Refer to the exhibit, which contains partial output from an IKE real-time debug.
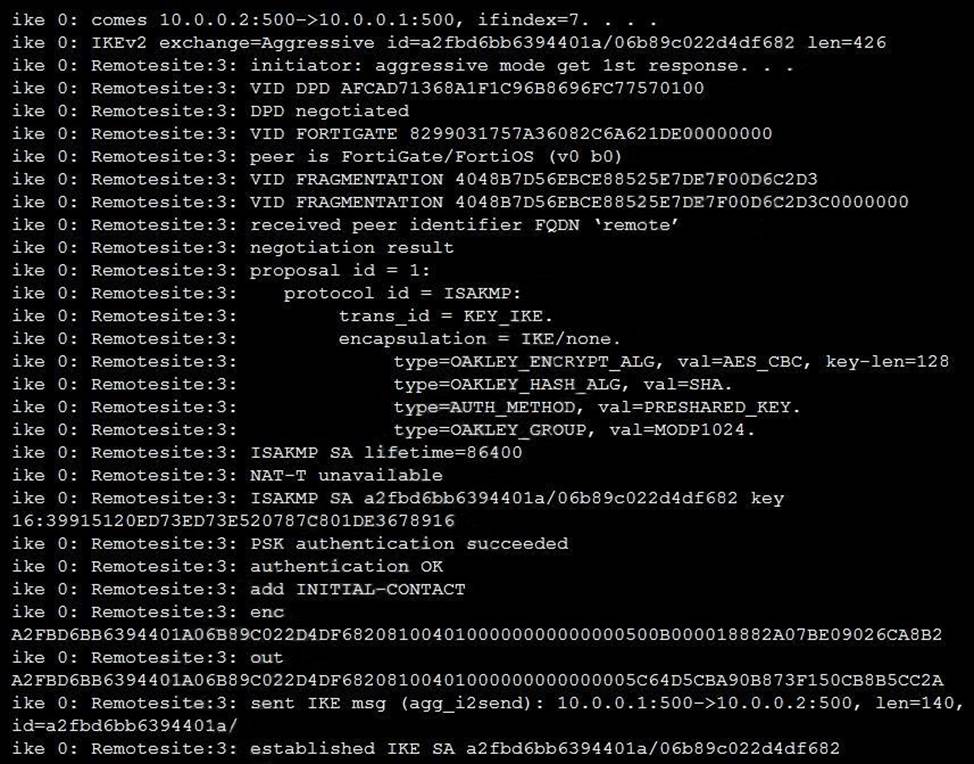
Which two statements about this debug output are correct? (Choose two.)
- A . The remote gateway IP address is 10.0.0.1.
- B . The initiator provided remote as its IPsec peer ID.
- C . It shows a phase 1 negotiation.
- D . The negotiation is using AES128 encryption with CBC hash.
A FortiGate has two default routes:
All Internet traffic is currently using port1. The exhibit shows partial information for one sample session of Internet traffic from an internal user:
What would happen with the traffic matching the above session if the priority on the first default route (IDd1) were changed from 5 to 20?
- A . The session would be deleted, and the client would need to start a new session.
- B . The session would remain in the session table, and its traffic would start to egress from port2.
- C . The session would remain in the session table, but its traffic would now egress from
both port1 and port2. - D . The session would remain in the session table, and its traffic would still egress from port1.
View the central management configuration shown in the exhibit, and then answer the question below.
Which server will FortiGate choose for antivirus and IPS updates if 10.0.1.243 is experiencing an outage?
- A . 10.0.1.240
- B . One of the public FortiGuard distribution servers
- C . 10.0.1.244
- D . 10.0.1.242
Examine the following partial outputs from two routing debug commands; then answer the question below:
Why the default route using port2 is not displayed in the output of the second command?
- A . It has a lower priority than the default route using port1.
- B . It has a higher priority than the default route using port1.
- C . It has a higher distance than the default route using port1.
- D . It is disabled in the FortiGate configuration.
C
Explanation:
http://kb.fortinet.com/kb/viewContent.do?externalId=FD32103
An administrator has configured a dial-up IPsec VPN with one phase 2, extended authentication (XAuth) and IKE mode configuration.
The administrator has also enabled the IKE real time debug:
diagnose debug application ike-1
diagnose debug enable
In which order is each step and phase displayed in the debug output each time a new dial-up user is connecting to the VPN?
- A . Phase1; IKE mode configuration; XAuth; phase 2.
