Refer to the exhibit.
Examine the intrusion prevention system (IPS) diagnostic command.
Which statement is correct If option 5 was used with the IPS diagnostic command and the outcome was a decrease in the CPU usage?
- A . The IPS engine was inspecting high volume of traffic.
- B . The IPS engine was unable to prevent an intrusion attack.
- C . The IPS engine was blocking all traffic.
- D . The IPS engine will continue to run in a normal state.
Which three authentication timeout types are availability for selection on FortiGate? (Choose three.)
- A . hard-timeout
- B . auth-on-demand
- C . soft-timeout
- D . new-session
- E . Idle-timeout
A,D,E
Explanation:
https://kb.fortinet.com/kb/documentLink.do?externalID=FD37221
FortiGate is configured as a policy-based next-generation firewall (NGFW) and is applying web filtering and application control directly on the security policy.
Which two other security profiles can you apply to the security policy? (Choose two.)
- A . Antivirus scanning
- B . File filter
- C . DNS filter
- D . Intrusion prevention
When a firewall policy is created, which attribute is added to the policy to support recording logs to a FortiAnalyzer or a FortiManager and improves functionality when a FortiGate is integrated with these devices?
- A . Log ID
- B . Universally Unique Identifier
- C . Policy ID
- D . Sequence ID
B
Explanation:
Reference: https://docs.fortinet.com/document/fortigate/6.0.0/handbook/554066/firewall-policies
Which three pieces of information does FortiGate use to identify the hostname of the SSL server when SSL certificate inspection is enabled? (Choose three.)
- A . The subject field in the server certificate
- B . The serial number in the server certificate
- C . The server name indication (SNI) extension in the client hello message
- D . The subject alternative name (SAN) field in the server certificate
- E . The host field in the HTTP header
ACD
Explanation:
Reference: https://checkthefirewall.com/blogs/fortinet/ssl-inspection
Which three CLI commands can you use to troubleshoot Layer 3 issues if the issue is in neither the physical layer nor the link layer? (Choose three.)
- A . diagnose sys top
- B . execute ping
- C . execute traceroute
- D . diagnose sniffer packet any
- E . get system arp
Consider the topology:
Application on a Windows machine <–{SSL VPN} –>FGT–> Telnet to Linux server.
An administrator is investigating a problem where an application establishes a Telnet session to a Linux server over the SSL VPN through FortiGate and the idle session times out after about 90 minutes. The administrator would like to increase or disable this timeout.
The administrator has already verified that the issue is not caused by the application or Linux server. This issue does not happen when the application establishes a Telnet connection to the Linux server directly on the LAN.
What two changes can the administrator make to resolve the issue without affecting services running through FortiGate? (Choose two.)
- A . Set the maximum session TTL value for the TELNET service object.
- B . Set the session TTL on the SSLVPN policy to maximum, so the idle session timeout will not happen after 90 minutes.
- C . Create a new service object for TELNET and set the maximum session TTL.
- D . Create a new firewall policy and place it above the existing SSLVPN policy for the SSL VPN traffic, and set the new TELNET service object in the policy.
NGFW mode allows policy-based configuration for most inspection rules.
Which security profile’s configuration does not change when you enable policy-based inspection?
- A . Web filtering
- B . Antivirus
- C . Web proxy
- D . Application control
Which of the following statements about backing up logs from the CLI and downloading logs from the GUI are true? (Choose two.)
- A . Log downloads from the GUI are limited to the current filter view
- B . Log backups from the CLI cannot be restored to another FortiGate.
- C . Log backups from the CLI can be configured to upload to FTP as a scheduled time
- D . Log downloads from the GUI are stored as LZ4 compressed files.
Which two statements are true about the FGCP protocol? (Choose two.)
- A . Not used when FortiGate is in Transparent mode
- B . Elects the primary FortiGate device
- C . Runs only over the heartbeat links
- D . Is used to discover FortiGate devices in different HA groups
An administrator needs to increase network bandwidth and provide redundancy.
What interface type must the administrator select to bind multiple FortiGate interfaces?
- A . VLAN interface
- B . Software Switch interface
- C . Aggregate interface
- D . Redundant interface
C
Explanation:
Reference: https://forum.fortinet.com/tm.aspx?m=120324
Which CLI command will display sessions both from client to the proxy and from the proxy to the servers?
