SRX Series device enrollment with Policy Enforcer fails To debug further, the user issues the following commandshow configuration services security―intelligence url
https://cloudfeeds.argon.juniperaecurity.net/api/manifeat.xml
and receives the following output:
What is the problem in this scenario?
- A . The device is directly enrolled with Juniper ATP Cloud.
- B . The device is already enrolled with Policy Enforcer.
- C . The SRX Series device does not have a valid license.
- D . Junos Space does not have matching schema based on the
You are asked to deploy filter-based forwarding on your SRX Series device for incoming traffic sourced from the 10.10 100 0/24 network in this scenario, which three statements are correct? (Choose three.)
- A . You must create a forwarding-type routing instance.
- B . You must create and apply a firewall filter that matches on the source address 10.10.100.0/24 and then sends this traffic to your routing
- C . You must create and apply a firewall filter that matches on the destination address 10 10.100.0/24 and then sends this traffic to your routing instance.
- D . You must create a RIB group that adds interface routes to your routing instance.
- E . You must create a VRF-type routing instance.
You are asked to provide single sign-on (SSO) to Juniper ATP Cloud.
Which two steps accomplish this goal? (Choose two.)
- A . Configure Microsoft Azure as the service provider (SP).
- B . Configure Microsoft Azure as the identity provider (IdP).
- C . Configure Juniper ATP Cloud as the service provider (SP).
- D . Configure Juniper ATP Cloud as the identity provider (IdP).
You want to identify potential threats within SSL-encrypted sessions without requiring SSL proxy to decrypt the session contents.
Which security feature achieves this objective?
- A . infected host feeds
- B . encrypted traffic insights
- C . DNS security
- D . Secure Web Proxy
Exhibit
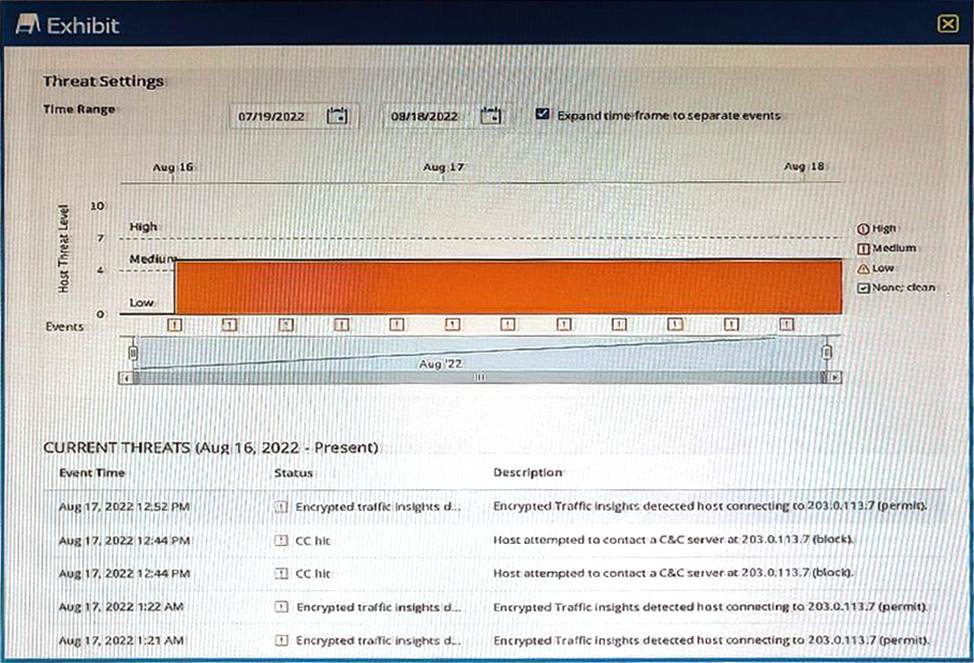
You are using ATP Cloud and notice that there is a host with a high number of ETI and C&C hits sourced from the same investigation and notice that some of the events have not been automatically mitigated.
Referring to the exhibit, what is a reason for this behavior?
- A . The C&C events are false positives.
