What do you need on the Vault to support LDAP over SSL?
- A . CA Certificate(s) used to sign the External Directory certificate
- B . RECPRV.key
- C . a private key for the external directory
- D . self-signed Certificate(s) for the Vault
You are troubleshooting a PVWA slow response.
Which log files should you analyze first? (Choose two.)
- A . ITALog.log
- B . web.config
- C . CyberArk.WebApplication.log
- D . CyberArk.WebConsole.log
What is the easiest way to duplicate an existing platform?
- A . From Private Ark, copy/paste the appropriate Policy.ini file; then rename it.
- B . From the PVWA, navigate to the platforms page, select an existing platform that is similar to the new target account platform and then click Duplicate; name the new platform.
- C . From Private Ark, copy/paste the appropriate settings in PVConfiguration.xml; then update the policy Name variable.
- D . From the PVWA, navigate to the platforms page, select an existing platform that is similar to the new target account platform, manually update the platform settings and click "Save as" INSTEAD of save to duplicate and rename the platform.
Due to corporate storage constraints, you have been asked to disable session monitoring and recording for 500 testing accounts used for your lab environment.
How do you accomplish this?
- A . Master Policy>select Session Management>add Exceptions to the platform(s)>disable Session Monitoring and Recording policies
- B . Administration>Platform Management>select the platform(s)>disable Session Monitoring and Recording
- C . Polices>Access Control (Safes)>select the safe(s)>disable Session Monitoring and Recording policies
- D . Administration>Configuration Options>Options>select Privilege Session Management>disable Session Monitoring and Recording policies
A user requested access to view a password secured by dual-control and is unsure who to contact to expedite the approval process. The Vault Admin has been asked to look at the account and identify who can approve their request.
What is the correct location to identify users or groups who can approve?
- A . PVWA > Administration > Platform Configuration > Edit Platform > UI & Workflow > Dual Control > Approvers
- B . PVWA > Policies > Access Control (Safes) > Select the safe > Safe Members > Workflow > Authorize Password Requests
- C . PVWA > Account List > Edit > Show Advanced Settings > Dual Control > Direct Managers
- D . Private Ark > Admin Tools > Users and Groups > Auditors (Group Membership)
What must you specify when configuring a discovery scan for UNIX? (Choose two.)
- A . Vault Administrator
- B . CPM Scanner
- C . root password for each machine
- D . list of machines to scan
- E . safe for discovered accounts
To change the safe where recordings are kept for a specific platform, which setting must you update in the platform configuration?
- A . SessionRecorderSafe
- B . SessionSafe
- C . RecordingsPath
- D . RecordingLocation
Which processes reduce the risk of credential theft? (Choose two.)
- A . require dual control password access approval
- B . require password change every X days
- C . enforce check-in/check-out exclusive access
- D . enforce one-time password access
You are onboarding 5,000 UNIX root accounts for rotation by the CPM. You discover that the CPM is unable to log in directly with the root account and will need to use a secondary account.
How can this be configured to allow for password management using least privilege?
- A . Configure each CPM to use the correct logon account.
- B . Configure each CPM to use the correct reconcile account.
- C . Configure the UNIX platform to use the correct logon account.
- D . Configure the UNIX platform to use the correct reconcile account.
