When discussing network reliability, what does the term “five nines” mean?
- A . The network is up 99.999% of the time.
- B . The network is up .99999% of the time.
- C . The network is up 9.9999% of the time.
- D . The network is up .09999% of the time.
Which component triggers the quarantine of an infected endpoint?
- A . ALG
- B . firewall
- C . Policy Enforcer
- D . switch
You are in the process of developing a business continuity plan for your network design. You must analyze data about weather patterns, maintenance history pertaining to leased buildings, and the frequency of power failures.
For which purpose would you collect this information?
- A . risk assessment
- B . redundancy
- C . high availability
- D . disaster recovery
You are asked to provide a design proposal for a service provider network. The design must ensure that
customers are able to send Layer 2 traffic between sites.
In this scenario, which VPN technology would be used to accomplish this task?
- A . IPsec VPN
- B . Layer 3 VPN
- C . GRE
- D . EVPN
You are asked to evaluate a WAN design for a corporation with a focus on cost, security, and the ability to have direct adjacencies between your remote sites.
Which two solutions would meet the requirements? (Choose two.)
- A . MPLS Layer 3 VPN
- B . GRE tunnels over the Internet
- C . VPLS Layer 2 VPN
- D . IPsec tunnels over the Internet
You are asked to provide a design proposal for an enterprise customer that currently has a three-tier switching infrastructure. The customer wants your design to collapse their Layer 2 infrastructure into two distinct layers. In this scenario, what are two benefits of moving to the new infrastructure? (Choose two.)
- A . The total number of devices is increased.
- B . The overall network performance is increased.
- C . The number of connections between devices is decreased.
- D . The number of protocols used is decreased.
You are designing a data center network that will require the rapid deployment and removal of security features between virtual machines based on triggered traffic flows. The data center will require the ability to scale up and down rapidly according to traffic load, and then release resources when security services are not needed. In this scenario, which type of security design would fulfill this requirement?
- A . a centralized security appliance
- B . a container-based security deployment
- C . a physical security device connected to each host
- D . an all-in-one virtual security device in each host
Which tool in a Juniper Networks SDSN solution is responsible for telling Juniper and third-party network switches to block a threat in real time?
- A . Policy Enforcer
- B . Sky ATP
- C . Juniper Secure Analytics
- D . SRX Series device
Click the Exhibit button.
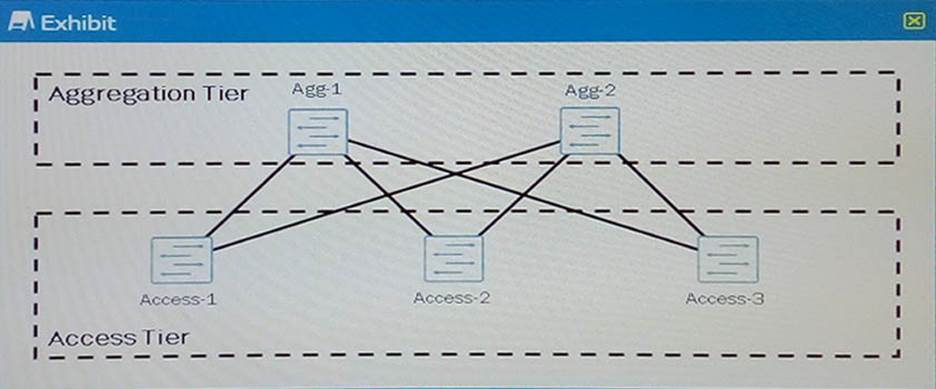
Referring to the exhibit, you are designing a Layer 2 data center and you want to make sure that all the links between the access tier and the aggregation tier are used.
What should you do to accomplish this task?
- A . Use VRRP on Agg-1 and Agg-2.
- B . Place Agg-1 and Agg-2 in a Virtual Chassis.
- C . Use RSTP on all devices.
- D . Use BGP load balancing on all devices.
Which Juniper automation tool enables administrators to write custom Python scripts that use the Junos XML API?
- A . REST Explorer
- B . JSNAPy
- C . JET
- D . PyEZ
What are two phases in Juniper’s lifecycle approach when designing a network? (Choose two.)
- A . plan
- B . build
- C . buy
- D . oversee
You are designing a WAN implementation to securely connect two remote sites to the corporate office. A public Internet connection will be used for the connections.
Which statement is true in this situation?
- A . The connection should be secured using IPsec.
- B . The WAN edge devices must support MPLS.
- C . The connections support Layer 2 traffic bridging.
- D . The service provider can isolate traffic in a private MPLS instance.
What is the first step of business continuity planning?
- A . know your network
- B . test the plan
- C . assess the risk
- D . formulate the plan
What are two features used to enable high availability? (Choose two.)
- A . VRRP
- B . chassis clustering
- C . full-duplex mode
- D . SNMP
You are evaluating an existing network to determine requirements for a network upgrade.
In this scenario, which statement is true?
- A . A network baseline identifies devices that do not have redundant components.
- B . A network baseline identifies traffic growth patterns across network devices.
- C . A network baseline identifies how many users are connected to the network.
- D . A network baseline identifies the type and level of traffic load on the network.
You are performing a risk assessment for a network design.
Which statement is true in this scenario?
- A . Some risks can be safely ignored.
- B . The likelihood of a risk occurring should not be considered.
- C . A network must be designed for an uptime of five nines.
- D . All identified risks must have a mitigation plan in place.
What are three examples of physical security? (Choose three.)
- A . security cameras
- B . access door keypads
- C . a mantrap
- D . man in the middle
- E . intrusion detection and prevention
Which two statements are true regarding a Virtual Chassis? (Choose two.)
- A . A Virtual Chassis must be configured on the same series but not the same model.
- B . A Virtual Chassis supports up to 10 participating devices.
- C . A Virtual Chassis supports only two participating devices.
- D . A Virtual Chassis can be configured on mixed series and models.
Which two statements are true regarding greenfield projects? (Choose two.)
- A . The amount of floor space and cooling are not defined as part of a greenfield project.
- B . In greenfield projects, the existing floor space and cooling may need to be considered.
- C . Greenfield projects are typically new networks with few or no restraints to consider.
- D . Greenfield projects typically consist of existing network components with extensive integration required.
Which two pieces of information should be included in an RFP response? (Choose two.)
- A . a list of contributing material including technical publications, training guides, and courseware used to build the proposed design
- B . design details including information about the devices, protocols, and technologies included in the
proposed design - C . configuration details including proposed devices, protocols, and technologies included in the proposed
design - D . a network topology including a high-level logical design as well as low-level physical design of the
proposed network
Which two features would cause latency in a WAN connection? (Choose two.)
- A . IPS
- B . syslog
- C . telemetry
- D . UTM antivirus
What are three environmental characteristics that affect the campus network design? (Choose three.)
- A . transmission media characteristics
- B . distribution of users
- C . locations of wiring closets
- D . PC operating system
- E . remote site connectivity
Click the Exhibit button.
Which device plays the role of authenticator in an 802.1X design as shown in the exhibit?
- A . Device C
- B . Device A
- C . Device D
- D . Device B
Why would you recommend Junos Space Security Director in a network design?
- A . It simplifies Ethernet switch deployments and provides rapid operation of campus and data center
networks. - B . It provides the power to quickly design, provision, and deliver MPLS and other Ethernet services.
- C . It helps administrators to more quickly and intuitively manage all phases of a security policy life cycle.
- D . It provides detection, isolation, and resolution of network faults and incidents.
What are three types of automation scripts used on a Junos device? (Choose three.)
- A . op scripts
- B . commit scripts
- C . boot scripts
- D . event scripts
- E . control scripts
You are required to stop zero-day threats while designing a secure network. Files are not allowed to leave the local network.
Which Juniper Networks product will accomplish this task?
- A . UTM
- B . Sky ATP
- C . JATP
- D . SDSN