Exhibit.
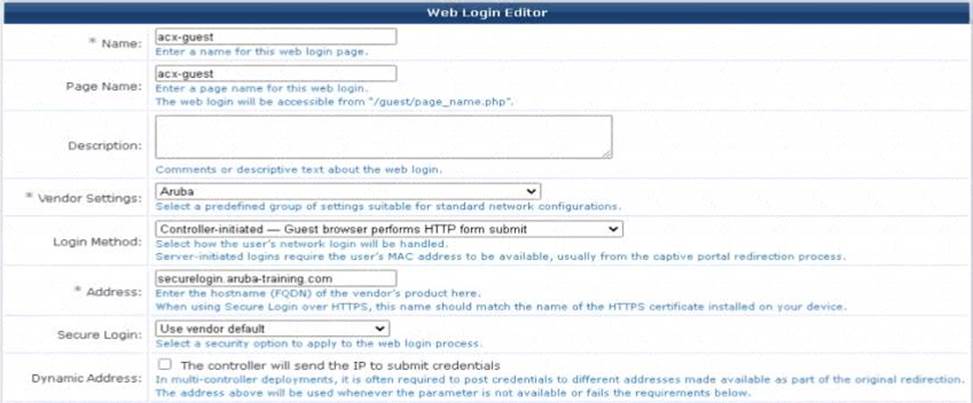
Which would explain this issue?
- A . HTTPS wildcard certificates are not supported
- B . HTTPS certificate is not required in ClearPass Guest.
- C . captiveportal-login aruba-training com needs to be entered m the Address field for the ClearPass Guest
- D . ".aruba-training com needs to be entered in the Address field for the ClearPass Guest
D
Explanation:
The correct address for the ClearPass Guest should match the FQDN of the HTTPS certificate installed on the device, which is often the FQDN of the vendor’s product. This ensures secureand proper redirection to the captive portal during the authentication process. The FQDN should be entered in the Address field for ClearPass Guest configuration.
A customer is evaluating device profiles on a CX 6300 switch.
The test device has the following attributes:
• MAC address = 81:cd:93:13:ab:31
• LLDP sys-desc = iotcontroller
The test device is being assigned to the ‘’lot-dev’’ role However, the customer requires the "lot-prod’’ role be applied.
Given the configuration, what is causing the "iot-dev" role to be applied to the device’?
- A . The test device does not support CDP.
- B . The device-profile precedence order is not configured.
- C . An external RADIUS server is unreachable.
- D . The LLDP system description matches the IIdp-group configuration.
D
Explanation:
In device profile configuration, the device role is often determined by matching attributes such as MAC address, LLDP system description, and CDP information against defined conditions. The test device is being assigned the "iot-dev" role because its LLDP system description matches the ‘iot-lldp’ group configuration that is associated with the ‘iot-dev’ role.
You configured" a bridgedmode SSID with WPA3-Enterprise and EAP-TLS security. When you connect an Active Directory joined client that has valid client certificates.
ClearPass shows the following error.
What is needed to resolve this issue?
- A . Enable authorization in your Authentication Method.
- B . Recreate the SSID m tunneled mode.
- C . Modify your ACX-AD authentication source to include the UPN in the search.
- D . Configure ClearPass to trust the client certificate.
C
Explanation:
The error message "User not found" indicates that the authentication source, in this case, Active Directory (AD), is not able to locate the user account based on the current search parameters. This often occurs when the User Principal Name (UPN) that the client is using to authenticate is not included in the search parameters of the AD authentication source within ClearPass. By modifying the AD authentication source to include the UPN in the search, ClearPass will be able to correctly locate the user account and proceed with the authentication using the valid client certificates.
Exhibit.
An engineer has applied the above configuration to R1 and R2 However the routers OSPF adjacency never progresses past the "EXSTART-DR" slate as shown below.
Which configuration action on either router will allow R1 and R2 to progress past the "EXSTART/DR" state?
- A . Change R1 and R2 to a network type of point-to-point.
- B . Remove the layer 3 MTU configuration.
- C . Ensure the OSPF process is not configured with passive-interface default.
- D . Change the IP address and mask applied to interface 1/1/1.
