GIAC GSSP-.NET GIAC Secure Software Programmer – C#.NET Online Training
GIAC GSSP-.NET Online Training
The questions for GSSP-.NET were last updated at Feb 27,2026.
- Exam Code: GSSP-.NET
- Exam Name: GIAC Secure Software Programmer - C#.NET
- Certification Provider: GIAC
- Latest update: Feb 27,2026
You work as a Software Developer for ABC Inc. The company uses Visual Studio .NET 2005 as its application development platform. You create a Web service using the .NET Framework 2.0. You call a method in the Web service. The following exception is thrown in the Web service: client.System.Web.Services.Protocols.SoapException: Server was unable to process request. System.NullReferenceException: Object reference not set to an instance of an object. You find out that it is the following line of code that throws the exception: if (Session ["StoredValue"] == null)
You must ensure that the method runs without throwing any exception.
What will you do to accomplish this task?
- A . Modify the WebMethod attribute in the Web service so that the EnableSession property is set to true.
- B . Add the following to the System.Web section of the Web.config file:
<sessionState mode="InProc" /> - C . Add the following to the System.Web section of the Web.config file:
<httpModules>
<add name="Session" type="System.Web.SessionState.SessionStateModule" /> </httpModules> - D . In the client code for the Web service’s proxy object, assign a new instance of the System.Net.CookieContainer object to the CookieContainer property.
- E . In the client code for the Web service’s proxy object, assign a new instance of the System.Net.CookieContainer object to the EnableSession property.
You work as a Software Developer for ManSoft Inc. You create an assembly. You place the assembly in a specific folder.
Which of the following classes can you use to determine whether the assembly was located in a specific folder? Each correct answer represents a complete solution. Choose two.
- A . UrlMembershipCondition
- B . ApplicationDirectoryMembershipCondition
- C . GacMembershipCondition
- D . SiteMembershipCondition
You work as a Web Application Developer for SunInfo Inc. The company uses Visual Studio 2008 as its application development platform. You create a Web application using .NET Framework 3.5. You want to ensure that when an unhandled exception occurs on the site, a custom error page errorpage.aspx is displayed. Also, you want to ensure that when the HTTP 500 error occurs, the servererror.aspx page is displayed.
Which of the following settings will you add inside the system.web section of the Web.config file to accomplish the task?
- A . <compilation debug="true">
</compilation> - B . <customErrors defaultRedirect="errorpage.aspx" mode="on"> <error statusCode="500" redirect="servererror.aspx"/>
- C . <customErrors defaultRedirect="servererror.aspx" mode="on"> <error statusCode="500" redirect="errorpage.aspx"/>
- D . <trace enabled="true" localOnly="false" />
John works as a Software Developer for InfoTech Inc. He develops an application named SerializeObj. He creates a custom class and wants to serialize its object. He also wants the object to be stored into an XML file named File1.xml.
He writes the following code:
public class Employees
{
public string EmpID;
public string EmpName;
public decimal Salary;
}
Which of the following code statements will John add in the application?
- A . XmlSerializer ObjectSerializer = new XmlSerializer(typeof(Employees), ObjectTypes);
- B . XmlSerializer ObjectSerializer = new XmlSerializer(typeof(Employees));
- C . XmlSerializer ObjectSerializer = new XmlSerializer(Employees);
- D . XmlSerializer ObjectSerializer = new XmlSerializer();
Which of the following techniques is used to transmit passwords during authentication?
- A . Asymmetric encryption
- B . Hashing
- C . Salted Hash
- D . Symmetric encryption
You work as a Software Developer for ABC Inc. The company uses Visual Studio.NET 2005 as its application development platform. You have recently finished development of Web services using the .NET Framework. The access control to Web services is part of your accountability. You are currently revealing an existing class as a XML Web service. You are required to ensure that the XML Web service is exclusively accessible to Web service clients within the ABC Inc. domain. To fulfill this requirement you want to change the access modifiers on methods that must be represented as Web methods.
What will you do to accomplish this task?
- A . Use the Public access modifier for each Web method.
- B . Use the Private access modifier for each Web method.
- C . Use the Internal or Friend access modifier for each Web method.
- D . Use the Protected access modifier for each Web method.
Georgina works as a Software Developer for BlueChip Inc. She develops an application named App1 using Visual Studio .NET. The company wants her to deploy App1 to a customer’s laptop. Georgina creates an assembly named Assembly1 to be stored in the Global Assembly Cache so that the Common Language Runtime (CLR) can locate and bind Assembly1.
As the application executes, the CLR locates the path of Assembly1 through the codebase setting. But, it finds no <codebase> element in the app.config file, and fails to bind Assembly1. Now, the CLR tries to locate Assembly1 through probing.
Which of the following will the CLR check to locate Assembly1? Each correct answer represents a part of the solution. Choose all that apply.
- A . Previously loaded assemblies
- B . The application base or root directory
- C . The Gacutil.exe tool in the Global Assembly Cache
- D . Sub-directories in the application’s root directory
- E . The culture attribute of the assembly
- F . The correct version of the assembly
- G . The assembly’s name
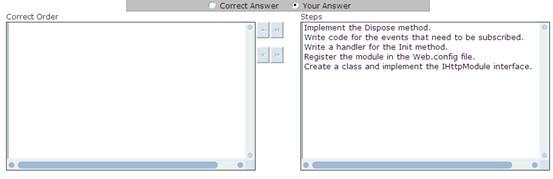
You work as a Software Developer for ABC Inc. The company uses Visual Studio.NET 2008 as its application development platform. You create an ASP.NET Web application using the .NET Framework 3.5. You want to use a HTTP module called on each and every request made by the application. It is called as part of the ASP.NET request pipeline. It has right to access life-cycle events throughout the request. You also want to ensure that the HTTP module allows a user to inspect incoming and outgoing requests and take appropriate action based on the request.
What will be the correct order to create the HTTP module?
- A .
You work as a Web Administrator for BlueWell Inc. The company’s sales employees access the Web server from remote locations via the Internet using Netscape Navigator or Internet Explorer. You want to secure the Web server. To secure the Web server, you want to use cookieless forms authentication.
Which of the following properties will you use to accomplish the task?
- A . FormsCookiePath
- B . CookieDomain
- C . CookieMode
- D . FormsCookieName
Which of the following security methods is used when the code requires a specific set of permissions, which are not known until runtime?
- A . Role-Based Security
- B . Windows NT Security
- C . Imperative Security
- D . Declarative Security
Latest GSSP-.NET Dumps Valid Version with 491 Q&As
Latest And Valid Q&A | Instant Download | Once Fail, Full Refund

