You enable unicast reverse path forwarding on the ge-0/0/1.0 interface A packet is received on the ge-0/0/1.0 interface with a source address of 10.10.10.10. A route lookup determines that the next hop for the 10.10.10.10 address is the ge-0/0/1.0 interface. In this scenario which action is performed?
- A . The packet is logged
- B . The packet is forwarded
- C . The packet is rejected
- D . The packet is discarded
B
Explanation:
https://www.juniper.net/documentation/us/en/software/junos/security-services/topics/topic-map/interfaces-configuring-unicast-rpf.html
Referring to the exhibit.
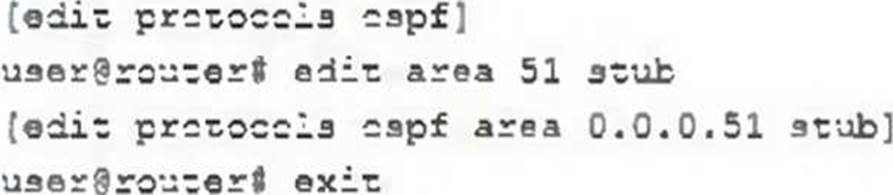
what happens when you issue the exit command at the [edit protocols ospf area 0.0.0.51 stub] hierarchy level?
- A . You move one level up to the [edit protocols ospf area 0.0.0.51] hierarchy level.
- B . You exit the configuration mode.
- C . You move to the [edit] hierarchy level.
- D . You move to the most recent higher level of the [edit protocols ospf] hierarchy.
Exhibit:
[edit routing-options]
user@router# show
static {
route 0.0.0.0/0 {
next-hop 10.1.1.1;
qualified-next-hop 10.1.1.254 {
preference 4;
}
}
}
Assuming both paths shown in the exhibit are available, which statement is correct?
- A . Traffic matching the default route will use 172.16.1.1 as the next hop
- B . Traffic matching the default route will use 172.16.1.254 as the next hop
- C . Traffic matching the default route will be load-balanced per flow across both next hops
- D . Traffic matching the default route will be load-balanced per packet across both next hops.
Which attribute must be defined when configunng a non-root user in Junos OS?
- A . class
- B . uid
- C . authentication
- D . full-name
A
Explanation:
UID is optional (it is automatically set) whereas class is required: https://www.juniper.net/documentation/us/en/software/junos/user-access/topics/topic-map/junos-os-user-accounts.html
Your Junos OS routers use a static route to provide connectivity to the management network. You do not want this static route to be redistributed using a dynamic routing protocol.
In this scenario, which static route configuration parameter will accomplish this task?
- A . no-install
- B . no-retain
- C . no-resolve
- D . no-readvertise
Click the Exhibit button.
The user root is unable to connect to the router using SSH.
Referring to the exhibit, which configuration change will correct the problem?
- A . [edit]
user@router# set system services ssh root-login allow - B . [edit]
userr@outer# set system services ssh - C . [edit]
user@router# delete system services ssh - D . [edit]
use^@router# delete system services ssh root-login deny
A
Explanation:
https://www.juniper.net/documentation/us/en/software/junos/user-access/topics/ref/statement/ssh-edit-system.html
After logging in as root, you enter the cl i command.
What does this command do?
- A . It enables you to enter configuration mode.
- B . It enables you to enter line edit mode.
- C . It enables you to enter operational mode.
- D . It enables you to enter interface mode.
Click the Exhibit button.
Referring to the exhibit, which two statements are true? (Choose two.)
- A . The logical interface is running IPv6.
- B . The interface is operating in full-duplex mode.
- C . The address 172.25.11.255 is the broadcast address for the logical interface.
- D . The interface MAC address has been changed from the default MAC address.
Click the Exhibit button.
Click the Exhibit button.
What happens if the packet shown in the exhibit is received by a device running Junos OS?
- A . The packet is received by the RE first and then redirected to the PFE.
- B . The packet is received by the PFE first and then redirected to the RE.
- C . The packet is handled by the PFE alone.
- D . The packet is handled by the RE alone.
