When the air interface frame is a management frame, how many bits are the ESS and IBSS in the Capability Info field of the management frame that can determine the device is a wireless bridge?
- A . 00
- B . 01
- C . 10
- D . 11
According to the detection results reported by the AP, the AC can obtain the neighbor relationship between the AP and the surrounding devices, as well as the neighbor relationship of all radio frequency devices under the entire AC including legal APs, illegal APs, and non-Wi-Fi interfering devices, as shown in the following figure:
In order to prevent the reported data from being too large, only the legal neighbors with signal strength greater than -85dBm and illegal neighbors with signal strength greater than () dBm are reported here.
- A . -75
- B . -80
- C . -85
- D . -90
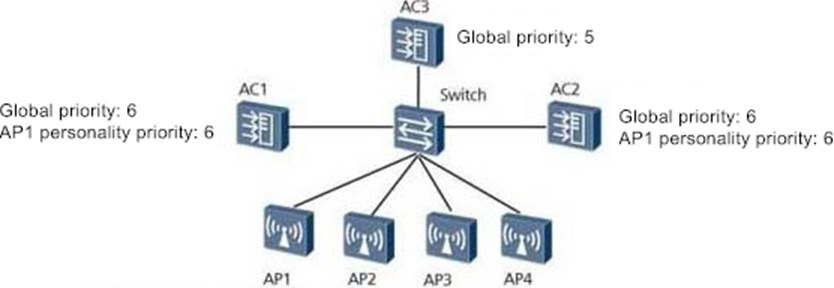
In the N+1 backup network as shown in the figure, AC3 is the backup AC of AC1 and AC2, the number of APs that are online on the main AC1 is 1024, the number of configured APs is 2048, and the number of APs that are online on the main AC2 is 512. Normally, what is the minimum number of APs allowed to access on AC3, and what is the minimum number of APs allowed to be configured on AC3?
- A . 2048, 1024
- B . 1024, 2048
- C . 3072, 512
- D . 1024, 2560
As shown in the figure, in the Mesh network, which STP spanning tree protocol needs to be enabled?
- A . AC G0/0/1 interface
- B . MPP
- C . MP
- D . Switch
As shown in the figure, a point-to-point link with a length of 3km, and an office building with a height of 9.1m from the ground at the midpoint of the link, if the signal transmission frequency is 5.8GHz, please refer to the following formula according to the actual situation, what is the minimum installation height of the transmit and receive antenna from the ground?
- A . 9.1m
- B . 10m
- C . 13m
- D . 18m
Which one of the following four scenarios does not belong to the Mesh network?
- A . (a)
- B . (b)
- C . (c)
- D . (d)
As shown in the figure, in a large enterprise WLAN network, the company’s network administrator recently discovered that the WLAN network traffic was abnormal, and the ping gateway was delayed or a large amount of packets was lost. After excluding other possibilities, it was suspected of being an illegal network attack. Which of the following illegal attacks is most likely?
- A . Flood attack
- B . Spoof attack
- C . Weak IV attack
- D . Brute force cracking
As shown in the figure, a point-to-point communication link with a length of 10km, a tree with an obstacle height of 12.2m in the link, and a distance between the tree and one of the antennas is 4km, calculate the radius of Fresnel zone at 4km, if the signal transmission frequency is 5.8GHz, refer to the following formula according to the actual situation, what is the minimum installation height of the transmit and receive antenna from the ground?
- A . 16
- B . 19
- C . 22
- D . 26
In the network shown in the figure below, the data traffic before roaming is forwarded as STA-HAP-HAC-upper network. After layer 2 roaming, what is the direction of data forwarding traffic?
- A . STA-FAP-FAC-HAC-Upper Network
- B . STA-FAP-FAC-HAC-HAP-HAC-upper network
- C . STA-FAP-FAC-Upper Network
- D . STA-FAP-FAC-HAC-FAC-Upper Network
According to the process of Mesh connection establishment, which of the following steps are correct?
- A . 4->3->2->1
- B . 4->2->3->1
- C . 2->3->4->1
- D . 2->4->3->1
Which of the following is correct about the Earth curvature formula?
- A . A.
- B . B.
- C . C.
- D . D.
As shown in the figure, what is the load sharing method of the dual-system hot backup solution?
- A . A.
- B . B.
- C . C.
- D . D.
As shown in the figure, in the dual-link cold standby load sharing network, AP1 is a newly online AP, and both the two ACs have access configurations, which AC will AP1 choose for access?
