Refer to the exhibit.
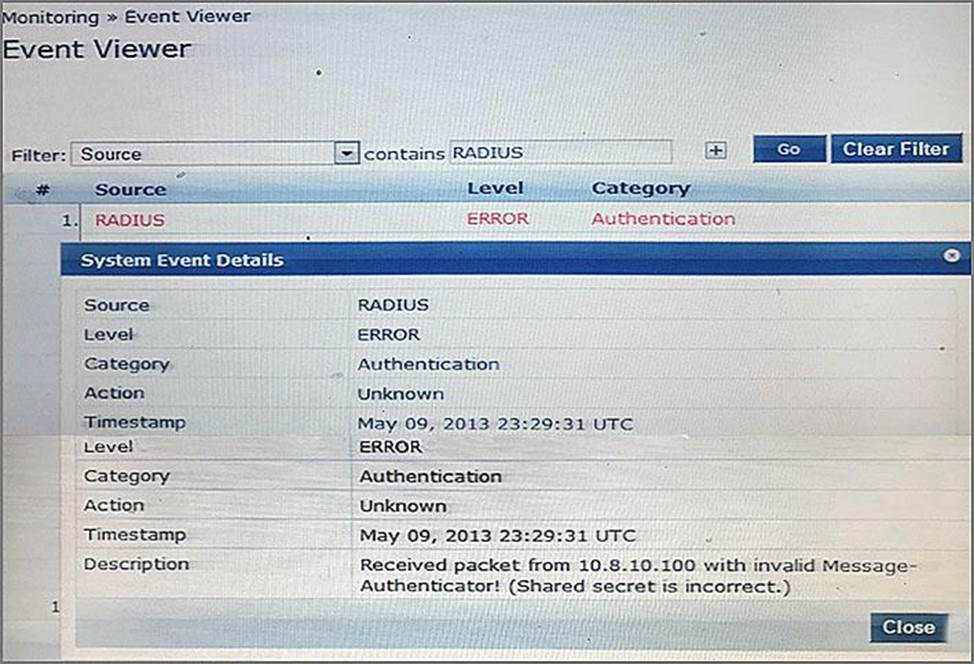
The ClearPass Event Viewer displays an error when a user authenticates with EAP-TLS to ClearPass through an Aruba Controller Wireless Network.
What is the cause of this error?
- A . The controller’s shared secret used during the certificate exchange is incorrect.
- B . The NAS source interface IP is incorrect.
- C . The client sent an incorrect shared secret for the 802.1X authentication.
- D . The controller used an incorrect shared secret for the RADIUS authentication.
- E . The client’s shared secret used during the certificate exchange is incorrect.
Which licenses are included in the built-in Starter kit for ClearPass?
- A . 10 ClearPass Guest licenses, 10 ClearPass Onguard licenses and 10 ClearPass Onboard licenses
- B . 25 ClearPass Profiler licenses
- C . 25 ClearPass Enterprise licenses
- D . 10 ClearPass Enterprise licenses
- E . 25 ClearPass Redundancy licenses
C
Explanation:
All CPPM’s comes bundled with 25 Enterprise application licenses so you can test the functionality of the Applications as this license can be used for any of them.
References: http://community.arubanetworks.com/t5/Security/ClearPass-licensing-explained-August-MHC/td-p/195719
Which statement accurately describes configuration of Data and Management ports on the ClearPass appliance? (Select two.)
- A . Static IP addresses are only allowed on the management port.
- B . Configuration of the data port is mandatory.
- C . Configuration on the management port is mandatory.
- D . Configuration of the data port if optional.
- E . Configuration of the management port is optional.
C,D
Explanation:
The Management port (ethernet 0) provides access for cluster administration and appliance maintenance using the WebUI, CLI, or internal cluster communication. This configuration is mandatory.
The configuration of the data port is optional. If this port is not configured, requests are redirected to the Management port.
References: http://www.arubanetworks.com/techdocs/ClearPass/Aruba_DeployGd_HTML/Content/1%20About%20ClearPass/Hardware_Appliance.htm
An employee provisions a personal smart phone using the Onboard process. In addition, the employee has a corporate laptop provided by IT that connects to the secure network.
