You are configuring the root FortiGate to implement the security fabric. You are configuring port10 to communicate with a downstream FortiGate. View the default Edit Interface in the exhibit below:
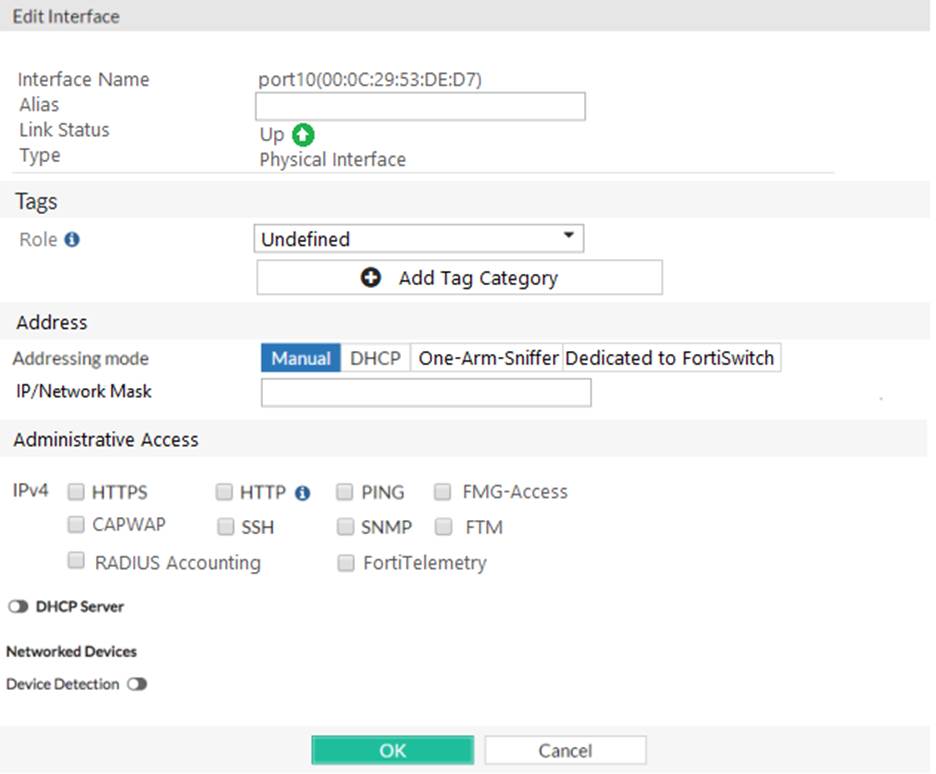
When configuring the root FortiGate to communicate with a downstream FortiGate, which settings are required to be configured? (Choose two.)
- A . Device detection enabled.
- B . Administrative Access: FortiTelemetry.
- C . IP/Network Mask.
- D . Role: Security Fabric.
When browsing to an internal web server using a web-mode SSL VPN bookmark, which IP address is used as the source of the HTTP request?
- A . remote user’s public IP address
- B . The public IP address of the FortiGate device.
- C . The remote user’s virtual IP address.
- D . The internal IP address of the FotiGate device.
Examine this output from a debug flow:
Why did the FortiGate drop the packet?
- A . The next-hop IP address is unreachable.
- B . It failed the RPF check.
- C . It matched an explicitly configured firewall policy with the action DENY.
- D . It matched the default implicit firewall policy.
Examine the exhibit, which shows the output of a web filtering real time debug.
Why is the site www.bing.com being blocked?
- A . The web site www.bing.com is categorized by FortiGuard as Malicious Websites.
- B . The user has not authenticated with the FortiGate yet.
- C . The web server IP address 204.79.197.200 is categorized by FortiGuard as Malicious Websites.
- D . The rating for the web site www.bing.com has been locally overridden to a category that is being blocked.
View the exhibit:
Which statement about the exhibit is true? (Choose two.)
- A . Broadcast traffic received in port1-VLAN10 will not be forwarded to port2-VLAN10.