- A . AC1
- B . AC2
- C . Random access
- D . No access
As shown in the figure, in public places, such as different companies on adjacent floors in an office building, there are multiple SSIDs. After a company turns on the WIDS illegal device counter function, it will counter the AP of other companies. Which of the following function can effectively solve this problem?
- A . Dynamic blacklist function
- B . WIDS countermeasure mode switching
- C . WIDS counterfeit SSID detection
- D . WIDS whitelist function
As shown in the figure, in order to avoid the transparent transmission of STP packets and cause loops to affect each other, which of the following does not need to enable the STP spanning tree protocol?
- A . Only the MPP wired side interface needs to enable the STP function
- B . Only the MP3 wired side interface needs to enable the STP function
- C . Both MPP and MP3 wired side interfaces need to enable STP function
- D . MP1 and MP2 need to enable STP
As shown in the figure is the WIDS attack detection process. After the dynamic blacklist is issued, how will the AP handle different data traffic when it is in the blacklist penalty period?
- A . Forward normal data traffic and discard attack traffic
- B . Discard normal data traffic and report attack traffic
- C . Forward normal data traffic and report attack traffic
- D . Discard normal data traffic and discard attack traffic
As shown in the figure, there are 4 online STAs (STA1-STA4) under AP1 radio frequency, and 1 online STA (STA5) under AP2 radio frequency. The load balancing start threshold 5 is exceeded, and the maximum number associated users supported by AP1 and AP2 radio frequencies is 10, and the configured load difference threshold is 10%.
When STA6 initiates a request to AP1 for the first time, which of the following statements is correct?
- A . AP1 is first calculated according to the load balancing algorithm, and STA6 is allowed to access
- B . AP1 is calculated according to the load difference threshold algorithm first, and STA6 is allowed to access
- C . AP1 is first calculated according to the load balancing algorithm, and STA6 is denied access
- D . AP1 is calculated based on the load difference threshold algorithm first, and STA6 is denied access
In the network shown in the figure, how is the route selected from A to D in the pro-active mode?
- A . A-MPP-D
- B . A-B-D
- C . A-B-C-D
- D . A-D
In the network shown in the figure below, the data traffic before roaming is forwarded as STA-HAP-HC-upper network, and the forwarding method is tunnel forwarding. After three-layer roaming, what is the direction of data forwarding traffic?
- A . STA-FAP-FAC-HAC-Upper Network
- B . STA-FAP-FAC-HAC-HAP-HAC-upper network
- C . STA-FAP-FAC-Upper Network
- D . FAP-FAC-HAC-FAC-Upper Network
In the network as shown in the figure below, the data traffic is forwarded as STA-HAP-HAC-upper network before roaming, and the forwarding method is direct forwarding, and the home agent is configured on the AC. After three-layer roaming, what is the direction of data forwarding traffic?
- A . STA-FAP-FAC-Upper Network
- B . STA-FAP-FAC-HAC-FAC-Upper Network
- C . STA-FAP-FAC-HAC-Upper Network
- D . STA-FAP-FAC-HAC-HAP-HAC-upper network
As shown in the figure, in a dual-link load balancing hot backup network, AP1 is a newly online AP, and both ACs have access configurations, which AC will AP1 choose for access?
- A . AC1
- B . AC2
- C . Random access
- D . No access
In a WLAN network, the AP group is named ap-group and the WIDS template is wids. Now you need to enable the WIDS device counter function to counter APs with counterfeit SSID=huawei. As shown in the figure, which of the following configuration is correct?
- A . 1>2>4
- B . 5>2>3
- C . 1>2>3
- D . 5>2>4
The following figure shows the mesh configuration process. What should be filled in for 5, 7, and 10 respectively?
- A . Quote Mesh template, configure Mesh whitelist, configure Mesh template
- B . Configure Mesh whitelist, configure Mesh template, quote Mesh template
- C . Configure Mesh template, quote Mesh template, configure Mesh whitelist
- D . Configure Mesh whitelist, quote Mesh template, configure Mesh template
As shown in the figure, regarding the active/standby mode of the dual-system hot backup solution, which of the following statements is wrong?
- A . VRRP can be applied to active/standby backup and load sharing
- B . The selection of dual-system hot backup master and backup devices is consistent with the selection of VRRP group master and backup devices
- C . The active/standby status of the HSB active/standby backup group is consistent with the VRRP active/standby status
- D . For the same AP associated with the active and standby ACs, the WLAN-related service configuration must be consistent. Otherwise, the normal operation of the AP cannot be guaranteed after the AC’s active and standby status is switched
If a small conference room with a maximum of 90 people is equipped with 3 APs, by configuring CAC on each AP, the number of users cannot exceed 30, and the SSID will be hidden after exceeding, which can indirectly achieve the effect of load balancing among APs.