How many licenses does the employee consume?
- A . 1 Policy Manager license, 2 Guest Licenses
- B . 2 Policy Manager licenses, 1 Onboard License
- C . 1 Policy Manager license, 1 Onboard License
- D . 1 Policy Manager license, 1 Guest License
- E . 2 Policy Manager licenses, 2 Onboard Licenses
Refer to the exhibit.
An Enforcement Profile has been created in the Policy Manager as shown.
Which action will ClearPass take based on this Enforcement Profile?
- A . ClearPass will count down 600 seconds and send a RADIUS CoA message to the user to end the user’s session after this time is up.
- B . ClearPass will send the Session-Timeout attribute in the RADIUS Access-Accept packet to the NAD and the NAD will end the user’s session after 600 seconds.
- C . ClearPass will count down 600 seconds and send a RADIUS CoA message to the NAD to end the user’s session after this time is up.
- D . ClearPass will send the Session-Timeout attribute in the RADIUS Access-Request packet to the NAD and the NAD will end the user’s session after 600 seconds.
- E . ClearPass will send the Session-Timeout attribute in the RADIUS Access-Accept packet to the User and the user’s session will be terminated after 600 seconds.
E
Explanation:
Session Timeout (in seconds) – Configure the agent session timeout interval to re-evaluate the system health again. OnGuard triggers auto-remediation using this value to enable or disable AV-RTP status check on endpoint. Agent re-authentication is determined based on session-time out value. You can specify the session timeout interval from 60 C 600 seconds. Setting the lower value for session timeout interval results numerous authentication requests in Access Tracker page. The default value is 0.
References: http://www.arubanetworks.com/techdocs/ClearPass/Aruba_CPPMOnlineHelp/Content/CPPM_UserGuide/Enforce/EPAgent_Enforcement.htm
Which devices support Apple over-the-air provisioning? (Select two.)
- A . IOS 5
- B . Laptop running Mac OS X 10.8
- C . Laptop running Mac OS X 10.6
- D . Android 2.2
- E . Windows XP
A,B
Explanation:
Apple over-the-air provisioning is supported by IOS and OSX above version 10.6.
References: https://community.arubanetworks.com/aruba/attachments/aruba/tkb@tkb/286/1/BYODwithClearPass_Cameron_Esdaile.pdf
DRAG DROP
Use the arrows to sort the steps to request a Policy Service on the left into the order they are performed on the right.
Which device type supports Exchange ActiveSync configuration with Onboard?
- A . Linux laptop
- B . Mac OS X device
- C . Apple iOS device
- D . Windows laptop
- E . Android device
C
Explanation:
Exchange ActiveSync configurations you define can be used in configuration profiles to automatically configure an email account on an iOS device.
References: http://www.arubanetworks.com/techdocs/ClearPass/6.6/Guest/Content/Onboard/CreateEdit
ActiveSync.htm
Refer to the exhibit.
An AD user’s department attribute is configured as “HR”. The user connects on Monday using an Android phone to an Aruba Controller that belongs to the Device Group Remote NAD.
Which roles are assigned to the user in ClearPass? (Select two.)
- A . Executive
- B . iOS Device
- C . Vendor
- D . Remote Employee
- E . HR Local
Refer to the exhibit.
What information can be drawn from the audit row detail shown? (Select two.)
- A . radius01 was deleted from the list of authentication sources.
- B . The policy service was moved to position number 4.
- C . radius01 was moved to position number 4.
- D . The policy service was moved to position number 3.
- E . raduis01 was added as an authentication source.
Refer to the exhibit.
Based on the Posture Policy configuration shown, above, which statement is true?
- A . This Posture Policy can only be applied to an 802.1x wired service not 802.1x wireless.
- B . This Posture Policy checks the health status of devices running Windows, Linux and Mac OS X.
- C . This Posture Policy can use either the persistent or dissolvable Onguard agent to obtain the statement of health.
- D . This Posture Policy checks for presence of a firewall application in Windows devices.
- E . This Posture Policy checks with a Windows NPS server for posture tokens.
Refer to the exhibit.
