Exhibit.
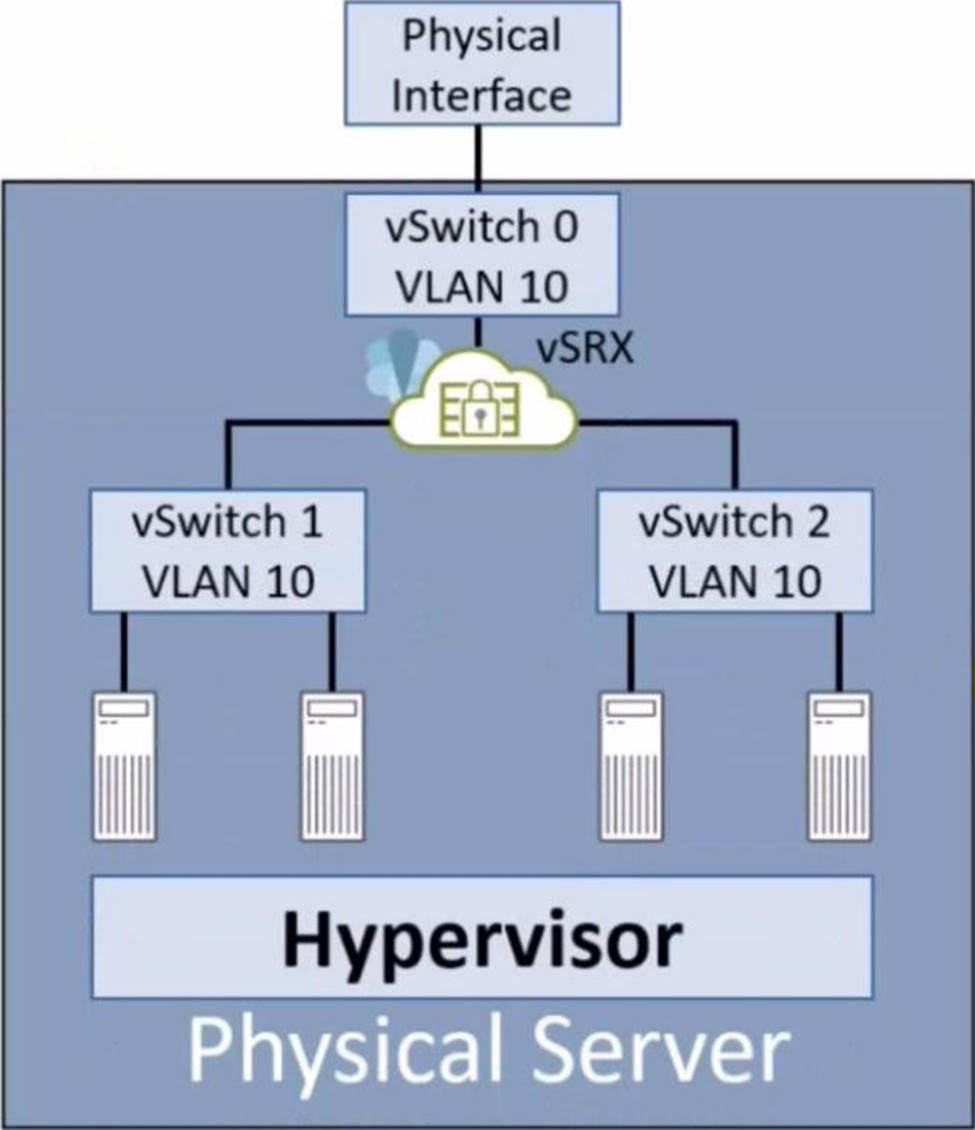
Referring to the exhibit, which two statements are true? (Choose two.)
- A . The vSRX is performing microsegmentation
- B . The vSRX is working in transparent mode.
- C . The vSRX is working in routed mode
- D . The vSRX is not performing microsegmentation
Which two Layer 2 Data Center Interconnect redundancy options support active/active forwarding? (Choose two.)
- A . VPLSLAG
- B . point-to-point LAG
- C . EVPN multihoming
- D . VPLS multihoming
Your company wants to expand operations and build small data centers in locations where it is difficult to maintain physical routing equipment. You must recommend a Juniper product that minimizes this issue.
Which product would you recommend in this situation?
- A . MX104
- B . vMX
- C . vRR
- D . Virtual Chassis
Which three statements about Contrail Networking are true? (Choose three.)