B
Explanation:
IP options are exception traffic
Packets addressed to the chassis, such as routing protocol updates, Telnet sessions, pings, traceroutes, and replies to traffic sourced from the RE;
• IP packets with the IP options field (options in the packet’s IP header are rarely seen, but the PFE was purposely designed not to handle IP options; packets with IP options must be sent to the RE for processing); and
• Traffic that requires the generation of Internet Control Message Protocol (ICMP) messages.
Click the Exhibit button.
Click the Exhibit button.
Referring to the exhibit, which statement is correct about traffic received on the ge-0/0/1.0 interface?
- A . All traffic will be silently dropped.
- B . All traffic will be accepted.
- C . All traffic will be dropped and a UDP message sent back to the source.
- D . All traffic will be dropped and an ICMP notification sent back to the source.
Click the Exhibit button.
You are attempting to capture traffic being sent to IP address 100.0.0.2, but are unable to see any packets.
Referring to the exhibit, what is the problem?
- A . You must use the dat 100.0.0.2 match condition instead of the src 100.0.0.2 match condition.
- B . You must add the size parameter to the command.
- C . Traffic destined for 100.0.0.2 is transit traffic.
- D . You must add the layer2-headers parameter to the command.
A
Explanation:
Questions and Answers PDF
Click the Exhibit button.
Click the Exhibit button.
What will happen when you commit the configuration shown in the exhibit?
- A . Gigabit interfaces on FPC 2 will inherit the family inet configuration.
- B . All gigabit interfaces will inherit the family inet configuration.
- C . VLAN 0 will be applied to gigabit interfaces on FPC 2.
- D . VLAN 0 will be applied to all gigabit interfaces.
13/97
Which output displays that the peer has been selected for NTP synchronization?
- A . Option A
- B . Option B
- C . Option C
- D . Option D
Click the Exhibit button
Referring to the exhibit, you are unable to see any traffic coming on interface ge-0/0/0.
What is causing this problem?
- A . The ge-0/0/0 interface is administratively down.
- B . The ge-0/0/0 interface has flow control disabled.
- C . The ge-0/0/0 interface’s physical link is down.
- D . The ge-0/0/0 interface has the link-mode set to half-duplex.
Click the Exhibit button.
Which two statements about the output shown in the exhibit are correct? (Choose two.)
- A . The neighbors are not using the Junos OS default OSPF priority value.
- B . The IP address assigned to the router’s ge-0/0/1.0 interface is 172.25.1.9.
- C . The router has two OSPF adjacencies.
- D . The router ID of the neighbor connected to the ge-0/0/1.0 interface is 192.168.100.3.
Click the Exhibit button.
Referring to the exhibit, which two statements are correct? (Choose two.)
- A . The last 5 second CPU utilization is 99%.
- B . The last 5 second CPU utilization is 1%.
- C . The control plane memory used is 63%.
- D . The data plane memory used is 63%.
Click the Exhibit button.
Referring to the exhibit, what happens when you filter the output of a command using the no-more parameter?
- A . The output is displayed in XML format.
- B . The output is displayed with no page breaks.
- C . The number of lines in the output are displayed.
- D . The last screen of information is displayed.
B
Explanation:
Ref: | (pipe) | Junos OS | Juniper Networks
“| (pipe)
…
Description
Filter the output of an operational mode or a configuration mode command.
…
Options
…
no-more Display output all at once rather than one screen at a time.
…”
Which two routing policy actions are considered policy flow control actions in the Junos OS? (Choose two.)
- A . accept
- B . next hop
- C . next policy
- D . next term
AB
Explanation:
https://www.juniper.net/documentation/us/en/software/junos/routing-policy/topics/concept/policy-configuring-actions-in-routing-policy-terms.html
In the show I compare rollback 49 command, what is the purpose of the I?
- A . The | is a shortcut to redirect output from a command line to a file.
- B . The filters the output of the show command.
- C . The | is used to represent an "either or” statement.
- D . The | changes the command from an operational command to a configuration mode command.
B
Explanation:
ttps://www.juniper.net/documentation/us/en/software/junos/cli/topics/ref/command/pipe.html
What is the network address for a host with an IP address of 192.168.87.125/16?