Which types of records will the report shown display?
- A . all RADIUS authentications from the 10.8.10.100 NAD to ClearPass
- B . all failed RADIUS authentications through ClearPass
- C . only Windows devices that have authenticated through the 10.8.10.100 NAD
- D . all successful RADIUS authentications through ClearPass
- E . all successful RADIUS authentications from the 10.8.10.100 NAD to ClearPass
Refer to the exhibit.
An administrator logs in to the Guest module in ClearPass and ‘Manage Accounts’ displays as shown.
When a user with username donald@disney.com attempts to access the Web Login page, what will be the outcome?
- A . The user will be able to log in and authenticate successfully but will then be immediate disconnected.
- B . The user will be able to log in for the next 4.9. days, but then will no longer be able to log in.
- C . The user will not be able to log in and authenticate.
- D . The user will be able to log in and authenticate successfully, but will then get a quarantine role.
- E . The user will not be able to access the Web Login page.
What is the purpose of the Audit Viewer in the Monitoring section of ClearPass Policy Manager?
- A . to audit client authentications
- B . to display changes made to the ClearPass configuration
- C . to display the entire configuration of the ClearPass Policy Manager
- D . to audit the network for PCI compliance
- E . to display system events like high CPU usage.
A university wants to deploy ClearPass with the Guest module. The university has two types that need to use web login authentication. The first type of users are students whose accounts are in an Active Directory server. The second type of users are friends of students who need to self-register to access the network.
How should the service be set up in the Policy Manager for this network?
- A . Guest User Repository and Active Directory server both as authentication sources
- B . Active Directory server as the authentication source, and Guest User Repository as the authorization source
- C . Guest User Repository as the authentication source, and Guest User Repository and Active Directory server as authorization sources
- D . Either the Guest User Repository or Active Directory server should be the single authentication source
- E . Guest User Repository as the authentication source and the Active Directory server as the authorization source
ClearPass and a wired switch are configured for 802.1x authentication with RADIUS CoA (RFC 3576) on UDP port 3799. This port has been blocked by a firewall between the wired switch and ClearPass.
What will be the outcome of this state?
- A . RADIUS Authentications will fail because the wired switch will not be able to reach the ClearPass server.
- B . During RADIUS Authentication, certificate exchange between the wired switch and ClearPass will fail.
- C . RADIUS Authentications will timeout because the wired switch will not be able to reach the ClearPass server.
- D . RADIUS Authentication will succeed, but Post-Authentication Disconnect-Requests from ClearPass to the wired switch will not be delivered.
- E . RADIUS Authentication will succeed, but RADIUS Access-Accept messages from ClearPass to the wired switch for Change of Role will not be delivered.
A customer wants to implement Virtual IP redundancy, such that in case of a ClearPass server outage, 802.1x authentications will not be interrupted. The administrator has enabled a single Virtual IP address on two ClearPass servers.
Which statements accurately describe next steps? (Select two.)
- A . The NAD should be configured with the primary node IP address for RADIUS authentication on the 802.1x network.
- B . A new Virtual IP address should be created for each NAD.
- C . Both the primary and secondary nodes will respond to authentication requests sent to the Virtual IP address when the primary node is active.
- D . The primary node will respond to authentication requests sent to the Virtual IP address when the primary node is active.
- E . The NAD should be configured with the Virtual IP address for RADIUS authentications on the 802.1x network.
D,E
Explanation:
In an Aruba network, APs are controlled by a controller. The APs tunnel all data to the controller for processing, including encryption/decryption and bridging/forwarding data. Local controller redundancy provides APs with failover to a backup controller if a controller becomes unavailable. Local controller redundancy is provided by running VRRP between a pair of controllers. The APs are then configured to connect to the “virtual-IP” configured for the VRRP instance.
References: http://www.arubanetworks.com/techdocs/ArubaOS_64x_WebHelp/Content/ArubaFrameSty les/VRRP/Redundancy_Parameters.htm
What is a benefit of ClearPass Onguard?
- A . It enables organizations to run advanced endpoint posture assessments.
- B . It allows a receptionist in a hotel to create accounts for guest users.
