What is the purpose of a linked account?
- A . To ensure that a particular collection of accounts all have the same password.
- B . To ensure a particular set of accounts all change at the same time.
- C . To connect the CPNI to a target system.
- D . To allow more than one account to work together as part of a password management process.
Which components support fault tolerance.
- A . CPM and PVWA
- B . PVWA and PSM
- C . PSM and PTA
- D . CPM and PTA
Which statement is correct concerning accounts that are discovered, but cannot be added to the Vault by an automated onboarding rule?
- A . They are added to the Pending Accounts list and can be reviewed and manually uploaded.
- B . They cannot be onboarded to the Password Vault.
- C . They must be uploaded using third party tools.
- D . They are not part of the Discovery Process.
D
Explanation:
Reference: https://docs.cyberark.com/Product-Doc/OnlineHelp/PrivCloud/Latest/en/Content/Privilege%20Cloud/privCloud-accounts-discovery.htm
What is the purpose of the Interval setting in a CPM policy?
- A . To control how often the CPM looks for System Initiated CPM work.
- B . To control how often the CPM looks for User Initiated CPM work.
- C . To control how long the CPM rests between password changes.
- D . To control the maximum amount of time the CPM will wait for a password change to complete.
It is possible to leverage DNA to provide discovery functions that are not available with auto-detection.
- A . TRUE
- B . FALS
Which CyberArk utility allows you to create lists of Master Policy Settings, owners and safes for output to text files or MSSQL databases?
- A . Export Vault Data
- B . Export Vault Information
- C . PrivateArk Client
- D . Privileged Threat Analytics
A
Explanation:
Reference: https://docs.cyberark.com/Product-Doc/OnlineHelp/PAS/Latest/en/Content/EVD/Exporting-Data-to-Files.htm?Highlight=evd%20italog
It is possible to restrict the time of day, or day of week that a [b]reconcile[/b] process can occur
- A . TRUE
- B . FALS
A
Explanation:
Password reconciliation can be restricted to specific days. This means that the CPM will only reconcile passwords on the days of the week specified in the RCExecutionDays parameter. The days of the week are represented by the first 3 letters of the name of the day. Sunday is represented by Sun, Mondayby Mon, etc.
Which user(s) can access all passwords in the Vault?
- A . Administrator
- B . Any member of Vault administrators
- C . Any member of auditors
- D . Master
You are installing HTML5 gateway on a Linux host using the RPM provided.
After installing the Tomcat webapp, what is the next step in the installation process?
- A . Deploy the HTML5 service (guacd)
- B . Secure the connection between the guacd and the webapp
- C . Secure the webapp and JWT validation endpoint
- D . Configure ASLR
For an account attached to a platform that requires Dual Control based on a Master Policy exception, how would you configure a group of users to access a password without approval.
- A . Create an exception to the Master Policy to exclude the group from the workflow process.
- B . Edith the master policy rule and modify the advanced’ Access safe without approval’ rule to include the group.
- C . On the safe in which the account is stored grant the group the’ Access safe without audit’ authorization.
- D . On the safe in which the account is stored grant the group the’ Access safe without confirmation’ authorization.
Which type of automatic remediation can be performed by the PTA in case of a suspected credential theft security event?
- A . Password change
- B . Password reconciliation
- C . Session suspension
- D . Session termination
Which components can connect to a satellite Vault in distributed Vault architecture?
- A . CPM, EPM, PTA
- B . PVWA, PSM
- C . CPM, PVWA, PSM
- D . CPM, PSM
Due to network activity, ACME Corp’s PrivateArk Server became active on the OR Vault while the Primary Vault was also running normally. All the components continued to point to the Primary Vault.
Which steps should you perform to restore DR replication to normal?