- B . Phase1; XAuth; IKE mode configuration; phase2.
- C . Phase1; XAuth; phase 2; IKE mode configuration.
- D . Phase1; IKE mode configuration; phase 2; XAuth.
B
Explanation:
https://help.fortinet.com/fos50hlp/54/Content/FortiOS/fortigate-ipsecvpn-54/IPsec_VPN_Concepts/IKE_Packet_Processing.htm
View the exhibit, which contains a partial web filter profile configuration, and then answer the question below.
Which action will FortiGate take if a user attempts to access www.dropbox.com, which is categorized as File Sharing and Storage?
- A . FortiGate will exempt the connection based on the Web Content Filter configuration.
- B . FortiGate will block the connection based on the URL Filter configuration.
- C . FortiGate will allow the connection based on the FortiGuard category based filter configuration.
- D . FortiGate will block the connection as an invalid URL.
B
Explanation:
fortigate does it in order Static URL -> FortiGuard C > Content -> Advanced (java, cookie removal..)so block it in first step
Which statement about NGFW policy-based application filtering is true?
- A . After the application has been identified, the kernel uses only the Layer 4 header to match the traffic.
- B . The IPS security profile is the only security option you can apply to the security policy with the action set to ACCEPT.
- C . After IPS identifies the application, it adds an entry to a dynamic ISDB table.
- D . FortiGate will drop all packets until the application can be identified.
An administrator has configured two FortiGate devices for an HA cluster. While testing HA failover, the administrator notices that some of the switches in the network continue to send traffic to the former primary device. The administrator decides to enable the setting link-failed-signal to fix the problem.
Which statement about this setting is true?
- A . It sends an ARP packet to all connected devices, indicating that the HA virtual MAC address is reachable through a new master after a failover.
- B . It sends a link failed signal to all connected devices.
- C . It disabled all the non-heartbeat interfaces in all HA members for two seconds after a failover.
- D . It forces the former primary device to shut down all its non-heartbeat interfaces for one second, while the failover occurs.
D
Explanation:
Reference: https://kb.fortinet.com/kb/viewContent.do?externalId=FD40860&sliceId=1
Examine the output from the BGP real time debug shown in the exhibit, then the answer the question below:
Which statements are true regarding the output in the exhibit? (Choose two.)
- A . BGP peers have successfully interchanged Open and Keepalive messages.
- B . Local BGP peer received a prefix for a default route.
- C . The state of the remote BGP peer is OpenConfirm.
- D . The state of the remote BGP peer will go to Connect after it confirms the received prefixes.
View the exhibit, which contains the output of a diagnose command, and the answer the question below.
Which statements are true regarding the Weight value?
- A . Its initial value is calculated based on the round trip delay (RTT).
- B . Its initial value is statically set to 10.
- C . Its value is incremented with each packet lost.
- D . It determines which FortiGuard server is used for license validation.
Refer to the exhibit, which shows a partial routing table.
Assuming all the appropriate firewall policies are configured, which two pings will FortiGate route? (Choose two.)
- A . Source IP address: 10.1.0.10. Destination IP address: 10.64.1.52
- B . Source IPaddress: 10.72.3.52. Destination IP address: 10.1.0.254
- C . Source IPaddress: 10.10.4.24, Destination IPaddress: 10.72.3.20
- D . Source IPaddress: 10.73.9.10, Destination IPaddress: 10.72.3.15
Refer to the exhibit, which shows a FortiGate configuration.
An administrator is troubleshooting a web filter issue on FortiGate. The administrator has configured a web filter profile and applied it to a policy; however, the web filter is not inspecting any traffic that is passing through the policy.
What must the administrator change to fix the issue?
- A . The administrator must increase webfilter-timeout.
- B . The administrator must disable webfilter-force-off.
- C . The administrator must change protocol to TCP.
- D . The administrator must enable fortiguard-anycast.
D
Explanation:
Reference: https://docs.fortinet.com/document/fortigate/6.4.5/cli-reference/109620/config-system-fortiguard
View the exhibit, which contains the output of a diagnose command, and then answer the question below.
What statements are correct regarding the output? (Choose two.)
- A . This is an expected session created by a session helper.
- B . Traffic in the original direction (coming from the IP address 10.171.122.38) will be routed to the next-hop IP address 10.0.1.10.
- C . Traffic in the original direction (coming from the IP address 10.171.122.38) will be routed to the next-hop IP address 10.200.1.1.