A
Explanation:
In OSPF, the "EXSTART/DR" state indicates that the routers are trying to establish an adjacency but are unable to progress. This can happen if the OSPF network type is incorrectly configured for the type of connection between the routers. Given that R1 and R2 are connected via a point-to-point link (as suggested by the /31 subnet), setting the network type to point-to-point on both routers will remove the need for DR/BDR election, which is unnecessary on a point-to-point link, and allow OSPF to progress past the "EXSTART" state and form a full adjacency.
Exhibit.
Which statement is true?
- A . The SSID supports HR-DSSS data rates
- B . The SSID is supports 6 GHz clients.
- C . The SSID supports 802 11ax clients.
- D . The SSID supports 802 11ac clients.
C
Explanation:
The exhibit shows that the SSID supports 802.11ax clients, which is indicated by the presence of HT (High Throughput) information, VHT (Very High Throughput) capabilities, and HE (High-Efficiency) operation, which are all features associated with 802.11ax, also known as Wi-Fi 6.
You are deploying a new AOS 10 mobility gateway cluster. Due to customer requirements, the gateways must be configured with static IP addresses and are restricted from communicating using port 443 to any URLs except tor "central arubanetworks.com
How would you onboard these gateways successfully into HPE Aruba Networking Central?
A)
B)
C)
D)
- A . Option A
- B . Option B
- C . Option C
- D . Option D
A
Explanation:
Option A includes all necessary steps for a full setup of an AOS 10 mobility gateway cluster, including setting the system name, switch role, ACP FQDN address, uplink port information, IP address and default gateway, DNS IP address, controller country code, timezone and clock, andadmin password. Since the gateways must have static IP addresses and can only communicate on port 443 for a specific URL, this configuration would need to allow for static IP configuration and restrict communication to the required URL.
You configured a tunneled SSID with captive portal and a ClearPass Guest Self Registration workflow when testing and launching the self-registration workflow, after successful registration, the login action shows the following error:
What is the best solution to resolve this error?
- A . You need to include the root and intermediate certificates in the captive portal certificate for your access points
- B . You need to De connected to the guest SSiD while testing.
- C . You need to change the Login Address in ClearPass to securelogin arubanetworKs.com
- D . You need to include the root and intermediate certificates in the captive portal certificate for your gateway
D
Explanation:
Including the root and intermediate certificates in the captive portal certificate for the gateway will resolve the error seen during the login action after successful registration. This is necessary to ensure the SSL/TLS handshake can be completed successfully, as the client browser needs to validate the entire certificate chain.
What directly affects the MCS used by wireless stations? (Select two.)
- A . SNR
- B . retry rate
- C . channel utilization
- D . number of connected clients
- E . frequency band
A E
Explanation:
The Modulation and Coding Scheme (MCS) used by wireless stations is directly affected by the signal-to-noise ratio (SNR) and the frequency band. Higher SNR can lead to higher MCS values, which means better data rates. The frequency band can affect MCS due to different channel characteristics, such as the presence of interference and propagation properties, which are factors in determining data rates.
Which command would allow you to verity receipt of a CoA message on an AOS 10 GW?
- A . packet-capture datapath udp 3799
- B . packet-capture controipath udp 3799
- C . packet-capture interprocess udp 3799
- D . tcpdump host-port 3799
B
Explanation:
The Change of Authorization (CoA) messages are used in network access control scenarios and are typically received by the network access server, in this case, an Aruba AOS 10 Gateway. The correct command to verify the receipt of a CoA message is related to the control path traffic because CoA is a control plane function.
Option B, packet-capture controlpath udp 3799, is the correct answer because it specifies capturing control plane traffic on UDP port 3799, which is the standard port for CoA messages.
Options A, C, and D are incorrect because:
Option A captures data plane traffic, not control plane traffic.
Option C’ spacket-capture interprocess udp 3799does not refer to a standard command for capturing CoA messages.
Option D, tcpdump host-port 3799, does not specify the correct syntax for capturing traffic on Aruba devices.
You created a new SSID with the security settings shown in the exhibit.
Some, but not all users complain that client devices are unable to connect to this SS1D.
What is the reason for this?
- A . The WPA3 Enterprise GCM-2S6 mode does not support transition mode.
- B . WPA3 Enterprise is not backward compatible with WPA2 Enterprise.
- C . MAC authentication after a failed 802. ix authentication is not possible as the option "MAC Authentication Fall-Through" is disabled.
- D . The primary servers shared key differs from the shared key configured for this server on HPE Aruba Networking Central.