- A . Replicate data from DR Vault to Primary Vault > Shutdown PrivateArk Server on DR Vault > Start replication on DR vault
- B . Shutdown PrivateArk Server on DR Vault > Start replication on DR vault
- C . Shutdown PrivateArk Server on Primary Vault > Replicate data from DR Vault to Primary Vault > Shutdown PrivateArk Server on DR Vault > Start replication on DR vault
- D . Shutdown PrivateArk Server on DR Vault > Replicate data from DR Vault to Primary Vault > Shutdown PrivateArk Server on DR Vault > Start replication on DR vault
What is a requirement for setting fault tolerance for PSMs?
- A . Use a load balancer
- B . use a backup solution
- C . CPM must be in all data centers
- D . Install the Vault in an HA Cluster
What is the easiest way to duplicate an existing platform?
- A . From PrivateArk, copy/paste the appropriate Policy.ini file: then rename it.
- B . from the PVWA, navigate to the platforms page, select the existing platform that is similar to the new target account platform and click Duplicate, name the new platform.
- C . From PrivateArk, cop/paste the appropriate setting in the PVConfiguration.xml then update the policName variable.
- D . From the PVWA, navigate to the platforms page, select existing platform that is similar to the new target account platform, manually update the platform settings and click "Save as" instead of save to duplicate and rename the platform.
Target account platforms can be restricted to accounts that are stored m specific Safes using the Allowed Safes property.
- A . TRUE
- B . FALSE
What is the purpose of the PrivateArk Database service?
- A . Communicates with components
- B . Sends email alerts from the Vault
- C . Executes password changes
- D . Maintains Vault metadata
Which combination of Safe member permissions will allow end users to log in to a remote machine transparently but NOT show or copy the password?
- A . Use Accounts, Retrieve Accounts, List Accounts
- B . Use Accounts, List Accounts
- C . Use Accounts
- D . List Accounts, Retrieve Accounts
What is the easiest way to duplicate an existing platform?
- A . From PrivateArk, copy/paste the appropriate Policy.ini file; then rename it.
- B . From the PVWA, navigate to the platforms page, select an existing platform that is similar to the new target account platform and then click Duplicate; name the new platform.
- C . From PrivateArk, copy/paste the appropriate settings in PVConfiguration.xml; then update the policyName variable.
- D . From the PVWA, navigate to the platforms page, select an existing platform that is similar to the new target account platform, manually update the platform settings and click “Save as” INSTEAD of save to duplicate and rename the platform.
D
Explanation:
Reference: https://docs.cyberark.com/Product-Doc/OnlineHelp/PAS/Latest/en/Content/PASIMP/Adding-New-Platforms.htm#:~:text=Click%20ADMINISTRATION%20to%20display%20the,the%20Duplicate%20Platform%20window%20appears
You need to recover an account localadmin02 for target server 10.0.123.73 stored in Safe Team1.
What do you need to recover and decrypt the object? (Choose three.)
- A . Recovery Private Key
- B . Recover.exe
- C . Vault data
- D . Recovery Public Key
- E . Server Key
- F . Master Password
A,D,E
Explanation:
Reference: https://docs.cyberark.com/Product-Doc/OnlineHelp/PAS/Latest/en/Content/PASIMP/Server-Keys.htm?TocPath=Administration%7CComponents%7CDigital%20Vault%7CAdvanced%20Digital%20Vault%20Environment%7CCyberArk%20Vault%20Structure%7C_____3
When onboarding multiple accounts from the Pending Accounts list, which associated setting must be the same across the selected accounts?
- A . Platform
- B . Connection Component
- C . CPM
- D . Vault
A
Explanation:
Reference: https://docs.cyberark.com/Product-Doc/OnlineHelp/PAS/Latest/en/Content/PASIMP/Onboarding-Accounts-and-SSH-Keys.htm?Highlight=safe%20does%20not%20support%20properties
The Privileged Access Management solution provides an out-of-the-box target platform to manage SSH keys, called UNIX Via SSH Keys.
How are these keys managed?
- A . CyberArk stores Private keys in the Vault and updates Public keys on target systems.
- B . CyberArk stores Public keys in the Vault and updates Private keys on target systems.