- A . 192.168.128.0
- B . 192.168.0.0
- C . 192.168.96.0
- D . 192.168.87.0
B
Explanation:
The network address for a host is determined by performing a bitwise AND operation between the host’s IP address and the subnet mask. In this case, the IP address is 192.168.87.125 and the subnet mask is 255.255.0.0 (or /16), which means that the first 16 bits are used for the network portion of the address and the remaining 16 bits are used for the host portion.
To find the network address, we perform the bitwise AND operation:
What is the network address for a host with an IP address of 192.168.87.125/16?
- A . 192.168.128.0
- B . 192.168.0.0
- C . 192.168.96.0
- D . 192.168.87.0
B
Explanation:
The network address for a host is determined by performing a bitwise AND operation between the host’s IP address and the subnet mask. In this case, the IP address is 192.168.87.125 and the subnet mask is 255.255.0.0 (or /16), which means that the first 16 bits are used for the network portion of the address and the remaining 16 bits are used for the host portion.
To find the network address, we perform the bitwise AND operation:
Which command should you use to check real-time statistics of all active interfaces?
- A . user@router> monitor traffic extensive
- B . user@router> monitor interface traffic
- C . user@router> show interface detail
- D . user@router> show interface terse
B
Explanation:
https://www.juniper.net/documentation/us/en/software/junos/network-mgmt/topics/topic-map/monitoring-interfaces-and-switching-functions.html
Click the Exhibit button.
UserA is currently working on routed and has issued the commands shown in the exhibit. UserB wants to update the IP address currently configured on interface xe-1/2/1.0.
What will UserB do to complete the configuration changes without interfering with UserA’s work?
- A . UserB should use the configure private option to complete the changes while UserA continues with the changes.
- B . UserB should use the configure exclusive option to complete the changes while UserA continues with the changes.
- C . Use the edit command and run the commit confirmed option then proceed with UserB’s changes.
- D . Wait for UserA to finish then proceed with changes using the configure private option.
Which routing instance type is used for filter-based forwarding applications?
- A . layer2-control
- B . vpls
- C . forwarding
- D . vrf
C
Explanation:
The forwarding routing instance type is used for filter-based forwarding applications, such as policy-based routing and traffic engineering. This type of routing instance is used when the routing table needs to contain more detailed information than what is available in the default routing table. According to the Juniper Networks Technical Certification Program (JNTCP) documents [1], the forwarding routing instance type is used for filter-based forwarding applications.
What are two functions of the transport layer? (Choose two.)
- A . data integrity
- B . segmentation
- C . flow control
- D . packet forwarding
BC
Explanation:
The transport layer is responsible for ensuring the reliable delivery of data between applications running on different devices.
It provides two main functions:
What are two functions of the transport layer? (Choose two.)
- A . data integrity
- B . segmentation
- C . flow control
- D . packet forwarding
BC
Explanation:
The transport layer is responsible for ensuring the reliable delivery of data between applications running on different devices.
It provides two main functions:
What are two functions of the transport layer? (Choose two.)
- A . data integrity
- B . segmentation
- C . flow control
- D . packet forwarding
BC
Explanation:
The transport layer is responsible for ensuring the reliable delivery of data between applications running on different devices.
It provides two main functions:
You are troubleshooting a problem on your Junos device. You want to view the syslog messages in real-time on your terminal.
In this scenario, which command will accomplish this task?
- A . monitor log messages
- B . monitor start messages
- C . show log messages
- D . show log trace options
B
Explanation:
The "monitor start messages" command is used to display syslog messages in real-time on the terminal. This command provides a convenient way to monitor system events and troubleshoot problems on the device. The output of this command is sent to the console and updates in real-time as new syslog messages are generated.
To use this command, you simply enter "monitor start messages" at the CLI prompt and the syslog messages will be displayed on the terminal. To stop the display, you can press "Ctrl+C".
Reference: Juniper Networks JNCIA-Junos Study Guide, Section 8.4 "Monitoring System Log Messages"
You are asked to enable the configuration archival feature on your device running Junos OS.