C
Explanation:
If some users are unable to connect to an SSID configured with WPA3-Enterprise GCM-256, and the "MAC Authentication Fall-Through" is disabled, it means that devices which fail 802.1X authentication will not attempt MAC authentication. If these client devices are configured to use MAC authentication as a backup method, they will fail to connect, explaining the issue faced by some users.
Exhibit.
Which statement is true given the following CLI output from a CX 6300?
- A . There are no active fabric clients on the CX switch with RD 172.16.10.1
- B . A wired client with IP address 10.203 1.100 is on a remote CX 6300 in the fabric with loopback IP address 172.21.11.2.
- C . A wired client with IP address 10 203 1 100 has a host route that is not being properly advertised
- D . The overlay loopbacK addresses are advertised in the faerie with 2d-bit subnet masks
B
Explanation:
The CLI output provided shows routing information from a CX 6300 switch. The output under "VRF: default" shows various IP routes, including a route for 10.203.1.100/32 with a next hop of 172.21.11.2. This indicates that the route to the client with IP address 10.203.1.100 is known in the network and is reachable via another device in the fabric, which has the loopback IP address 172.21.11.2. Since the route is present in the routing table, it means that the client is known and active within the fabric network.
Your customer asked for help to apply an ACL for wireless guest users with the following criteria:
• Wi-Fi guests are on VLAN 555
• allow internet access
• only allow access to public DNS servers
• deny access to all internal networks except for any DHCP server
These session ACLs are already present in the CLI of the mobility gateway group:
You have access to the CLl.
Which user role meets all the criteria?
A)
B)
C)
D)
- A . Option A
- B . Option B
- C . Option C
- D . Option D
A
Explanation:
Based on the criteria provided for wireless guest users, the correct user role configuration must allow internet access, only allow access to public DNS servers, deny access to all internal networks except for any DHCP server, and place the Wi-Fi guests on VLAN 555. The ACLs must permit services necessary for basic internet access (such as DNS and DHCP) and block access to internal networks.
Option A satisfies these criteria with the following configurations:
user-role "WiFi-guest":
This defines the role for Wi-Fi guests.
access-list session dhcp-acl: This applies the access list that likely permits DHCP, which is necessary for guests to obtain an IP address.
access-list session dns-acl: This applies the DNS access list, which likely restricts guests to using public DNS servers.
access-list session internal-networks: This applies the internal networks access list, which denies access to internal networks.
vlan 555: This sets the VLAN for Wi-Fi guests to 555.
Options B, C, and D are incorrect because they includeaccess-list session allowallwhich would permit all traffic, contradicting the requirement to deny access to all internal networks.
Refer to the CLI output below:
What statement about the output above is correct?
- A . The port-access role was configured with gateway-role visitor
- B . The secondary tunnel endpoint IP is 10.10-10.151.
- C . The client authenticated using dot1x.
- D . The UBT zone was configured to use a user-defined VRF
B
Explanation:
The CLI output indicates a tunnel creation process, where "SW hw tun created" refers to the switch hardware tunnel being created. The line mentioning "BYP-10.10.10.101 -> SW hw tun created to 10.10.10.151 tunnel 15." implies that a tunnel was established to the secondary tunnel endpoint with the IP address 10.10.10.151. This is a common configuration for User-Based Tunneling (UBT) setups where traffic is tunneled to a specific endpoint.
A Windows device attempts to connect to an 802.1X network but it is not receiving the correct role. TEAP has been configured asthe only authentication method in ClearPass.
The wireless configuration is correct.
Exhibit.
What is me mostlikelycause?
- A . The Windows device needs 10 De configured tor TEAP.
- B . ClearPass requires a second authentication method.
- C . 802.1X is not compatible with TEAP in windows device
- D . Only machine authentication should be configured on the Windows device
A
Explanation:
The issue likely stems from the Windows device not being configured to use TEAP (Tunneled Extensible Authentication Protocol) as specified in the ClearPass configuration. TEAP is an EAP method that encapsulates an inner EAP method for secure authentication. The Windows device must have TEAP enabled and correctly configured in its network settings to authenticate successfully on the network using ClearPass.
Exhibit.
Which user role will be assigned when a voice client tries to connect for the first time, but the RADIUS server is unavailable?