- B . port-VLAN1 is the native VLAN for the port1 physical interface.
- C . port1-VLAN10 and port2-VLAN10 can be assigned to different VDOMs.
- D . Traffic between port1-VLAN1 and port2-VLAN1 is allowed by default.
Which of the following statements about backing up logs from the CLI and downloading logs from the GUI are true? (Choose two.)
- A . Log downloads from the GUI are limited to the current log filter view
- B . Log backups from the CLI cannot be restored to another FortiGate.
- C . Log backups from the CLI can be configured to upload to FTP at a scheduled time
- D . Log downloads from the GUI are stored as LZ4 compressed files.
Examine the network diagram shown in the exhibit, then answer the following question:
Which one of the following routes is the best candidate route for FGT1 to route traffic from the Workstation to the Web server?
A)
B)
C)
D)
- A . Option A
- B . Option B
- C . Option C
- D . Option D
A team manager has decided that while some members of the team need access to particular website, the majority of the team does not.
Which configuration option is the most effective option to support this request?
- A . Implement a web filter category override for the specified website.
- B . Implement web filter authentication for the specified website
- C . Implement web filter quotas for the specified website.
- D . Implement DNS filter for the specified website.
Examine this output from a debug flow:
Which statements about the output are correct? (Choose two.)
- A . FortiGate received a TCP SYN/ACK packet.
- B . The source IP address of the packet was translated to 10.0.1.10.
- C . FortiGate routed the packet through port 3.
- D . The packet was allowed by the firewall policy with the ID 00007fc0.
Examine this FortiGate configuration:
How does the FortiGate handle web proxy traffic coming from the IP address 10.2.1.200 that requires authorization?
- A . It always authorizes the traffic without requiring authentication.
- B . It drops the traffic.
- C . It authenticates the traffic using the authentication scheme SCHEME2.
- D . It authenticates the traffic using the authentication scheme SCHEME1.
Which of the following statements are best practices for troubleshooting FSSO? (Choose two.)
- A . Include the group of guest users in a policy.
- B . Extend timeout timers.
- C . Guarantee at least 34 Kbps bandwidth between FortiGate and domain controllers.
- D . Ensure all firewalls allow the FSSO required ports.
Which statements about antivirus scanning mode are true? (Choose two.)
- A . In proxy-based inspection mode antivirus buffers the whole file for scarring before sending it to the client.
- B . In flow-based inspection mode, you can use the CLI to configure antivirus profiles to use protocol option profiles.
- C . In proxy-based inspection mode, if a virus is detected, a replacement message may not be displayed immediately.
- D . In quick scan mode, you can configure antivirus profiles to use any of the available signature data bases.
In a high availability (HA) cluster operating in active-active mode, which of the following correctly describes the path taken by the SYN packet of an HTTP session that is offloaded to a secondary FortiGate?
- A . Client > primary FortiGate> secondary FortiGate> primary FortiGate> web server.
- B . Client > secondary FortiGate> web server.
- C . Client >secondary FortiGate> primary FortiGate> web server.
- D . Client> primary FortiGate> secondary FortiGate> web server.
An administrator is configuring an IPsec between site A and site B. The Remotes Gateway setting in both sites has been configured as Static IP Address. For site A, the local quick mode selector is 192.16.1.0/24 and the remote quick mode selector is 192.16.2.0/24.
How must the administrator configure the local quick mode selector for site B?
- A . 192.168.3.0.24
- B . 192.168.2.0.24
- C . 192.168.1.0.24
- D . 192.168.0.0.8
Which of the following are purposes of NAT traversal in IPsec? (Choose two.)
- A . To delete intermediary NAT devices in the tunnel path.
- B . To dynamically change phase 1 negotiation mode aggressive mode.
- C . To encapsulation ESP packets in UDP packets using port 4500.
- D . To force a new DH exchange with each phase 2 rekey.
