ISC CISSP-ISSMP ISC Information Systems Security Management Professional Online Training
ISC CISSP-ISSMP Online Training
The questions for CISSP-ISSMP were last updated at Dec 13,2025.
- Exam Code: CISSP-ISSMP
- Exam Name: ISC Information Systems Security Management Professional
- Certification Provider: ISC
- Latest update: Dec 13,2025
Which of the following laws is the first to implement penalties for the creator of viruses, worms, and other types of malicious code that causes harm to the computer systems?
- A . Gramm-Leach-Bliley Act
- B . Computer Fraud and Abuse Act
- C . Computer Security Act
- D . Digital Millennium Copyright Act
SIMULATION
Fill in the blank with an appropriate phrase.________ models address specifications, requirements, and design, verification and validation, and maintenance activities.
You are the project manager of the GHE Project.
You have identified the following risks with the characteristics as shown in the following figure:
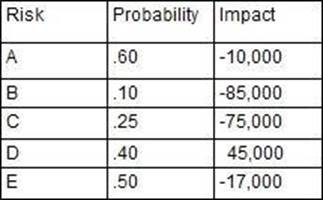
How much capital should the project set aside for the risk contingency reserve?
- A . $142,000
- B . $232,000
- C . $41,750
- D . $23,750
Which of the following statements about system hardening are true? Each correct answer represents a complete solution. Choose two.
- A . It can be achieved by installing service packs and security updates on a regular basis.
- B . It is used for securing the computer hardware.
- C . It can be achieved by locking the computer room.
- D . It is used for securing an operating system.
Which of the following are the common roles with regard to data in an information classification program? Each correct answer represents a complete solution. Choose all that apply.
- A . Editor
- B . Custodian
- C . Owner
- D . Security auditor
- E . User
Which of the following processes is described in the statement below? "It is the process of implementing risk response plans, tracking identified risks, monitoring residual risk, identifying new risks, and evaluating risk process effectiveness throughout the project."
- A . Monitor and Control Risks
- B . Identify Risks
- C . Perform Qualitative Risk Analysis
- D . Perform Quantitative Risk Analysis
Walter is the project manager of a large construction project. He’ll be working with several vendors on the project. Vendors will be providing materials and labor for several parts of the project. Some of the works in the project are very dangerous so Walter has implemented safety requirements for all of the vendors and his own project team. Stakeholders for the project have added new requirements, which have caused new risks in the project. A vendor has identified a new risk that could affect the project if it comes into fruition. Walter agrees with the vendor and has updated the risk register and created potential risk responses to mitigate the risk.
What should Walter also update in this scenario considering the risk event?
- A . Project contractual relationship with the vendor
- B . Project management plan
- C . Project communications plan
- D . Project scope statement
You are the project manager of the HJK Project for your organization. You and the project team have created risk responses for many of the risk events in the project.
Where should you document the proposed responses and the current status of all identified risks?
- A . Risk management plan
- B . Lessons learned documentation
- C . Risk register
- D . Stakeholder management strategy
Which of the following security controls will you use for the deployment phase of the SDLC to build secure software? Each correct answer represents a complete solution. Choose all that apply.
- A . Vulnerability Assessment and Penetration Testing
- B . Security Certification and Accreditation (C&A)
- C . Change and Configuration Control
- D . Risk Adjustments
Which of the following can be prevented by an organization using job rotation and separation of duties policies?
- A . Collusion
- B . Eavesdropping
- C . Buffer overflow
- D . Phishing
Latest CISSP-ISSMP Dumps Valid Version with 218 Q&As
Latest And Valid Q&A | Instant Download | Once Fail, Full Refund