- B . The infected host score is globally set bellow a threat level of 5.
- C . The infected host score is globally set above a threat level of 5.
- D . The ETI events are false positives.
Exhibit
Which statement is true about the output shown in the exhibit?
- A . The SRX Series device is configured with default security forwarding options.
- B . The SRX Series device is configured with packet-based IPv6 forwarding options.
- C . The SRX Series device is configured with flow-based IPv6 forwarding options.
- D . The SRX Series device is configured to disable IPv6 packet forwarding.
Exhibit
You are implementing filter-based forwarding to send traffic from the 172.25.0.0/24 network through ISP-1 while sending all other traffic through your connection to ISP-2. Your ge-0/0/1 interface connects to two networks, including the 172.25.0.0/24 network. You have implemented the configuration shown in the exhibit. The traffic from the 172.25.0.0/24 network is being forwarded as expected to 172.20.0.2, however traffic from the other network (172.25.1.0/24) is not being forwarded to the upstream 172.21.0.2 neighbor.
In this scenario, which action will solve this problem?
- A . You must specify that the 172.25.1.1/24 IP address is the primary address on the ge-0/0/1 interface.
- B . You must apply the firewall filter to the lo0 interface when using filter-based forwarding.
- C . You must add another term to the firewall filter to accept the traffic from the 172.25.1.0/24 network.
- D . You must create the static default route to neighbor 172.21 0.2 under the ISP-1 routing instance hierarchy.
Exhibit
You configure a traceoptions file called radius on your returns the output shown in the exhibit
What is the source of the problem?
- A . An incorrect password is being used.
- B . The authentication order is misconfigured.
- C . The RADIUS server IP address is unreachable.
- D . The RADIUS server suffered a hardware failure.
Your Source NAT implementation uses an address pool that contains multiple IPv4 addresses Your users report that when they establish more than one session with an external application, they are prompted to authenticate multiple times External hosts must not be able to establish sessions with internal network hosts
What will solve this problem?
- A . Disable PAT.
- B . Enable destination NAT.
- C . Enable persistent NAT
- D . Enable address persistence.
What is the purpose of the Switch Microservice of Policy Enforcer?
- A . to isolate infected hosts
- B . to enroll SRX Series devices with Juniper ATP Cloud
- C . to inspect traffic for malware
- D . to synchronize security policies to SRX Series devices
Exhibit
Referring to the exhibit, which statement is true?
- A . This custom block list feed will be used before the Juniper Seclntel
- B . This custom block list feed cannot be saved if the Juniper Seclntel block list feed is configured.
- C . This custom block list feed will be used instead of the Juniper Seclntel block list feed
- D . This custom block list feed will be used after the Juniper Seclntel block list feed.
Exhibit
The exhibit shows a snippet of a security flow trace.
In this scenario, which two statements are correct? (Choose two.)
- A . This packet arrived on interface ge-0/0/4.0.
- B . Destination NAT occurs.
- C . The capture is a packet from the source address 172.20.101.10 destined to 10.0.1.129.
- D . An existing session is found in the table.
Regarding IPsec CoS-based VPNs, what is the number of IPsec SAs associated with a peer based upon?
- A . The number of traffic selectors configured for the VPN.
- B . The number of CoS queues configured for the VPN.
- C . The number of classifiers configured for the VPN.
- D . The number of forwarding classes configured for the VPN.
Exhibit
You are trying to configure an IPsec tunnel between SRX Series devices in the corporate office and branch1. You have committed the configuration shown in the exhibit, but the IPsec tunnel is not establishing.
In this scenario, what would solve this problem.
- A . Add multipoint to the st0.0 interface configuration on the branch1 device.
- B . Change the IKE proposal-set to compatible on the branch1 and corporate devices.
- C . Change the local identity to inet advpn on the branch1 device.
- D . Change the IKE mode to aggressive on the branch1 and corporate devices.
You want to configure a threat prevention policy.
Which three profiles are configurable in this scenario? (Choose three.)
- A . device profile
- B . SSL proxy profile
- C . infected host profile
- D . C&C profile
- E . malware profile
You are asked to detect domain generation algorithms
Which two steps will accomplish this goal on an SRX Series firewall? (Choose two.)