- C . CyberArk does not store Public or Private keys and instead uses a reconcile account to create keys on demand.
- D . CyberArk stores both Private and Public keys and can update target systems with either key.
A
Explanation:
Reference: https://docs.cyberark.com/Product-Doc/OnlineHelp/PAS/11.4/en/Content/SSHKM/Using%20SSH%20Keys.htm
You are creating a shared safe for the help desk.
What must be considered regarding the naming convention?
- A . Ensure your naming convention is no longer than 20 characters.
- B . Combine environments, owners and platforms to minimize the total number of safes created.
- C . Safe owners should determine the safe name to enable them to easily remember it.
- D . The use of these characters V:*<>".| is not allowed.
D
Explanation:
Reference: https://docs.cyberark.com/Product-Doc/OnlineHelp/PAS/Latest/en/Content/MESSAGES/Safe%20Properties%20New%20Safe.htm?TocPath=Administration%7CReferences%7CMessages%20and%20Responses%7C PrivateArk%20Client%7C_____11
If a user is a member of more than one group that has authorizations on a safe, by default that user is granted________.
- A . the vault will not allow this situation to occur.
- B . only those permissions that exist on the group added to the safe first.
- C . only those permissions that exist in all groups to which the user belongs.
- D . the cumulative permissions of all groups to which that user belongs.
You are creating a Dual Control workflow for a team’s safe.
Which safe permissions must you grant to the Approvers group?
- A . List accounts, Authorize account request
- B . Retrieve accounts, Access Safe without confirmation
- C . Retrieve accounts, Authorize account request
- D . List accounts, Unlock accounts
C
Explanation:
Reference: https://docs.cyberark.com/Product-Doc/OnlineHelp/PAS/Latest/en/Content/PASIMP/PVWA-Dual-Control.htm (expand all and search for retrieve accounts)
CyberArk recommends implementing object level access control on all Safes.
- A . True
- B . False
The vault supports Role Based Access Control.
- A . TRUE
- B . FALSE
B
Explanation:
Reference https://docs.cyberark.com/Product-Doc/OnlineHelp/PAS/Latest/en/Content/PASIMP/Object-Level-Access-Control.htm
Which of the following logs contains information about errors related to PTA?
- A . ITAlog.log
- B . diamond.log
- C . pm_error.log
- D . WebApplication.log
By default, members of which built-in groups will be able to view and configure Automatic Remediation and Session Analysis and Response in the PVWA?
- A . Vault Admins
- B . Security Admins
- C . Security Operators
- D . Auditors
As long as you are a member of the Vault Admins group, you can grant any permission on any safe that you have access to.
- A . TRUE
- B . FALSE
B
Explanation:
Being in Vault admins group only give you access to safes which are created during installation (safe created in installation process) -This is clearly mentioned in documents.
Which of the following PTA detections are included in the Core PAS offering?
- A . Suspected Credential Theft
- B . Over-Pass-The Hash
- C . Golden Ticket
- D . Unmanaged Privileged Access
A Logon Account can be specified in the Master Policy.
- A . TRUE
- B . FALSE
In addition to disabling Windows services or features not needed for PVWA operations, which tasks does PVWA Hardening.ps1 perform when run?
- A . Performs IIS hardening: Imports the CyberArk INF configuration
- B . Performs IIS hardening: Configures all group policy settings
- C . Performs IIS hardening: Renames the local Administrator Account
- D . Configures Windows Firewall: Removes all installation files.
For Digital Vault Cluster in a high availability configuration, how does the cluster determine if a node is down?
- A . The heartbeat s no longer detected on the private network.
- B . The shared storage array is offline.
- C . An alert is generated in the Windows Event log.
- D . The Digital Vault Cluster does not detect a node failure.