- A . True
- B . False
Regarding the precautions for configuring HSB main and backup services, which of the following statements is wrong?
- A . If you want to modify, you need to delete the HSB active and standby services first, and then reconfigure
- B . Only after enabling the dual-system hot backup function, the configured HSB active/standby backup channel parameters will take effect
- C . After the configuration is complete, you can modify the HSB main and backup channel parameters
- D . After the configuration is complete, you cannot directly modify the HSB main and backup channel parameters
Regarding the relationship between the two technologies of 802.1x and RADIU S, which of the following descriptions is correct?
- A . 802.1x and RADIUS are different names of the same technology
- B . 802.1x is a technical system, which includes RADIUS
- C . 802.1x and RADIUS are different technologies, but they are often used together to complete the access control of end users.
- D . 802.1x and RADIUS are two completely different technologies, and they are usually not used together
In the WLAN outdoor long-distance point-to-point communication, if a stable communication link is to be maintained, what percentage of the first Fresnel area generally cannot be blocked?
- A . 0.2
- B . 0.4
- C . 0.5
- D . 0.6
In the load balancing mode, which of the following regarding the statement about the processing method of hot backup by RADIUS/Portal server is correct?
- A . Account and authenty the NAS-IP-Address and accounting session-id filled in the backup packet
- B . The srcip in the Radius packet sent by the AC needs to be the same, and the COA/DM device address configured in the Radius server can be different from one to the other
- C . In the case of DOWN/uplink interruption of the original master node, the COA/DM message received by the node needs to be processed and synchronized to the opposite end, and the master device needs to issue authorization information to the AP
- D . When the original master node, not the whole machine down/uplink is interrupted, the backup node also configures a Loopback interface with the same IP as the master node. This interface is not directly added to the IGP, but imported through import direct
In smart roaming, which of the following methods to identify sticky terminals is correct?
- A . When the results of 3 consecutive detection cycles are less than the set roaming threshold
- B . When the results of 3 consecutive detection cycles are greater than the set roaming threshold
- C . When the results of 6 consecutive detection cycles are less than the set roaming threshold
- D . When the results of 6 consecutive detection cycles are greater than the set roaming threshold
APs in monitoring mode in the WLAN network can not only monitor peripheral devices but also forward WLAN data.
- A . True
- B . False
In the Mesh network, if the MP is connected to the wired network, it is necessary to ensure that the MP and MPP cannot communicate with each other through the wired network. Otherwise, the MPP and MP can communicate with each other through the Mesh link and the wired link. Mesh and wired The link will form a loop between MPP and MP.
- A . True
- B . False
When the air interface frame is a data frame, the DS value needs to be compared. When the values of To DS and From DS are respectively, the device type is AP?
- A . 0, 0
- B . 0, 1
- C . 1, 0
- D . 1, 0
There are three implementations of CAC. Which of the following statements about the implementation of CAC based on channel utilization is wrong?
- A . When the AP receives a new user online request, it first calculates the channel utilization rate on the current radio, and if the new user threshold is not reached, the new user is allowed to go online
- B . If the channel utilization reaches the new user threshold after the new user goes online, the access request of other new users is rejected and an alarm is sent, but the SSID cannot be hidden
- C . For the access of roaming users, check whether the channel utilization rate has reached the roaming user threshold. If it reaches, then reject the roaming user’s access request and send an alarm
- D . The AP periodically checks the channel utilization of the radio frequency, and once it drops below the threshold for new users, it sends a release alarm to allow new users to go online
Which of the following descriptions about Mesh routing establishment in pro-active mode is correct?
- A . MP periodically sends broadcast PREQ, receives MP/MPP response unicast PREP, and establishes a round-trip route between any two points
- B . MPP sends broadcast RANN periodically, receives MP and sends unicast PREQ to MPP, MPP responds to PREP after receiving it, and establishes a route between MP and MPP
- C . MPP periodically sends broadcast RANN, receives MP and sends unicast PREP to MPP, and establishes a route between MP and MPP
- D . MPP periodically sends broadcast PREQ, the received MP responds to unicast PREP, and establishes a route between MP and MPP
In the WLAN network, the Weak IV attack detection function does not require the support of the dynamic blacklist function.
- A . True
- B . False
The antenna is different from the signal amplifier. It is a passive device that does not require power supply, but only guides and shapes the wireless signal.
