Which statement describes the AppTrack module in AppSecure?
- A . The AppTrack module provides enforcement with the ability to block traffic, based on specific applications.
- B . The AppTrack module provides control by the routing of traffic, based on the application.
- C . The AppTrack module identifies the applications that are present in network traffic.
- D . The AppTrack module provides visibility and volumetric reporting of application usage on the network.
D
Explanation:
https://www.juniper.net/documentation/en_US/junos/topics/topic-map/security-application-tracking.html
Click the Exhibit button.
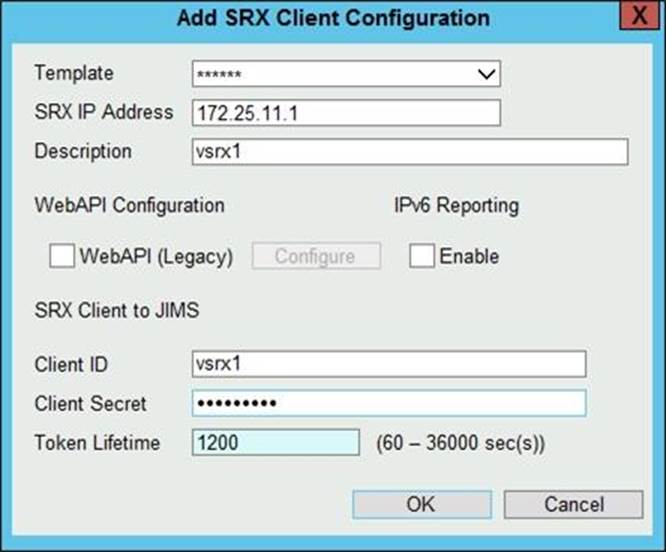
Referring to the exhibit, which two values in the JIMS SRX client configuration must match the values configured on the SRX client? (Choose two.)
- A . IPv6 Reporting
- B . Client ID
- C . Client Secret
- D . Token Lifetime
B,C
Explanation:
Reference: https://www.juniper.net/documentation/en_US/jims/topics/task/configuration/jims-srx-configuring.html
Click the Exhibit button.
Referring to the exhibit, which statement is true?
- A . IDP blocks root users.
- B . IDP closes the connection on matched sessions.
- C . IDP ignores the connection on matched sessions.
- D . IDP blocks all users.
What are two valid JIMS event log sources? (Choose two.)
- A . Microsoft Windows Server 2012 audit logs
- B . Microsoft Active Directory server event logs
- C . Microsoft Exchange Server event logs
- D . Microsoft Active Directory audit logs
Which three statements are true about the difference between cSRX-based virtual security deployments and vSRX-based virtual security deployments? (Choose three.)
- A . vSRX provides Layer 2 to Layer 7 secure services and cSRX provides Layer 4 to Layer 7 secure services.
- B . cSRX requires less storage and memory space for a given deployment than vSRX-based solutions.
- C . cSRX-based solutions are more scalable than vSRX-based solutions.
- D . vSRX and cSRX both provide Layer 2 to Layer 7 secure services.
- E . vSRX provides faster deployment time and faster reboots compared to cSRX.
A,B,C
Explanation:
Reference: https://www.juniper.net/documentation/en_US/day-one-books/topics/concept/juniper-vsrx-versus-csrx.html
Click the Exhibit button.
You have implemented SSL proxy client protection. After implementing this feature, your users are complaining about the warning message shown in the exhibit.
Which action must you perform to eliminate the warning message?
- A . Configure the SRX Series device as a trusted site in the client Web browsers.
- B . Regenerate the SRX self-signed CA certificate and include the correct organization name.
- C . Import the SRX self-signed CA certificate into the client Web browsers.
- D . Import the SRX self-signed CA certificate into the SRX certificate public store.
Which two statements are correct about server-protection SSP proxy? (Choose two.)
- A . The server-protection SSL proxy intercepts the server certificate.
