Which configuration objects can be selected for the Source field of a firewall policy? (Choose two.)
- A . Firewall service
- B . User or user group
- C . IP Pool
- D . FQDN address
By default, when logging to disk, when does FortiGate delete logs?
- A . 30 days
- B . 1 year
- C . Never
- D . 7 days
Which of the following conditions are required for establishing an IP Sec VPN between two FortiGate devices? (Choose two)
- A . If XAuth is enabled as a server in one peer, it must be enabled as a client in the other peer
- B . If the VPN is configured as route-based, there must be at least one firewall policy with the action set to IP Sec
- C . If the VPN is configured as Dial Up User in one peer, it must be configured as either Static IP Address or Dynamic DNS in the other peer.
- D . If the VPN is configured as a policy-based in one peer, it must also be configured as policy based in the other peer.
Based on this output, which statements are correct? (Choose two.)
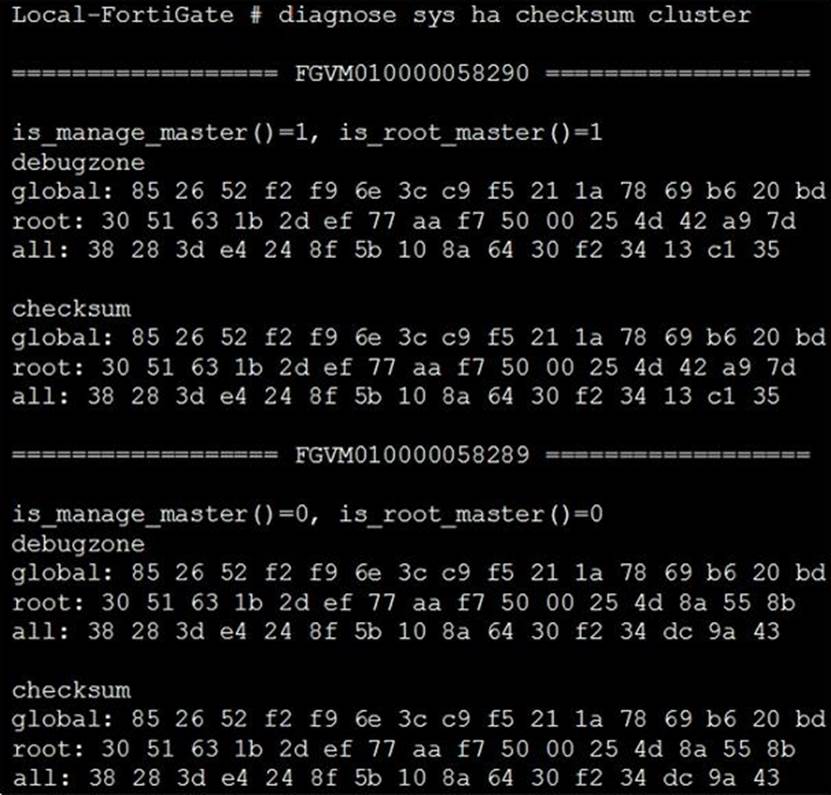
- A . The all V DOM is not synchronized between the primary and secondary FortiGate devices
- B . The root V DOM is not synchronized between the primary and secondary FortiGate devices
- C . The global configuration is synchronized between the primary and secondary FortiGate devices
- D . The FortiGate devices have three V DOMS
Which of the following statements about NTLM authentication are correct? (Choose two.)
- A . It is useful when users login to DCs that are not monitored by a collector agent
- B . It takes over as the primary authentication method when configured alongside FS SO.
- C . Multidomain environments require DC agents on every domain controller.
- D . NTLM-enabled web browsers are required.
Refer to the exhibit.
The exhibits show the firewall policies and the objects used in the firewall policies.
The administrator is using the Policy Lookup feature and has entered the search criteria shown in the exhibit.
Which of the following will be highlighted based on the input criteria?