- A . True
- B . False
Regarding enabling the HSB backup group, if the AP is already online on the main AC, and then the AP information is added offline on the standby AC, the AP status on the standby AC will display fault. In this case, you need to execute the undo hsb enable command in the HSB backup group view of the standby AC to enable the HSB active/standby backup function, and then execute the hsb enable command to enable the HSB active/standby backup function, and then back up the information on the active AC again. The backup information of the active and standby is consistent, and the AP status on the standby AC will be displayed as standby at this time.
- A . True
- B . False
In a large-scale WLAN network, in order to improve the reliability of the C APWAP link between AP and AC, the DSCP priority of CAPWAP management messages can be configured as high priority.
- A . True
- B . False
Which of the following commands can be used to check whether the AP channel and transmit power are enabled with the automatic selection function?
- A . [AC-wlan-view] display station ssid wlan-net
- B . [AC-wlan-view] display rrm-profile name profile-name
- C . [AC-wlan-view] display radio all
- D . [AC-wlan-view] display yap-profile name profile-name
In the WLAN network environment using the Agile Controller, regarding the 802.1x authentication failure, which of the following phenomena does not meet?
- A . The client’s 802.1x authentication fails
- B . The client is repeatedly disconnected after passing 802.1x authentication
- C . The device test-aaa login test is normal, and the authentication interface cannot be opened
- D . Enter the correct account password and always prompt that the account name and password are incorrect
In smart roaming, sticky terminals that do not support 802.11k need to scan to obtain information of the surrounding APs to determine whether there are better neighbor APs.
- A . True
- B . False
In the packet-by-packet power adjustment feature, the basis for the AP to select the transmission power for the terminal each time before sending a data packet is mainly the current signal strength of the terminal. If the terminal signal is good, it will be sent at a lower power, otherwise it will be sent at a higher power.
- A . True
- B . False
When a large enterprise deploys a WLAN Layer 3 network, it needs to configure the Option 43 field on the Windows 2003 DHCP Server to notify the AP of the AC’s IP address.
The AC’s IP address is 10.23.100.1. Which of the following needs to be configured in the Option 43 field on the JDHCP Server?
- A . 030831302E32332E3130302E31
- B . 040831302E32332E3130302E31
- C . 030B31302E32332E3130302E31
- D . 030B31302E32332E31302E3031
If the time is set in the authorization element of the Agile Controller, what is the purpose of configuring the time during authentication and authorization rules?
- A . Specify the total duration of user access
- B . Specify the time point of user access
- C . Specify the deadline for users to be offline
- D . Specify the time range for user access
Which of the following commands can be used to create an RF tuning template?
- A . [AC-wlan-view] rrm-profile name wlan-net
- B . [AC-wlan-view] regulatory-domain-profile name domain1
- C . [AC-wlan-view] wired-port-profile name wired-port
- D . [AC-wlan-view] ap-system-profile name mesh-sys
Which of the following commands can be used to create an RF tuning template?
- A . [AC-wlan-view] rrm-profile name wlan-net
- B . [AC-wlan-view] regulatory-domain-profile name domain1
- C . [AC-wlan-view] wired-port-profile name wired-port
- D . [AC-wlan-view] ap-system-profile name mesh-sys
Which of the following commands can be used to create an RF tuning template?
- A . [AC-wlan-view] rrm-profile name wlan-net
- B . [AC-wlan-view] regulatory-domain-profile name domain1
- C . [AC-wlan-view] wired-port-profile name wired-port
- D . [AC-wlan-view] ap-system-profile name mesh-sys
Which of the following commands can be used to create an RF tuning template?
- A . [AC-wlan-view] rrm-profile name wlan-net
- B . [AC-wlan-view] regulatory-domain-profile name domain1
- C . [AC-wlan-view] wired-port-profile name wired-port
- D . [AC-wlan-view] ap-system-profile name mesh-sys
Which of the following commands can be used to create an RF tuning template?
- A . [AC-wlan-view] rrm-profile name wlan-net
- B . [AC-wlan-view] regulatory-domain-profile name domain1
- C . [AC-wlan-view] wired-port-profile name wired-port
- D . [AC-wlan-view] ap-system-profile name mesh-sys
Which of the following commands can be used to create an RF tuning template?
- A . [AC-wlan-view] rrm-profile name wlan-net
- B . [AC-wlan-view] regulatory-domain-profile name domain1
- C . [AC-wlan-view] wired-port-profile name wired-port
- D . [AC-wlan-view] ap-system-profile name mesh-sys
Which of the following commands can be used to create an RF tuning template?