Which two backup scenarios exist? (Choose two.)
- A . When a user performs a commit operation.
- B . When a user logs out of the device.
- C . When a specific time interval passes.
- D . When a user logs in to the device.
AC
Explanation:
Ref: Back Up Configurations to an Archive Site | Junos OS | Juniper Networks
"Back Up Configurations to an Archive Site
…
Configure the Transfer of the Active Configuration
If you want to back up your device’s current configuration to an archive site, you can configure the device to transfer its active configuration by FTP, HTTP, or secure copy (SCP) periodically or after each commit.
A router contains both a static route and an OSPF route for the 172.18.100.0/24 prefix in its routing table. The router is configured to use the factory-default Junos OS routing preference values.
In this scenario, which statement is correct?
- A . The OSPF route will be active because of a higher default preference value.
- B . The OSPF route will be active because of a lower default preference value.
- C . The static route will be active because of a lower default preference value.
- D . The static route will be active because of a higher default preference value.
Which two operating systems are used as the foundation of the Junos OS? (Choose two.)
- A . Ubuntu
- B . CentOS
- C . Linux
- D . FreeBSD
What does the commit check command do?
- A . It validates the syntax of a candidate configuration without actually committing the configuration.
- B . It commits the configuration when a validation check succeeds.
- C . It schedules the commit to a future time.
- D . It adds a comment to the messages log.
A
Explanation:
The commit check command allows you to validate the syntax of a candidate configuration without actually committing the configuration. This is useful for validating the syntax of a configuration before committing it to ensure that the configuration can be applied without any errors. According to the Juniper Networks JNCIA-Junos study guide, the commit check command validates the syntax of a candidate configuration without actually committing the configuration.
Click the Exhibit button.
Referring to the exhibit, a firewall filter is configured and applied to the ge-0/0/1 interface.
In this scenario, which statement is correct?
- A . All traffic to destination 10.10.10.0/24 is accepted.
- B . All traffic entering on interface ge-0/0/1 is discarded.
- C . All traffic entering on interface ge-0/0/1 is accepted.
- D . All traffic from source 10.10.10.0/24 is accepted.
D
Explanation:
if term has no "then" configured, matched packets are accepted by default
https://www.juniper.net/documentation/us/en/software/junos/routing-policy/topics/concept/firewall-filter-ex-series-evaluation-understanding.html
Additionaly:
if term has no "from" configured, every packet is matched to term
if packet does not match any term – default term (implicit discard) is used
You loaded the factory-default configuration on your Junos device.
Which single element must be configured before a commit command will succeed?
- A . An IPv4 address must be configured on the fxpO or emO interface.
- B . An IPv4 default route must be configured.
- C . A hostname must be configured.
- D . A root password must be configured.
D
Explanation:
Ref: Root Password | Junos OS | Juniper Networks
“Root Password
…
When the device is powered on for the first time, it is ready to be configured. Initially, you log in as the user root with no password. You must configure a plain-text password for the root-level user (whose username is root) the first time you modify and commit the configuration.
…”
Which Junos OS routing instance type is used for non-VPN-related applications such as system virtualization?
- A . vpls
- B . forwarding
- C . virtual-router
- D . vrf
Which two statements describe the functions of the Routing Engine (RE)? (Choose two.)
- A . The RE will apply filters and routing policies when forwarding the packets to their final destination.
- B . The RE will calculate the best network path to each individual subnet based on input from various routing protocols and static routes.
- C . The RE will route or switch packets or frames out of the correct interface as quickly as possible.
- D . The RE will process management traffic to help monitor and manage the network device.
When you choose to read your e-mail using an e-mail client, your e-mail client interacts with which OSI layer?
- A . presentation
- B . transport
- C . application
- D . session
C
Explanation:
According to the OSI (Open Systems Interconnection) model, the application layer is responsible for providing the user with a means to access the network services, such as e-mail, file transfer, and virtual terminal access. An e-mail client, such as Microsoft Outlook or Apple Mail, operates at the application layer and interacts with the underlying network services to retrieve and manage e-mail messages.
