DELL EMC D-ISM-FN-23 Dell Information Storage and Management Foundations 2023 Online Training
DELL EMC D-ISM-FN-23 Online Training
The questions for D-ISM-FN-23 were last updated at Feb 03,2026.
- Exam Code: D-ISM-FN-23
- Exam Name: Dell Information Storage and Management Foundations 2023
- Certification Provider: DELL EMC
- Latest update: Feb 03,2026
Under the IaaS model, which elements are managed by the provider?
- A . Applications
Data
OS - B . Applications
Middleware
Runtime - C . Data
Servers
Networking - D . Virtualization
Servers
Networking
Which storage management function ensures that the services and service levels are delivered per SLAs?
- A . Infrastructure discovery management
- B . Portfolio management
- C . Financial management
- D . Operation management
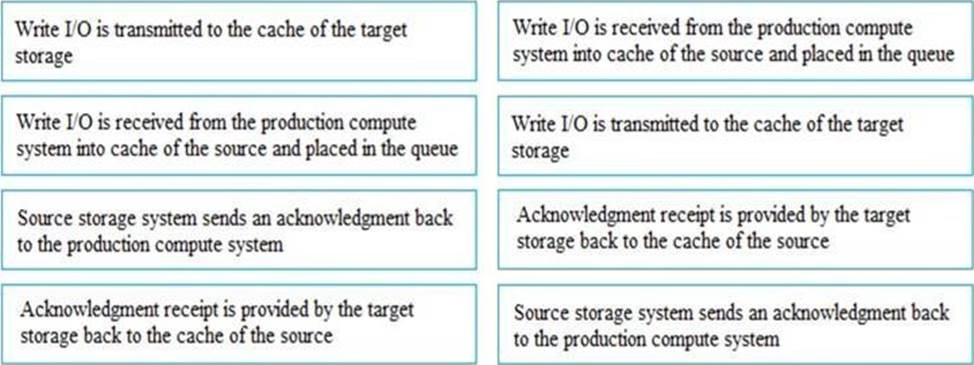
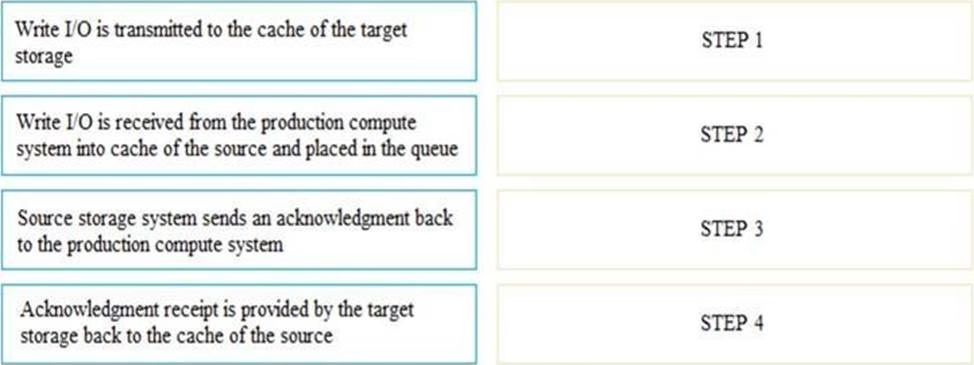
What is the correct sequence of steps that need to be performed in storage system-based synchronous remote replication?
What is a benefit of using a purpose-build NAS solution vs. general purpose file servers?
- A . provides more efficient object sharing across Windows and Linux users
- B . provides more efficient file sharing across Windows and Linux users
- C . provides higher compute security and efficient file sharing across Windows and Linux users
- D . provides higher network security and efficient object sharing across Windows and Linux users
A customer has a requirement to perform a backup each night. However, the customer has a limited amount of time for backups to run on week nights, Monday through Friday evenings.
Which backup granularity type is recommended to meet the backup window for those nights?
- A . Incremental
- B . Cumulative
- C . Full
- D . Differential
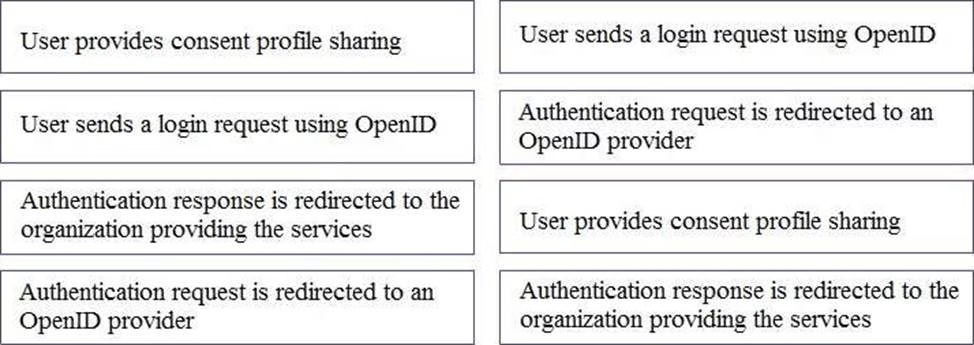
To authenticate a user using OpenID authentication control, what are the correct sequence of steps?

What accurately describes the flow control mechanism in an FC SAN?
- A . Both transmitting and receiving ports agree on the number of buffers available during port login
- B . Negotiation occurs between an E_Port and an F_Port, and between two N_Ports
- C . Credit value is incremented when a frame is transmitted and decremented upon receiving a response
- D . Receiver Ready (R_RDY) is sent from the receiving port if available credits reach zero
Which of the following are key characteristics of Big Data? (Choose two)
- A . Variety
- B . Velocity
- C . Veracity
- D . Vulnerability
Which iSCSI host connectivity option is recommended in a CPU-intensive application environment?
- A . NIC with software-based iSCSI initiator
- B . TCP offload engine
- C . iSCSI HBA
- D . Converged Network Adapter
What is an accurate statement about the Network File System (NFS) protocol?
- A . Provides a set of remote procedure calls to access a remote file system
- B . Uses the server message block protocol to provide file locking capability
- C . Translates block I/O requests from a file system into object-level requests
- D . Automatically scales the file systems on clients as the workload increases
Latest D-ISM-FN-23 Dumps Valid Version with 580 Q&As
Latest And Valid Q&A | Instant Download | Once Fail, Full Refund