Refer to the exhibits.
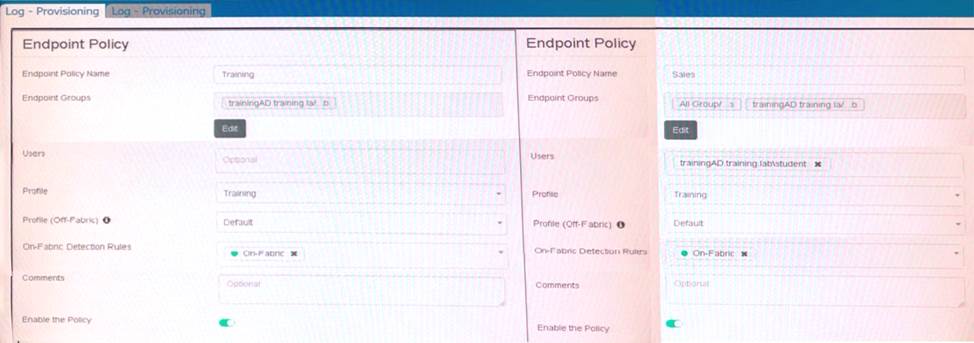
Which shows the configuration of endpoint policies.
Based on the configuration, what will happen when someone logs in with the user account student on an endpoint in the training AD domain?
- A . FortiClient EMS will assign the Sales policy
- B . FortiClient EMS will assign the Training policy
- C . FortiClient EMS will assign the Default policy
- D . FortiClient EMS will assign the Training policy for on-fabric endpoints and the Sales policy for the off-fabric endpoint
Refer to the exhibit.
Based on the settings shown in the exhibit, which two actions must the administrator take to make the endpoint compliant? (Choose two.)
- A . Enable the webfilter profile
- B . Integrate FortiSandbox for infected file analysis
- C . Patch applications that have vulnerability rated as high or above
- D . Run Calculator application on the endpoint
An administrator has a requirement to add user authentication to the ZTNA access for remote or off-fabric users.
Which FortiGate feature is required m addition to ZTNA?
- A . FortiGate FSSO
- B . FortiGate certificates
- C . FortiGate explicit proxy
- D . FortiGate endpoint control
What action does FortiClient anti-exploit detection take when it detects exploits?
- A . Terminates the compromised application process
- B . Blocks memory allocation to the compromised application process
- C . Patches the compromised application process
- D . Deletes the compromised application process
Refer to the exhibit.
Which shows multiple endpoint policies on FortiClient EMS.
Which policy is applied to the endpoint in the AD group training AD?
- A . The Sales policy
- B . The Training policy
- C . Both the Sales and Training policies because their priority is higher than the Default policy
- D . The Default policy because it has the highest priority
Refer to the exhibit.
Based on the FortiClient log details shown in the exhibit, which two statements are true? (Choose two.)
- A . The filename is Unconfirmed 899290 .crdownload.
- B . The file status is Quarantined
- C . The filename is sent to ForuSandbox for further inspection.
- D . The file location IS ??D:Users.
Refer to the exhibit.
Based on the logs shown in the exhibit, why did FortiClient EMS fail to install FortiClient on the endpoint?
- A . The remote registry service is not running
- B . The Windows installer service is not running
- C . The task scheduler service is not running.
- D . The FortiClient antivirus service is not running
An administrator installs FortiClient EMS in the enterprise.
Which component is responsible for enforcing protection and checking security posture?
- A . FortiClient vulnerability scan
- B . FortiClient EMS tags
- C . FortiClient EMS
- D . FortiClient
Which three features does FortiClient endpoint security include? (Choose three.)
- A . L2TP
- B . Real-time protection
- C . DLP
- D . Vulnerability management
- E . IPsec
A new chrome book is connected in a school’s network.
Which component can the EMS administrator use to manage the FortiClient web filter extension installed on the Google Chromebook endpoint?
- A . FortiClient EMS
- B . FortiClient site categories
- C . FortiClient customer URL list
- D . FortiClient web filter extension
A FortiClient EMS administrator has enabled the compliance rule for the sales department.
Which Fortinet device will enforce compliance with dynamic access control?
- A . FortiClient
- B . FortiClient EMS
- C . FortiGate
- D . FortiAnalyzer
An administrator configures ZTNA configuration on the FortiGate for remote users.
Which statement is true about the firewall policy?
- A . It enforces access control
- B . It redirects the client request to the access proxy
- C . It defines the access proxy
- D . It applies security profiles to protect traffic
B
Explanation:
https://docs.fortinet.com/document/fortigate/7.0.0/new-features/194961/basic-ztna-configuration
An administrator wants to simplify remote access without asking users to provide user credentials.
Which access control method provides this solution?
- A . SSL VPN
- B . ZTNA full mode
- C . L2TP
- D . ZTNA IP/MAC filtering mode
Why does FortiGate need the root CA certificate of FortiClient EMS?
- A . To sign FortiClient CSR requests
- B . To revoke FortiClient client certificates
- C . To trust certificates issued by FortiClient EMS
- D . To update FortiClient client certificates
Which two statements are true about ZTNA? (Choose two.)
- A . ZTNA provides role-based access
- B . ZTNA manages access for remote users only
- C . ZTNA manages access through the client only
- D . ZTNA provides a security posture check
What does FortiClient do as a fabric agent? (Choose two.)
- A . Provides application inventory
- B . Provides IOC verdicts
- C . Automates Responses
- D . Creates dynamic policies
Which component or device shares ZTNA tag information through Security Fabric integration?
- A . FortiClient EMS
- B . FortiGate
- C . FortiGate Access Proxy
- D . FortiClient
An administrator is required to maintain a software vulnerability on the endpoints, without showing the feature on the FortiClient dashboard.
What must the administrator do to achieve this requirement?
- A . Disable select the vulnerability scan feature in the deployment package
- B . Use the default endpoint profile
- C . Select the vulnerability scan feature in the deployment package, but disable the feature on the endpoint profile
- D . Click the hide icon on the vulnerability scan tab
Refer to the exhibit.
Which shows FortiClient EMS deployment profiles.
When an administrator creates a deployment profile on FortiClient EMS, which statement about the deployment profile is true?
- A . Deployment-1 will install FortiClient on new AD group endpoints
- B . Deployment-2 will install FortiClient on both the AD group and workgroup
- C . Deployment-2 will upgrade FortiClient on both the AD group and workgroup
- D . Deployment-1 will upgrade FortiClient only on the workgroup
An administrator needs to connect FortiClient EMS as a fabric connector to FortiGate.
What is the prerequisite to get FortiClient EMS to connect to FortiGate successfully?
- A . Revoke and update the FortiClient EMS root CA.
- B . Revoke and update the FortiClient client certificate on EMS.
- C . Import and verify the FortiClient client certificate on FortiGate.
- D . Import and verify the FortiClient EMS root CA certificate on FortiGate