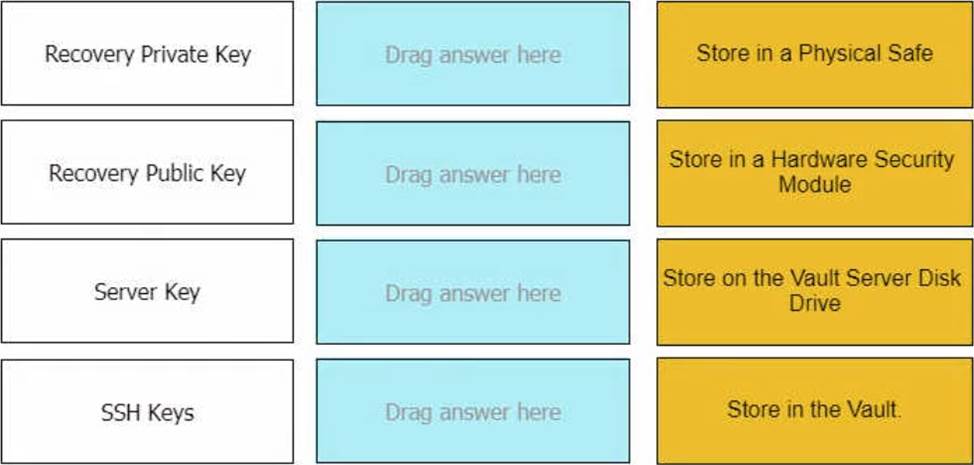
DRAG DROP
ADR Vault became active due to a failure of the primary Vault. Service on the primary Vault has now been restored. Arrange the steps to return the DR vault to its normal standby mode in the correct sequence.
DRAG DROP
ADR Vault became active due to a failure of the primary Vault. Service on the primary Vault has now been restored. Arrange the steps to return the DR vault to its normal standby mode in the correct sequence.
DRAG DROP
ADR Vault became active due to a failure of the primary Vault. Service on the primary Vault has now been restored. Arrange the steps to return the DR vault to its normal standby mode in the correct sequence.
DRAG DROP
ADR Vault became active due to a failure of the primary Vault. Service on the primary Vault has now been restored. Arrange the steps to return the DR vault to its normal standby mode in the correct sequence.
Which methods can you use to add a user directly to the Vault Admin Group? (Choose three.)
- A . REST API
- B . PrivateArk Client
- C . PACLI
- D . PVWA
- E . Active Directory
- F . Sailpoint
Which Automatic Remediation is configurable for a PTA detection of a "Suspected Credential Theft"?
- A . Add to Pending
- B . Rotate Credentials
- C . Reconcile Credentials
- D . Disable Account
Which item is an option for PSM recording customization?
- A . Windows events text recorder with automatic play-back
- B . Windows events text recorder and universal keystrokes recording simultaneously
- C . Universal keystrokes text recorder with windows events text recorder disabled
- D . Custom audio recording for windows events
C (75%)
B (25%)
DRAG DROP
Match the built-in Vault user with the correct definition.
You want to create a new onboarding rule.
Where do you accomplish this?
- A . In PVWA, click Reports > Unmanaged Accounts > Rules
- B . In PVWA, click Options > Platform Management > Onboarding Rules
- C . In PrivateArk, click Tools > Onboarding Rules
- D . In PVWA, click Accounts > Onboarding Rules
What does the Export Vault Data (EVD) utility do?
- A . exports data from the Vault to TXT or CSV files, or to MSSQL databases
- B . generates a backup file that can be used as a cold backup
- C . exports all passwords and imports them into another instance of CyberArk
- D . keeps two active vaults in sync
When are external vault users and groups synchronized by default?
- A . They are synchronized once every 24 hours between 1 AM and 5 AM.
- B . They are synchronized once every 24 hours between 7 PM and 12 AM.
- C . They are synchronized every 2 hours.
- D . They are not synchronized according to a specific schedule.
You created a new safe and need to ensure the user group cannot see the password, but can connect through the PSM.
Which safe permissions must you grant to the group? (Choose two.)
- A . List Accounts
- B . Use Accounts
- C . Access Safe without Confirmation
- D . Retrieve Files
- E . Confirm Request
During a High Availability node switch you notice an error and the Cluster Vault Manager Utility fails back to the original node.
Which log files should you check to investigate the cause of the issue? (Choose three.)
- A . CyberArk Webconsole.log
- B . VaultDB.log
- C . PM_Error.log
- D . ITALog.log
- E . ClusterVault.console.log
- F . logiccontainer.log
Which parameters can be used to harden the Credential Files (CredFiles) while using CreateCredFile Utility? (Choose three.)