Reference: Juniper Networks JNCIA-Junos Study Guide, Section 2.2 "The OSI Model"
What information is provided by the help topic interface? command?
- A . It displays the administration manual for the interface command.
- B . It displays usage examples for the top-ten interface commands.
- C . It displays the available options and a brief description of usage guidelines.
- D . It displays the best options to use with the interface command regarding your current configuration.
What is a function of the PFE?
- A . to generate protocol control traffic
- B . to monitor chassis components
- C . to apply stateless firewall filters
- D . to generate forwarding tables
What are two benefits of a modular operating system? (Choose two.)
- A . A malfunction in one module causes a full system shutdown.
- B . Each module runs in its own protected memory space.
- C . It enables the independent restart of each module as necessary.
- D . It enables CPU scheduling strictly using kernel system calls.
BC
Explanation:
Ref: Junos OS Overview | Junos OS | Juniper Networks
“Junos OS Overview
…
Modular Software Architecture
Although individual architecture modules of Junos OS communicate through well-defined interfaces, each module runs in its own protected memory space, preventing one module from disrupting another. It also enables the independent restart of each module as necessary.
…”
What is the default action for packets not matching a firewall filter?
- A . The packet will be silently discarded.
- B . The packet will be accepted.
- C . The packet will be rejected.
- D . The packet will be ignored.
Which two statements describe the RE on Junos OS devices? (Choose two.)
- A . The RE is considered the control plane.
- B . The RE forwards traffic based on its local copy of the forwarding table.
- C . The RE provides hardware status messages for the PFE
- D . The RE maintains the routing tables.
A, D
Explanation:
Ref: Juniper Networks Partner Solution Development Platform: Architecture of the JUNOS System
“Architecture of the JUNOS System
…
The Routing Engine operates all routing protocols and makes all routing decisions by creating a routing table that includes the best path to each destination. The router writes these paths to a forwarding table in the Routing Engine and then copies the same data to the forwarding table on the Packet Forwarding Engine (PFE) which actually forwards the packets.
…
The Control Plane
…
The control plane runs on the Routing Engine. Its role is to manage and control the behavior of the device, including the data plane and the services plane.
…”
Which command allows multiple users to edit a configuration while conning only their unique changes?
- A . configure exclusive
- B . configure batch
- C . configure private
- D . configure dynamic
C
Explanation:
The configure private command allows multiple users to edit different parts of a configuration at the same time and commit only their changes or roll back, without interfering with each other’s changes. When the configure private command is used, you work in a private candidate configuration, which is a copy of the most recently committed configuration.
https://kb.juniper.net/InfoCenter/index?page=content&id=KB19653&actp=METADATA
Which statement is true about using custom login class permissions?
- A . If you allow and deny the same command, the command is denied.
- B . If you allow and deny the same command, Junos OS will randomly choose the action.
- C . If you allow and deny the same command, the command is allowed.
- D . If you allow and deny the same command, the Junos OS will fail the commit check.
C
Explanation:
Understanding the Allow and Deny Statement Precedence and Matching By default, the allow-commands and allow-configuration regular expressions take precedence over deny-commands and deny-configuration expresssions. Thus, if you configure the same command for both the allow-commands and deny-commands statements, then the allow operation takes precedence over the deny operation.
Ref: User Access Privileges | Junos OS | Juniper Networks
“User Access Privileges
…
Understanding the Allow and Deny Statement Precedence and Matching
By default, the allow-commands and allow-configuration regular expressions take precedence over deny-commands and deny-configuration expresssions. Thus, if you configure the same command for both the allow-commands and deny-commands statements, then the allow operation takes precedence over the deny operation.
..,.”
By default, which Junos directory contains the primary syslog file?
- A . /var/syslog
- B . /var/home
- C . /var/log
- D . /var/tmp
C
Explanation:
Ref: Junos® OS Overview for Junos OS | Juniper Networks
Page 23
“…
• /var―This directory is located either on the hard drive (device wd2) or internal flash storage. It contains the following subdirectories:
…
• /log―Contains system log and tracing files. …”
Which two statements about routing policies are correct? (Choose two.)