Which of the following statements correctly describes FortiGates route lookup behavior when searching for a suitable gateway? (Choose two)
- A . Lookup is done on the trust packet from the session originator
- B . Lookup is done on the last packet sent from the re spender
- C . Lookup is done on every packet, regardless of direction
- D . Lookup is done on the trust reply packet from the re spender
Examine the two static routes shown in the exhibit, then answer title following question.
Which of the following is the expected FortiGate behavior regarding these two routes to the same destination?
- A . FortiGate will load balance all traffic across both routes.
- B . FortiGate will use the port1 route as the primary candidate.
- C . FortiGate will route twice as much traffic to the port2 route
- D . FortiGate will only actuate the portl route m tlie routing table
Which of the following statements about central NAT are true? (Choose two.)
- A . IP tool references must be removed from existing firewall policies before enabling central NAT.
- B . Central NAT can be enabled or disabled from the CLI only.
- C . Source NAT, using central NAT, requires at least one central SNAT policy.
- D . Destination NAT, using central NAT, requires a VIP object as the destination address in a firewall policy.
Refer to the following exhibit.
Why is FortiGate not blocking the test file over FTP download?
- A . Deep-inspection must be enabled for FortiGate to fully scan FTP traffic.
- B . FortiGate needs to be operating in flow-based inspection mode in order to scan FTP traffic.
- C . The FortiSandbox signature database is required to successfully scan FTP traffic.
- D . The proxy options profile needs to scan FTP traffic on a non-standard port.
View the following exhibit, which shows the firewall policies and the object uses in the firewall policies.
The administrator is using the Policy Lookup feature and has entered the search create shown in the following exhibit.
Which of the following will be highlighted based oil the input criteria?
- A . Policy with ID 1.
- B . Policies with ID 2 and 3.
- C . Policy with ID 5.
- D . Policy with ID 4
An administrator wants to create a policy-based IPsec VPN tunnel between two FortiGate devices Winch configuration steps must be performed on both devices to support this scenario? (Choose three.)
- A . Define the phase 1 parameters, without enabling IPsec interface mode
- B . Define the phase 2 parameters.
- C . Set the phase 2 encapsulation method to transport mode
- D . Define at least one firewall policy, with the action set to IPsec.
- E . Define a route to the remote network over the IPsec tunnel.
Which of the following statements about NTLM authentication are correct? (Choose two.)
- A . It is useful when users log in to DCs that are not monitored by a collector agent.
- B . It takes over as the primary authentication method when configured alongside FSSO.
- C . Multi-domain environments require DC agents on every domain controller.
- D . NTLM-enabled web browsers are required.
View the certificate shown to the exhibit, and then answer the following question:
The CA issued this certificate to which entity?
- A . A root CA
- B . A person
- C . A bridge CA
- D . A subordinate CA
Why does FortiGate keep TCP sessions in the session table for some seconds even after both sides (client and server) have terminated the session?
- A . To remove the NAT operation.
- B . To generate logs
- C . To finish any inspection operations.
- D . To allow for out-of-order packets that could arrive after the FIN/ACK packets.
A FortiGate is operating in NAT mode and configured with two virtual LAN (VLAN) sub interfaces added to the physical interface.
Which statements about the VLAN sub interfaces can have the same VLAND ID, only if they have IP addresses in different subnets.
- A . The two VLAN sub interfaces can have the same VLAN ID, only if they have IP addresses in different subnets.
- B . The two VLAN sub interfaces must have different VLAN IDs.
- C . The two VLAN sub interfaces can have the same VLAN ID, only if they belong to different VDOMs.
- D . The two VLAN sub interfaces can have the same VLAN ID, only if they have IP addresses in the same subnet.
You mc tasked to design a new IPsec deployment with the following criteria:
– There are two HQ sues that all satellite offices must connect to
– The satellite offices do not need to communicate directly with other satellite offices
– No dynamic routing will be used
– The design should minimize the number of tannels being configured.
Winch topology should be used to satisfy all of the requirements?
- A . Partial mesh
- B . Hub-and-spoke
- C . Fully meshed
- D . Redundant
Which of the following statements is true regarding SSL VPN settings for an SSL VPN portal?