- A . Policy with 1
- B . Policies with ID 2 and 3
- C . Policy with ID 5
- D . Policy with ID 4
An administrator is attempting to allow access to https://fortinet. com through a firewall policy that is configured with a webfilter and an SSL inspection profile configured for deep inspection which of the following are possible actions to eliminate the certificate error generated by deep inspection? (Choose Two)
- A . Implement firewall authentication for all users that need access to fortinet.com
- B . Manually install the FortiGate deep inspection certificate as a trusted CA
- C . Configure fortinet.com access to bypass the IPS engine
- D . Configure an SSL-inspection exemption for fortinet.com
An administrator has configured a dialup IPsec VPN with XAuth.
Which statement best describes what occurs during this scenario?
- A . Phase 1 negotiations will skip preshared key exchange.
- B . Only digital certificates will be accepted as an authentication method in phase 1.
- C . Dialup clients must provide a username and password for authentication
- D . Dialup clients must provide their localID during phase 2 negotiations
What are the expected actions if traffic matches this IPS sensor? (Choose two)
- A . The sensor will gather a packet log for all matched traffic
- B . The sensor will not block attackers matching the A32S. Botnet signature
- C . The sensor will block all attacks for Windows Servers
- D . The sensor will reset all connections that match these signatures
An administrator has configured the following settings
config system settings
set ses-denied-traffic enable end
config system global
set block-session-timer 30 end
What does the configuration do? (Choose two)
- A . Reduces the amount of logs generated by denied traffic
- B . Enforces device detection on all interfaces for 30 minutes
- C . Blocks denied users for 30 minutes
- D . Creates a session for traffic being denied
How does FortiGate verify the login credentials of a remote LDAP user?
- A . FortiGate regenerates the algorithm based on the login credentials and compares it to the algorithm stored on the LDAP server
- B . FortiGate sends the user-entered credentials to the LDAP server for authentication
- C . FortiGate queries the LDAP server for credentials.
- D . FortiGate queries its own database for credentials.
Which users and user groups are allowed access to the network through captive portal?
- A . Users and groups defined in the firewall policy.
- B . Only individual users – not groups – defined in the captive portal configuration
- C . Groups defined in the captive portal configuration
- D . All users
Which of the following statements about policy-based IPsec tunnels are true? (Choose two. )
- A . They can be configured in both NAT/Route and transparent operation modes.
- B . They support L2TP-over-IPsec.
- C . They require two firewall policies, one for each directions of traffic flow.
- D . They support GRE-over-IPsec.
An administrator wants to block HTTP uploads Examine the exhibit, which contains the proxy address created for that purpose.
Where must the proxy address be used?
- A . As the source in a firewall policy
- B . As the source in a proxy policy
- C . As the destination in a firewall policy
- D . As the destination in a proxy policy
Which one of the following processes is involved in updating IPS from FortiGuard?
- A . FortiGate IPS update requests are sent using UDP port 443.
- B . Protocol decoder update requests are sent to service. fortiguard.net.
- C . IPS signature update requests are sent to update fortiguard.net.
- D . IPS engine updates can only be obtained using push updates.
An administrator wants to create a policy-based IPsec VPN tunnel between two FortiGate devices which configuration steps must be performed on both devices to support this scenario? (Choose three)
- A . Define the phase 1 parameters, without enabling IPsec interface mode
- B . Define the phase 2 parameters
- C . Set the phase 2 encapsulation method to transport mode
- D . Define at least one firewall policy, with the action set to IPsec
- E . Define a route to the remote network over the IPsec tunnel
An administrator wants to configure a FortiGate as a DNS server. FotiGate must use a DNS database first, and then relay all irresolvable queries to an external DNS server.
Which of the following DNS methods must you use?
- A . Recursive
- B . Non-recursive
- C . Forward to primary and secondary DNS
- D . Forward to system DNS
Why is the administrator getting the error shown in the exhibit?
- A . The administrator must first enter the command edit global
- B . The administrator admin does not have the privileges required to configure global settings.
- C . The global settings cannot be configured from the root VDOM context.
- D . The command config system global does not exist in FortiGate.
If the issuer and Subject values are the same in a digital certificate, which type of entity was the certificate issued to?
- A . A CRL
- B . A person
- C . A subordinate CA
- D . A root CA
Which statements about a One-to-One IP pool are true? (Choose two. )
- A . It is used for destination NAT.
- B . It allows the fixed mapping of an internal address range to an external address range.