- A . Define an advanced-anti-malware policy under [edit services].
- B . Attach the security-metadata-streaming policy to a security
- C . Define a security-metadata-streaming policy under [edit
- D . Attach the advanced-anti-malware policy to a security policy.
You are deploying a virtualization solution with the security devices in your network Each SRX Series device must support at least 100 virtualized instances and each virtualized instance must have its own discrete administrative domain.
In this scenario, which solution would you choose?
- A . VRF instances
- B . virtual router instances
- C . logical systems
- D . tenant systems
Exhibit
You configure Source NAT using a pool of addresses that are in the same subnet range as the external ge-0/0/0 interface on your vSRX device. Traffic that is exiting the internal network can reach external destinations, but the return traffic is being dropped by the service provider router.
Referring to the exhibit, what must be enabled on the vSRX device to solve this problem?
- A . STUN
- B . Proxy ARP
- C . Persistent NAT
- D . DNS Doctoring
Exhibit
An administrator wants to configure an SRX Series device to log binary security events for tenant systems.
Referring to the exhibit, which statement would complete the configuration?
- A . Configure the tenant as TSYS1 for the pi security profile.
- B . Configure the tenant as root for the pi security profile.
- C . Configure the tenant as master for the pi security profile.
- D . Configure the tenant as local for the pi security profile
Your company wants to use the Juniper Seclntel feeds to block access to known command and control servers, but they do not want to use Security Director to manage the feeds.
Which two Juniper devices work in this situation? (Choose two)
- A . EX Series devices
- B . MX Series devices
- C . SRX Series devices
- D . QFX Series devices
Your IPsec VPN configuration uses two CoS forwarding classes to separate voice and data traffic.
How many IKE security associations are required between the IPsec peers in this scenario?
- A . 1
- B . 3
- C . 4
- D . 2
Exhibit
Referring to the exhibit, which two statements are true? (Choose two.)
- A . The SRX-1 device can use the Proxy__Nodes feed in another security policy.
- B . You can use the Proxy_Nodes feed as the source-address and destination-address match criteria of another security policy on a different SRX Series device.
- C . The SRX-1 device creates the Proxy_wodes feed, so it cannot use it in another security policy.
- D . You can only use the Proxy_Node3 feed as the destination-address match criteria of another security policy on a different SRX Series device.
You are connecting two remote sites to your corporate headquarters site.You must ensure that all traffic is secured and sent directly between sites In this scenario, which VPN should be used?
- A . IPsec ADVPN
- B . hub-and-spoke IPsec VPN
- C . Layer 2 VPN
- D . full mesh Layer 3 VPN with EBGP
All interfaces involved in transparent mode are configured with which protocol family?
- A . mpls
- B . bridge
- C . inet
- D . ethernet ― switching
Exhibit
You are using traceoptions to verify NAT session information on your SRX Series device.
Referring to the exhibit, which two statements are correct? (Choose two.)
- A . This is the last packet in the session.
- B . The SRX Series device is performing both source and destination NAT on this session.
- C . This is the first packet in the session.
- D . The SRX Series device is performing only source NAT on this session.
You are asked to determine if the 203.0.113.5 IP address has been added to the third-party security feed, DS hield, from Juniper Seclnte1. You have an SRX Series device that is using Seclnte1 feeds from Juniper ATP Cloud
Which command will return this information?
- A . show security dynamic―address category―name CC | match 203.0.113.5
- B . show security dynamic―address category―name Infected―Hosts | match 203.0.113.5
- C . show security dynamic-address category-name IPFilter I match 203.0.113.5
- D . show Security dynamic-address category-name JWAS | match 203.0.113.5
You want to enroll an SRX Series device with Juniper ATP Appliance. There is a firewall device in the path between the devices.
In this scenario, which port should be opened in the firewall device?
- A . 8080
- B . 443
- C . 80
- D . 22
Exhibit
Which two statements are correct about the output shown in the exhibit. (Choose two.)
- A . The source address is translated.