- A . CRITICAl_AUTH
- B . DEFAULT_AUTH
- C . CRIT1CAL_V0ICE
- D . PRE_AUTH
C
Explanation:
In the provided configuration for interface 1/1/7, there are roles specified for different scenarios concerning authentication. When a voice client attempts to connect and the RADIUS server is unreachable, the role that is assigned is the one specified as the "critical-voice-role". In this case, the "CRITICAL_VOICE" role is configured to be assigned under such circumstances, ensuring that voice clients receive appropriate network access permissions even when the RADIUS server is not available to authenticate them.
A customer is evaluating device profiles on a CX 6300 switch.
The test device has the following attribute:
• MAC address=81:cd:93:13:ab:31
The test device needs to be assigned the "lot-prod” role, in addition the "lot-default" role must be applied for any other device connected lo interface 1/1/1. This is a lab environment with no configuration of any external authentication server for the test.
Given the configuration example, what is required to meet this testing requirement?
- A . Enter the command "pot-access device-profile mode block-until-profile-applied"" for interface 1/1/1.
- B . Enter the command "port-access fallback-role lot-default globally
- C . Enter the command "port-access onboarding-method precedence" to set device profiles with a lower precedence.
- D . Enter the command "port-access device-profile mode block-until-profile-applied" globally.
B
Explanation:
The fallback role is used as a default role in the absence of a specified role or when an authentication server is not available. Given the scenario, where the test device with MAC address 81:cd:93:13:ab:31 needs to be assigned to "iot-prod" and other devices to "iot-default", and considering there is no external authentication server configured for the test, the appropriate action would be to set a global fallback role that applies to all devices connecting to the network. This ensures that any device that does not match the specific device profile will inherit the "iot-default" role. Since the configuration for a specific MAC address (81:cd:93:xx:xx:xx) to associate with the "iot-prod" role is already in place, setting the fallback role globally accommodates the requirement for other devices.
What is me recommended configuration to ensure link aggregation is consistent in a campus topology using VSX with two aggregation switches and downlinks to access switches?
- A . Use a custom LACP hash algorithm for improved load Balancing.
- B . Keep the MTU values at the default setting for GRE and VXLAN communications
- C . Use the command "vsx-sync mclag-interfaces" under the VSX context.
- D . Use the command "vsx-sync active-gateways" under the VSX context.
C
Explanation:
When configuring Virtual Switching Extension (VSX) in a campus topology for link aggregation across two aggregation switches, it is important to synchronize Multi-Chassis Link Aggregation Group (MC-LAG) interfaces. The command "vsx-sync mclag-interfaces" ensures that the state and configuration of MC-LAG interfaces are synchronized between the two VSX-linked switches,providing consistent link aggregation and preventing any loops or mismatched configurations that might occur if the interfaces were not in sync.
A customer has interfering devices that are seen over the air. They contact you and ask you to configure RAPIDS to help identify interfering and rogue APs. HPE Aruba Networking Central identifies a rogue AP and displays the connected switch port.
How can HPE Aruba Networking Central identify which switch port the AP is connected to?
- A . device profiting on the switch
- B . from the AP MAC address table
- C . from the switch LLDP neighbors table
- D . from the switch MAC address table
D
Explanation:
HPE Aruba Networking Central can identify which switch port a rogue AP is connected to by using the switch’s MAC address table. The MAC address table contains the associations between MAC addresses and the switch ports to which devices (including APs) are connected. When Aruba Central detects a rogue AP, it can look up the MAC address of the rogue AP in the switch’s MAC address table to find the specific switch port it is connected to. This enables network administrators to quickly locate and address the rogue AP issue.
A deployment using AP-635S is connected to a stack of CX 6300s as shown.
The output of the snow LACPinterfaces shews the following:
What is causing this issue?
- A . e0 is connected to a smart rate interface, and e1 is connected to a non-smart rate interface.
- B . Spanning tree and loop protect are enabled on both AP uplink ports.
- C . Each AP interface is connected to a routed-only interlace on different networks
- D . The AP is configured with LACP active
D
Explanation:
In an Aruba deployment, if an AP’s interfaces show different LACP states, it often indicates a configuration mismatch. If one interface is up and the other is blocked as shown in the output, it’s likely due to both interfaces on the AP being set to LACP active mode, which is a correct setting for establishing an LACP channel with Aruba switches like the CX 6300 series.
Exhibit.
A network administrator attempts to improve multicast traffic flow and performs some packet captures for validation.
What can the network administrator conclude from the results?
- A . The data rate increased from 6 Mops to 300 Mops because Broadcast Multicast optimization (BCMCO) was configured.