- A . diagnose wad session list
- B . diagnose wad session list | grep hook-pre&&hook-out
- C . diagnose wad session list | grep hook=pre&&hook=out
- D . diagnose wad session list | grep "hook=pre"&"hook=out"
What types of traffic and attacks can be blocked by a web application firewall (WAF) profile? (Choose three.)
- A . Traffic to botnetservers
- B . Traffic to inappropriate web sites
- C . Server information disclosure attacks
- D . Credit card data leaks
- E . SQL injection attacks
If Internet Service is already selected as Source in a firewall policy, which other configuration objects can be added to the Source filed of a firewall policy?
- A . IP address
- B . Once Internet Service is selected, no other object can be added
- C . User or User Group
- D . FQDN address
Refer to the exhibit.
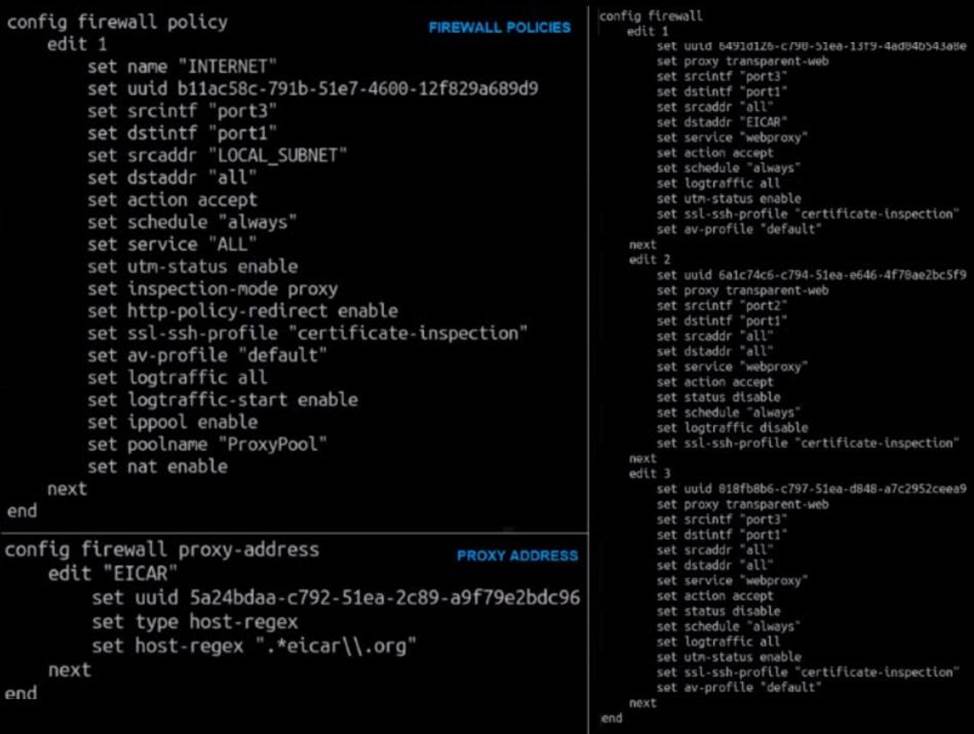
The exhibit shows a CLI output of firewall policies, proxy policies, and proxy addresses.
How does FortiGate process the traffic sent to http://www.fortinet.com?
- A . Traffic will be redirected to the transparent proxy and it will be allowed by proxy policy ID 3.
- B . Traffic will not be redirected to the transparent proxy and it will be allowed by firewall policy ID 1.
- C . Traffic will be redirected to the transparent proxy and It will be allowed by proxy policy ID 1.
- D . Traffic will be redirected to the transparent proxy and it will be denied by the proxy implicit deny policy.
Refer to the exhibit to view the firewall policy.
Which statement is correct if well-known viruses are not being blocked?
- A . The firewall policy does not apply deep content inspection.
- B . The firewall policy must be configured in proxy-based inspection mode.
- C . The action on the firewall policy must be set to deny.
- D . Web filter should be enabled on the firewall policy to complement the antivirus profile.
Which two protocols are used to enable administrator access of a FortiGate device? (Choose two.)
- A . SSH
- B . HTTPS
- C . FTM
- D . FortiTelemetry
A,B
Explanation:
Reference: https://docs.fortinet.com/document/fortigate/6.4.0/hardening-your-fortigate/995103/buildingsecurity-into-fortios
Refer to the exhibit.