- C . It allows employees to self-provision their personal devices on the corporate network.
- D . It offers an easy way for users to self-configure their devices to support 802.1X authentication on wired and wireless networks.
- E . It allows employees to create temporary accounts for Wi-Fi access.
Refer to the exhibit.
Based on the information shown, which field in the Captive Portal Authentication profile should be changed so that guest users are redirected to a page on ClearPass when they connect to the Guest SSID?
- A . both Login and Welcome Page
- B . Default Role
- C . Welcome Page
- D . Default Guest Role
- E . Login Page
E
Explanation:
The Login page is the URL of the page that appears for the user logon. This can be set to any URL.
The Welcome page is the URL of the page that appears after logon and before redirection to the web URL. This can be set to any URL.
References: http://www.arubanetworks.com/techdocs/ArubaOS_63_Web_Help/Content/ArubaFrameStyles/Captive_Portal/Captive_Portal_Authentic.htm
Refer to the exhibit.
Based on the guest Self-Registration with Sponsor Approval workflow shown, at which stage does the sponsor approve the user’s request?
- A . After the RADIUS Access-Request
- B . After the NAS login, but before the RADIUS Access-Request
- C . Before the user can submit the registration form
- D . After the RADIUS Access-Response
- E . After the receipt page is displayed, before the NAS login
Which types of files are stored in the Local Shared Folders database in ClearPass? (Select two.)
- A . Software image
- B . Backup files
- C . Log files
- D . Device fingerprint dictionaries
- E . Posture dictionaries
What are Operator Profiles used for?
- A . to enforce role based access control for Aruba Controllers
- B . to enforce role based access control for ClearPass Policy Manager admin users
- C . to enforce role based access control for ClearPass Guest Admin users
- D . to assign ClearPass roles to guest users
- E . to map AD attributes to admin privilege levels in ClearPass Guest
C
Explanation:
An operator profile determines what actions an operator is permitted to take when using ClearPass Guest.
References: http://www.arubanetworks.com/techdocs/ClearPass/CPGuest_UG_HTML_6.5/Content/OperatorLogins/OperatorProfiles.htm
Refer to the exhibit.
Based on the configuration of the create_user form shown, which statement accurately describes the status?
- A . The email field will be visible to guest users when they access the web login page.
- B . The visitor_company field will be visible to operators creating the account.
- C . The visitor_company field will be visible to the guest users when they access the web login page.
- D . The visitor_phone field will be visible to the guest users in the web login page.
- E . The visitor_phone field will be visible to operators creating the account.
A
Explanation:
References: https://community.arubanetworks.com/t5/AAA-NAC-Guest-Access-BYOD/expire-timezone-field-is-not-showing-up-on-the-create-user-form/ta-p/250230
Refer to the exhibit.
Based on the Enforcement Policy configuration shown, when a user with Role Engineer connects to the network and the posture token assigned is Unknown, which Enforcement Profile will be applied?
- A . EMPLOYEE_VLAN
- B . RestrictedACL
- C . Deny Access Profile
- D . HR VLAN
- E . Remote Employee ACL
Based on the Local User repository in ClearPass shown, which Aruba firewall role will be assigned to “mike” when this user authenticates Aruba Controller?
- A . We can’t know this from the screenshot above.
- B . mike
- C . Employee
- D . john
A customer would like to deploy ClearPass with these requirements:
✑ between 2000 to 3000 corporate users need to authenticate daily using EAP-TLS
✑ should allow for up to 1000 employee devices to be Onboarded
✑ should allow up to 100 guest users each day to authenticate using the web login feature
What is the license mix that customer will need to purchase?
- A . CP-HW-2k, 1000 Onboard, 100 Guest
- B . CP-HW-500, 1000 Onboard, 100 Guest
- C . CP-HW-5k, 2500 Enterprise
- D . CP-HW-5k, 1000 Enterprise
- E . CP-HW-5k, 100 Onboard, 100 Guest
What must be configured to enable RADIUS authentication with ClearPass on a network access device (NAD)? (Select two.)