- B . The server-protection SSL proxy is also known as SSL reverse proxy.
- C . The server-protection SSL proxy forwards the server certificate after modification.
- D . The server-protection SSL proxy acts as the server from the client’s perspective.
B,D
Explanation:
https://www.juniper.net/documentation/en_US/junos/topics/topic-map/security-ssl-proxy.html
Which two statements describe application-layer gateways (ALGs)? (Choose two.)
- A . ALGs are designed for specific protocols that require multiple sessions.
- B . ALGs are used with protocols that use multiple ports.
- C . ALGs can only be configured using Security Director.
- D . ALGs are designed for specific protocols that use a single TCP session.
When referencing a SSL proxy profile in a security policy, which two statements are correct? (Choose two.)
- A . A security policy can reference both a client-protection SSL proxy profile and a server-protection proxy profile.
- B . If you apply an SSL proxy profile to a security policy and forget to apply any Layer7 services to the security policy, any encrypted traffic that matches the security policy is not decrypted.
- C . A security policy can only reference a client-protection SSL proxy profile or a server-protection SSL proxy profile.
- D . If you apply an SSL proxy profile to a security policy and forget to apply any Layer7 services to the security policy, any encrypted traffic that matches the security policy is decrypted.
B,C
Explanation:
https://www.juniper.net/documentation/en_US/junos/topics/topic-map/security-ssl-proxy.html
You want to support reth LAG interfaces on a chassis cluster.
What must be enabled on the interconnecting switch to accomplish this task?
- A . RSTP
- B . 802.3ad
- C . LLDP
- D . swfab
B
Explanation:
Reference: https://www.juniper.net/documentation/en_US/junos/topics/topic-map/security-chassis-cluster-redundant-ethernet-lag-interfaces.html
Click the Exhibit button.
Referring to the exhibit, which two devices are considered to be part of the secure fabric site with Policy Enforcer? (Choose two.)
- A . Server-2
- B . SRX-1
- C . Server-1
- D . QFX-1
What is the maximum number of supported interfaces on a vSRX hosted in a VMware environment?
- A . 4
- B . 10
- C . 3
- D . 12
Click the Exhibit button.
You examine the log file shown in the exhibit after running the set security idp active-policy
command.
Which two statements are true in this scenario? (Choose two.)
- A . The IDP policy compiled successfully.
- B . The IDP policy loaded successfully.
- C . The IDP hit cache is set to 16384.
- D . The entire configuration was committed.
A,B
Explanation:
Reference: https://www.juniper.net/documentation/en_US/junos/topics/topic-map/security-idp-policies-overview.html
What is the default timeout period for a TCP session in the session table of a Junos security device?
- A . 1 minute
- B . 60 minutes
- C . 15 minutes
- D . 30 minutes
Click the Exhibit button.
The output shown in the exhibit is displayed in which format?
- A . syslog
- B . sd-syslog
- C . binary
- D . WELF
Which two functions are performed by Juniper Identity Management Service (JIMS)? (Choose two.)
- A . JIMS synchronizes Active Directory authentication information between a primary and secondary JIMS server.
- B . JIMS forwards Active Directory authentication information to SRX Series client devices.
- C . JIMS collects and maintains a database of authentication information from Active Directory domains.
- D . JIMS replicates Active Directory authentication information to non-trusted Active Directory domain controllers.
A,C
Explanation:
https://www.juniper.net/documentation/en_US/junos/topics/reference/configuration-statement/services-user-identification-identity-management-connection-primary.html
You are deploying the Junos application firewall feature in your network.
In this scenario, which two elements are mapped to applications in the application system cache? (Choose two.)
- A . destination port
- B . source port
- C . destination IP address
- D . source IP address
You must fine tune an IPS security policy to eliminate false positives. You want to create exemptions to the normal traffic examination for specific traffic.
Which two parameters are required to accomplish this task? (Choose two.)