The exhibit contains the configuration for an SD-WAN Performance SLA, as well as the output of diagnose sys virtual-wan-link health-check.
Which interface will be selected as an outgoing interface?
- A . port2
- B . port4
- C . port3
- D . port1
Which statement regarding the firewall policy authentication timeout is true?
- A . It is an idle timeout. The FortiGate considers a user to be “idle” if it does not see any packets coming from the user’s source IP.
- B . It is a hard timeout. The FortiGate removes the temporary policy for a user’s source IP address after this timer has expired.
- C . It is an idle timeout. The FortiGate considers a user to be “idle” if it does not see any packets coming from the user’s source MAC.
- D . It is a hard timeout. The FortiGate removes the temporary policy for a user’s source MAC address after this timer has expired.
Which of the following statements about central NAT are true? (Choose two.)
- A . IP tool references must be removed from existing firewall policies before enabling central NAT.
- B . Central NAT can be enabled or disabled from the CLI only.
- C . Source NAT, using central NAT, requires at least one central SNAT policy.
- D . Destination NAT, using central NAT, requires a VIP object as the destination address in a firewall.
Refer to the exhibit.
A network administrator is troubleshooting an IPsec tunnel between two FortiGate devices.
The administrator has determined that phase 1 status is up. but phase 2 fails to come up.
Based on the phase 2 configuration shown in the exhibit, what configuration change will bring phase 2 up?
- A . On HQ-FortiGate, enable Auto-negotiate.
- B . On Remote-FortiGate, set Seconds to 43200.
- C . On HQ-FortiGate, enable Diffie-Hellman Group 2.
- D . On HQ-FortiGate, set Encryption to AES256.
D
Explanation:
Reference: https://docs.fortinet.com/document/fortigate/5.4.0/cookbook/168495
Which scanning technique on FortiGate can be enabled only on the CLI?
- A . Heuristics scan
- B . Trojan scan
- C . Antivirus scan
- D . Ransomware scan
A
Explanation:
Reference: https://docs.fortinet.com/document/fortigate/6.0.0/handbook/567568/enabling-scanning
An administrator has configured two-factor authentication to strengthen SSL VPN access.
Which additional best practice can an administrator implement?
- A . Configure Source IP Pools.
- B . Configure split tunneling in tunnel mode.
- C . Configure different SSL VPN realms.
- D . Configure host check.
Which two types of traffic are managed only by the management VDOM? (Choose two.)
- A . FortiGuard web filter queries
- B . PKI
- C . Traffic shaping
- D . DNS
If the Services field is configured in a Virtual IP (VIP), which statement is true when central NAT is used?
- A . The Services field prevents SNAT and DNAT from being combined in the same policy.
- B . The Services field is used when you need to bundle several VIPs into VIP groups.
- C . The Services field removes the requirement to create multiple VIPs for different services.
- D . The Services field prevents multiple sources of traffic from using multiple services to
connect to a single computer.
Refer to the web filter raw logs.
Based on the raw logs shown in the exhibit, which statement is correct?
- A . Social networking web filter category is configured with the action set to authenticate.
- B . The action on firewall policy ID 1 is set to warning.
- C . Access to the social networking web filter category was explicitly blocked to all users.
- D . The name of the firewall policy is all_users_web.
Which of the following statements correctly describes FortiGates route lookup behavior when searching for a suitable gateway? (Choose two)
- A . Lookup is done on the first packet from the session originator
- B . Lookup is done on the last packet sent from the responder
- C . Lookup is done on every packet, regardless of direction
- D . Lookup is done on the trust reply packet from the responder
Refer to the exhibit, which contains a session diagnostic output.
Which statement is true about the session diagnostic output?
- A . The session is a UDP unidirectional state.
- B . The session is in TCP ESTABLISHED state.
- C . The session is a bidirectional UDP connection.
- D . The session is a bidirectional TCP connection.
Refer to the exhibit.
The Root and To_Internet VDOMs are configured in NAT mode. The DMZ and Local VDOMs are configured in transparent mode.
The Root VDOM is the management VDOM. The To_Internet VDOM allows LAN users to access internet. The To_lnternet VDOM is the only VDOM with internet access and is directly connected to ISP modem.
Which two statements are true? (Choose two.)
- A . Inter-VDOM links are required to allow traffic between the Local and Root VDOMs.