A
Explanation:
Reference: https://docs.cyberark.com/Product-Doc/OnlineHelp/PAS/Latest/en/Content/PASIMP/Managing-the-CyberArk-Digital-Cluster-Vault-Server.htm?TocPath=Administration%7CComponents%7CDigital%20Vault%7COperate%20the%20CyberArk%20Vault%7CCyberArk%20High-Availability%20Vault%20Cluster%7C_____1
Which parameters can be used to harden the Credential Files (CredFiles) while using CreateCredFile Utility? (Choose three.)
- A . Operating System Username
- B . Host IP Address
- C . Client Hostname
- D . Operating System Type (Linux/Windows/HP-UX)
- E . Vault IP Address
- F . Time Frame
A,B,C
Explanation:
Reference: https://docs.cyberark.com/Product-Doc/OnlineHelp/PAS/11.2/en/Content/PASIMP/CreateCredFile-Utility.htm
A new HTML5 Gateway has been deployed in your organization.
Where do you configure the PSM to use the HTML5 Gateway?
- A . Administration > Options > Privileged Session Management > Configured PSM Servers > Connection Details > Add PSM Gateway
- B . Administration > Options > Privileged Session Management > Add Configured PSM Gateway Servers
- C . Administration > Options > Privileged Session Management > Configured PSM Servers > Add PSM Gateway
- D . Administration > Options > Privileged Session Management > Configured PSM Servers > Connection Details
Which Automatic Remediation is configurable for a PTA detection of a “Suspected Credential Theft”?
- A . Add to Pending
- B . Rotate Credentials
- C . Reconcile Credentials
- D . Disable Account
Which SMTP address can be set on the Notification Settings page to re-invoke the ENE setup wizard after the initial Vault installation.
- A . 255.255.255.255
- B . 8.8.8.8
- C . 192.168.1.1
- D . 1.1.1.1
DRAG DROP
For each listed prerequisite, identify if it is mandatory or not mandatory to run the PSM Health Check.
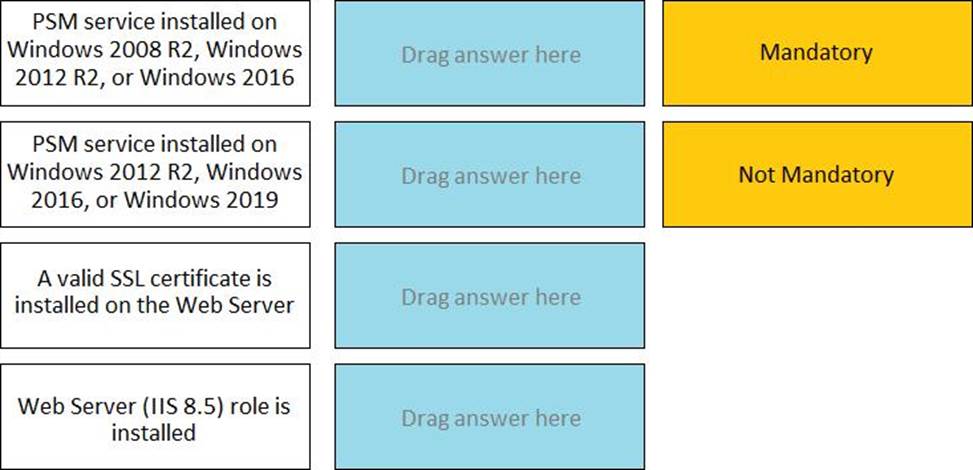
The password upload utility must run from the CPM server
- A . TRUE
- B . FALSE
Which permissions are needed for the Active Directory user required by the Windows Discovery process?
- A . Domain Admin
- B . LDAP Admin
- C . Read/Write
- D . Read
tsparm.ini is the main configuration file for the Vault.
- A . True
- B . False
Which Master Policy Setting must be active in order to have an account checked-out by one user for a pre-determined amount of time?
- A . Require dual control password access Approval
- B . Enforce check-in/check-out exclusive access
- C . Enforce one-time password access
- D . Enforce check-in/check-out exclusive access & Enforce one-time password access
If a customer has one data center and requires high availability, how many PVWA’s should be deployed.