- A . [AC-wlan-view] rrm-profile name wlan-net
- B . [AC-wlan-view] regulatory-domain-profile name domain1
- C . [AC-wlan-view] wired-port-profile name wired-port
- D . [AC-wlan-view] ap-system-profile name mesh-sys
Which of the following commands can be used to create an RF tuning template?
- A . [AC-wlan-view] rrm-profile name wlan-net
- B . [AC-wlan-view] regulatory-domain-profile name domain1
- C . [AC-wlan-view] wired-port-profile name wired-port
- D . [AC-wlan-view] ap-system-profile name mesh-sys
Configure the country code
- A . 4 → 1 → 3 → 7 → 2 → 6 → 5
- B . 7 → 1 → 3 → 4 → 2 → 6 → 5
- C . 7 → 4 → 3 → 1 → 2 → 6 → 5
- D . 4 → 3 → 1 → 7 → 2 → 6 → 5
Three-layer roaming means that when the user roams from the original AP to the new AP, the service VLAN corresponding to the VAP changes, and the user’s data message is switched to the VLAN of the new AP after roaming.
- A . True
- B . False
In smart roaming, terminals that support 802.11k can actively collect neighbor AP information and report it to the associated AP.
- A . True
- B . False
Configure the Option 43 field on the Windows 2003 DHCP Server. For example, the string 030C3139322E3136382E32322E31 represents 192.168.22.1. The fixed value of 03, 0C changed to decimal is 12, which means the string length of the IP address, the address 192.168.22.1 has a total of 12 characters, 31 means the ASCII value corresponds to 1, 9 corresponds to 9, and so on, 2E means dot.
So what should be the string corresponding to the IP address 32.15.2.14?
- A . 030733322E31352E322E3134
- B . 030A33322E31352E322E3134
- C . 030A3033322E3031352E3030322E303134
- D . 030A32332E35312E322E3431
In WLAN smart roaming, what is the mechanism time for blind user protection?
- A . 20 minutes
- B . 30 minutes
- C . 60 minutes
- D . 15 minutes
In WLAN smart roaming, what is the mechanism time for blind user protection?
- A . 20 minutes
- B . 30 minutes
- C . 60 minutes
- D . 15 minutes
In WLAN smart roaming, what is the mechanism time for blind user protection?
- A . 20 minutes
- B . 30 minutes
- C . 60 minutes
- D . 15 minutes
In WLAN smart roaming, what is the mechanism time for blind user protection?
- A . 20 minutes
- B . 30 minutes
- C . 60 minutes
- D . 15 minutes
In WLAN smart roaming, what is the mechanism time for blind user protection?
- A . 20 minutes
- B . 30 minutes
- C . 60 minutes
- D . 15 minutes
In WLAN smart roaming, what is the mechanism time for blind user protection?
- A . 20 minutes
- B . 30 minutes
- C . 60 minutes
- D . 15 minutes
Filter out APs that meet the threshold difference condition
- A . 1 → 2 → 3 → 4 → 5
- B . 1 → 3 → 4 → 5 → 2
- C . 1 → 5 → 3 → 2 → 4
- D . 1 → 4 → 5 → 3 → 2
Although the Fresnel zone exists in all radio frequency communication scenarios, its impact is mainly considered in which of the following communications?
- A . Outdoor point-to-point scene
- B . Indoor Mesh scene
- C . Indoor cellular coverage
- D . Outdoor cellular coverage
The typical networking of Huawei outdoor AP6510DN, AP6610DN, AP8030DN, AP8130DN all support access point mode and bridge mode.
- A . True
- B . False
Which of the following does not belong to the purpose of WLAN equipment upgrade?
- A . Fix existing problems
- B . Optimize the performance of the equipment
- C . Get new features and functions
- D . Extend the service life of the equipment
In large WLAN networks, customers usually deploy directory servers. What is the main function of the directory server?
- A . Provide users with database resource index
- B . Provide users with mail management services
- C . Provide server cluster management services for large networks
- D . Provide user information for the authentication server
AC6005 enables the flood attack detection function. By default, what is the flood attack detection cycle and the maximum number of similar packets?
- A . 30s, 100
- B . 45s, 150
- C . 60s, 300
- D . 90s, 400
In the WLAN network, the AP group is named ap-group1, and the WIDS template is named widsl. Now you need to enable the WIDS device detection function globally. Which of the following configurations is correct?