- B . A static route is required on the To_Internet VDOM to allow LAN users to access the internet.
- C . Inter-VDOM links are required to allow traffic between the Local and DMZ VDOMs.
- D . Inter-VDOM links are not required between the Root and To_Internet VDOMs because the Root VDOM is used only as a management VDOM.
Which CLI command allows administrators to troubleshoot Layer 2 issues, such as an IP address conflict?
- A . get system status
- B . get system performance status
- C . diagnose sys top
- D . get system arp
Which of the following statements is true regarding SSL VPN settings for an SSL VPN portal?
- A . By default, FortiGate uses WINS servers to resolve names.
- B . By default, the SSL VPN portal requires the installation of a client’s certificate.
- C . By default, split tunneling is enabled.
- D . By default, the admin GUI and SSL VPN portal use the same HTTPS port.
Which three statements about a flow-based antivirus profile are correct? (Choose three.)
- A . IPS engine handles the process as a standalone.
- B . FortiGate buffers the whole file but transmits to the client simultaneously.
- C . If the virus is detected, the last packet is delivered to the client.
- D . Optimized performance compared to proxy-based inspection.
- E . Flow-based inspection uses a hybrid of scanning modes available in proxy-based inspection.
Refer to the exhibit.
Given the interfaces shown in the exhibit. which two statements are true? (Choose two.)
- A . Traffic between port2 and port2-vlan1 is allowed by default.
- B . port1-vlan10 and port2-vlan10 are part of the same broadcast domain.
- C . port1 is a native VLAN.
- D . port1-vlan and port2-vlan1 can be assigned in the same VDOM or to different VDOMs.
Refer to the FortiGuard connection debug output.
Based on the output shown in the exhibit, which two statements are correct? (Choose two.)
- A . A local FortiManager is one of the servers FortiGate communicates with.
- B . One server was contacted to retrieve the contract information.
- C . There is at least one server that lost packets consecutively.
- D . FortiGate is using default FortiGuard communication settings.
Examine this output from a debug flow:
Why did the FortiGate drop the packet?
- A . The next-hop IP address is unreachable.
- B . It failed the RPF check.
- C . It matched an explicitly configured firewall policy with the action DENY.
- D . It matched the default implicit firewall policy.
D
Explanation:
https://kb.fortinet.com/kb/documentLink.do?externalID=13900
Refer to the exhibit.
In the network shown in the exhibit, the web client cannot connect to the HTTP web server. The administrator runs the FortiGate built-in sniffer and gets the output as shown in the exhibit.
What should the administrator do next to troubleshoot the problem?
- A . Run a sniffer on the web server.
- B . Capture the traffic using an external sniffer connected to port1.
- C . Execute another sniffer in the FortiGate, this time with the filter “host 10.0.1.10”
- D . Execute a debug flow.
Which statements about the firmware upgrade process on an active-active HA cluster are true? (Choose two.)
- A . The firmware image must be manually uploaded to each FortiGate.
- B . Only secondary FortiGate devices are rebooted.
- C . Uninterruptable upgrade is enabled by default.
- D . Traffic load balancing is temporally disabled while upgrading the firmware.
An administrator is running the following sniffer command:
diagnose aniffer packer any "host 192.168.2.12" 5
Which three pieces of Information will be Included in me sniffer output? {Choose three.)
- A . Interface name
- B . Packet payload
- C . Ethernet header
- D . IP header
- E . Application header
Which two statements about IPsec authentication on FortiGate are correct? (Choose two.)
- A . For a stronger authentication, you can also enable extended authentication (XAuth) to request the remote peer to provide a username and password
- B . FortiGate supports pre-shared key and signature as authentication methods.
- C . Enabling XAuth results in a faster authentication because fewer packets are exchanged.
- D . A certificate is not required on the remote peer when you set the signature as the authentication method.
A,B
Explanation:
Reference: https://docs.fortinet.com/document/fortigate/6.2.0/cookbook/913287/ipsec-vpn-authenticating-aremote-fortigate-peer-with-a-pre-shared-key
An administrator is configuring an Ipsec between site A and siteB. The Remotes Gateway setting in both sites has been configured as Static IP Address. For site A, the local quick mode selector is 192.16.1.0/24 and the remote quick mode selector is 192.16.2.0/24.
How must the administrator configure the local quick mode selector for site B?