- A . It is used to service chain network functions.
- B . It is used to program physical network functions.
- C . It is used to virtualize and program networks.
- D . It is used to virtualize and program compute.
- E . It is used to create distributed cloud storage.
Exhibit.
Which two statements about the redundancy design shown in the exhibit are true? (Choose two)
- A . Inter-server traffic must use an alternate IP address
- B . Multicast IP addressing is in use
- C . User traffic must be policy-routed to the active data center
- D . Anycast IP addressing is in use
What are two elements of data center security? (Choose two.)
- A . DDoS protection
- B . segmentation with VLANs in hypervisors
- C . ATP Cloud advanced anti-malware
- D . JIMS for user identify and management
You are asked to create an underlay network that will scale from a small system to a large system and can be integrated into a Contrail solution In this scenario, which protocol satisfies these requirements’5
- A . EVPN
- B . VXLAN
- C . BGP
- D . MPLS
Which three statements are correct regarding a Clos-style IP fabric network? (Choose three)
- A . Leaf nodes can be interconnected
- B . Spine nodes can be interconnected
- C . Leaf nodes should be connected to spine nodes
- D . Spine nodes should not be interconnected
- E . Leaf nodes should not be interconnected
You are designing an EVPN/VXLAN network and want to ensure that latency between VMs on the same host is as low as possible for both Layer 2 and Layer 3 traffic.
Which two design choices will accomplish this task? (Choose two.)
- A . Configure leaf nodes as VXLAN Layer 2 gateways
- B . Configure leaf nodes as VXLAN Layer 3 gateways
- C . Configure spine nodes as VXLAN Layer 3 gateways
- D . Configure spine nodes as VXLAN Layer 2 gateways
You are designing an IP fabric underlay using IBGP with the spines serving as route reflectors.
In this scenario, which BGP capability must be supported on the spines?
- A . add-path
- B . route-monitoring
- C . rib-sharding
- D . route-refresh-priority
Which data center architecture is open, flexible, and uses Layer 3 only?
- A . STP
- B . IP fabric
- C . virtual chassis
- D . MC-LAG
You are designing a new Data Center Interconnect (DCI) that will be MPLS-based where the PE routers need to learn local and remote MAC addresses.
In this scenario, which two CXI deployment methodologies satisfy this requirement? (Choose two)
- A . VPLS
- B . EVPN
- C . LDP Layer 2 circuits
- D . BGP Layer 2 VPNs
Which two scripting languages are supported for creating on-box scripts? (Choose two.)
- A . Chef
- B . Python
- C . SLAX
- D . Ansible
B,C
Reference: https://www.juniper.net/documentation/us/en/software/junos/automation-scripting/automation-scripting.pdf
Exhibit.
For a fully configured and functional IP fabric underlay as shown in the exhibit how many external BGP neighbors are expected to be in established state for Leaf 1?
- A . 2
- B . 5
- C . 4
- D . 3
A customer has concerns about various groups having the ability to easily access their corporate network infrastructure They want to implement tighter controls for network infrastructure system access
Which three actions will accomplish this task? (Choose three)
- A . Use a secure access VPN
- B . Open console port access
- C . Disable root access
- D . Use RADIUS accounting.
- E . Provide local passwords
Which two statements describe SDN? (Choose two.)
- A . SDN can alleviate the need for manually configuring each network device.
- B . SDN moves forwarding functions to a centralized management platform.
- C . SDN combines the control plane and the forwarding plane into a single fabric.
- D . SDN moves compute intensive functions to a centralized controller.
Your company is deploying a private cloud based on OpenStack and has selected Contrail Networking as their SDN controller. The data center supporting this private cloud will use an IP fabric architecture consisting of QFX Series switches and MX Series routers.
Which two statements are true in this scenario? (Choose two)
- A . SDN Gateway devices may contain per-tenant MAC and IP addresses
- B . Each vRouter maintains separate forwarding tables for various virtual networks
- C . All vRouters maintain identical forwarding tables for all virtual networks.
- D . Spine and leaf devices may contain per-tenant MAC and IP addresses
What are two considerations when designing an IP fabric? (Choose two)
- A . Uplinks from servers to the leaf nodes should be 40GbE links
- B . All spine nodes should be the same type of device
- C . Leaf nodes and spine nodes should be the same type of device
- D . Every leaf node should have an uplink to every spine node
You have a highly latency-sensitive application that is mission critical to your company’s operation. In this scenario, what will enable you to identify issues within three second accuracy?
- A . RMON1
- B . RMON2
- C . JTI
- D . LDAP
Which two Junos components does cRPD contain? (Choose two.)
- A . Kubernetes
- B . RIB
- C . Kernel
- D . MGD
You are asked to design a solution for your data center EVPN/VXLAN fabric that will allow connectivity for all of your service platforms, such as firewalls and load balancers into a dedicated pair of border leaf devices
Which three Juniper Networks platforms would support this requirement? (Choose three)
- A . SRX Series
- B . QFX10000 Series
- C . EX4300-MP Series
- D . 0MX Series
- E . QFX5120 Series
Which two features add NGFW capabilities to a traditional security device” (Choose two)
- A . IPS
- B . UTM
- C . IP filters
- D . NAT
You are asked to design a DCI that offers policy control, active/active multihoming with load balancing, and minimizes flooding of BUM traffic.
Which DCI implementation satisfies these requirements?
- A . EVPN
- B . circuit cross-connect
- C . BGP Layer 2 VPN
- D . VPLSLAG
You must deploy a solution within your data center that will provide capacity planning for your virtual machine environment.
In this scenario, which Juniper Networks solution would accomplish this task?
- A . Contrail Cloud
- B . Juniper Secure Analytics
- C . Contrail Insights
- D . Junos Space
You are asked to design an IP fabric that uses the same routing protocol in both the underlay and overlay networks.
Which routing protocol will satisfy this requirement?
- A . IS-IS
- B . MPLS
- C . OSPF
- D . BGP
You are designing a QoS scheme for your data center. You must ensure lossless Ethernet.
What are three protocols that would be used in this scenario? (Choose three.)
- A . TRILL
- B . SPB
- C . ETS
- D . DCBx
- E . PFC
When using BGP Layer 2 VPN for a Data Center Interconnect, which statement about MAC learning is correct?
- A . MAC learning is not used.
- B . Management plane MAC learning is used.
- C . Data plane MAC learning is used.
- D . Control plane MAC learning is used
You are implementing a new data center and need to plan to connect it to your existing data center. You have the requirement for active/active forwarding to enable load balancing and reduce failure times
Which two technologies should be evaluated for this design? (Choose two.)
- A . point-to-point links
- B . Layer 2 VPN
- C . VPLS
- D . CVPN
You are asked to design a new data center connection where connections between switches will be encrypted for Layer 2 traffic In this scenario, which solution will provide the required encryption^
- A . IPsec
- B . TLS
- C . SSL
- D . MACsec
Exhibit.
Given the information shown below.
2 spine nodes with (4) 40GbE interfaces each
4 leaf nodes.
✑ Each leaf node has half-utilized (24) 10GbE interfaces,
✑ Each leaf node has (1) 40GbE interface to each of the 2 spine nodes What is the oversubscription ratio for the IP fabric shown in the exhibit?
- A . 2:1
- B . 1:1
- C . 4:1
- D . 3:1
You are designing a large IP fabric and must determine if you should use IBGP or EBGP to signal your underlay.
Which statement is correct in this scenario?
- A . EBGP will require more BGP neighbors per device.
- B . IBGP will require a full mesh on all devices
- C . EBGP will require that an IGP is also configured
- D . IBGP will allow your network to scale to larger device numbers.
You are inspecting a small data center your company just purchased You notice several blank panels and cable management system components in a storage room that are not installed on the equipment racks
In this scenario, which two statements would you include in your inspection report? (Choose two.)
- A . The cable management system function is cosmetic only and is not necessary.
- B . The blank panels were removed to improve cooling air flow through the racks.
- C . The cable management system should be installed as soon as possible
- D . The blank panels should be installed as soon as possible
You must implement Layer 4 security services between VMs that are hosted on the same server You require a low footprint with Docker support.
In this scenario, which Juniper Networks product would you deploy?
- A . QFX
- B . vSRX
- C . cSRX
- D . cRPD
Which statement is true about traffic prioritization?
- A . QoS is experienced hop-by-hop
- B . FCoE does not require DCB.
- C . PFC and Ethernet PAUSE produce the same result
- D . CoS is the treatment of traffic end-to-end
You are asked to design security policies based on team membership.
Which access control methodology should you use in this scenario?
- A . non-discretionary access control
- B . role-based access control
- C . mandatory access control
- D . discretionary access control