- C . It does not use port address translation.
- D . ID It allows the configuration of ARP replies
Examine the two static routes shown in the exhibit, then answer the following question
Which of the following is the expected FortiGate behavior regarding these two routes to the same destination?
- A . FortiGate will load balance all traffic across both routes.
- B . FortiGate will use the port1 route as the primary candidate
- C . FortiGate will route twice as much traffic to the port2 route
- D . FortiGate will only actuate the port1 route in the routing table
Examine the exhibit, which shows the partial output of an IKE real-time debug.
Which of the following statement about the output is true?
- A . The VPN is configured to use pre-shared key authentication.
- B . Extended authentication (XAuth) was successful
- C . Remote is the host name of the remote lPsec peer.
- D . Phase 1went down.
How can you block or allow to Twitter using a firewall policy?
- A . Configure the Destination field as Internet Service objects for Twitter
- B . Configure the Action field as Learn and select Twitter.
- C . Configure the Service field as Internet Service objects for Twitter
- D . Configure the source field as Internet Service objects for Twitter
When browsing to an internal web server using a web-mode SSL VPN bookmark, which IP address is used as the source of the HTTP request?
- A . remote user’s public IPaddress
- B . The public IP address of the FortiGate device.
- C . The remote user’s virtual lP address.
- D . The internal IP address of the FortiGate device.
Which of the following services can be inspected by the DLP profile? (Choose three.)
- A . NFS
- B . FTP
- C . IMAP
- D . CIFS
- E . HTTP-POST
A company needs to provide SSL VPN access to two user groups. The company also needs to display different welcome messages on the SSL VPN login screen for both user groups.
What is required in the SSL VPN configuration to meet these requirements?
- A . Different SSL VPN realms for each group
- B . Two separate SSL VPNs in different interfaces mapping the same ss root
- C . Two firewall policies with different captive portals
- D . Different virtual SSL VPN IP addresses for each group.
The FSSO Collector Agent set to advanced access mode for the Windows Active Directory uses which of the following?
- A . LDAP convention
- B . NTLM convention
- C . Windows convention – NetBiosUsername
- D . RSSO convention
NGFW mode allows policy-based configuration for most inspection rules. Which security profile’s configuration does not change when you enable policy-based inspection?
- A . Web filtering
- B . Antivirus
- C . Web proxy
- D . Application control
Which of the following statements are true when using WPAD with the DHCP discovery method? (Choose two.)
- A . If the DHCP method fails, browsers will try the DNS method.
- B . The browser needs to be preconfigured with the DHCP server’s IP address
- C . The browser sends a DHCPONFORM request to the DHCP server.
- D . The DHCP server provides the PAC file for download
What is the limitation of using a URL list and application control on the same firewall policy, in NGFW policy-based mode?
- A . It limits the scope of application control to the browser-based technology category only
- B . It limits the scope of application control to scan application traffic based on application category only.
- C . It limits the scope of application control to scan application traffic using parent signatures only.
- D . It limits the scope of application control to scan application traffic on DNS protocol only.
View the exhibit:
Based on the configuration shown in the exhibit, what statements about application control behavior are true? (Choose two)
- A . Access to all unknown applications will be allowed
- B . Access to browser based Social.Media applications will be blocked
- C . Access to mobile social media applications will be blocked
- D . Access to all applications in Social.Media category will be blocked
An administrator is running the following sniffer command :
diagnose sniffer packet any"host 10.0.2.10" 3
What information will be included in the sniffer output? (Choose three.)
- A . IP header
- B . Ethernet header
- C . Packet payload
- D . Application header
- E . Interface name
An administrator has configured two VLAN interfaces :
A DHCP server is connected to the VLAN 10 interface , A DHCP Client is connected to the VLAN5 interface. However , the DHCP client cannot get a dynamic IP address from the DHCP server.
What is the cause of the problem?
- A . Both interfaces must belong to the same forward domain
- B . The role of the VLAN10 interface must be set to server
- C . Both interfaces must have the same VLAN ID.
- D . Both interfaces must be in different VDOMs.
An administrator observes that the port1 interface cannot be configured with an IP address.
What can be the reasons for that? (Choose three.)