- A . OS Username
- B . Current machine IP
- C . Current machine hostname
- D . Operating System Type (Linux/Windows/HP-UX)
- E . Vault IP Address
- F . Time Frame
Where can a user with the appropriate permissions generate a report? (Choose two.)
- A . PVWA > Reports
- B . PrivateArk Client
- C . Cluster Vault Manager
- D . PrivateArk Server Monitor
- E . PARClient
Users are unable to launch Web Type Connection components from the PSM server. Your manager asked you to open the case with CyberArk Support.
Which logs will be most useful for the CyberArk Support Team to debug the issue? (Choose three.)
- A . PSMConsole.log
- B . PSMDebug.log
- C . PSMTrace.log
- D . <Session_ID>.Component.log
- E . PMconsole.log
- F . ITALog.log
You have been asked to identify the up or down status of Vault Services.
Which CyberArk utility can you use to accomplish this task?
- A . PrivateArk Central Administration Console
- B . PAS Reporter
- C . PrivateArk Remote Control Agent
- D . Syslog
A new colleague created a directory mapping between the Active Directory groups and the Vault.
Where can the newly Configured directory mapping be tested?
- A . Connect to the Active Directory and ensure the organizational unit exists.
- B . Connect to Sailpoint (or similar tool) to ensure the organizational unit is correctly named; log in to the PVWA with "Administrator" and confirm authentication succeeds.
- C . Search for members that exist only in the mapping group to grant them safe permissions through the PVWA.
- D . Connect to the PrivateArk Client with the Administrator Account to see if there is a user in the Vault Admin Group.
A user needs to view recorded sessions through the PVWA.
Without giving auditor access, which safes does a user need access to view PSM recordings? (Choose two.)
- A . Recordings safe
- B . Safe the account is in
- C . System safe
- D . PVWA Configuration safe
- E . Vault Internal safe
Which file must be edited on the Vault to configure it to send data to PTA?
- A . dbparm.ini
- B . PARAgent.ini
- C . my.ini
- D . padr.ini
You want to build a connector that connects to a website through the Web applications for PSM framework.
Which default connector do you duplicate and modify?
- A . PSM-ChromeSample
- B . PSM-WebForm
- C . PSM-WebApp
- D . PSM-WebAppSample
DRAG DROP
A new HTML5 Gateway has been deployed in your organization.
From the PVWA, arrange the steps to configure a PSM host to use the HTML5 Gateway in the correct sequence.
When an account is unable to change its own password, how can you ensure that password reset with the reconcile account is performed each time instead of a change?
- A . Set the parameter RCAllowManualReconciliation to Yes.
- B . Set the parameter ChangePasswordinResetMade to Yes.
- C . Set the parameter IgnoreReconcileOnMissingAccount to No.
- D . Set the UnlockUserOnReconcile to Yes.
In a default CyberArk installation, which group must a user be a member of to view the "reports" page in PVWA?
- A . PVWAMonitor
- B . ReportUsers
- C . PVWAReports
- D . Operators
Your organization requires all passwords be rotated every 90 days.
Where can you set this requirement?
- A . Master Policy
- B . Safe Templates
- C . PVWAConfig.xml
- D . Platform Configuration
According to CyberArk, which issues most commonly cause installed components to display as disconnected in the System Health Dashboard? (Choose two.)
- A . network instabilities/outages
- B . vault license expiry
- C . credential de-sync
- D . browser compatibility issues
- E . installed location file corruption
Where can reconcile and/or logon accounts be linked to an account? (Choose two.)
- A . account settings
- B . platform settings
- C . master policy
- D . safe settings
- E . service account settings
You are running a "Privileged Accounts Inventory" Report through the Reports page in PVWA on a specific safe.
To show complete account inventory information, which permission/s are needed on that safe?
- A . List Accounts, View Safe Members
- B . Manage Safe Owners
- C . List Accounts, Access Safe without confirmation
- D . Manage Safe, View Audit