- A . By default, FortiGate uses WINS servers to resolve names.
- B . By default, the SSL VPN portal requires the installation of a client’s certificate.
- C . By default, split tunneling is enabled.
- D . By default, the admin GUI and SSL VPN portal use the same HTTPS port.
Which of the following conditions roust be met in order for a web browser to trust a web server certificate signed by a third-party CA?
- A . The web-server certificate DM be installed on the browser
- B . The public key of the web server certificate must be installed on die browser
- C . The CA certificate that signed the web-server certificate inutile installed on the browser
- D . The private key of the CA certificate that signed the browser certificate must be installed on the browser.
An administrator has configured the following settings:
What does the configuration do? (Choose two.)
- A . Reduces the amount of logs generated by denied traffic.
- B . Enforces device detection on all interfaces for 30 minutes.
- C . Blocks denied users for 30 minutes.
- D . Creates a session for traffic being denied.
An administrator observes that the port1 interface cannot be configured with an IP address.
What can be the reasons for that? (Choose three.)
- A . The interface has been configured for one-arm sniffer.
- B . The interface is a member of a virtual wire pair.
- C . The operation mode is transparent.
- D . The interface is a member of a zone.
- E . Captive portal is enabled in the interface.
What information is flushed when the chunk-size value is changed in the config dlp settings?
- A . The database for DLP document fingerprinting
- B . The supported file types in the DLP filters
- C . The archived files and messages
- D . The file name patterns in the DLP filters
Which is the correct description of a hash result as it relates to digital certificates?
- A . A unique value used to verify the input data
- B . An output value that is used to identify the person or deuce that authored the input data.
- C . An obfuscation used to mask the input data.
- D . An encrypted output value used to safe-guard die input data
Examine the exhibit, which shows the partial output of an IKE real-time debug.
Which of the following statement about the output is true?
- A . The VPN is configured to use pre-shared key authentication.
- B . Extended authentication (XAuth) was successful.
- C . Remote is the host name of the remote IPsec peer.
- D . Phase 1 went down.
Examine the network diagram shown in the exhibit, and then answer the following question:
A firewall administrator must configure equal cost multipath (ECMP) routing on FGT1 to ensure both port1 and port3 links are used at the same time for all traffic destined for 172.20.2.0/24.
Which of the following static routes will satisfy this requirement on FGT1? (Choose two.)
- A . 172.20.2.0/24 (1/0) via 10.10.1.2, port1 [0/0]
- B . 172.20.2.0/24 (25/0) via 10.10.3.2, port3 [5/0]
- C . 172.20.2.0/24 (1/150) via 10.10.3.2, port3 [10/0]
- D . 172.20.2.0/24 (1/150) via 10.30.3.2, port3 [10/0]
On a FortiGate with a hard disk, how can you upload logs to FortiAnalyzer or FortiManager? (Choose two.)
- A . hourly
- B . real tune
- C . on-demand
- D . store-and-upload
Examine this FortiGate configuration:
Examine the output of the following debug command:
Based on the diagnostic outputs above, how is the FortiGate handling the traffic for new sessions that require inspection?
- A . It is allowed, but with no inspection
- B . It is allowed and inspected as long as the inspection is flow based
- C . It is dropped.
- D . It is allowed and inspected, as long as the only inspection required is antivirus.
When using WPAD DNS method, winch FQDN format do browsers use to query the DNS server?
A)
B)
C)
D)
- A . Option A
- B . Option B
- C . Option C
- D . Option D
Examine the IPS sensor configuration and forward traffic logs shown in the exhibit; then, answer the question below.
An administrator has configured the WINDOS_SERVERS IPS sensor in an attempt to determine whether the influx of HTTPS traffic is an attack attempt or not. After applying the IPS sensor, FortiGate is still not generating any IPS logs for the HTTPS traffic.
What is a possible reason for this?
- A . The IPS filter is missing the Protocol: HTTPS option.
- B . The HTTPS signatures have not been added to the sensor.