- A . The interface has been configured for one-arm sniffer
- B . The interface is a member of a virtual wire pair
- C . The operation mode is transparent.
- D . The interface is a member of a zone.
- E . Captive portal is enabled in the interface.
Examine the IPS sensor and DoS policy configuration shown in the exhibit, then answer the question below.
When detecting attacks, which anomaly, signature, or filter wil FortiGate evaluate first?
- A . SMTP.Login.Brute Force
- B . IMAP.Login.brute.Force
- C . ip_src_session
- D . Location: server Protocol: SMTP
When using SD-WAN, how do you configure the next-hop gateway address for a member interface so that FortiGate can forward Internet traffic?
- A . It must be configured in a static route using the sdwan virtual interface.
- B . It must be provided in the SD-WAN member interface configuration.
- C . It must be configured in a policy-route using the sdwan virtual interface.
- D . It must be learned automatically through a dynamic routing protocol.
Examine the IPS sensor configuration shown in the exhibit, and then answer the question below.
An administrator has configured the WinDOS_SERVERS IPS sensor in an attempt to determine whether the influx of HTTPS traffic is an attack attempt or not. After applying the IPS sensor, FortiGate is still not generating any IPS logs for the HTTPS traffic.
What is a possible reason for this?
- A . The IPS filter is missing the Protocol: HTTPS option.
- B . The HTTPS signatures have not been added to the sensor.
- C . A DOS policy should be used, instead of an IPS sensor.
- D . A DOS policy should be used, instead of an IPS sensor.
- E . The firewall policy is not using a full SSL inspection profile.
A FortiGate is operating in NAT mode and configured with two virtual LAN (VLAN) sub interfaces added to the physical interface. Which statements about the VLAN sub interfaces can have the same VLAN ID, only if they have IP addresses in different subnets.
- A . The two VLAN sub interfaces can have the same VLAN ID, only if they have lP addresses in
different subnets , - B . The two VLAN sub interfaces must have different VLAN IDs ,
- C . The two VLAN sub interfaces can have the same VLAN ID, only if they belong to different VDOMs.
- D . The two VLAN sub interfaces can have the same VLAN ID, only if they have IP addresses in the same subnet.
How does FortiGate select the central SNAT policy that is applied to a TCP session?
- A . It selects the SNAT policy specified in the configuration of the outgoing interface ,
- B . It selects the first matching central SNAT policy, reviewing from top to bottom.
- C . It selects the central SNAT policy with the lowest priority.
- D . It selects the 5NAT policy specified in the configuration of the firewall policy that matches the traffic.
Which of the following SD-WAN-load balancing method use interface weight value to distribute traffic?
- A . Source IP
- B . Spillover
- C . Volume
- D . Session
View the exhibit.
Which of the following statements are correct? (Choose two.)
- A . This setup requires at least two firewall policies with the action set to lPsec.
- B . Dead peer detection must be disabled to support this type of IPsec setup.
- C . The Tunnel route is the primary route for reaching the remote site. The TunnelA route is used only if the TunnelB VPN is down.
- D . This is a redundant IPsec setup.
What information is flushed when the chunk-size value is changed in the config dip settings?
- A . The database for DLP document fingerprinting
- B . The supported file types in the DLP filters
- C . The archived files and messages
- D . The file name patterns in the DLP filters
Which is the correct description of a hash result as it relates to digital certificates?
- A . A unique value used to verify the input data.
- B . An output value that is used to identify the person or deduce that authored the input data.
- C . An obfuscation used to mask the input data.
- D . An encrypted output value used to safeguard the input data.
View the exhibit.
What does this raw log indicate? (Choose two.)
- A . FortiGate blocked the traffic
- B . type indicates that a security event was recorded
- C . 10.0.1.20 is the IP address for lavito tk.
- D . policyid indicates that traffic went through the IPS firewall policy
An administrator needs to strengthen the security for SSL VPN access.
Which of the following statements are best practices to do so? (Choose three)
- A . Configure split tunneling for content inspection.
- B . Configure host restrictions by IP or MAC address.
- C . Configure two-factor authentication using security certificates
- D . Configure SSL offloading to a content processor (FortiASIC)
- E . Configure a client integrity check host-check)