- B . The capture taken after optimization does not show a packet length because Multicast Transmission Optimization was configured.
- C . The type flew remains consistent because Dynamic Multicast Optimization (DMO) was configured.
- D . The data rate increased from 6 Mbps to 300 Mops because Dynamic Multicast Optimization (DMO) was configured.
D
Explanation:
Dynamic Multicast Optimization (DMO) is a feature that enhances the delivery of multicast traffic by optimizing the data rate. The before and after optimization images show a significant increase in the data rate, which is a typical result of DMO being configured, as it allows multicast traffic to be transmitted at higher data rates by converting multicast streams into unicast streams for the clients that need them.
You configured a WPA3-SAE with the following MAC Authentication Role Mapping inCloud Authentication and Policy:
With further default settings assume a new Android phone is connected to the network.
Which role will the client be assigned after connecting forthe first time?
- A . byod
- B . client will be rejected network access
- C . lot-local
- D . unmatched-device
D
Explanation:
The configuration shown in the third exhibit details a client role mapping that associates different client profile tags with specific client roles. When a new device, such as an Android phone, connects to the network, it will be profiled and assigned a role based on the mappings defined. If the device does not match any predefined profiles, it would be assigned the "unmatched-device" role. This is under the assumption that default settings are in place and the client does not match the criteria for any of the specific roles like "byod", "iot-internet", or "iot-local". Therefore, an Android phone connecting for the first time and not matching any specific profile tag would be assigned to the "unmatched-device" role.
Exhibit.
You updated your gateway to me most recent firmware However after the firmware was updated, the gateway could no longer connect to HPE Aruba Networking Central. Your corporate ITIL procedures require you to implement your backout plan. You connected a console cable to your gateway and saw the following prompt.
Cpxload#
in what order, do you need to execute the following commands to return to the previous firmware version?
Explanation:
The sequence to return to the previous firmware version after an unsuccessful update would typically be:
hit any key to stop autoboot (This would prevent the system from automatically booting into the current, problematic firmware.)
def_part 1 (This command sets the default boot partition, which is likely where the previous working firmware is located.)
bootf (This command would boot from the specified flash partition, which after the second step, would be the previous firmware.)
osinfo (After the system is booted, this command could be used to confirm the firmware version now running on the gateway.)
Your customer is requesting a4-ciass LAN queuing model tor QoS. Following best practices, match the PHB/DSCP values to the application types.
Explanation:
Best Effort and Scavenger =DF (0)
Bulk and Transactional Data =AF21 (18)
Multimedia Streaming =AF31 (26)
Real-Time Interactive =EF (46)
After onboarding three new AOS 10 gateways using the full-setup methodinto the same Central group, a customer cannot log in to one of the gateways using the HPE Aruba Networking Central remote console due to an incorrect password.
- A . The admin password created using full-setup does not match the global Central admin password.
- B . The admin password created during the run-setup process is not configured to allow me remote console access
- C . The admin password created during the full-setup process does not match the Central group admin password
- D . The admin password created at the Central group level has expired
C
Explanation:
When onboarding devices into a centralized management system, each device can have its individual admin password set during the onboarding process. If this password doesn’t match what is expected at the group level in the central management platform, login issues such as the one described can occur.
A customer is deploying a new warehouse with AP-634 APs inthe unitedStates with mobile devices that can operate in the 6GHz spectrum All testing and RF analyses were performed during the POC using AP-635 APs In a different location During the deployment, they noticed fewer 6GHz channels were broadcasting in the air.
Why would the AP-634 deployment have a lesser amount of broadcasting channels?
- A . The AP-634 APs do not have an advanced subscription.
- B . The AP-634 APs cannot broadcast an 6Gnz channels due to regulatory restrictions.
- C . The AP-635 APs received different allowable 6GHz channels from the AFC service versus the AP-634 APs due to the POC running in a different location.
- D . The AP-634 AP’s persona was configured in the Central group as Standard Power.
C
Explanation:
In the United States, the operation in the 6GHz band for Wi-Fi devices such as the AP-634 and AP-635 is regulated by the Automated Frequency Coordination (AFC) system, which determines the channels that can be used based on the location. Since the Proof of Concept (POC) was conducted in a different location using AP-635 APs, the allowable channels identified by the AFC service for that location would be different than the channels allowed for the actual deployment location of the AP-634 APs. This would result in a different set of broadcasting channels being available for use in the new warehouse deployment.