Refer to the exhibit.
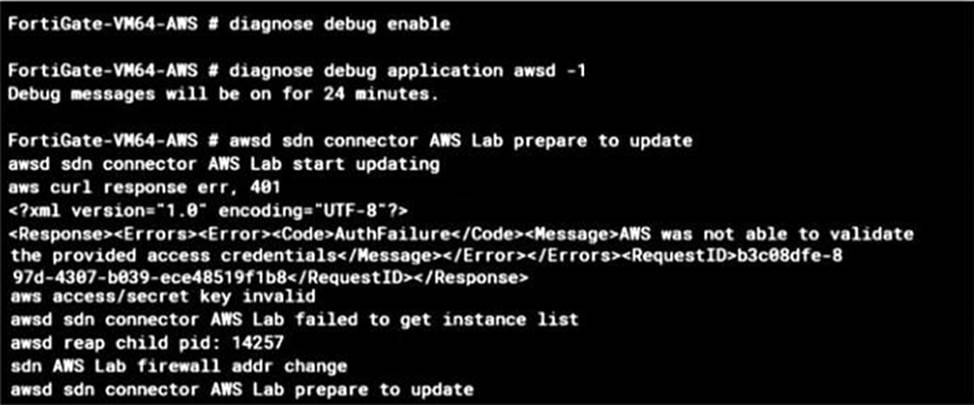
An administrator configured a FortiGate device to connect to me AWS API to retrieve resource values from the AWS console to create dynamic objects for the FortiGatepolicies. The administrator is unable to retrieve AWS dynamic objects on FortiGate.
Which three reasons can explain btw? (Choose three.)
- A . AWS was not able to validate credentials provided by the AWS Lab SON connector.
- B . The AWS Lab SON connector failed to connect on port 401.
- C . The AWS Lab SON connector failed to retrieve the instance list.
- D . The AWS API call is not supported on XML version I . O.
- E . The AWS Lab SON connector is configured with an invalid AWS access or secret key
An administrator has deployed an environment in AWS and is now trying to send outbound traffic from the web servers to the internet through FortiGate. The FortiGate policies are configured to allow all outbound traffic. however. the traffic is not reaching the FortiGate internal interface.
Which two statements Can be the reasons for this behavior? (Choose two)
- A . FortiGate is not configured as a default gateway tor web servers.
- B . Internet Gateway (IGW) is not configured for VPC.
- C . AWS security groups are blocking the traffic.
- D . AWS source destination checks are enabled on the FortiGate internal interfaces.
Refer to the exhibit.
A customer is using the AWS Elastic Load Balancer.
Which two statements are correct about the Elastic LoadBalancer configuration? (Choose two.)
- A . The Amazon resource name is used to access the load balancer node and targets.
- B . The DNS name is used to access devices.
- C . The load balancer is configured to load balance traffic between devices in two AZS.
- D . The load balancer is configuredfor the internal traffic oftheVPC
Refer to the exhibit.
A customer is using the AWS Elastic Load Balancer.
Which two statements are correct about the Elastic LoadBalancer configuration? (Choose two.)
- A . The Amazon resource name is used to access the load balancer node and targets.
- B . The DNS name is used to access devices.
- C . The load balancer is configured to load balance traffic between devices in two AZS.
- D . The load balancer is configuredfor the internal traffic oftheVPC
Refer to the exhibit.
You have created an autoscale configuration using a FortiGate HA Cloud Formation template. You want to examine the autoscale FortiOS configuration to confirm that FortiGate autoscale is configured to synchronize primary and secondary devices. On one of the FortiGate devices, you execute the command
shown in the exhibit.
Which statement is correct about the output of the command?
- A . The device is the primary in the HA configuration. with the IP address 10.0.0.173.
- B . The device is the secondary in the HA configuration, and the IP address Of the primary device is 10.0.0.173.
- C . The device is the primary in the HA configuration and the IP address of the secondary device is10.0.0.173.
- D . The device is the secondary in the HA configuration. with the IP address 10.0.0.173.
Which features are only available on FortiWeb when compared to Fortinet Managed Rules for AWS WAF?
- A . FortiWeb meets PCI 6.6 compliance.
- B . FortiWeb can scan web application vulnerabilities.
- C . FortiWeb provides a WAF subscription (FortiGuard) option.
- D . FortiWeb provides web application attack signatures.
Which three Fortinet products are available in Amazon Web Services in both on-demand and bring your own license (BYOL) formats? (Choose three.)
- A . FortiGate
- B . FortiWeb
- C . FortiADC
- D . FortiSlEM
- E . FortiSOAR
You connected to the AWS Management Console at 10:00 AM and verified that there are two FortiGate VMS running, You receive a call from a user reporting about a temporary slow Internet connection that lasted only a few minutes. When you go back to the AWS portal. you notice there are now two additional FortiGate VMS that you did not create. Later that day, the number of VMS returns to two without your intervention. A similar situation occurs several times during the week.
What is the most likely reason for this to happen?
- A . The VMS are in an availability group with dynamic membership.
- B . Autoscaling is configured to act as described in the scenario.
- C . The user ran a script to create the extra VMS to get faster connectivity.
- D . The AWS portal is not refreshed automatically. and another administrator is creating and removing the VMS as needed.
Your company deployed a FortiSandb0X for AWS.
Which statement is correct about FortiSandbox for AWS?
- A . FortiSandbox for AWS does not need more resources because it performs only management and analysis tasks.
- B . The FortiSandbox manager is installed on AWS platform and analyzes the results of the sandboxing process received from on-premises Windows instances.
- C . FortiSandbox for AWS comes as hybrid solution. The FortiSandb0X manager is installed on-premises and analyzes the results Of the sandboxing process received from AWS EC2 instances
- D . FortiSandbox deploys new EC2 instances with the custom Windows and Linux VMS, then it sends malware, runs it, and captures the results for analysis.
As part of the security plan you have been tasked with deploying a FortiGate in AWS.
Which two are the security responsibility of the customer in a cloud environment? (Choose two.)
- A . Virtualization platform
- B . Traffic encryption
- C . User management
- D . Storage infrastructure