- D . This is an expected session created by an application control profile.
Examine the output of the ‘get router info bgp summary’ command shown in the exhibit; then answer the question below.
Which statements are true regarding the output in the exhibit? (Choose two.)
- A . BGP state of the peer 10.125.0.60 is Established.
- B . BGP peer 10.200.3.1 has never been down since the BGP counters were cleared.
- C . Local BGP peer has not received an OpenConfirm from 10.200.3.1.
- D . The local BGP peer has received a total of 3 BGP prefixes.
Two independent FortiGate HA clusters are connected to the same broadcast domain. The administrator has reported that both clusters are using the same HA virtual MAC address. This creates a duplicated MAC address problem in the network .
What HA setting must be changed in one of the HA clusters to fix the problem?
- A . Group ID.
- B . Group name.
- C . Session pickup.
- D . Gratuitous ARPs.
A
Explanation:
https://help.fortinet.com/fos50hlp/54/Content/FortiOS/fortigate-high-availability-52/HA_failoverVMAC.htm
View the exhibit, which contains the output of a BGP debug command, and then answer the question below.
Which of the following statements about the exhibit are true? (Choose two.)
- A . For the peer 10.125.0.60, the BGP state of is Established.
- B . The local BGP peer has received a total of three BGP prefixes.
- C . Since the BGP counters were last reset, the BGP peer 10.200.3.1 has never been down.
- D . The local BGP peer has not established a TCP session to the BGP peer 10.200.3.1.
Examine the IPsec configuration shown in the exhibit; then answer the question below.
An administrator wants to monitor the VPN by enabling the IKE real time debug using these commands:
diagnose vpn ike log-filter src-addr4 10.0.10.1
diagnose debug application ike -1
diagnose debug enable
The VPN is currently up, there is no traffic crossing the tunnel and DPD packets are being interchanged between both IPsec gateways. However, the IKE real time debug does NOT show any output .
Why isn’t there any output?
- A . The IKE real time shows the phases 1 and 2 negotiations only. It does not show any more output once the tunnel is up.
- B . The log-filter setting is set incorrectly. The VPN’s traffic does not match this filter.
- C . The IKE real time debug shows the phase 1 negotiation only. For information after that, the administrator must use the IPsec real time debug instead: diagnose debug application ipsec -1.
- D . The IKE real time debug shows error messages only. If it does not provide any output, it indicates that the tunnel is operating normally.
Which real time debug should an administrator enable to troubleshoot RADIUS authentication problems?
- A . Diagnose debug application radius -1.
- B . Diagnose debug application fnbamd -1.
- C . Diagnose authd console Clog enable.
- D . Diagnose radius console Clog enable.
B
Explanation:
https://kb.fortinet.com/kb/documentLink.do?externalID=FD32838
View the exhibit, which contains the output of get sys ha status, and then answer the question below.
Which statements are correct regarding the output? (Choose two.)
- A . The slave configuration is not synchronized with the master.
- B . The HA management IP is 169.254.0.2.
- C . Master is selected because it is the only device in the cluster.
- D . port 7 is used the HA heartbeat on all devices in the cluster.
What events are recorded in the crashlogs of a FortiGate device? (Choose two.)
- A . A process crash.
- B . Configuration changes.
- C . Changes in the status of any of the FortiGuard licenses.
- D . System entering to and leaving from the proxy conserve mode.
A,D
Explanation:
diagnose debug crashlog read
275: 2014-08-05 13:03:53 proxy=acceptor service=imap session fail
mode=activated276: 2014-08-05 13:03:53 proxy=acceptor service=ftp session fail
mode=activated277: 2014-08-05 13:03:53 proxy=acceptor service=nntp session fail
mode=activated278: 2014-08-06 11:05:47 service=kernel conserve=on free=”45034
pages” red=”45874 pages” msg=”Kernel279: 2014-08-06 11:05:47 enters conserve
mode”280: 2014-08-06 13:07:16 service=kernel conserve=exit free=”86704 pages”
green=”68811 pages”281: 2014-08-06 13:07:16 msg=”Kernel leaves conserve
mode”282: 2014-08-06 13:07:16 proxy=imd sysconserve=exited total=1008 free=349
marginenter=201283: 2014-08-06 13:07:16 marginexit=302
View these partial outputs from two routing debug commands:
Which outbound interface will FortiGate use to route web traffic from internal users to the Internet?
- A . Both port1 and port2
- B . port3
- C . port1
- D . port2
View the global IPS configuration, and then answer the question below.
