment that will contain a root management group and 10 child management groups. Each child management group will contain five Azure subscriptions. You plan to have between 10 and 30 resource groups in each subscription.
You need to design an Azure governance solution.
The solution must meet the following requirements:
• Use Azure Blueprints to control governance across all the subscriptions and resource groups.
• Ensure that Blueprints-based configurations are consistent across all the subscriptions and resource groups.
• Minimize the number of blueprint definitions and assignments.
What should you include in the solution? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point.
Explanation:
You have an Azure subscription that contains an Azure Blob storage account named store1.
You have an on-premises file server named Setver1 that runs Windows Sewer 2016.
Server1 stores 500 GB of company files.
You need to store a copy of the company files from Server 1 in store1.
Which two possible Azure services achieve this goal? Each correct answer presents a complete solution. NOTE: Each correct selection is worth one point
- A . an Azure Batch account
- B . an integration account
- C . an On-premises data gateway
- D . an Azure Import/Export job
- E . Azure Data factory
HOTSPOT
You have a web application that uses a MongoDB database. You plan to migrate the web application to Azure.
You must migrate to Cosmos DB while minimizing code and configuration changes.
You need to design the Cosmos DB configuration.
What should you recommend? To answer, select the appropriate values in the answer area. NOTE: Each correct selection is worth one point.
Explanation:
MongoDB compatibility: API
✑ API: MongoDB API
✑ Azure Cosmos DB comes with multiple APIs:
✑ SQL API, a JSON document database service that supports SQL queries.
This is compatible with the former Azure DocumentDB.
✑ MongoDB API, compatible with existing Mongo DB libraries, drivers, tools and applications.
✑ Cassandra API, compatible with existing Apache Cassandra libraries, drivers, tools, and applications.
✑ Azure Table API, a key-value database service compatible with existing Azure Table Storage.
✑ Gremlin (graph) API, a graph database service supporting Apache Tinkerpop’s graph traversal language, Gremlin.
References: https://docs.microsoft.com/en-us/azure/cosmos-db/create-mongodb-dotnet
You have a hybrid deployment of Azure Active Directory (Azure AD).
You need to recommend a solution to ensure that the Azure AD tenant can be managed only from the computers on your on-premises network.
What should you include in the recommendation?
- A . Azure AD roles and administrators
- B . Azure AD Privileged identity Management
- C . A conditional access policy
- D . Azure AD Application Proxy
A company named Contoso, Ltd. has an Azure Active Directory (Azure AD) tenant that is integrated with Microsoft Office 365 and an Azure subscription.
Contoso has an on-premises identity infrastructure. The infrastructure includes servers that run Active Directory Domain Services (AD DS), Active Directory Federation Services (AD FS), Azure AD Connect, and Microsoft Identity Manager (MIM).
Contoso has a partnership with a company named Fabrikam, Inc. Fabrikam has an Active Directory forest and an Office 365 tenant. Fabrikam has the same on-premises identity infrastructure as Contoso.
A team of 10 developers from Fabrikam will work on an Azure solution that will be hosted in the Azure subscription of Contoso. The developers must be added to the Contributor role for a resource in the Contoso subscription.
You need to recommend a solution to ensure that Contoso can assign the role to the 10 Fabrikam developers. The solution must ensure that the Fabrikam developers use their existing credentials to access resources.
What should you recommend?
- A . Configure a forest trust between the on-premises Active Directory forests of Contoso and Fabrikam.
- B . Configure an organization relationship between the Office 365 tenants of Fabrikam and Contoso.
- C . In the Azure AD tenant of Contoso, use MIM to create guest accounts for the Fabrikam developers.
- D . Configure an AD FS relying party trust between the fabrikam and Contoso AD FS infrastructures.
A
Explanation:
Trust configurations – Configure trust from managed forests(s) or domain(s) to the administrative forest
✑ A one-way trust is required from production environment to the admin forest.
✑ Selective authentication should be used to restrict accounts in the admin forest to only logging on to the appropriate production hosts.
References: https://docs.microsoft.com/en-us/windows-server/identity/securing-privileged-access/securing-privileged-access-reference-material
You have 70 TB of files on your on-premises file server.
You need to recommend solution for importing data to Azure. The solution must minimize cost.
What Azure service should you recommend?
- A . Azure StorSimple
- B . Azure Batch
- C . Azure Data Box
- D . Azure Stack
C
Explanation:
Microsoft has engineered an extremely powerful solution that helps customers get their data to the Azure public cloud in a cost-effective, secure, and efficient manner with powerful Azure and machine learning at play. The solution is called Data Box.
Data Box and is in general availability status. It is a rugged device that allows organizations to have 100 TB of capacity on which to copy their data and then send it to be transferred to Azure.