- A . Two
- B . One PVWA cluster
- C . One
- D . Two PVWA Cluster
What is the purpose of the Immediate Interval setting in a CPM policy?
- A . To control how often the CPM looks for System Initiated CPM work.
- B . To control how often the CPM looks for User Initiated CPM work.
- C . To control how often the CPM rests between password changes.
- D . To Control the maximum amount of time the CPM will wait for a password change to complete.
B
Explanation:
When the Master Policy enforces check-in/check-out exclusive access, passwords are changed when the user clicks the Release button and releases the account. This is based on the ImmediateInterval parameter in the applied platform. If the user forgets to release the account, it is automatically released and changed by the CPM after a predetermined number of minutes, defined in the MinValidityPeriod parameter specified in the platform
Which report could show all accounts that are past their expiration dates?
- A . Privileged Account Compliance Status report
- B . Activity log
- C . Privileged Account Inventory report
- D . Application Inventory report
In a default CyberArk installation, which group must a user be a member of to view the “reports” page in PVWA?
- A . PVWAMonitor
- B . ReportUsers
- C . PVWAReports
- D . Operators
A
Explanation:
Reference: https://docs.cyberark.com/Product-Doc/OnlineHelp/PAS/Latest/en/Content/PASIMP/ReportsInPVWA.htm?TocPath=End%20User%7CReports%20and%20Audits%7C_____1#:~:text=Reports%20can%20be%20genera ted%20in,this%20is%20the%20PVWAMonitor%20group
An auditor needs to login to the PSM in order to live monitor an active session.
Which user ID is used to establish the RDP connection to the PSM server?
- A . PSMConnect
- B . PSMMaster
- C . PSMGwUser
- D . PSMAdminConnect
Which Cyber Are components or products can be used to discover Windows Services or Scheduled Tasks that use privileged accounts? Select all that apply.
- A . Discovery and Audit (DMA)
- B . Auto Detection (AD)
- C . Export Vault Data (EVD)
- D . On Demand Privileges Manager (OPM)
- E . Accounts Discovery
If a password is changed manually on a server, bypassing the CPM, how would you configure the account so that the CPM could resume management automatically?
- A . Configure the Provider to change the password to match the Vault’s Password
- B . Associate a reconcile account and configure the platform to reconcile automatically
- C . Associate a logon account and configure the platform to reconcile automatically
- D . Run the correct auto detection process to rediscover the password
Assuming a safe has been configured to be accessible during certain hours of the day, a Vault Admin may still access that safe outside of those hours.
- A . TRUE
- B . FALSE
Which option in the Private Ark client is used to update users’ Vault group memberships?
- A . Update > General tab
- B . Update > Authorizations tab
- C . Update > Member Of tab
- D . Update > Group tab
A
Explanation:
Reference: https://docs.cyberark.com/Product-Doc/OnlineHelp/PAS/Latest/en/Content/PASIMP/Predefined-Users-and-Groups.htm?TocPath=Administration%7CUser%20Management%7C_____7
As long as you are a member of the Vault Admins group you can grant any permission on any safe.
- A . TRUE
- B . FALSE
B
Explanation:
Being in Vault admins group only give you access to safes which are created during installation (safe created in installation process) -This is clearly mentioned in documents .
You have associated a logon account to one your UNIX cool accounts in the vault.
When attempting to [b]change [/b] the root account’s password the CPM will…..
- A . Log in to the system as root, then change root’s password
- B . Log in to the system as the logon account, then change roofs password
- C . Log in to the system as the logon account, run the su command to log in as root, and
then change root’s password. - D . None of these
How much disk space do you need on the server for a PAReplicate?
- A . 500 GB
- B . 1 TB
- C . same as disk size on Satellite Vault
- D . same as disk size on Primary Vault
D
Explanation:
Reference: https://docs.cyberark.com/Product-Doc/OnlineHelp/PAS/Latest/en/Content/PAS%20INST/Installing-the-Vault-Backup-Utility.htm#Beforeinstallation
Which of the following options is not set in the Master Policy?