- A . [AC-wlan-view] ap-group name ap-group1
[AC-wlan-ap-group-ap-group1] radio 0
[AC-wlan-group-radio-ap-group1/0] work-mode monitor
[AC-wlan-group-radio-ap-group1/0] wids device detect enable - B . [AC-wlan-view] ap-id 0 [AC-wlan-ap-0] radio 0
[AC-wlan-radio-0/0] work-mode monitor
[AC-wlan-radio-0/0] wids device detect enable - C . [AC-wlan-view] wids-profile name wids1
[AC-wlan-wids-prof-wids1] device detect enable - D . [AC-wlan-view] wids-profile name wids1
[AC-wlan-wids-prof-wids1] wids device detect enable
Which of the following behaviors is a threat to WLAN network security?
- A . Weak IV attack
- B . WDS
- C . WIDS
- D . WIPS
The following is the URL template configuration when configuring the AC6005 to connect to the Portal server. Which of the following statement is error?
- A . The port number 8080 can be changed to 8443
- B . Portal can be changed to webauth
- C . url-parameter ssid ssid means SSID=ssid
- D . url-parameter ssid ssid means any ssid
Regarding the definition of WIPS/WIDS, which of the following statements is correct?
- A . WIDS is a wireless intrusion prevention system
- B . WIPS is a wireless intrusion detection system
- C . WIDS is a wireless intrusion countermeasure system
- D . WIPS is a wireless intrusion prevention system
Which of the following descriptions of Mesh wired port parameters are correct?
- A . Enabling the user isolation function is mainly convenient for centralized billing, but it does not help improve user communication security
- B . Wired ports of Mesh APs can pass all VLANs by default
- C . Mesh only supports adding AP wired ports to VLANs in untagged form
- D . Mesh supports adding AP wired ports to ^WLAN in the form of Untagged and Tagged
Regarding the dual-link hot standby configuration, when configuring the priority of an AC, the larger the priority value, the higher the actual priority of the AC.
- A . True
- B . False
Regarding the precautions for configuring the dual-system hot backup function, which of the following statements is wrong?
- A . When configuring dual-link hot backup, you need to use the commit command on the AC to deliver the configuration to the AP after completing the service configuration on both the active and standby ACs.
- B . When configuring dual-link hot backup, after the main AC completes the service configuration, execute the commit command to deliver the configuration to the AP, and then complete the configuration of the standby AC
- C . When configuring dual-link hot backup, for the same AP associated with the active and standby ACs, the WLAN-related service configuration must be consistent. Otherwise, the normal operation of the AP cannot be guaranteed after the AC’s active and standby status is switched.
- D . During dual-link hot backup active/standby switching, due to the long switching time, the business data forwarded by the tunnel will be interrupted during this period, and new user will not be able to go online, and online users will not be able to roam.
When the engineer adjusted the directional antenna, it was found that when the antenna was placed far from the other antenna, the signal would drop, and then the signal would increase slightly. What caused this increase in signal?
- A . Signal reflection
- B . Frequency harmonics
- C . Sideband
- D . Sidelobes
Regarding the maintenance of the link status of the active and standby channels, to prevent the TCP from being interrupted for a long time but the protocol stack does not detect the connection interruption, which can be prevented by sending the active and standby service messages and retransmission mechanisms.
- A . True
- B . False
Which of the following descriptions of the Fresnel zone is correct?
- A . The narrower the beam width, the larger the Fresnel area
- B . The narrower the beam width, the smaller the Fresnel area
- C . The Fresnel zone has nothing to do with the beam width
- D . Other options are incorrect
When a user is online, it is convenient to find which AC the user is currently online, so as to obtain user data. In order to quickly know which AC a user is currently online, each AC needs to save the online status of all ACs in the roaming group and all users.
- A . True
- B . False
When a user is online, it is convenient to find which AC the user is currently online, so as to obtain user data. In order to quickly know which AC a user is currently online, each AC needs to save the online status of all ACs in the roaming group and all users.
- A . True
- B . False
When a user is online, it is convenient to find which AC the user is currently online, so as to obtain user data. In order to quickly know which AC a user is currently online, each AC needs to save the online status of all ACs in the roaming group and all users.
- A . True
- B . False
When a user is online, it is convenient to find which AC the user is currently online, so as to obtain user data. In order to quickly know which AC a user is currently online, each AC needs to save the online status of all ACs in the roaming group and all users.
- A . True
- B . False
When a user is online, it is convenient to find which AC the user is currently online, so as to obtain user data. In order to quickly know which AC a user is currently online, each AC needs to save the online status of all ACs in the roaming group and all users.
- A . True
- B . False
Assign VLAN to the terminal according to the VLAN algorithm
- A . 3 → 2 → 4 → 1
- B . 4 → 2 → 3 → 1
- C . 4 → 3 → 2 → 1
- D . 3 → 4 → 2 → 1
In the same frequency Mesh network, the transmission bandwidth of two APs is about 200M. What is the average transmission bandwidth when adding one AP?