Reference: https://www.vembu.com/blog/what-is-microsoft-azure-data-box-disk-edge-heavy-gateway-overview/
You have an Azure Active Directory (Azure AD) tenant and Windows 10 devices.
You configure a conditional access policy as shown in the exhibit. (Click the Exhibit tab.)
What is the result of the policy?
- A . All users will always be prompted for multi-factor authentication (MFA).
- B . Users will be prompted for multi-factor authentication (MFA) only when they sign in from devices that are NOT joined to Azure AD.
- C . All users will be able to sign in without using multi-factor authentication (MFA).
- D . Users will be prompted for multi-factor authentication (MFA) only when they sign in from
devices that are joined to Azure AD.
C
Explanation:
https://docs.microsoft.com/en-us/azure/active-directory/authentication/tutorial-enable-azure-mfa "Conditional Access policies can be set to Report-only if you want to see how the configuration would impact users, or Off if you don’t want to the use policy right now. As a test group of users was targeted for this tutorial, lets enable the policy and then test Azure AD Multi-Factor Authentication.
HOTSPOT
You have the application architecture shown in the following exhibit.
Use the drop-down menus to select choice that completes each statement based on the information presented in the graphic. NOTE: Each correct selection is worth one point.
Explanation:
References:
https://docs.microsoft.com/en-us/azure/traffic-manager/traffic-manager-routing-methods
https://docs.microsoft.com/en-us/azure/traffic-manager/traffic-manager-monitoring
HOTSPOT
You are designing a software as a service (SaaS) application that will enable Azure Active Directory (Azure AD) users to create and publish surveys. The SaaS application will have a front-end web app and a back-end web API. The web app will rely on the web API to handle updates to customer surveys.
You need to design an authorization flow for the SaaS application.
The solution must meet the following requirements:
✑ To access the back-end web API, the web app must authenticate by using OAuth 2 bearer tokens.
✑ The web app must authenticate by using the identities of individual users.
What should you include in the solution? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point.
Explanation:
References:
https://docs.microsoft.com/lb-lu/azure/architecture/multitenant-identity/web-api
https://docs.microsoft.com/en-us/azure/active-directory/develop/quickstart-v1-dotnet-webapi
HOTSPOT
Your company has 20 web APIs that were developed in-house.
The company is developing 10 web apps that will use the web APIs. The web apps and the APIs are registered in the company’s Azure Active Directory (Azure AD) tenant. The web APIs are published by using Azure API Management.
You need to recommend a solution to block unauthorized requests originating from the web apps from reaching the web APIs.
The solution must meet the following requirements:
✑ Use Azure AD-generated claims.
✑ Minimize configuration and management effort.
What should you include in the recommendation? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point.
Explanation:
HOTSPOT
Your company has 20 web APIs that were developed in-house.
The company is developing 10 web apps that will use the web APIs. The web apps and the APIs are registered in the company’s Azure Active Directory (Azure AD) tenant. The web APIs are published by using Azure API Management.
You need to recommend a solution to block unauthorized requests originating from the web apps from reaching the web APIs.
The solution must meet the following requirements:
✑ Use Azure AD-generated claims.
✑ Minimize configuration and management effort.
What should you include in the recommendation? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point.
Explanation:
HOTSPOT
Your company has 20 web APIs that were developed in-house.
The company is developing 10 web apps that will use the web APIs. The web apps and the APIs are registered in the company’s Azure Active Directory (Azure AD) tenant. The web APIs are published by using Azure API Management.
You need to recommend a solution to block unauthorized requests originating from the web apps from reaching the web APIs.
The solution must meet the following requirements:
✑ Use Azure AD-generated claims.
✑ Minimize configuration and management effort.
What should you include in the recommendation? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point.
Explanation:
HOTSPOT
Your company has 20 web APIs that were developed in-house.
The company is developing 10 web apps that will use the web APIs. The web apps and the APIs are registered in the company’s Azure Active Directory (Azure AD) tenant. The web APIs are published by using Azure API Management.
You need to recommend a solution to block unauthorized requests originating from the web apps from reaching the web APIs.
The solution must meet the following requirements:
✑ Use Azure AD-generated claims.
✑ Minimize configuration and management effort.
What should you include in the recommendation? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point.
Explanation:
HOTSPOT
Your company has 20 web APIs that were developed in-house.
The company is developing 10 web apps that will use the web APIs. The web apps and the APIs are registered in the company’s Azure Active Directory (Azure AD) tenant. The web APIs are published by using Azure API Management.
You need to recommend a solution to block unauthorized requests originating from the web apps from reaching the web APIs.
The solution must meet the following requirements:
✑ Use Azure AD-generated claims.
✑ Minimize configuration and management effort.
What should you include in the recommendation? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point.
Explanation: