Which Junos security feature is used for signature-based attack prevention?
- A . RADIUS
- B . AppQoS
- C . IPS
- D . PIM
Using content filtering on an SRX Series device, which three types of HTTP content are able to be blocked? (Choose three.)
- A . PDF files
- B . ZIP files
- C . Java applets
- D . Active X
- E . Flash
After using Security Director to add a new firewall policy rule on an SRX Series device, you notice that the hit count on the policy is not increasing. Upon further investigation, you find that the devices listed in the new rule are able to communicate as expected. Your firewall policy consists of hundreds of rules.
Using only Security Director, how do you find the rule that is allowing the communication to occur in this scenario?
- A . Generate a Top Firewall Rules report.
- B . Generate a Policy Analysis report.
- C . Generate a Top Source IPs report.
- D . Generate a Top Firewall Events report.
Your network includes SRX Series devices at the headquarters location. The SRX Series devices at this location are part of a high availability chassis cluster and are configured for IPS. There has been a node failover.
In this scenario, which statement is true?
- A . Existing sessions continue to be processed by IPS because of table synchronization.
- B . Existing sessions are no longer processed by IPS and become firewall sessions.
- C . Existing session continue to be processed by IPS as long as GRES is configured.
- D . Existing sessions are dropped and must be reestablished so IPS processing can occur.
You are scanning files that are being transferred from the Internet to hosts on your internal network with Sky ATP. However, you notice that files that are 1 GB in size are not being scanned by Sky ATP.
In this scenario, which two statements are true? (Choose two.)
- A . The Sky ATP failback option is set to permit.
- B . The Sky ATP engine or the SRX Series device is too busy.
- C . The 1 GB file size is larger than the scan size limit for Sky ATP.
- D . The Sky ATP policy on the SRX Series device is misconfigured.
Click the Exhibit button.
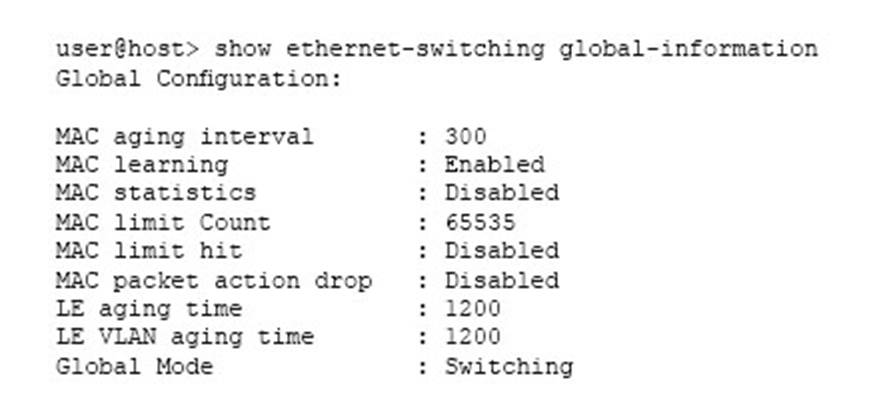
Referring to the exhibit, which two statements are true? (Choose two.)
- A . You can secure inter-VLAN traffic with a security policy on this device.
- B . You can secure intra-VLAN traffic with a security policy on this device.
- C . The device can pass Layer 2 and Layer 3 traffic at the same time.
- D . The device cannot pass Layer 2 and Layer 3 traffic at the same time.
Click the Exhibit button.
You are trying to implement secure wire on your SRX Series device. However, you are receiving the commit error shown in the exhibit.
What must you do to solve the problem?
- A . Add the correct logical units to the interfaces in the secure wire.
- B . Put the ge-0/0/4 and ge-0/0/5 interfaces in separate secure wires.
- C . Change the Ethernet switching mode from access to trunk for the ge-0/0/4 and ge-0/0/5 interfaces.
- D . Add the ge-0/0/4 and ge-0/0/5 interfaces to the SV VLAN.
You want to review AppTrack statistics to determine the characteristics of the traffic being monitored.
Which operational mode command would accomplish this task on an SRX Series device?
- A . show services application-identification statistics applications
- B . show services application-identification application detail
- C . show security application-tracking counters
- D . show services security-intelligence statistics
Which AppSecure feature identifies applications that are present in traffic?
- A . AppID
- B . AppTrack
- C . AppFW
- D . AppQoS
What is the correct application mapping sequence when a user goes to Facebook for the first time through an SRX Series device?
- A . first packet > process packet > check application system cache > classify application > process packet > match and identify application
- B . first packet > check application system cache > process packet > classify application > match and identify application
- C . first packet > check application system cache > classify application > process packet > match and identify application
- D . first packet > process packet > check application system cache > classify application > match and identify application
You have been notified by your colocation provider that your infrastructure racks will no longer be adjacent to each other.
In this scenario, which technology would you use to secure all Layer 2 and Layer 3 traffic between racks?
- A . IPsec
- B . GRE
- C . 802.1BR
- D . MACsec
You need to add all of the sites in the domain example.com to urllist2. You decide to use wildcards to account for any changes made to the domain in the future.
In this scenario, which two commands would you use to meet this requirement? (Choose two.)
- A . set custom-objects url-pattern urllist2 value http://*.example.com
- B . set custom-objects url-pattern urllist2 value http://*example.com
- C . set custom-objects url-pattern urllist2 value http://*.example.???
- D . set custom-objects url-pattern urllist2 value http://*.example.*
What is a function of UTM?
- A . AppFW
- B . IPsec
- C . content filtering
- D . bridge mode
You are configuring transparent mode on an SRX Series device. You must permit IP-based traffic only, and BPDUs must be restarted to the VLANs from which they originate.
Which configuration accomplishes these objectives?
- A . bridge {block-non-ip-all;bpdu-vlan-flooding;}
- B . bridge {block-non-ip-all;bypass-non-ip-unicast;no-packet-flooding;}
- C . bridge {bypass-non-ip-unicast;bpdu-vlan-flooding;}
- D . bridge {block-non-ip-all;bypass-non-ip-unicast;bpdu-vlan-flooding;}
You have configured a log collector VM and Security Director. System logging is enabled on a branch SRX Series device, but security logs do not appear in the monitor charts.
How would you solve this problem?
- A . Configure a security policy to forward logs to the collector.
- B . Configure application identification on the SRX Series device.
- C . Configure security logging on the SRX Series device.
- D . Configure J-Flow on the SRX Series device.
Click the Exhibit button.
Referring to the configuration shown in the exhibit, which statement explains why traffic matching the IDP signature DNS:OVERFLOW:TOO-LONG-TCP-MSG is not being stopped by the SRX Series device?
- A . The security policy dmz-pol1 has an action of permit.
- B . The IDP policy idp-pol1 is not configured as active.
- C . The IDP rule r2 has an ip-action value of notify.
- D . The IDP rule r1 has an action of ignore-connection.
Click the Exhibit button.
Which statement explains the current state value of the command output shown in the exhibit?
- A . A valid response was received from a domain PC probe, and the user is a valid domain user programmed in the PFE.
- B . An invalid response was received from a domain PC probe, and the user is an invalid domain user.
- C . A probe event generated an entry in the authentication table, but no probe response has been received from the domain PC.
- D . The user-to-address mapping was successfully read from the domain controller event logs, and an entry was added to the authentication table witch currently resides on the Routing Engine.
What are three types of content that are filtered by the Junos UTM feature set? (Choose three.)
- A . IMAP
- B . HTTP
- C . SIP
- D . SSL
- E . FTP
You are using IDP on your SRX Series device and are asked to ensure that the SRX Series device has the latest IDP database, as well as the latest application signature database.
In this scenario, which statement is true?
- A . The application signature database cannot be updated on a device with the IDP database installed.
- B . You must download each database separately.
- C . The IDP database includes the latest application signature database.
- D . You must download the application signature database before installing the IDP database.
Using the Policy Controller API, which configuration would post Sky ATP with PE mode to the Policy Enforcer controller configuration?
- A . “configs”: {“sdsn”: false“cloudonly”: true}
- B . “configs”: {“sdsn”: false“cloud”: false}
- C . “configs”: {“sdsn”: true“cloudonly”: false}
- D . “configs”: {“sdsn”: false“cloud”: true}
You are creating an IPS policy with multiple rules. You want traffic that matches rule 5 to silently be dropped, along with any future packets that match the appropriate attributes of the incoming traffic.
In this scenario, which ip-action parameter should you use?
- A . ip-block
- B . ip-close
- C . log-create
- D . timeout
Click the Exhibit button.
Referring to the exhibit, you have expanded the disk storage size in ESXi for your log collector from 500 GB to 600 GB. However, your log collector’s disk size has not changed.
Given the scenario, which two statements are true? (Choose two.)
- A . You must run a script from the console to expand the disk size.
- B . The ESXi storage parameter is not associated with the Elasticsearch disk size parameter.
- C . You must reboot the log collector for storage settings to be updated
- D . You must re-run the log collector setup script to update the storage settings.
Click the Exhibit button.
Your organization requests that you direct Facebook traffic out a different link to ensure that the bandwidth for critical applications is protected.
Referring to the exhibit, which forwarding instance will be used on your SRX Series device?
- A . R3
- B . R1
- C . R2
- D . inet.0
Click the Exhibit button.
You have recently committed the IPS policy shown in the exhibit. When evaluating the expected behavior, you notice that you have a session that matches all of the rules in your IPS policy.
In this scenario, which action would be taken?
- A . ignore-connection
- B . drop packet
- C . no-action
- D . close-client-and-server
What is the required when deploying a log collector in Junos Space?
- A . root user access to the log collector
- B . a shared log file directory on the log collector
- C . the IP address of interface eth1 on the log collector
- D . a distributed deployment of the log collector nodes
Click the Exhibit button.
The UTM policy shown in the exhibit has been applied to a security policy on a branch SRX Series device.
In this scenario, which statement is true?
- A . HTTP downloads of ZIP files will be blocked.
- B . FTP downloads of ZIP files will be blocked.
- C . E-mail downloads of ZIP files will be blocked.
- D . ZIP files can be renamed with a new extension to pass through the filter.