- A . the ClearPass server must have the network device added as a valid NAD
- B . the ClearPass server certificate must be installed on the NAD
- C . a matching shared secret must be configured on both the ClearPass server and NAD
- D . an NTP server needs to be set up on the NAD
- E . a bind username and bind password must be provided
In which ways can ClearPass derive client roles during policy service processing? (Select two.)
- A . From the attributes configured in Active Directory
- B . From the server derivation rule in the Aruba Controller server group for the client
- C . From the Aruba Network Access Device
- D . From the attributes configured in a Network Access Device
- E . Through a role mapping policy
A hotel chain deployed ClearPass Guest. When hotel guests connect to the Guest SSID, launch a web browser and enter the address www.google.com, they are unable to immediately see the web login page.
What are the likely causes of this? (Select two.)
- A . The ClearPass server has a trusted server certificate issued by Verisign.
- B . The ClearPass server has an untrusted server certificate issued by the internal Microsoft Certificate server.
- C . The ClearPass server does not recognize the client’s certificate.
- D . The DNS server is not replying with an IP address for www.google.com.
B,D
Explanation:
You would need a publicly signed certificate.
References: http://community.arubanetworks.com/t5/Security/Clearpass-Guest-certificate-error-for-guest-visitors/td-p/221992
What is the purpose of ClearPass Onboard?
- A . to provide MAC authentication for devices that don’t support 802.1x
- B . to run health checks on end user devices
- C . to provision personal devices to securely connect to the network
- D . to configure self-registration pages for guest users
- E . to provide guest access for visitors to connect to the network
A customer with an Aruba Controller wants it to work with ClearPass Guest.
How should the customer configure ClearPass as an authentication server in the controller so that guests are able to authenticate successfully?
- A . Add ClearPass as a RADIUS CoA server.
- B . Add ClearPass as a RADIUS authentication server.
- C . Add ClearPass as a TACACS+ authentication server.
- D . Add ClearPass as an HTTPS authentication server.
B
Explanation:
A customer with an Aruba Controller wants it to work with ClearPass Guest.
How should the customer configure ClearPass as an authentication server in the controller so that guests are able to authenticate successfully?
- A . Add ClearPass as a RADIUS CoA server.
- B . Add ClearPass as a RADIUS authentication server.
- C . Add ClearPass as a TACACS+ authentication server.
- D . Add ClearPass as an HTTPS authentication server.
B
Explanation:
A customer with an Aruba Controller wants it to work with ClearPass Guest.
How should the customer configure ClearPass as an authentication server in the controller so that guests are able to authenticate successfully?
- A . Add ClearPass as a RADIUS CoA server.
- B . Add ClearPass as a RADIUS authentication server.
- C . Add ClearPass as a TACACS+ authentication server.
- D . Add ClearPass as an HTTPS authentication server.
B
Explanation:
Which statement is true? (Choose two.)
- A . Mobile device Management is the result of Onboarding.
- B . Third party Mobile Device Management solutions can be integrated with ClearPass.
- C . Mobile Device Management is the authentication that happens before Onboarding.
- D . Mobile Device Management is an application container that is used to provision work applications.
- E . Mobile Device Management is used to control device functions post-Onboarding.
Refer to the exhibit.
Based on the Authentication sources configuration shown, which statement accurately describes the outcome if the user is not found?
- A . If the user is not found in the remotelab AD but is present in the local user repository, a reject message is sent back to the NAD.
- B . If the user is not found in the local user repository but is present in the remotelab AD, a reject message is sent back to the NAD.
- C . If the user is not found in the local user repository a reject message is sent back to the NAD.
- D . If the user is not found in the local user repository and remotelab AD, a reject message is sent back to the NAD.
- E . If the user is not found in the local user repository a timeout message is sent back to the NAD.
D
Explanation:
Policy Manager looks for the device or user by executing the first filter associated with the authentication source.
After the device or user is found, Policy Manager then authenticates this entity against this authentication
source.
The flow is outlined below:
* On successful authentication, Policy Manager moves on to the next stage of policy evaluation, which collects role mapping attributes from the authorization sources.
* Where no authentication source is specified (for example, for unmanageable devices), Policy Manager passes the request to the next configured policy component for this service.