- A . 192.168.3.0/24
- B . 192.168.2.0/24
- C . 192.168.1.0/24
- D . 192.168.0.0/8
How does FortiGate act when using SSL VPN in web mode?
- A . FortiGate acts as an FDS server.
- B . FortiGate acts as an HTTP reverse proxy.
- C . FortiGate acts as DNS server.
- D . FortiGate acts as router.
Refer to the exhibit.
Based on the administrator profile settings, what permissions must the administrator set to run the diagnose firewall auth list CLI command on FortiGate?
- A . Custom permission for Network
- B . Read/Write permission for Log & Report
- C . CLI diagnostics commands permission
- D . Read/Write permission for Firewall
Examine the exhibit, which contains a virtual IP and firewall policy configuration.
The WAN (port1) interface has the IP address 10.200.1.1/24. The LAN (port2) interface has the IP address 10.0.1.254/24.
The first firewall policy has NAT enabled on the outgoing interface address. The second firewall policy is configured with a VIP as the destination address.
Which IP address will be used to source NAT the Internet traffic coming from a workstation with the IP address 10.0.1.10/24?
- A . 10.200.1.10
- B . Any available IP address in the WAN (port1) subnet 10.200.1.0/24
- C . 10.200.1.1
- D . 10.0.1.254
Refer to the exhibits.
The SSL VPN connection fails when a user attempts to connect to it.
What should the user do to successfully connect to SSL VPN?
- A . Change the SSL VPN port on the client.
- B . Change the Server IP address.
- C . Change the idle-timeout.
- D . Change the SSL VPN portal to the tunnel.
A
Explanation:
Reference: https://docs.fortinet.com/document/fortigate/5.4.0/cookbook/150494
Which two protocol options are available on the CLI but not on the GUI when configuring an SD-WAN Performance SLA? (Choose two.)
- A . DNS
- B . ping
- C . udp-echo
- D . TWAMP
How do you format the FortiGate flash disk?
- A . Load a debug FortiOS image.
- B . Load the hardware test (HQIP) image.
- C . Execute the CLI command execute formatlogdisk.
- D . Select the format boot device option from the BIOS menu.
Examine the IPS sensor configuration shown in the exhibit, and then answer the question below.
An administrator has configured the WINDOWS_SERVERS IPS sensor in an attempt to determine
whether the influx of HTTPS traffic is an attack attempt or not. After applying the IPS sensor, FortiGate is still not generating any IPS logs for the HTTPS traffic.
What is a possible reason for this?
- A . The IPS filter is missing the Protocol: HTTPS option.
- B . The HTTPS signatures have not been added to the sensor.
- C . A DoS policy should be used, instead of an IPS sensor.
- D . A DoS policy should be used, instead of an IPS sensor.
- E . The firewall policy is not using a full SSL inspection profile.
Refer to the exhibit.
The exhibit contains a network diagram, central SNAT policy, and IP pool configuration.
The WAN (port1) interface has the IP address 10.200.1.1/24.
The LAN (port3) interface has the IP address 10.0.1.254/24.
A firewall policy is configured to allow to destinations from LAN (port3) to WAN (port1).
Central NAT is enabled, so NAT settings from matching Central SNAT policies will be
applied.
Which IP address will be used to source NAT the traffic, if the user on Local-Client (10.0.1.10) pings the IP address of Remote-FortiGate (10.200.3.1)?
- A . 10.200.1.149
- B . 10.200.1.1
- C . 10.200.1.49
- D . 10.200.1.99
Which statement about the policy ID number of a firewall policy is true?
- A . It is required to modify a firewall policy using the CLI.
- B . It represents the number of objects used in the firewall policy.
- C . It changes when firewall policies are reordered.
- D . It defines the order in which rules are processed.
Refer to the exhibit.
Which contains a Performance SLA configuration.
An administrator has configured a performance SLA on FortiGate.
Which failed to generate any traffic.
Why is FortiGate not generating any traffic for the performance SLA?
- A . Participants configured are not SD-WAN members.
- B . There may not be a static route to route the performance SLA traffic.
- C . The Ping protocol is not supported for the public servers that are configured.
- D . You need to turn on the Enable probe packets switch.
D
Explanation:
Reference: https://docs.fortinet.com/document/fortigate/6.2.0/cookbook/478384/performance-sla-linkmonitoring