Which of the following statements is true regarding this configuration?
- A . IPS will scan every byte in every session.
- B . FortiGate will spawn IPS engine instances based on the system load.
- C . New packets will be passed through without inspection if the IPS socket buffer runs out of memory.
- D . IPS will use the faster matching algorithm which is only available for units with more than 4 GB memory.
Refer to the exhibit, which contains partial output from an IKE real-time debug.
Based on the debug output, which phase 1 setting is enabled in the configuration of this VPN?
- A . auto-discovery-shortcut
- B . auto-discovery-forwarder
- C . auto-discovery-sender
- D . auto-discovery-receiver
D
Explanation:
Reference: https://docs.fortinet.com/document/fortigate/6.0.0/handbook/320160/example-advpn-configuration
First the Spoke receives SHORTCUT_OFFER, it respondes with sending shortcut-query.
AT the end it receives SHORTCUT_REPLY and creates new dynamic tunnel (H2S_0_0).
Examine the following partial output from a sniffer command; then answer the question below.
What is the meaning of the packets dropped counter at the end of the sniffer?
- A . Number of packets that didn’t match the sniffer filter.
- B . Number of total packets dropped by the FortiGate.
- C . Number of packets that matched the sniffer filter and were dropped by the FortiGate.
- D . Number of packets that matched the sniffer filter but could not be captured by the sniffer.
D
Explanation:
https://kb.fortinet.com/kb/documentLink.do?externalID=11655
In which two states is a given session categorized as ephemeral? (Choose two.)
- A . A TCP session waiting to complete the three-way handshake.
- B . A TCP session waiting for FIN ACK.
- C . A UDP session with packets sent and received.
- D . A UDP session with only one packet received.
Four FortiGate devices configured for OSPF connected to the same broadcast domain. The first unit is elected as the designated router. The second unit is elected as the backup designated router.
Under normal operation, how many OSPF full adjacencies are formed to each of the other two units?
- A . 1
- B . 2
- C . 3
- D . 4
An administrator has configured a FortiGate device with two VDOMs: root and internal. The administrator has also created and inter-VDOM link that connects both VDOMs. The objective is to have each VDOM advertise some routes to the other VDOM via OSPF through the inter-VDOM link .
What OSPF configuration settings must match in both VDOMs to have the OSPF adjacency successfully forming? (Choose three.)
- A . Router ID.
- B . OSPF interface area.
- C . OSPF interface cost.
- D . OSPF interface MTU.
- E . Interface subnet mask.
An administrator wants to capture ESP traffic between two FortiGates using the built-in sniffer.
If the administrator knows that there is no NAT device located between both FortiGates, what command should the administrator execute?
- A . diagnose sniffer packet any ‘udp port 500’
- B . diagnose sniffer packet any ‘udp port 4500’
- C . diagnose sniffer packet any ‘esp’
- D . diagnose sniffer packet any ‘udp port 500 or udp port 4500’
C
Explanation:
Capture IKE Traffic without NAT:diagnose sniffer packet ‘host and udp port 500’―――――――――――――――――――――――――――――――――――――-Capture ESP Traffic without NAT:diagnose sniffer packet any ‘host and esp’―――――――――――――――――――――――――――――――――――――-Capture IKE and ESP with NAT-T:diagnose sniffer packet any ‘host and (udp port 500 or udp port 4500)’
Which two statements about the Security Fabric are true? (Choose two.)
- A . Only the root FortiGate collects network information and forwards it to FortiAnalyzer.
- B . FortiGate uses FortiTelemetry protocol to communicate with FortiAnalyzer.
- C . All FortiGate devices in the Security Fabric must have bidirectional FortiTelemetry connectivity.
- D . Branch FortiGate devices must be configured first.
B,C
Explanation:
Reference: https://docs.fortinet.com/document/fortigate/6.2.0/cookbook/327890/deploying-security-fabric
Which two configuration settings change the behavior for content-inspected traffic while FortiGate is in conserve mode? (Choose two.)
- A . IPS failopen
- B . mem failopen
- C . AV failopen
- D . UTM failopen
An administrator has configured the following CLI script on FortiManager, which failed to apply any changes to the managed device after being executed.
Why didn’t the script make any changes to the managed device?
- A . Commands that start with the # sign are not executed.
- B . CLI scripts will add objects only if they are referenced by policies.
- C . Incomplete commands are ignored in CLI scripts.