- A . source IP address
- B . destination IP address
- C . destination port
- D . source port
Click the Exhibit button.
Which two statements are true about the configuration shown in the exhibit? (Choose two.)
- A . The session is removed from the session table after 10 seconds of inactivity.
- B . The session is removed from the session table after 10 milliseconds of inactivity.
- C . Aggressive aging is triggered if the session table reaches 95% capacity.
- D . Aggressive aging is triggered if the session table reaches 80% capacity.
Click the Exhibit button.
You are configuring an SRX chassis cluster with the node-specific hostname and management address. Referring to the exhibit, which configuration completes this requirement?
A)
B)
C)
D)
- A . Option A
- B . Option B
- C . Option C
- D . Option D
C
Explanation:
https://kb.juniper.net/InfoCenter/index?page=content&id=KB31080
Which two statements describe SSL proxy on SRX Series devices? (Choose two.)
- A . SSL proxy supports TLS version 1.2.
- B . Client-protection is also known as reverse proxy.
- C . SSL proxy is supported when enabled within logical systems.
- D . SSL proxy relies on Active Directory to provide secure communication.
A,C
Explanation:
Reference: https://www.juniper.net/documentation/en_US/junos/topics/topic-map/security-user-auth-ssl-tls.html
How many nodes are configurable in a chassis cluster using SRX Series devices?
- A . 2
- B . 4
- C . 6
- D . 8
Which statement is true about high availability (HA) chassis clusters for the SRX Series device?
- A . Cluster nodes require an upgrade to HA compliant Routing Engines.
- B . Cluster nodes must be connected through a Layer 2 switch.
- C . There can be active/passive or active/active clusters.
- D . HA clusters must use NAT to prevent overlapping subnets between the nodes.
Which default protocol and port are used for JIMS to SRX client communication?
- A . WMI over TCP; port 389
- B . ADSI over TCP; port 389
- C . HTTPS over TCP: port 443
- D . RPC over TCP, port 135
C
Explanation:
Reference: https://www.juniper.net/documentation/en_US/jims/topics/task/configuration/jims-certificate-configuring.html#:~:text=By%20default%2C%20the%20HTTPS%20port%20is%20443.&text=The%20JIMS%20server%20communicates%20with,Firewall%20to%20allow%20this%20communication
You must ensure that all encrypted traffic passing through your SRX device uses strong protocols and ciphers.
Which feature should you implement to satisfy this requirement?
- A . SSL proxy
- B . AppSecure
- C . JIMS
- D . JATP
You are configuring a client-protection SSL proxy profile.
Which statement is correct in this scenario?
- A . A server certificate is not used but a root certificate authority is used.
- B . A server certificate and root certificate authority are not used.
- C . A server certificate is used but a root certificate authority is not used.
- D . A server certificate and a root certificate authority are both used.
Which two statements describe JSA? (Choose two.)
- A . Security Director must be used to view third-party events rom JSA flow collectors.
- B . JSA supports events and flows from Junos devices, including third-party devices.
- C . JSA events must be manually imported into Security Directory using an SSH connection.
- D . JSA can be used as a log node with Security Director or as a standalone solution.
Which statement about the control link in a chassis cluster is correct?
- A . A cluster can have redundant control links.
- B . Recovering from a control link failure requires a reboot.
- C . The control link heartbeats contain the configuration file of the nodes.
- D . The control messages sent over the link are encrypted by default.
A
Explanation:
Reference: https://www.juniper.net/documentation/en_US/junos/topics/topic-map/security-chassis-cluster-dual-control-links.html
Which solution should you use if you want to detect known attacks using signature-based methods?
- A . SSL proxy
- B . JIMS
- C . IPS
- D . ALGs
Which two solutions provide a sandboxing feature for finding zero-day malware threats? (Choose two.)
- A . Sky ATP
- B . UTM
- C . JATP
- D . IPS