- A . Password Expiration Time
- B . Enabling and Disabling of the Connection Through the PSM
- C . Password Complexity
- D . The use of “One-Time-Passwords”
What is the maximum number of levels of authorization you can set up in Dual Control?
- A . 1
- B . 2
- C . 3
- D . 4
In PVWA, you are attempting to play a recording made of a session by user jsmith, but there is no option to “Fast Forward” within the video. It plays and only allows you to skip between commands instead. You are also unable to download the video.
What could be the cause?
- A . Recording is of a PSM for SSH session.
- B . The browser you are using is out of date and needs an update to be supported.
- C . You do not have the “View Audit” permission on the safe where the account is stored.
- D . You need to update the recorder settings in the platform to enable screen capture every 10000 ms or less.
B
Explanation:
Reference: https://cyberark-customers.force.com/s/article/00004935
You are installing multiple PVWAs behind a load balancer.
Which statement is correct?
- A . Port 1858 must be opened between the load balancer and the PVWAs
- B . The load balancer must be configured in DNS round robin.
- C . The load balancer must support "sticky sessions".
- D . The Load Balancer Client Address Header parameter in the PVwA.ini file must be set.
CyberArk user Neil is trying to connect to the Target Linux server 192.168.1.64 using a domain account ACME/linuxuser01 on Domain Acme.corp using PSM for SSH server 192.168.65.145.
What is the correct syntax?
- A . Ssh neil@linuxuser01: acme.corp@192.168.1.64@192.168.1.45
- B . Ssh neil@linuxuser01#acme.corp@192.168.1.64@192.168.1.45
- C . Ssh neil@linuxuser01@192.168.1.64@192.168.65.145
- D . Ssh neil@linuxuser01@acme.corp@192.168.1.64@192.168.1.45
According to the DEFAULT Web Options settings, which group grants access to the REPORTS page?
- A . PVWAUsers
- B . Vault Admins
- C . Auditors
- D . PVWAMonitor
To manage automated onboarding rules, a CyberArk user must be a member of which group?
- A . Vault Admins
- B . CPM User
- C . Auditors
- D . Administrators
A
Explanation:
Reference: https://docs.cyberark.com/Product-Doc/OnlineHelp/PAS/11.2/en/Content/PASIMP/automatic_onboarding_rules.htm#:~:text=To%20manage%20onboarding%20rules%2C%20users,to%20the%20Vault%20admins%20 group
What is the name of the Platform parameters that controls how long a password will stay valid when One Time Passwords are enabled via the Master Policy?
- A . Min Validity Period
- B . Interval
- C . Immediate Interval
- D . Timeout
A
Explanation:
Min Validity Period -The number of minutes to wait from the last retrieval of the password until it is replaced. This gives the user a minimum period to be able to use the password before it is replaced. Use -1 to ignore this property. This parameter is also used to release exclusive accounts automatically Interval C“The number of minutes that the Central Policy Manager waits between running periodic searches for the platform. Note: It is recommended to leave the default value of 1440. If a change/verify policy has been configured, the Central Policy Manager will automatically align the periodic searches with the start of the defined timeframes.”
When a DR Vault Server becomes an active vault, it will automatically fail back to the original state once the Primary Vault comes back online.
- A . True; this is the default behavior
- B . False; this is not possible
- C . True, if the AllowFailback setting is set to “yes” in the padr.ini file
- D . True, if the AllowFailback setting is set to “yes” in the dbparm.ini file
Which usage can be added as a service account platform?
- A . Kerberos Tokens
- B . IIS Application Pools
- C . PowerShell Libraries
- D . Loosely Connected Devices
D
Explanation:
Reference: https://docs.cyberark.com/Product-Doc/OnlineHelp/PAS/11.3/en/Content/PASIMP/LooselyConnectedDevices.htm
Which built-in report from the reports page in PVWA displays the number of days until a password is due to expire?