- A . Up to 200M
- B . Up to 150M
- C . Up to 100M
- D . Up to 50M
The Agile Controller synchronization methods include manual synchronization and automatic synchronization. Which of the following statements about synchronization methods are correct?
- A . Agile Controller can only use one synchronization method to avoid mutual interference
- B . The first time the Agile Controller is synchronized, manual synchronization must be used, and then automatic synchronization can be used.
- C . The synchronization time point for the automatic synchronization of the Agile Controller can be modified
- D . Agile Controller manual synchronization can only be used three times a day to prevent artificial increase in network load
When installing a long-distance point-to-point radio frequency communication link, if the distance between the transmitting and receiving antennas exceeds how many kilometers, the influence of the curvature of the earth needs to be considered?
- A . 3.3km
- B . 5.3km
- C . 7.3km
- D . 11.3km
In a WLAN network, when the AP is in monitoring mode, what kind of message does the AP use to determine the device type?
- A . DHCP
- B . ARP
- C . CAPWAP
- D . 802.11MAC
In dual-system hot backup, which of the following statements about HSB backup channels is wrong?
- A . The HSB backup channel between the main and standby ACs is recommended to be connected separately to ensure its high reliability
- B . The HSB backup combination backup service is independent of each other, and the HSB backup group can work normally without binding.
- C . Under VRRP hot standby, the active/standby status of the HSB backup channel follows the changes in the active/standby status of VRRP
- D . Under dual-link hot backup, HSB channels have no active/standby status, only data backup channels
Regarding the MAP in the Mesh network, what is wrong in the following description?
- A . MAP is a special form of MP
- B . MAP is a special form of MPP
- C . MAP is usually used to connect to the terminal
- D . Any Mesh Point that supports AP function can provide access function for STA
When the user uses the WPA2-802.1x security policy and the STA supports fast roaming technology, the user does not need to re-complete the 802.1x authentication process during the roaming process, but only needs to complete the key negotiation process.
- A . True
- B . False
The following is the configuration when configuring the AC6005 to connect to the Portal server. What port does port 50200 refer to?
Web-auth-server huawei
Server-ip 10.254.1.100
Port 50200
Shared-key ciper huawei url-template huawei
- A . The destination port number used when actively sending messages to the Portal server
- B . Port number for processing Portal protocol packets on the device
- C . The source port number used when actively sending messages to the Portal server
- D . Port number for receiving Portal protocol packets on the device
Which of the following statement about neighbor active detection is wrong?
- A . The AP periodically sends Probe Request frames with specified multicast addresses on different channels, and the surrounding APs perceive that the AP is a neighbor AP after receiving it.
- B . Active detection is mainly used to establish neighbor relationships between legitimate APs
- C . Active detection is mainly used to obtain the maximum interference signal strength between legal neighbors, the most important of which is the signal strength of neighbor APs
- D . Both active detection and passive detection are used to collect interference from illegal Aps
When the WLAN network supports inter-AC roaming, multiple ACs will establish a full connection through the inter-AC tunnel. To ensure that users roaming to other ACs at Layer 3 can still receive broadcast messages in the original subnet, and simply broadcast the broadcast messages to other ACs through the roaming tunnel, a broadcast loop may be formed.
- A . True
- B . False
Which of the following commands is not necessary to configure the Mesh whitelist?
- A . radio radio-id
- B . ap-system-profile
- C . mesh-whitelist-profile
- D . peer-ap mac
What does the OU in the directory server stand for?
- A . User
- B . User Group
- C . Organizational unit
- D . Domain
Regarding the default configuration of common parameters of dual-link cold backup, which of the following statements is correct?
- A . AC global priority is 0
- B . AC personality priority is 0
- C . The dual-link backup and switchback function is not enabled
- D . Dual link backup function is enabled
The "5W" in "5W1H" in the Agile Controller function introduction refers to:
Who has access to the network?
Where to access the network from?
When is the access time?
Why connect?
What equipment is connected?
- A . True
- B . False
In the Agile Controller admission control scenario, the description of the role of the RADIUS server/client, which is correct?
- A . Agile Controller integrates all functions of RADIUS server and client
- B . The Agile Controller acts as a RADIUS server, and the user terminal acts as a RADIUS client
- C . The authentication device (such as an 802.1x switch) acts as a RADIUS server, and the user terminal acts as a RADIUS client
- D . The Agile Controller acts as a RADIUS server, and the authentication device is a RADIUS client
The illegal device prevention function refers to the configuration of the blacklist function based on illegal devices to restrict AP or Client access.