- A . An import policy is used to control incoming traffic on a specific interface.
- B . An export policy determines the routes in the local routing table that are advertised to peers.
- C . An import policy is used to control routes that are accepted by the local routing table.
- D . An export policy is used to control outgoing traffic on a specific interface.
BC
Explanation:
Ref: Understanding Routing Policies | Junos OS | Juniper Networks
“Understanding Routing Policies
…
Importing and Exporting Routes
Two terms―import and export―explain how routes move between the routing protocols and the routing table.
• When the Routing Engine places the routes of a routing protocol into the routing table, it is importing routes into the routing table.
• When the Routing Engine uses active routes from the routing table to send a protocol advertisement, it is exporting routes from the routing table.
…”
You are creating a route filter that will match the network address of 192.168.64.0/24 In this scenario, which configuration statement will accomplish this task?
- A . from route-filter 192.168.32.0/24 longer
- B . from route-filter 152.168.128.0/24 orlonger
- C . from route-filter 192.168.64.0/24 longer
- D . from route-filter 192.168.64.0/24 orlonger
You must recover a device by loading the rescue configuration file.
In this scenario, which command will accomplish this task?
- A . {master:0}
user@router> load override rescue - B . {master:0}
user@router> rollback rescue - C . {master:0} [edit]
user@routert load override rescue - D . {master:0} [edit]
user@router# rollback rescue
D
Explanation:
{master:0} [edit] user@router# rollback rescue
This command is used to load the rescue configuration file on a Junos device. The "rollback rescue" command will restore the device to a previously saved backup configuration, which is stored as a rescue configuration file. This is useful in case the current configuration becomes unavailable or if the device is unable to boot properly. The "rollback" keyword indicates that we want to restore the previous configuration and the "rescue" keyword specifies that we want to restore the rescue configuration file.
It is important to note that the correct prompt for this command is in configuration mode, indicated by "[edit]" in the prompt.
Which two statements describe firewall filters? (Choose two.)
- A . Firewall filters are applied to interfaces.
- B . Firewall filters are applied to security policies
- C . Firewall filters provide stateless security.
- D . Firewall filters provide stateful security.
Click the Exhibit button.
You must apply the policy shown in the exhibit to readvertise BGP routes to OSPF neighbors
Which action will accomplish this task?
- A . You must apply the policy as an import policy within the BGP configuration
- B . You must apply the policy as an import policy within the OSPF configuration.
- C . You must apply the policy as an export policy within the BGP configuration
- D . You must apply the policy as an export policy within the OSPF configuration
What are two benefits of class of service (CoS)? (Choose two.)
- A . CoS can increase the performance of a slow network.
- B . CoS can manage traffic congestion
- C . CoS can prioritize latency-sensitive traffic
- D . CoS can increase network bandwidth.
B, C
Explanation:
Ref: Benefits of CoS | Junos OS | Juniper Networks
“Benefits of CoS
…
CoS features allow a Juniper Networks device to improve its processing of critical packets while maintaining best-effort traffic flows, even during periods of congestion.
…
CoS dedicates a guaranteed minimum bandwidth to a particular service class by reducing forwarding queue delays.
Which component is responsible for performing protocol updates and system management?
- A . forwarding tables
- B . Routing Engine
- C . bridging table
- D . Packet Forwarding Engine
B
Explanation:
The Routing Engine is the brain of the platform. It is responsible for performing protocol updates and system management. The Routing Engine runs various protocol and management software processes that reside inside a protected memory environment.
https://www.coursera.org/lecture/juniper-automation-xml/junos-os-basic-design-architecture-T3hpf#:~:text=The%20Routing%20Engine%20is%20the,inside%20a%20protected%20memory%20en vironment.
Click the Exhibit button
Referring to the exhibit, what will be the source address for packets egressing et-0/0/34.07
- A . 10.20.0.1
- B . 10.30.0.1
- C . 10.10.0.1
- D . 10.40.0.1
A
Explanation:
https://www.youtube.com/watch?v=045KRRS9fCg&t=396s