An OT network administrator is trying to implement active authentication.
Which two methods should the administrator use to achieve this? (Choose two.)
- A . Two-factor authentication on FortiAuthenticator
- B . Role-based authentication on FortiNAC
- C . FSSO authentication on FortiGate
- D . Local authentication on FortiGate
An OT administrator is defining an incident notification policy using FortiSIEM and would like to configure the system with a notification policy. If an incident occurs, the administrator would like to be able to intervene and block an IP address or disable a user in Active Directory from FortiSIEM.
Which step must the administrator take to achieve this task?
- A . Configure a fabric connector with a notification policy on FortiSIEM to connect with FortiGate.
- B . Create a notification policy and define a script/remediation on FortiSIEM.
- C . Define a script/remediation on FortiManager and enable a notification rule on FortiSIEM.
- D . Deploy a mitigation script on Active Directory and create a notification policy on FortiSIEM.
B
Explanation:
Reference: https://fortinetweb.s3.amazonaws.com/docs.fortinet.com/v2/attachments/06918379-afd1-11e9-a989-00505692583a/Standalone_PDF.pdf
An OT supervisor has configured LDAP and FSSO for the authentication. The goal is that all the users be authenticated against passive authentication first and, if passive authentication is not successful, then users should be challenged with active authentication.
What should the OT supervisor do to achieve this on FortiGate?
- A . Configure a firewall policy with LDAP users and place it on the top of list of firewall policies.
- B . Enable two-factor authentication with FSSO.
- C . Configure a firewall policy with FSSO users and place it on the top of list of firewall policies.
- D . Under config user settings configure set auth-on-demand implicit.
Which three Fortinet products can be used for device identification in an OT industrial control system (ICS)? (Choose three.)
- A . FortiNAC
- B . FortiManager
- C . FortiAnalyzer
- D . FortiSIEM
- E . FortiGate
Refer to the exhibit.
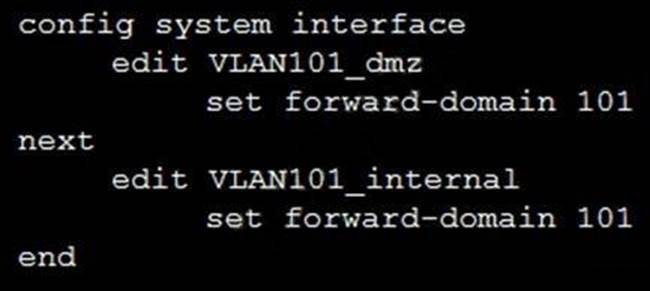
Given the configurations on the FortiGate, which statement is true?
- A . FortiGate is configured with forward-domains to reduce unnecessary traffic.
- B . FortiGate is configured with forward-domains to forward only domain controller traffic.
- C . FortiGate is configured with forward-domains to forward only company domain website traffic.
- D . FortiGate is configured with forward-domains to filter and drop non-domain controller traffic.
An OT supervisor needs to protect their network by implementing security with an industrial signature database on the FortiGate device.
Which statement about the industrial signature database on FortiGate is true?
- A . A supervisor must purchase an industrial signature database and import it to the FortiGate.
- B . An administrator must create their own database using custom signatures.
- C . By default, the industrial database is enabled.
- D . A supervisor can enable it through the FortiGate CLI.
Refer to the exhibit.
You are navigating through FortiSIEM in an OT network.
How do you view information presented in the exhibit and what does the FortiGate device security status tell you?
- A . In the PCI logging dashboard and there are one or more high-severity security incidents for the FortiGate device.
- B . In the summary dashboard and there are one or more high-severity security incidents for the FortiGate device.
- C . In the widget dashboard and there are one or more high-severity incidents for the FortiGate device.
- D . In the business service dashboard and there are one or more high-severity security incidents for the FortiGate device.
Refer to the exhibit.
You need to configure VPN user access for supervisors at the breach and HQ sites using the same soft FortiToken. Each site has a FortiGate VPN gateway.
What must you do to achieve this objective?
- A . You must use a FortiAuthenticator.
- B . You must register the same FortiToken on more than one FortiGate.
- C . You must use the user self-registration server.
- D . You must use a third-party RADIUS OTP server.
What are two benefits of a Nozomi integration with FortiNAC? (Choose two.)
- A . Enhanced point of connection details
- B . Direct VLAN assignment
- C . Adapter consolidation for multi-adapter hosts
- D . Importation and classification of hosts
Refer to the exhibit, which shows a non-protected OT environment.
An administrator needs to implement proper protection on the OT network.
Which three steps should an administrator take to protect the OT network? (Choose three.)
- A . Deploy an edge FortiGate between the internet and an OT network as a one-arm sniffer.
- B . Deploy a FortiGate device within each ICS network.
- C . Configure firewall policies with web filter to protect the different ICS networks.
- D . Configure firewall policies with industrial protocol sensors
- E . Use segmentation