IIBA CBAP Cetified business analysis professional (CBAP) appliaction Online Training
IIBA CBAP Online Training
The questions for CBAP were last updated at Dec 17,2025.
- Exam Code: CBAP
- Exam Name: Cetified business analysis professional (CBAP) appliaction
- Certification Provider: IIBA
- Latest update: Dec 17,2025
Which of the following compares two or more systems, states, services, products, or things to determine the best viable choice?
- A . Benchmarking
- B . Risk Identification
- C . Risk analysis
- D . Cost-benefit analysis
Contracts are currently managed by more than 20 contract owners across the organization, each happily managing in their own way. A business analyst (BA) is tasked to elicit requirements for centrally managing software maintenance and license contracts.
Which of the following does the BA need to carry out first?
- A . Identify business requirements
- B . Identify future state conditions
- C . Recommend an off the shelf product
- D . Complete an enterprise readiness assessment
An insurance company wants to implement a business intelligence solution to consolidate data from various different internal system to provide a better understanding of their customer base.
A business analysis (BA) is engaged to put together a tender (bid) to be sent to various business intelligence providers and implemention partners.
Among other information the business analysis request the following:
* Licensing costs for year 0 based on needing 1 Central processing Unit (CPU) license
* Licensing costs for specific user types such as Report Creators Online Analytical Process (OLAO) user and Power users
* Predicted licensing costs for renewing in Years 1 and 2
* Full implementation costs
After reviewing the received vendor responses the project team shortlists the candidates to 3 and the BA structures the received information as follows:
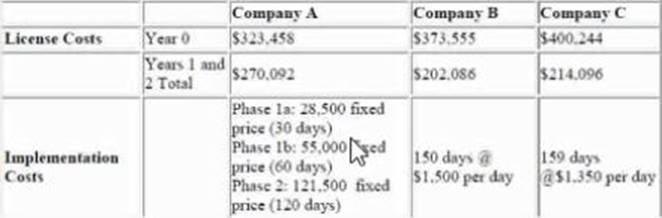
The Insurance company has a maximum bucket of $310,000 for the entire to implementation and operation over the first three years .
Which vendor or vendors meet that criteria?
- A . Both companies B and C
- B . Company B
- C . Company A
- D . Both companies A and C
What document defines the business needs, identifies key stakeholders, and describes the positive impact the solution will provide on the key stakeholders?
- A . Project charter
- B . Project scope statement
- C . Solution scope
- D . Vision statement
You have completed the requirements documentation and the stakeholders have signed off on the requirements. Now the requirements are advancing into a project as your organization has chartered a project based on the identified requirements.
What stakeholder is now responsible for assessing the solution scope to determine the
project scope?
- A . Project sponsor
- B . Project manager
- C . Business analyst
- D . Key stakeholders
Which of the following roles approves the project scope statement, phase gate reviews, solution validations, scope changes, and project success criteria?
- A . Project manager
- B . Subject matter expert
- C . Solution owner
- D . Stakeholder
Which of the following tasks does not rely on other activities, and no other activities rely on this task completing?
- A . Analysis task
- B . Independent task
- C . Predecessor task
- D . Dependent task
You are the business analyst for the NHQ Project. You have identified several stakeholders that need different types of information related to the requirements.
Which stakeholder would need detailed technical interface requirements?
- A . Project manager
- B . Regulators
- C . Testers
- D . Implementation subject matter experts
A conservative company with rigorous risk control plans and internal audit rules has a recurrent problem with a core Business application. As a result access to this application must be restricted and controlled and maintenance must be on-site. However the company feels that the application must have an emergency service team. The routine maintenance of this solution is provided by an external vendor and the vendor requested 24 hours remote access to quality and production data.
In this context what is the company’s response to the vendor’s request?
- A . Dented because of the company’s risk aversion
- B . Accepted, because the company has an urgent problem to solve
- C . Denied- because the vendor requested it
- D . Accepted, because immediate remote access will resolve any issue
Which of the following processes is used by organizations to set the risk tolerance, identify the potential risks, and prioritize the tolerance for risk?
- A . Risk communication
- B . Risk identification
- C . Risk analysis
- D . Risk management
Latest CBAP Dumps Valid Version with 498 Q&As
Latest And Valid Q&A | Instant Download | Once Fail, Full Refund