- C . A DoS policy should be used, instead of an IPS sensor.
- D . A DoS policy should be used, instead of an IPS sensor.
- E . The firewall policy is not using a full SSL inspection profile.
What types of traffic and attacks can be blocked by a web application firewall (WAF) profile? (Choose three.)
- A . Traffic to botnet servers
- B . Traffic to inappropriate web sites
- C . Server information disclosure attacks
- D . Credit card data leaks
- E . SQL injection attacks
Which statement about DLP on FortiGate is true?
- A . It can archive files and messages.
- B . It can be applied to a firewall policy in a flow-based VDOM
- C . Traffic shaping can be applied to DLP sensors.
- D . Files can be sent to FortiSandbox for detecting DLP threats.
Examine this PAC file configuration.
Which of the following statements are true? (Choose two.)
- A . Browsers can be configured to retrieve this PAC file from the FortiGate.
- B . Any web request to the 172.25.120.0/24 subnet is allowed to bypass the proxy.
- C . All requests not made to Fortinet.com or the 172.25.120.0/24 subnet, have to go through altproxy.corp.com: 8060.
- D . Any web request fortinet.com is allowed to bypass the proxy.
Which statements about the firmware upgrade process on an active-active HA cluster are true? (Choose two.)
- A . The firmware image must be manually uploaded to each FortiGate.
- B . Only secondary FortiGate devices are rebooted.
- C . Uninterruptable upgrade is enabled by default.
- D . Traffic load balancing is temporally disabled while upgrading the firmware.
Which statements best describe auto discovery VPN (ADVPN). (Choose two.)
- A . It requires the use of dynamic routing protocols so that spokes can learn the routes to other spokes.
- B . ADVPN is only supported with IKEv2.
- C . Tunnels are negotiated dynamically between spokes.
- D . Every spoke requires a static tunnel to be configured to other spokes so that phase 1 and phase 2 proposals are defined in advance.
An administrator needs to create an SSL-VPN connection for accessing an internal server using the bookmark Port Forward.
What step is required for this configuration?
- A . Configure an SSL VPN realm for clients to use the port forward bookmark.
- B . Configure the client application to forward IP traffic through FortiClient.
- C . Configure the virtual IP address to be assigned t the SSL VPN users.
- D . Configure the client application to forward IP traffic to a Java applet proxy.
What FortiGate configuration is required to actively prompt users for credentials?
- A . You must enable one or more protocols that support active authentication on a firewall policy
- B . You must position the firewall policy for active authentication before a firewall policy foe passive authentication.
- C . You must assign users to a group for active authentication
- D . You must enable the Authentication setting on the firewall policy
Which statements are true regarding firewall policy NAT using the outgoing interface IP address with fixed port disabled? (Choose two.)
- A . This is known as many-to-one NAT.
- B . Source IP is translated to the outgoing interface IP.
- C . Connections are tracked using source port and source MAC address.
- D . Port address translation is not used.
If the Issuer and Subject values are the same in a digital certificate, which type of entity was the certificate issued to?
- A . A CRL
- B . A person
- C . A subordinate CA
- D . A root CA
What is the limitation of using a URL list and application control on the same firewall policy, in NCFW policy-based mode?
- A . It limits the scope of application control to the browser-based technology category only.
- B . It limits the scope of application control to scan application traffic based on application category only.
- C . It limits the scope of application control to scan application traffic using parent signatures only
- D . It limits the scope of application control to scan application traffic on DNS protocol only.
The FSSO Collector Agent set to advanced access mode for the Windows Active Directory uses which of the following?
- A . LDAP convention
- B . NTLM convention
- C . Windows convention – NetBios: DomainUsemame
- D . RSSO convention
Examine the following web filtering log.
Which statement about the log message is true?
- A . The action for the category Games is set to block.
- B . The usage quota for the IP address 10.0.1.10 has expired.
- C . The name of the applied web filter profile is default.
- D . The web site miniclip.com matches a static URL filter whose action is set to Warning.