- A . Privileged Accounts Inventory
- B . Privileged Accounts Compliance Status
- C . Activity Log
- D . Privileged Accounts CPM Status
B
Explanation:
Reference: https://docs.cyberark.com/Product-Doc/OnlineHelp/PAS/Latest/en/Content/PASIMP/ReportsInPVWA.htm?TocPath=End%20U ser%7CReports%20and%20Audits%7C_____1
Which keys are required to be present in order to start the PrivateArk Server service?
- A . Recovery public key
- B . Recovery private key
- C . Server key
- D . Safe key
Which tools are used during a CPM renaming process?
- A . APIKeyManager Utility
- B . CreateCredFile Utility
- C . CPMinDomain_Hardening.ps1
- D . PMTerminal.exe
- E . Data Execution Prevention
Which of the following components can be used to create a tape backup of the Vault?
- A . Disaster Recovery
- B . Distributed Vaults
- C . Replicate
- D . High Availability
Which authentication methods does PSM for SSH support?
- A . CyberArk Password, LDAP, RADIUS, SAML
- B . LDAP, Windows Authentication, SSH Keys
- C . RADIUS, Oracle SSO, CyberArk Password
- D . CyberArk Password, LDAP, RADIUS
Accounts Discovery allows secure connections to domain controllers.
- A . TRUE
- B . FALSE
It is possible to restrict the time of day, or day of week that a [b]verify[/b] process can occur
- A . TRUE
- B . FALSE
A
Explanation:
Password verification can be restricted to specific days. This means that the CPM will only verify passwords on the days of the week specified in the VFExecutionDays parameter. The days of the week are represented by the first 3 letters of the name of the day. Sunday is represented by Sun, Monday by Mon, etc.
You received a notification from one of your CyberArk auditors that they are missing Vault level audit permissions. You confirmed that all auditors are missing the Audit Users Vault permission.
Where do you update this permission for all auditors?
- A . Private Ark Client > Tools > Administrative Tools > Directory Mapping > Vault Authorizations
- B . Private Ark Client > Tools > Administrative Tools > Users and Groups > Auditors > Authorizations tab
- C . PVWA User Provisioning > LDAP integration > Vault Auditors Mapping > Vault Authorizations
- D . PVWA> Administration > Configuration Options > LDAP integration > Vault Auditors Mapping > Vault Authorizations
B
Explanation:
Reference: https://docs.cyberark.com/Product-Doc/OnlineHelp/PAS/Latest/en/Content/PASIMP/Managing-Users.htm
Can the ‘Connect’ button be used to initiate an SSH connection, as root, to a Unix system when SSH access for root is denied?
- A . Yes, when using the connect button, CyberArk uses the PMTerminal.exe process which bypasses the root SSH restriction.
- B . Yes, only if a logon account is associated with the root account and the user connects through the PSM-SSH connection component.
- C . Yes, if a logon account is associated with the root account.
- D . No, it is not possible.
DRAG DROP
Match each PTA alert category with the PTA sensors that collect the data for it.
Which onboarding method would you use to integrate CyberArk with your accounts provisioning process?
- A . Accounts Discovery
- B . Auto Detection
- C . Onboarding RestAPI functions
- D . PTA Rules
A user with administrative privileges to the vault can only grant other users privileges that he himself has.
- A . TRUE
- B . FALSE
Which of the following properties are mandatory when adding accounts from a file? (Choose three.)
- A . Safe Name
- B . Platform ID
- C . All required properties specified in the Platform
- D . Username
- E . Address
- F . Hostname
A,B,C
Explanation:
Reference: https://docs.cyberark.com/Product-Doc/OnlineHelp/PAS/Latest/en/Content/NewUI/NewUI-Add-multiple-accounts-in-PVWA.htm
Which is the primary purpose of exclusive accounts?
- A . Reduced risk of credential theft
- B . More frequent password changes
- C . Non-repudiation (individual accountability)
- D . To force a ‘collusion to commit’ fraud ensuring no single actor may use a password without authorization