- D . Static routes can only be added using TCL scripts.
A
Explanation:
https://help.fortinet.com/fmgr/50hlp/56/5-6-2/FortiManager_Admin_Guide/1000_Device%20Manager/2400_Scripts/1000_Script%20sa mples/0200_CLI%20scripts+.htm#Error_Messages
A sequence of FortiGate CLI commands, as you would type them at the command line. A comment line starts with the number sign (#). A comment line will not be executed.
View the exhibit, which contains the output of a debug command, and then answer the question below.
Which one of the following statements about this FortiGate is correct?
- A . It is currently in system conserve mode because of high CPU usage.
- B . It is currently in extreme conserve mode because of high memory usage.
- C . It is currently in proxy conserve mode because of high memory usage.
- D . It is currently in memory conserve mode because of high memory usage.
Examine the output of the ‘diagnose ips anomaly list’ command shown in the exhibit; then answer the question below.
Which IP addresses are included in the output of this command?
- A . Those whose traffic matches a DoS policy.
- B . Those whose traffic matches an IPS sensor.
- C . Those whose traffic exceeded a threshold of a matching DoS policy.
- D . Those whose traffic was detected as an anomaly by an IPS sensor.
View the exhibit, which contains the partial output of an IKE real-time debug, and then answer the question below.
Why didn’t the tunnel come up?
- A . The pre-shared keys do not match.
- B . The remote gateway’s phase 2 configuration does not match the local gateway’s phase 2 configuration.
- C . The remote gateway’s phase 1 configuration does not match the local gateway’s phase 1 configuration.
- D . The remote gateway is using aggressive mode and the local gateway is configured to use man mode.
Which statement about the designated router (DR) and backup designated router (BDR) in an OSPF multi-access network is true?
- A . FortiGate first checks the OSPF ID to elect a DR.
- B . Non-DR and non-BDR routers will form full adjacencies to DR and BDR only.
- C . BDR is responsible for forwarding link state information from one router to another.
- D . Only the DR receives link state information from non-DR routers.
Examine the following traffic log; then answer the question below.
date-20xx-02-01 time=19:52:01 devname=master device_id="xxxxxxx"
log_id=0100020007 type=event subtype=system pri critical vd=root service=kemel status=failure msg="NAT port is exhausted."
What does the log mean?
- A . There is not enough available memory in the system to create a new entry in the NAT port table.
- B . The limit for the maximum number of simultaneous sessions sharing the same NAT port has been reached.
- C . FortiGate does not have any available NAT port for a new connection.
- D . The limit for the maximum number of entries in the NAT port table has been reached.
View the exhibit, which contains a partial routing table, and then answer the question below.
Assuming all the appropriate firewall policies are configured, which of the following pings will FortiGate route? (Choose two.)
- A . Source IP address 10.1.0.24, Destination IP address 10.72.3.20.
- B . Source IP address 10.72.3.27, Destination IP address 10.1.0.52.
- C . Source IP address 10.72.3.52, Destination IP address 10.1.0.254.
- D . Source IP address 10.73.9.10, Destination IP address 10.72.3.15.
View the exhibit, which contains the output of a diagnose command, and then answer the question below.
Which statements are true regarding the output in the exhibit? (Choose two.)
- A . FortiGate will probe 121.111.236.179 every fifteen minutes for a response.
- B . Servers with the D flag are considered to be down.
- C . Servers with a negative TZ value are experiencing a service outage.
- D . FortiGate used 209.222.147.3 as the initial server to validate its contract.
A,D
Explanation:
A C because flag is Failed so fortigate will check if server is available every 15 minD-state is I , contact to validate contract info
Which of the following statements are correct regarding application layer test commands? (Choose two.)
- A . They are used to filter real-time debugs.
- B . They display real-time application debugs.
- C . Some of them display statistics and configuration information about a feature or process.
- D . Some of them can be used to restart an application.
C,D
Explanation:
Application layer test commands don’t display info in real time, but they do show statistics and configuration info about a feature or process. You can also use some of these commands to restart a process or execute a change in its operation.
Which statement about memory conserve mode is true?
- A . A FortiGate exits conserve mode when the configured memory use threshold reaches yellow.
- B . A FortiGate starts dropping all the new and old sessions when the configured memory use threshold reaches extreme.
- C . A FortiGate starts dropping new sessions when the configured memory use threshold reaches red
- D . A FortiGate enters conserve mode when the configured memory use threshold reaches red