- A . True
- B . False
Which of the following servers is a directory server?
- A . Radius server
- B . AD server
- C . DNS server
- D . Portal server
In the WLAN network environment using the Agile Controller, which of the following are not part of the 802.1x authentication troubleshooting process steps?
- A . Check whether the number of online users reaches the maximum
- B . Check whether the AAA configuration of the device is correct
- C . Check if the 802.1x configuration is correct
- D . Check whether the web authentication configuration is correct
The AP will periodically send Discovery Request messages to detect the status of the original main link. When the link is restored, the AP detects that the priority of the link is higher than the priority of the main link currently in use and triggers a fallback. In order to avoid frequent switching caused by network shocks, after waiting for 6 Echo cycles, the AC is notified to perform active and standby simultaneous switching, and at the same time, the AP sends the STA’s data service to the newly upgraded AC.
- A . True
- B . False
Which of the following commands can be used to view the role of Mesh?
- A . display wlan mes route
- B . display ap-system-profile
- C . display mesh-profile
- D . display mesh vap
There are a large number of employees in an enterprise building, and they usually start to access the company’s WLAN network in the lobby when they go to work. As each employee walks to their respective working location, each person’s mobile terminal also roams Roam to their respective network coverage areas.
In order to ensure that the IP address of each terminal is fixed as much as possible, what is the recommended approach?
- A . Configure VLAN Pool and configure Hash algorithm
- B . Configure VLAN Pool and configure sequential algorithm
- C . Configure VLAN Pool, configure any algorithm
- D . Without configuring VLAN Pool, configure a static IP address for each mobile terminal
Intelligent roaming, that is, the user associates with a new AP from the original associated AP. This process is initiated by the user.
- A . True
- B . False
In the wireless admission control scenario, which of the following methods is recommended to distinguish between internal employees and external visitors?
- A . According to different user names
- B . According to whether the wireless terminal MAC address is registered or not
- C . Set different SSID for employees and visitors
- D . According to the type of wireless terminal
Which statement about N+1 backup is correct?
- A . The model and software version of the active and standby ACs must be exactly the same
- B . The main and standby AC product forms can be different, only need to ensure that the AC software version is consistent
- C . One backup AC can provide backup services for multiple main ACs, reducing the cost of purchasing equipment, and the reliability is higher than VRRP hot backup
- D . N+1 backup is cold backup. AP information and STA information are backed up
A company has deployed a WLAN network, and WLAN services have been carried on the AP. The company now needs to upgrade the AP version. In order to minimize the impact on users, which of the following upgrade methods is recommended?
- A . Automatically upgrade AP
- B . Upgrade AP online
- C . Upgrade AP through AP’s web network management
- D . Upgrade AP through AP Boot
In order not to change the existing wired network, an enterprise decided to adopt the bypass AC networking method when choosing the WLAN networking method. Considering that the current WLAN user data traffic is large, and there will be AC expansion requirements in the future, it is recommended to use tunnel forwarding when configuring WLAN services.
- A . True
- B . False
The two frequency bands of the AP that implement the spectrum navigation function must use the same SSID and security strategy.
- A . True
- B . False
Which of the following statements about WLAN hot backup is wrong?
- A . When configuring VRRP hot backup, you can determine the priority of the AC device by configuring the priority of VRRP
- B . To configure VRRP hot standby, the active and standby AC must be on the same Layer 2 network
- C . In dual-link hot standby, the active and standby AC can be in different Layer 2 networks and can be backed up through Layer 3 intercommunication.
- D . In dual-link hot backup, the priority of the active and standby AC can be configured to be the same to achieve backup in load sharing mode
General antennas are reversible, that is, the same antenna can be used as a transmitting antenna or a receiving antenna. The basic characteristic parameters of the same antenna as transmitting or receiving are the same.
- A . TRUE
- B . FALSE
Regarding the NAC statement, which is wrong in the following description?
- A . NAC (Network Admission Control) is called Network Admission Control
- B . NAC is an end-to-end security structure, including 802.1x, MAC and Portal authentication
- C . NAC access terminal equipment, if Portal authentication is used, client software needs to be installed
- D . NAC’s access terminal adopts 802.1x authentication, you need to install client software
Regarding AD server and LDAP server, which of the following descriptions is wrong?
- A . AD is a dedicated directory server for Windows Server
- B . LDAP can be installed on Windows Server
- C . The directory service protocol used by the AD server is the AD protocol
- D . The directory service protocol used by the AD server is the LDAP protocol