* If Policy Manager does not find the connecting entity in any of the configured authentication sources, it rejects the request.
References: ClearPass Policy Manager 6.5 User Guide (October 2015), page 134 https://community.arubanetworks.com/aruba/attachments/aruba/SoftwareUserReferenceGuides/52/1/ClearPass%20Policy%20Manager%206.5%20User%20Guide.pdf
What does Authorization allow users to do in a Policy Service?
- A . To use attributes in databases in role mapping and Enforcement.
- B . To use attributes stored in databases in Enforcement only, but not role mapping.
- C . To use attributes stored in external databases for Enforcement, but not internal databases.
- D . To use attributes stored in databases in role mapping only, but not Enforcement.
- E . To use attributes sored in internal databases for Enforcement, but not external databases.
Refer to the exhibit.
An administrator configured a service and tested authentication, but was unable to complete authentication successfully. The administrator performs a Search using insight and the information displays as shown.
What is a possible reason for the ErrorCode ‘Failed to classify request to service’ shown?
- A . The user failed authentication due to an incorrect password.
- B . ClearPass could not match the authentication request to a service, but the user passed authentication.
- C . ClearPass service authentication sources were not configured correctly.
- D . The NAD did not send the authentication request.
- E . ClearPass service rules were not configured correctly.
Refer to the exhibit.
Based on the Attribute configuration shown, which statement accurately describes the status of attribute values?
- A . Only the attribute values of department and memberOf can be used in role mapping policies.
- B . The attribute values of department, title, memberOf, telephoneNumber, and mail are directly applied as ClearPass.
- C . Only the attribute value of company can be used in role mapping policies, not the other attributes.
- D . The attribute values of department and memberOf are directly applied as ClearPass roles.
- E . Only the attribute values of title, telephoneNumber, and mail can be used in role mapping policies.
Refer to the exhibit.
Which statement accurately reflects the status of the Policy Simulation test figure shown?
- A . The test verifies that a client with username test1 can authenticate using EAP-PEAP.
- B . Role mapping simulation verifies if the remote lab AD has the ClearPass server certificate.
- C . Role mapping simulation verifies that the client certificate is valid during EAP-TLS authentication.
- D . The simulation test result shows the firewall roles assigned to the client by the Aruba Controller.
- E . The roles assigned in the results tab are based on rules matched in the AD Role Mapping Policy.
A customer would like to deploy ClearPass with these requirements:
✑ every day, 100 employees need to authenticate with their corporate laptops using EAP-TLS
✑ every Friday, a meeting with business partners takes place and an additional 50 devices need to authenticate using Web Login Guest Authentication
What should the customer do regarding licenses? (Select two.)
- A . When counting policy manager licenses, include the additional 50 business partner devices.
- B . When counting policy manager licenses, exclude the additional 50 business partner devices.
- C . Purchase Onboard licenses.
- D . Purchase guest licenses.
- E . Purchase Onguard licenses.
Refer to the exhibit.
Based on the Access Tracker output for the user shown, which statement describes the status?
- A . The Aruba Terminate Session enforcement profile as applied because the posture check failed.
- B . A Healthy Posture Token was sent to the Policy Manager.
- C . A RADIUS-Access-Accept message is sent back to the Network Access Device.
- D . The authentication method used is EAP-PEAP.
- E . A NAP agent was used to obtain the posture token for the user.
B
Explanation:
We see System Posture Status: HEALTHY (0)
End systems that pass all SHV tests receive a Healthy Posture Token, if they fail a single test they receive a Quarantine Posture Token.
References: CLEARPASS ONGUARD CONFIGURATION GUIDE (July 2015), page 13 https://community.arubanetworks.com/aruba/attachments/aruba/aaa-nac-guest-access-byod/21122/1/OnGuard%20config%20Tech%20Note%20v1.pdf
Refer to the exhibit.
Based on the information shown, what is the purpose of using [Time Source] for authorization?
- A . to check how long it has been since the last login authentication
- B . to check whether the guest account expired
- C . to check whether the MAC address is in the MAC Caching repository
- D . to check whether the MAC address status is known in the endpoints table
- E . to check whether the MAC address status is unknown in the endpoints table