- B . The packet is an SSH packet
- C . The packet matches a user-configured policy
- D . The destination address is translated.
Which two types of source NAT translations are supported in this scenario? (Choose two.)
- A . translation of IPv4 hosts to IPv6 hosts with or without port address translation
- B . translation of one IPv4 subnet to one IPv6 subnet with port address translation
- C . translation of one IPv6 subnet to another IPv6 subnet without port address translation
- D . translation of one IPv6 subnet to another IPv6 subnet with port address translation
Which statement is true about persistent NAT types?
- A . The target-host-port parameter cannot be used with IPv4 addresses in NAT46.
- B . The target-host parameter cannot be used with IPv6 addressee in NAT64.
- C . The target-host parameter cannot be used with IPv4 addresses inNAT46
- D . The target-host-port parameter cannot be used with IPv6 addresses in NAT64
Exhibit
Referring to the exhibit, which two statements are true? (Choose two.)
- A . The 3uspicious_Endpoint3 feed is only usable by the SRX-1 device.
- B . You must manually create the suspicious_Endpoint3 feed in the Juniper ATP Cloud interface.
- C . The 3uspiciou3_Endpoint3 feed is usable by any SRX Series device that is a part of the same realm as SRX-1
- D . Juniper ATP Cloud automatically creates the 3uopi’cioua_Endpoints feed after you commit the security policy.
Exhibit
Referring to the exhibit, a spoke member of an ADVPN is not functioning correctly.
Which two commands will solve this problem? (Choose two.)
A)
B)
C)
D)
- A . Option A
- B . Option B
- C . Option C
- D . Option D
In Juniper ATP Cloud, what are two different actions available in a threat prevention policy to deal with an infected host? (Choose two.)
- A . Send a custom message
- B . Close the connection.
- C . Drop the connection silently.
- D . Quarantine the host.
You are required to deploy a security policy on an SRX Series device that blocks all known Tor network IP addresses.
Which two steps will fulfill this requirement? (Choose two.)
- A . Enroll the devices with Juniper ATP Appliance.
- B . Enroll the devices with Juniper ATP Cloud.
- C . Enable a third-party Tor feed.
- D . Create a custom feed containing all current known MAC addresses.
Exhibit
Which two statements are correct about the output shown in the exhibit? (Choose two.)
- A . The packet is processed as host inbound traffic.
- B . The packet matches the default security policy.
- C . The packet matches a configured security policy.
- D . The packet is processed in the first path packet flow.
Exhibit
You are not able to ping the default gateway of 192.168 100 1 (or your network that is located on your SRX Series firewall.
Referring to the exhibit, which two commands would correct the configuration of your SRX Series device? (Choose two.)
A)
B)
C)
D)
- A . Option A
- B . Option B
- C . Option C
- D . Option D
Exhibit
You have configured the SRX Series device to switch packets for multiple directly connected hosts that are within the same broadcast domain However, the traffic between two hosts in the same broadcast domain are not matching any security policies
Referring to the exhibit, what should you do to solve this problem?
- A . You must change the global mode to security switching mode.
- B . You must change the global mode to security bridging mode
- C . You must change the global mode to transparent bridge mode.
- D . You must change the global mode to switching mode.
You are asked to download and install the IPS signature database to a device operating in chassis cluster mode.
Which statement is correct in this scenario?
- A . You must download and install the IPS signature package on the primary node.
- B . The first synchronization of the backup node and the primary node must be performed manually.
- C . The first time you synchronize the IPS signature package from the primary node to the backup node, the primary node must be rebooted.
- D . The IPS signature package must be downloaded and installed on the primary and backup nodes.
Exhibit
Your company recently acquired a competitor. You want to use using the same IPv4 address space as your company.
Referring to the exhibit, which two actions solve this problem? (Choose two)
- A . Configure static NAT on the SRX Series devices.
- B . Connect the competitor network using IPsec policy-based VPNs.
- C . Identify two neutral IPv4 address spaces for address translation.
- D . Configure IPsec Transport mode.
What are two valid modes for the Juniper ATP Appliance? (Choose two.)
- A . flow collector
- B . event collector
- C . all-in-one
- D . core